Exam 7: HCNA-Security-CBSN (Huawei Certified Network Associate - Constructing Basic Security Network)
Exam 1: HCNA-VC (Huawei Certified Network Associate - Video Conference)151 Questions
Exam 2: HHCIA Routing&Switching456 Questions
Exam 3: HCNP-R&S-IERN (Huawei Certified Network Professional-Implementing Enterprise Routing Network)206 Questions
Exam 4: HCNP-R&S-IENPÂ (Huawei Certified Network Professional-Improving Enterprise Network Performance)10 Questions
Exam 5: HCNP-R&S Fast Track (Huawei Certified Network Professional - Routing & Switching Fast Track)733 Questions
Exam 6: HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching)331 Questions
Exam 7: HCNA-Security-CBSN (Huawei Certified Network Associate - Constructing Basic Security Network)27 Questions
Exam 8: HCNA-Storage-BSSN (Huawei Certified Network Associate - Building the Structure of Storage Network)170 Questions
Exam 9: HCNA-Storage-BSSN60 Questions
Exam 10: Huawei Certified Network Professional- Constructing Big Data Solution215 Questions
Exam 11: HCIE-Storage472 Questions
Exam 12: HCIA-Cloud Service V2.236 Questions
Exam 13: Huawei Certified Pre-sales Associate-IP Network(Datacom)-ENU101 Questions
Exam 14: Huawei Certified Pre-sales Associate - ECC (HCPA-ECC)24 Questions
Exam 15: HCNA - Carrier IP25 Questions
Exam 16: HCIP-Cloud Computing-CDSM28 Questions
Exam 17: HCIA-SDN53 Questions
Select questions type
In the GRE configuration environment, which of the following interface or IP address is the local GRE device configuration of the end private network route required to point to? (Choose two.)
Free
(Multiple Choice)
4.9/5  (35)
(35)
Correct Answer:
A,C
In IPSEC VPN, which of the following scenarios can be applied by tunnel mode?
Free
(Multiple Choice)
4.8/5  (29)
(29)
Correct Answer:
C
How to view the matching number of security policy?
Free
(Multiple Choice)
4.8/5  (50)
(50)
Correct Answer:
B
In the environment of GRE configuration, which of the following statements are true? (Choose three.)
(Multiple Choice)
4.8/5  (33)
(33)
What are the classification of USG firewall user authentication? (Choose three.)
(Multiple Choice)
5.0/5  (41)
(41)
Which of the following statement about Internet user group management is wrong?
(Multiple Choice)
4.8/5  (42)
(42)
Which scenarios does IPSec WEB configuration wizard not support?
(Multiple Choice)
4.8/5  (37)
(37)
Which of the following addresses can be used for web management address of USG product? (Choose three.)
(Multiple Choice)
4.8/5  (40)
(40)
In SSL handshake protocol, what is the role of Server Key Exchange message?
(Multiple Choice)
4.9/5  (31)
(31)
In most scenarios, NAT Inbound is used to the enterprise private network users to access the Internet scenario.
(True/False)
4.8/5  (39)
(39)
In the first stage of IKE negotiation, which of the following IKE exchange mode does not provide identity protection features?
(Multiple Choice)
4.9/5  (32)
(32)
When you configure a firewall between the domain security policy, if the 192.168.0.0/24 network segment is set to match object, the following configuration, which is correct? (Choose two.)
(Multiple Choice)
4.8/5  (27)
(27)
As shown, when configuring the point-to-multipoint scenarios, the headquarters network segment is 10.1.1.0/24, the segment of branch 1 is 10.1.2.0/24, of branch 2 is 10.1.3.0/24. About the protected data flow configuration which defined by headquarters and branch offices, which of the following combinations can be the full matched requirements? 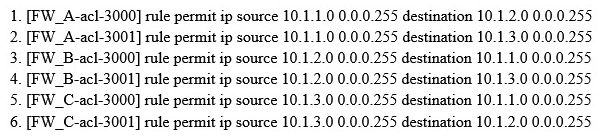
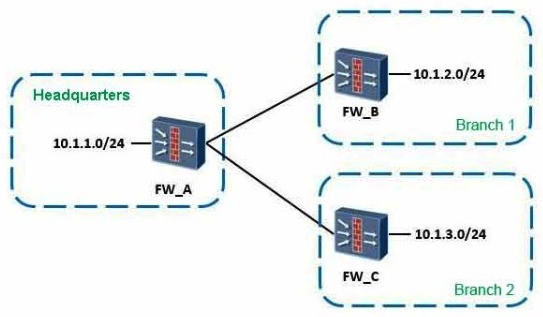
(Multiple Choice)
4.8/5  (40)
(40)
Some applications, such as Oracle database application, there is no data transfer for a long time, so that firewall session connection is interrupted, thus resulting in service interruption, which of the following technology can solve this problem?
(Multiple Choice)
4.7/5  (32)
(32)
What are the following values can be set as in USG series firewall security level definition from the security zone? (Choose two.)
(Multiple Choice)
4.9/5  (35)
(35)
Policy Center system can implement two dimensions' management functions: organizational management and regional management
(True/False)
4.8/5  (44)
(44)
Showing 1 - 20 of 27
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)