Exam 12: Monitoring and Auditing AIS
Exam 1: Accounting Information Systems and Firm Value62 Questions
Exam 2: Accountants As Business Analysts43 Questions
Exam 3: Data Modeling45 Questions
Exam 4: Relational Databases and Enterprise Systems48 Questions
Exam 5: Sales and Collections Business Process25 Questions
Exam 6: Purchases and Payments Business Process15 Questions
Exam 7: Conversion Business Process18 Questions
Exam 9: Reporting Processes and Extensible Business Reporting Language XBRL50 Questions
Exam 10: Accounting Information Systems and Internal Controls57 Questions
Exam 11: Information Security and Computer Fraud47 Questions
Exam 12: Monitoring and Auditing AIS48 Questions
Exam 13: The Balanced Scorecard and Business Value of Information Technology27 Questions
Exam 14: Evaluating AIS Investments25 Questions
Exam 15: The Systems Development Life Cycle and Project Management: Addressing the Challenges of Building Ais Systems45 Questions
Select questions type
Parallel simulation attempts to simulate the firm's key features or processes.
Free
(True/False)
4.8/5  (43)
(43)
Correct Answer:
True
Data governance is the convergence of data quality,data management,data policies,business process management,and risk management surrounding the handling of data in a company.
Free
(True/False)
4.8/5  (34)
(34)
Correct Answer:
True
Which of the following statements is not correct?
Free
(Multiple Choice)
4.9/5  (31)
(31)
Correct Answer:
B
The results of a generalized audit software simulation of the aging of accounts receivable revealed substantial differences in the aging contribution,even though grand totals reconciled.Which of the following should the IS auditor do first to resolve the discrepancy?
(Multiple Choice)
4.9/5  (44)
(44)
A data warehouse is for daily operations and often includes data for the current fiscal year only.
(True/False)
4.9/5  (34)
(34)
Embedded audit module is a programmed audit module that is added to the system under review.
(True/False)
4.9/5  (43)
(43)
Which statements are incorrect about virtual private network (VPN)?
(Multiple Choice)
4.8/5  (44)
(44)
What are the benefits of conducting continuous audits (or monitoring)?
(Essay)
4.7/5  (33)
(33)
Within a WAN,a router would perform which of the following functions?
(Multiple Choice)
4.9/5  (41)
(41)
Which of the following describes a group of computers that connects the internal users of a company distributed over an office building?
(Multiple Choice)
4.8/5  (32)
(32)
Which of the following is the primary reason that many auditors hesitate to use embedded audit modules?
(Multiple Choice)
4.9/5  (50)
(50)
Data mining is the process of searching for patterns in the data in a data warehouse and to analyze the patterns for decision making.
(True/False)
4.8/5  (35)
(35)
Categorize the following scenarios as management,operational,or technical controls for wireless networks' security controls. 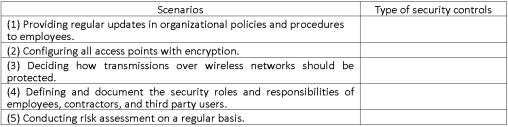
(Essay)
4.8/5  (38)
(38)
Accountants increasingly participate in designing internal controls and improving business and IT processes in a database environment.
(True/False)
4.7/5  (33)
(33)
What are the differences between LANs and WANs? Have you ever used any LANs and WANS?
1)LANs covers a small area while WANs covers a significantly larger area.
2)LANs speeds are also significantly faster than WANs.
3)LANs is more secure than WANs.
4)WANs are much more expensive to implement than LANs.
The Internet is the most popular WAN.A local area network is often used in a computer lab on campus.(Students' answers may vary.)
(Short Answer)
4.8/5  (37)
(37)
Virtual private network (VPN)is a private network,provided by a third party,for exchanging information through a high capacity connection.
(True/False)
4.8/5  (38)
(38)
Which of the following statements is wrong regarding continuous audit?
(Multiple Choice)
4.9/5  (35)
(35)
Showing 1 - 20 of 48
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)