Exam 20: Auditing in a Computerized Environment
Exam 1: Auditing and Assurance Services115 Questions
Exam 2: Professional Standards124 Questions
Exam 3: Engagement Planning146 Questions
Exam 4: Management Fraud and Audit Risk125 Questions
Exam 5: Risk Assessment: Internal Control Evaluation125 Questions
Exam 6: Employee Fraud and the Audit of Cash104 Questions
Exam 7: Revenue and Collection Cycle109 Questions
Exam 8: Acquisition and Expenditure Cycle129 Questions
Exam 9: Production Cycle98 Questions
Exam 10: Finance and Investment Cycle114 Questions
Exam 11: Completing the Audit132 Questions
Exam 12: Reports on Audited Financial Statements114 Questions
Exam 13: Other Public Accounting Services114 Questions
Exam 14: Professional Ethics124 Questions
Exam 15: Legal Liability137 Questions
Exam 16: Internal Governmental and Fraud Audits119 Questions
Exam 17: Overview of Sampling131 Questions
Exam 18: Attributes Sampling137 Questions
Exam 19: Variables Sampling136 Questions
Exam 20: Auditing in a Computerized Environment118 Questions
Select questions type
Which of the following is not an appropriate statement with regard to computer control activities?
(Multiple Choice)
4.7/5  (36)
(36)
An example of a program in which the audit team would be most interested in testing automated application controls is a(n)
(Multiple Choice)
4.7/5  (37)
(37)
The evaluation of computer controls with simulated data processed through the client's computer programs is referred to as
(Multiple Choice)
4.9/5  (34)
(34)
The effectiveness of general controls is an important consideration for audit teams when assessing control risk on an audit.Which management assertions are primarily affected by general controls?
(Multiple Choice)
4.8/5  (42)
(42)
Computer operators should have complete access to programs and application documentation.
(True/False)
4.8/5  (32)
(32)
____________________________ techniques are special audit modules designed and coded into computer programs to allow audit teams to evaluate various stages of transaction processing.
(Short Answer)
4.8/5  (39)
(39)
Match each of the following program-embedded techniques (letters A-I)with a description of these techniques (numbers 1-9).Each technique relates to only one description. 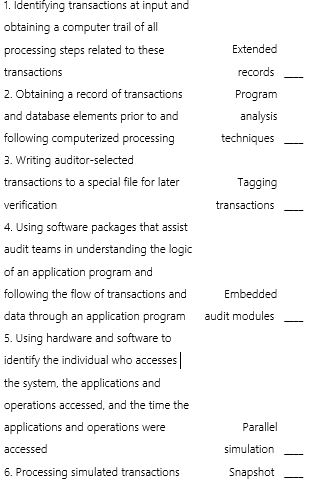

(Essay)
4.8/5  (41)
(41)
Which of the following is true with respect to fraud risk factors in a computerized environment?
(Multiple Choice)
5.0/5  (41)
(41)
Auditing _________________________________________________ refers to the actual evaluation of the hardware and programs to determine the reliability of computer operations and test the operating effectiveness of the related controls.
(Short Answer)
4.7/5  (46)
(46)
Controls used in the management of a computer center to minimize the possibility of using an incorrect file or program are
(Multiple Choice)
4.9/5  (42)
(42)
Which of the following is not a category of general controls?
(Multiple Choice)
4.7/5  (34)
(34)
Input controls are one of the major categories of general controls.
(True/False)
4.8/5  (40)
(40)
When processing controls within the computerized processing system may not leave visible evidence that could be inspected by audit teams,the teams should:
(Multiple Choice)
4.8/5  (24)
(24)
Techniques needed to select specific transactions of audit interest for testing would not include
(Multiple Choice)
4.8/5  (33)
(33)
To test the operating effectiveness of computer controls,audit teams can use each of the following methods except
(Multiple Choice)
4.8/5  (29)
(29)
The major phases in the audit team's study of internal control are the same in a computerized processing environment as those in a manual processing environment.
(True/False)
4.9/5  (43)
(43)
Which of the following is not true with respect to the test data approach for evaluating computer controls?
(Multiple Choice)
4.7/5  (27)
(27)
The most important preventive controls for computer fraud are those that limit access to computers.
(True/False)
5.0/5  (36)
(36)
After obtaining a preliminary understanding of a client's computer controls,audit teams may decide not to perform tests of controls.Which of the following would not be a valid reason for choosing to omit tests of controls?
(Multiple Choice)
4.9/5  (36)
(36)
Which of the following input controls would not be effective in identifying the erroneous input of numeric fields in a transaction?
(Multiple Choice)
4.9/5  (40)
(40)
Showing 61 - 80 of 118
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)