Exam 7: Controlling Information Systems: Introduction to Enterprise Risk Management and Internal Control
Exam 1: Introduction to Accounting Information Systems115 Questions
Exam 2: Enterprise Systems140 Questions
Exam 3: Electronic Business E-Business Systems113 Questions
Exam 4: Documenting Information Systems108 Questions
Exam 5: Database Management Systems180 Questions
Exam 6: Relational Databases and Sql93 Questions
Exam 7: Controlling Information Systems: Introduction to Enterprise Risk Management and Internal Control161 Questions
Exam 8: Controlling Information Systems: Introduction to Pervasive Controls157 Questions
Exam 9: Controlling Information Systems: Business Process and Application Controls126 Questions
Exam 10: The Order Entrysales Oes Process128 Questions
Exam 11: The Billingaccounts Receivable Cash Receipts Barcr Process134 Questions
Exam 12: The Purchasing Process131 Questions
Exam 13: Accounts Payablecash Disbursements Apcd Process104 Questions
Exam 14: The Human Resources Process HR Management and Payroll Processes118 Questions
Exam 15: Integrated Production Processes IPP106 Questions
Exam 16: General Ledger and Business Reporting Glbr Process78 Questions
Exam 17: Acquiring and Implementing Accounting Information Systems206 Questions
Select questions type
Fraud is the possibility that an event or action will cause an organization to fail to meet its objectives (or goals).
(True/False)
4.9/5  (29)
(29)
Which of the following statements regarding internal controls systems is false?
(Multiple Choice)
4.9/5  (40)
(40)
The section of Sarbanes Oxley that provides for fines and imprisonment of up to 20 years to individuals who corruptly alter, destroy, mutilate, or conceal documents with the intent to impair the document's integrity or availability for use in an official proceeding, or to otherwise obstruct, influence or impede any official proceeding is ____________________________________________.
(Essay)
4.7/5  (42)
(42)
The CFO of Exeter Corporation is very uncomfortable with its current risk exposure related to the possibility of business disruptions.Specifically, Exeter is heavily involved with e-business and its internal information systems are tightly interlinked with its key customers' systems.The CFO has estimated that every hour of system downtime will cost the company about $5,000 in sales.The CFO and CIO have further estimated that if the system were to fail, the average downtime would be about 2 hours per incident.The have anticipated (assume with 100% annual probability) that Exeter will likely experience 10 downtime incidents in a given year due to internal computer system problems, and another 10 incidents per year due to external problems; specifically system failures with the Internet service provider (ISP).Currently, Exeter pays an annualized cost of $25,000 for redundant computer and communication systems, and another $25,000 for Internet service provider (ISP) support just to keep total expected number of incidents to 20 per year.Required:
a.Given the information provided thus far, how much ($) is the company's current expected gross risk?
b.A further preventative control would be to purchase and maintain more redundant computers and communication lines where possible, at an annualized cost of $30,000, which would reduce the expected number of downtimes per year to 5 per year due to internal computer system problems.What would the dollar amount of Exeter's current residual expected risk at this point?
(Essay)
4.7/5  (24)
(24)
The control goal of ensure input ____________________ requires that all valid objects or events are captured and entered into the computer.
(Short Answer)
4.8/5  (38)
(38)
A computer abuse technique called a back door involves a programmer's inserting special code or passwords in a computer program that will allow the programmer to bypass the security features of the program.
(True/False)
4.9/5  (41)
(41)
Salami slicing is program code that can attach itself to other programs (i.e., "infect" those programs), that can reproduce itself, and that operates to alter the programs or to destroy data.
(True/False)
4.7/5  (37)
(37)
A computer abuse technique called a(n) _________________________ involves a programmer's inserting special code or passwords in a computer program that will allow the programmer to bypass the security features of the program.
(Short Answer)
4.8/5  (46)
(46)
Assuring that cash collections recorded in the cash receipts event data are credited to the right customer in the accounts receivable master data addresses the control goal of:
(Multiple Choice)
4.9/5  (47)
(47)
Ethical behavior and management integrity are products of the corporate culture.
(True/False)
4.8/5  (35)
(35)
A corrective control plan is designed to discover problems that have occurred.
(True/False)
5.0/5  (46)
(46)
The control goal of input accuracy is concerned with the correctness of the transaction data that are entered into a system.
(True/False)
4.9/5  (37)
(37)
Failing to record a customer's order for the purchase of inventory violates the information system control goal of:
(Multiple Choice)
4.7/5  (43)
(43)
____________________ is the possibility that an event will occur.
(Short Answer)
5.0/5  (41)
(41)
SAS No.99 emphasizes auditors should brainstorm fraud risks, increase professional skepticism, use unpredictable audit test patterns, and detect management override of internal controls
(True/False)
4.8/5  (31)
(31)
The section of Sarbanes Oxley that sets forth criminal penalties applicable to CEOs and CFOs of up to $5 million and up to 20 years imprisonment if they knowingly or willfully certify false or misleading periodic reports is _______________________________________________________.
(Essay)
4.8/5  (41)
(41)
The control environment reflects the organization's general awareness and commitment to the importance of control throughout the organization.
(True/False)
4.8/5  (40)
(40)
The section of Sarbanes Oxley that establishes an independent board to oversee public company audits is _________________________________________________________________.
(Essay)
4.7/5  (29)
(29)
Listed below are 13 specific fraud examples taken from some well-known fraud cases: MiniScribe, ZZZZ Best Carpet Cleaning, Lesley Fay, and Equity Funding.Required:
For each fraud example, enter a letter corresponding to which information control goal was initially violated--Validity, Completeness, or Accuracy.Some examples might involve more than one violation.NOTE: When we say initially, we mean what control goal failure led to this example, not what is the present condition.For example, master data might contain information that is inaccurate, but it might have been an inaccurate input that initially caused the data to be inaccurate.Fraud Examples:
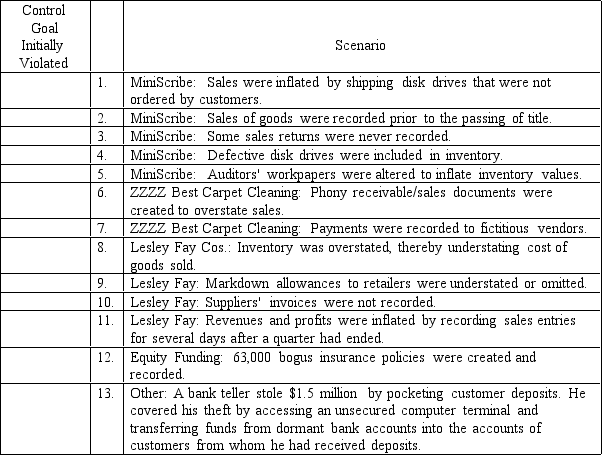
(Essay)
4.8/5  (37)
(37)
Showing 101 - 120 of 161
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)