Deck 30: Computer Safety and Ethics
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Match between columns
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/46
Play
Full screen (f)
Deck 30: Computer Safety and Ethics
1
Surge protectors help protect computers from ____.
A) hackers
B) sniffers
C) power spikes
D) hard disk crashes
A) hackers
B) sniffers
C) power spikes
D) hard disk crashes
C
2
Before providing personal information or credit card information on an e-commerce site, first verify that the site is secure.
True
3
A software firewall is more secure and easier to monitor than a hardware firewall.
False
4
It is the responsibility of a company or individual to protect their data.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
5
A(n) public key deciphers the encrypted information in a transmission.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
6
When communicating on a forum, blog, or social network or other similar Internet-related sites, use a(n) alias to protect your privacy.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
7
Computer phishing involves invading someone else's computer, usually for personal gain or the satisfaction of a security system.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
8
Data that has been saved cannot be lost or corrupted by equipment failure, software viruses or hackers, fire or flood, or power irregularities.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
9
One easy way to avoid data loss is to ____.
A) plug the computer into a grounded outlet
B) save frequently
C) install a firewall
D) turn on some form of encryption
A) plug the computer into a grounded outlet
B) save frequently
C) install a firewall
D) turn on some form of encryption

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
10
It is estimated that ____ causes millions of dollars of damage each year, along with the theft of important and valuable data.
A) hacking
B) encryption
C) spying
D) eavesdropping
A) hacking
B) encryption
C) spying
D) eavesdropping

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
11
Sniffer attacks use a script or program to log on to an account using hundreds of words or phrases stored in a dictionary file.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
12
Some spyware disguises itself as antispyware to gain access to your system.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
13
Eavesdropping software can be downloaded free from the Internet and used by a hacker to access an unsecured wireless connection.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
14
If a network is large, a software firewall that controls the computers from one point should be implemented.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
15
Old computer hardware such as monitors can create an environmental hazard if disposed of improperly.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
16
Using a notebook computer introduces risks not associated with desktop computers.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
17
What can result from making too many of the same motions over a long period of time?
A) Browser hijacking
B) Brute force attacks
C) Repetitive strain injury
D) Relaxed eye muscles
A) Browser hijacking
B) Brute force attacks
C) Repetitive strain injury
D) Relaxed eye muscles

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
18
What action might obstruct the air vents in your notebook computer and cause it to overheat?
A) Leaving it in the same position on the desk for too long
B) Using a cooling pad
C) Setting it directly on your lap
D) Plugging it into a grounded outlet
A) Leaving it in the same position on the desk for too long
B) Using a cooling pad
C) Setting it directly on your lap
D) Plugging it into a grounded outlet

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
19
If you work for a company that provides e-mail services, the information that you send is your property.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
20
Firewalls help prevent employees from tampering with or deleting data.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
21
The goal of ____ is to collect information about the user, the user's browsing habits, and other personal information.
A) a sniffer
B) worms
C) a virus
D) spyware
A) a sniffer
B) worms
C) a virus
D) spyware

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
22
TSL and SSL technology enables ____.
A) data to be backed up securely
B) companies to monitor unauthorized computer activity
C) system administrators to restrict access to files
D) sensitive information to be encrypted
A) data to be backed up securely
B) companies to monitor unauthorized computer activity
C) system administrators to restrict access to files
D) sensitive information to be encrypted

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
23
Case 30-2 Molly has just purchased a router and is setting up a wireless network in her home office. She wants to secure it properly. If Molly does not properly secure her wireless network connection, what could happen if her neighbor uses her broadband connection?
A) Her Internet access could be slower
B) She could be charged additional costs
C) She could be held responsible for any illegal activity
D) Any of the above
A) Her Internet access could be slower
B) She could be charged additional costs
C) She could be held responsible for any illegal activity
D) Any of the above

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
24
Case 30-2 Molly has just purchased a router and is setting up a wireless network in her home office. She wants to secure it properly. What is the first step Molly should take when setting up her wireless network?
A) Download eavesdropping software
B) Change the default password
C) Turn off the default encryption
D) Configure a hardware firewall
A) Download eavesdropping software
B) Change the default password
C) Turn off the default encryption
D) Configure a hardware firewall

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
25
FIGURE 30-1 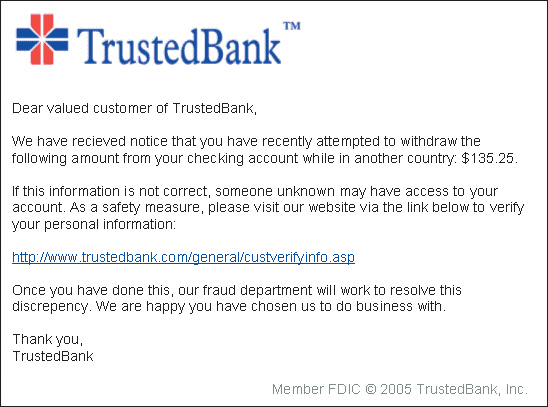 The message in Figure 30-1 above shows an example of ____.
The message in Figure 30-1 above shows an example of ____.
A) hacking
B) phishing
C) sniffing
D) browser hijacking
 The message in Figure 30-1 above shows an example of ____.
The message in Figure 30-1 above shows an example of ____.A) hacking
B) phishing
C) sniffing
D) browser hijacking

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
26
Case 30-1 Nelson is a graphic designer who works long hours on his computer. He tries to take precautions to avoid chronic physical maladies such as eyestrain, back problems, and repetitive strain injuries. What kind of furniture should Nelson use to help adapt his equipment and his workplace to fit himself?
A) Expensive
B) Light-weight
C) Ergonomic
D) Soft
A) Expensive
B) Light-weight
C) Ergonomic
D) Soft

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
27
A(n) ____________________ is a program that hackers use to capture IDs and passwords on a network.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
28
Which of the following would be considered the strongest password?
A) JeR3My
B) tHund3r$t0rM
C) SouTHWeST!
D) #1fusion
A) JeR3My
B) tHund3r$t0rM
C) SouTHWeST!
D) #1fusion

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
29
External hard drives can be used to help ____.
A) prevent computer hacking
B) avoid data loss
C) safeguard against software threats
D) protect your system against spyware
A) prevent computer hacking
B) avoid data loss
C) safeguard against software threats
D) protect your system against spyware

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
30
If non-copyrighted information is published on a Web site, ____.
A) it is true
B) it cannot be copied and used as your own
C) it is false
D) the author is relieved of any responsibility
A) it is true
B) it cannot be copied and used as your own
C) it is false
D) the author is relieved of any responsibility

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
31
Case 30-1 Nelson is a graphic designer who works long hours on his computer. He tries to take precautions to avoid chronic physical maladies such as eyestrain, back problems, and repetitive strain injuries. What can Nelson do to help avoid or minimize eyestrain?
A) Use a low-resolution monitor to increase visibility
B) Stay in the same position so his eyes become more comfortable
C) Avoid using extra lighting so the monitor is more easily visible
D) Take regular breaks to allow the eye muscles to relax
A) Use a low-resolution monitor to increase visibility
B) Stay in the same position so his eyes become more comfortable
C) Avoid using extra lighting so the monitor is more easily visible
D) Take regular breaks to allow the eye muscles to relax

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
32
Any information stored on a computer in an educational facility is the property of the ____.
A) person using the computer
B) school
C) person who created the information
D) none of the above
A) person using the computer
B) school
C) person who created the information
D) none of the above

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
33
When is it possible for the information that you submit on the Internet to be gathered by many persons and used for various situations?
A) When you use a secure site
B) Only if you don't have a firewall
C) When the data is encrypted
D) Any time
A) When you use a secure site
B) Only if you don't have a firewall
C) When the data is encrypted
D) Any time

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
34
To make sure your e-commerce transactions are secure and to protect your private information, you should ____.
A) use a secure browser
B) check privacy policies
C) keep personal information private
D) all of the above
A) use a secure browser
B) check privacy policies
C) keep personal information private
D) all of the above

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
35
Which of the following is not true about spyware?
A) It tracks your Web habits
B) It can take over control of your computer
C) It has redeeming qualities
D) It can direct you to Web sites you have not chosen to visit
A) It tracks your Web habits
B) It can take over control of your computer
C) It has redeeming qualities
D) It can direct you to Web sites you have not chosen to visit

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
36
Often, you can inadvertently run a virus program by ____.
A) installing a security update
B) backing up data
C) opening an e-mail message or attachment
D) using a surge protector
A) installing a security update
B) backing up data
C) opening an e-mail message or attachment
D) using a surge protector

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
37
What is another term for brute force attacks?
A) Browser hijacking
B) Spyware attacks
C) Keylogger attacks
D) Dictionary attacks
A) Browser hijacking
B) Spyware attacks
C) Keylogger attacks
D) Dictionary attacks

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
38
When you use a computer in a public place, you should ____.
A) verify that you have logged off
B) install antivirus software
C) use cookies to track your computer use
D) use a code name
A) verify that you have logged off
B) install antivirus software
C) use cookies to track your computer use
D) use a code name

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
39
FIGURE 30-2 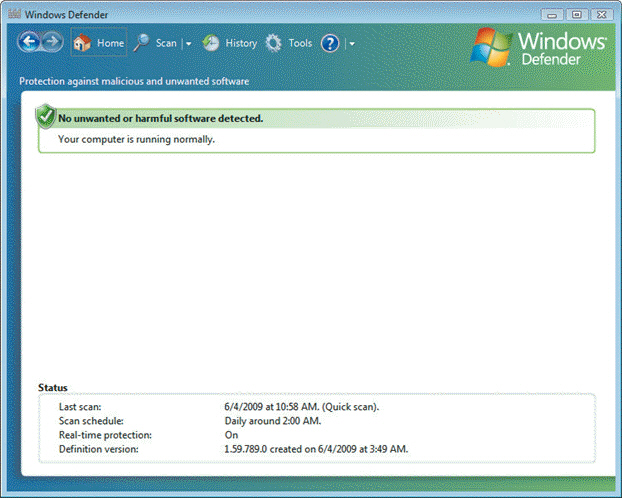 You could use the program shown in Figure 30-2 above to ____.
You could use the program shown in Figure 30-2 above to ____.
A) protect your system against spyware
B) back up files
C) configure a hardware firewall
D) password protect your wireless network
 You could use the program shown in Figure 30-2 above to ____.
You could use the program shown in Figure 30-2 above to ____.A) protect your system against spyware
B) back up files
C) configure a hardware firewall
D) password protect your wireless network

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
40
What should you do before donating a computer?
A) Remove the antivirus software
B) Password-protect the operating system
C) Delete data from the hard drive
D) Turn off any encryption technologies
A) Remove the antivirus software
B) Password-protect the operating system
C) Delete data from the hard drive
D) Turn off any encryption technologies

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
41
A(n) ____________________ is a malicious program that records keystrokes.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
42
Match between columns

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
43
Why are passwords important? How do you maintain passwords and keep them secure? How do you create a strong password?

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
44
____________________ are small files that are created when you visit a Web site and are stored on your computer, then accessed again the next time you visit the same site.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
45
A(n) ____________________ encrypts the information in a data transmission.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck
46
Hackers often use spyware to control your browser, a practice called ____________________.

Unlock Deck
Unlock for access to all 46 flashcards in this deck.
Unlock Deck
k this deck


