Exam 30: Computer Safety and Ethics
Exam 1: Computers and Computer Systems46 Questions
Exam 2: Input, Output, and Processing46 Questions
Exam 3: Computer Protection46 Questions
Exam 4: Computer Maintenance46 Questions
Exam 5: Computer-Related Issues46 Questions
Exam 6: Software and Hardware Interaction46 Questions
Exam 7: Software Fundamentals46 Questions
Exam 8: Operating Systems46 Questions
Exam 9: Windows Management46 Questions
Exam 10: Operating System Customization46 Questions
Exam 11: Exploring Microsoft Office 200746 Questions
Exam 12: Getting Started With Word Essentials46 Questions
Exam 13: Editing and Formatting Documents46 Questions
Exam 14: Sharing Documents46 Questions
Exam 15: Working With Tables46 Questions
Exam 16: Enhancing Documents46 Questions
Exam 17: Getting Started With Excel Essentials46 Questions
Exam 18: Organizing and Enhancing Worksheets46 Questions
Exam 19: Creating Formulas and Charting Data46 Questions
Exam 20: Getting Started With Powerpoint Essentials46 Questions
Exam 21: Enhancing Presentations With Multimedia Effects46 Questions
Exam 22: Getting Started With Access Essentials46 Questions
Exam 23: Managing and Reporting Database Information46 Questions
Exam 24: Network Fundamentals46 Questions
Exam 25: Communication Services46 Questions
Exam 26: Communications and Collaboration46 Questions
Exam 27: Using the Internet and the World Wide Web46 Questions
Exam 28: Web Content46 Questions
Exam 29: Technology and Society46 Questions
Exam 30: Computer Safety and Ethics46 Questions
Select questions type
It is estimated that ____ causes millions of dollars of damage each year, along with the theft of important and valuable data.
Free
(Multiple Choice)
4.8/5  (34)
(34)
Correct Answer:
A
Which of the following is not true about spyware?
Free
(Multiple Choice)
4.7/5  (30)
(30)
Correct Answer:
C
A(n) ____________________ is a malicious program that records keystrokes.
Free
(Short Answer)
4.8/5  (25)
(25)
Correct Answer:
keylogger
Firewalls help prevent employees from tampering with or deleting data.
(True/False)
4.8/5  (32)
(32)
Case 30-2 Molly has just purchased a router and is setting up a wireless network in her home office. She wants to secure it properly. What is the first step Molly should take when setting up her wireless network?
(Multiple Choice)
4.8/5  (31)
(31)
Data that has been saved cannot be lost or corrupted by equipment failure, software viruses or hackers, fire or flood, or power irregularities.
(True/False)
4.8/5  (27)
(27)
If non-copyrighted information is published on a Web site, ____.
(Multiple Choice)
4.8/5  (41)
(41)
Case 30-1 Nelson is a graphic designer who works long hours on his computer. He tries to take precautions to avoid chronic physical maladies such as eyestrain, back problems, and repetitive strain injuries. What can Nelson do to help avoid or minimize eyestrain?
(Multiple Choice)
4.8/5  (35)
(35)
A(n) ____________________ is a program that hackers use to capture IDs and passwords on a network.
(Short Answer)
5.0/5  (31)
(31)
If you work for a company that provides e-mail services, the information that you send is your property.
(True/False)
4.8/5  (33)
(33)
A(n) ____________________ encrypts the information in a data transmission.
(Short Answer)
4.8/5  (35)
(35)
Old computer hardware such as monitors can create an environmental hazard if disposed of improperly.
(True/False)
4.9/5  (30)
(30)
When communicating on a forum, blog, or social network or other similar Internet-related sites, use a(n) alias to protect your privacy.
(True/False)
4.8/5  (32)
(32)
Sniffer attacks use a script or program to log on to an account using hundreds of words or phrases stored in a dictionary file.
(True/False)
5.0/5  (28)
(28)
FIGURE 30-1 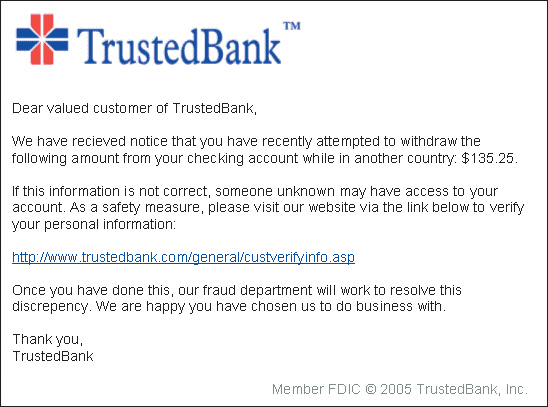 The message in Figure 30-1 above shows an example of ____.
The message in Figure 30-1 above shows an example of ____.
(Multiple Choice)
4.8/5  (36)
(36)
Any information stored on a computer in an educational facility is the property of the ____.
(Multiple Choice)
4.9/5  (30)
(30)
If a network is large, a software firewall that controls the computers from one point should be implemented.
(True/False)
4.9/5  (38)
(38)
Showing 1 - 20 of 46
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)