Deck 5: Outlook 2007 Unit A: Getting Started With E-Mail
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Match between columns
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/65
Play
Full screen (f)
Deck 5: Outlook 2007 Unit A: Getting Started With E-Mail
1
Names entered in the Bcc text box of a message window are not visible to other message recipients.
True
2
Message headers only provide information about the sender and subject of a message.
False
3
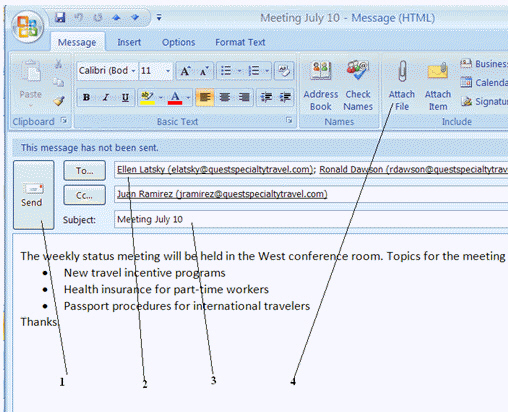 You click the button labeled 1 in the Figure above when you are finished writing and addressing your e-mail message.
You click the button labeled 1 in the Figure above when you are finished writing and addressing your e-mail message.True
4
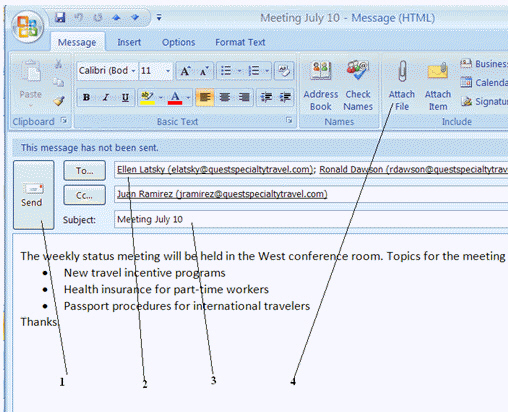 You click the item labeled 4 in the Figure to attach a file to an e-mail message.
You click the item labeled 4 in the Figure to attach a file to an e-mail message.
Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
5
The benefits of using e-mail include all the following, except ____.
A) You can send confidential information and files without worrying about privacy issues.
B) You can communicate with several people at once.
C) You can communicate from a remote place.
D) You will have a record of messages sent.
A) You can send confidential information and files without worrying about privacy issues.
B) You can communicate with several people at once.
C) You can communicate from a remote place.
D) You will have a record of messages sent.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
6
Some e-mail systems will not be able to handle sending a large file attached to an e-mail message.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
7
E-mail software lets you send and receive electronic messages over a network.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
8
Possible ways to connect to the Internet include a ____.
A) Cable modem
B) Telephone modem
C) DSL
D) All of the above
A) Cable modem
B) Telephone modem
C) DSL
D) All of the above

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
9
You can assume that e-mail messages you send at your office are private.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
10
Messages that have been sent remain in the Inbox until you delete them.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
11
The Outbox contains all e-mail messages that you want to throw out.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
12
Cc stands for courtesy copy.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
13
The Inbox folder stores all incoming e-mail messages.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
14
When you reply to a message, you must reply to everyone that the original message was sent to.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
15
When you reply to a message, the subject line remains the same and is preceded by "RE:".

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
16
Which of the following programs is an integrated desktop information management program?
A) Microsoft Internet Explorer
B) Microsoft Office 2007
C) Microsoft Information Express
D) Microsoft Outlook 2007
A) Microsoft Internet Explorer
B) Microsoft Office 2007
C) Microsoft Information Express
D) Microsoft Outlook 2007

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
17
The first part of an e-mail address is the ____.
A) domain name
B) service provider
C) username
D) address
A) domain name
B) service provider
C) username
D) address

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
18
E-mail uses store-and-forward technology: messages are stored for a limited amount of time on a server before they are forwarded to the recipients computer.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
19
E-mail software uses store and ____ technology; messages are stored on a server until the recipient logs onto a computer and requests the messages.
A) Internet
B) forward
C) retain
D) None of the above
A) Internet
B) forward
C) retain
D) None of the above

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
20
A network is a(n) ____.
A) Group of computers connected to each other to share information and resources
B) Online service provider
C) Record of communications
D) Electronic mail program
A) Group of computers connected to each other to share information and resources
B) Online service provider
C) Record of communications
D) Electronic mail program

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
21
To automatically send a response back to the original sender of a message you receive, you can use the ____.
A) Reply command
B) Next command
C) Respond command
D) Send command
A) Reply command
B) Next command
C) Respond command
D) Send command

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
22
The window in which you can preview messages prior to opening them is the ____.
A) Preview or Reading pane
B) Status pane
C) Message Pane
D) Navigation Pane
A) Preview or Reading pane
B) Status pane
C) Message Pane
D) Navigation Pane

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
23
Which of the following is a valid Web-based e-mail address?
A) username.hotmail.com
B) username@hotmail.com
C) username@myschool.col
D) username$myschool.edu
A) username.hotmail.com
B) username@hotmail.com
C) username@myschool.col
D) username$myschool.edu

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
24
An example of a file attached to an e-mail message that may be too large for an e-mail system to handle is a ____.
A) Spreadsheet
B) Movie
C) Text file
D) None of the above
A) Spreadsheet
B) Movie
C) Text file
D) None of the above

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
25
Junk e-mail, or ____, is unwanted mail that arrives from unsolicited sources.
A) spam
B) phish
C) trash
D) junk
A) spam
B) phish
C) trash
D) junk

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
26
When composing and sending an e-mail message, you can specify options such as ____.
A) specifying a future delivery date
B) assigning the level of importance
C) adding voting buttons for recipients
D) All of the above
A) specifying a future delivery date
B) assigning the level of importance
C) adding voting buttons for recipients
D) All of the above

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
27
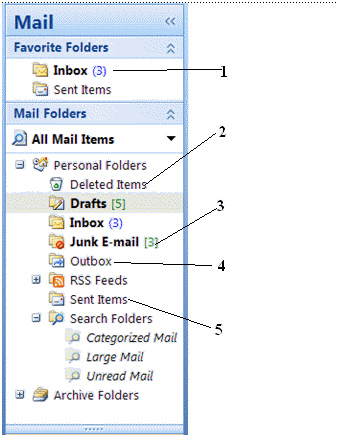 In the figure above, the folder that stores the mail before it is sent out is identified by item number ____.
In the figure above, the folder that stores the mail before it is sent out is identified by item number ____.A) 1
B) 2
C) 3
D) 4

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
28
A benefit of using electronic mail is that it allows you to ____.
A) Send large amounts of information
B) Communicate with several people at once
C) Communicate from a remote place
D) All of the above
A) Send large amounts of information
B) Communicate with several people at once
C) Communicate from a remote place
D) All of the above

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
29
To send a message so that the recipients cannot see who else received the message you enter the addresses in the ____ text box.
A) CC
B) BCC
C) To
D) Subject
A) CC
B) BCC
C) To
D) Subject

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
30
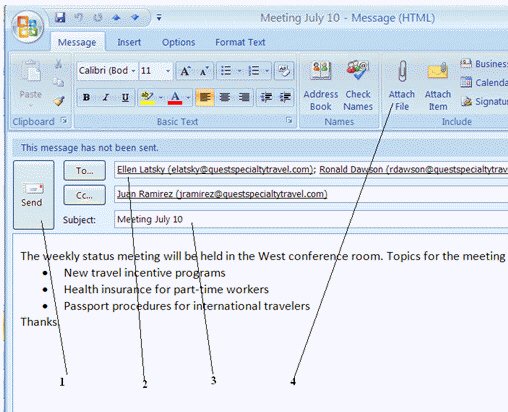 The text identified by Item 3 in the figure above, is ____.
The text identified by Item 3 in the figure above, is ____.A) A statement that indicates the purpose of the message
B) An e-mail address
C) A person who will receive the message but not be identified to the other recipients
D) None of the above

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
31
To forward a message that you have received to someone else, you ____.
A) Click Send, Reply, then Forward
B) Click Send, then Forward
C) Click Forward, then Send
D) Click Reply, then Forward
A) Click Send, Reply, then Forward
B) Click Send, then Forward
C) Click Forward, then Send
D) Click Reply, then Forward

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
32
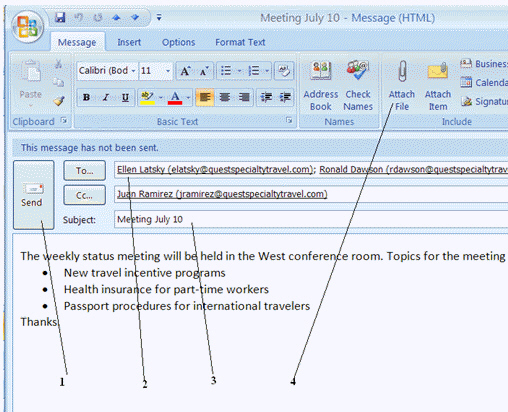 Item 2 in the figure above shows the ____.
Item 2 in the figure above shows the ____.A) Carbon copy recipients
B) Color copy icon
C) Recipients
D) Address book

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
33
The letters FW in the subject area of a message indicate that the message ____.
A) Is a forwarded message
B) Is a reply message
C) Has an attachment
D) Was printed
A) Is a forwarded message
B) Is a reply message
C) Has an attachment
D) Was printed

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
34
If the subject line of a message is preceded by "RE:" it indicates that the message ____.
A) was forwarded
B) was read
C) is a reply
D) is recent
A) was forwarded
B) was read
C) is a reply
D) is recent

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
35
A distribution list is a ____.
A) List of all the people to whom you send messages
B) Collection of contacts to whom you regularly send the same messages
C) List of all the people who have sent you messages
D) List of all the subjects of the messages you have sent
A) List of all the people to whom you send messages
B) Collection of contacts to whom you regularly send the same messages
C) List of all the people who have sent you messages
D) List of all the subjects of the messages you have sent

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
36
When composing e-mail messages it is not appropriate to use all capital letters because this is the e-mail equivalent of ____.
A) Laughing
B) Whispering
C) Shouting
D) Arguing
A) Laughing
B) Whispering
C) Shouting
D) Arguing

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
37
The message ____ contains basic information about the message, such as the recipients, date and time stamp, and the subject.
A) header
B) body
C) composition
D) address
A) header
B) body
C) composition
D) address

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
38
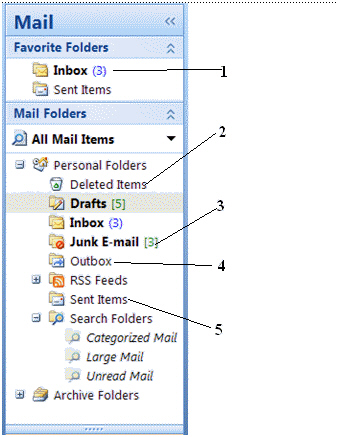 In the figure above, the number of unread messages that have arrived is ____.
In the figure above, the number of unread messages that have arrived is ____.A) 5
B) 1
C) 3
D) 0

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
39
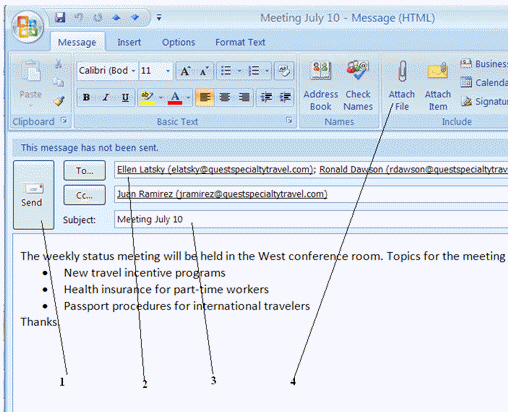 Item 4 in the figure above is used to ____.
Item 4 in the figure above is used to ____.A) Print an e-mail message
B) Attach a file to an e-mail message
C) Create a distribution list
D) Place emphasis on an e-mail message

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
40
One advantage of using an e-mail address book is that ____.
A) It stores the mailing addresses of the people you want to send messages to
B) It reduces errors in entering e-mail addresses
C) It tracks files that you sent to your contacts
D) It updates new information automatically
A) It stores the mailing addresses of the people you want to send messages to
B) It reduces errors in entering e-mail addresses
C) It tracks files that you sent to your contacts
D) It updates new information automatically

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
41
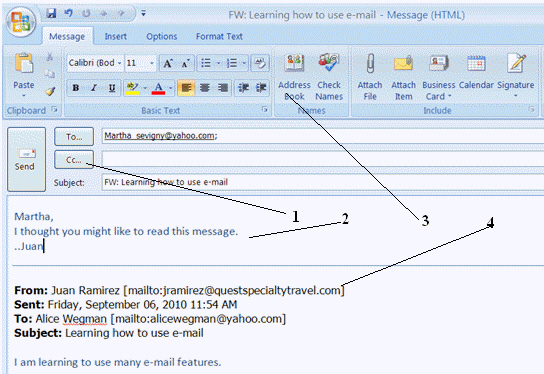 In the figure above, Item 2 is the ____________________ of the message.
In the figure above, Item 2 is the ____________________ of the message.
Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
42
An e-mail message ____________________ identifies the sender of the message, the subject, the date and time the message was received, and the size of the message.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
43
A(n) ____________________ is the hardware and software that makes it possible for two or more computers to share information and resources.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
44
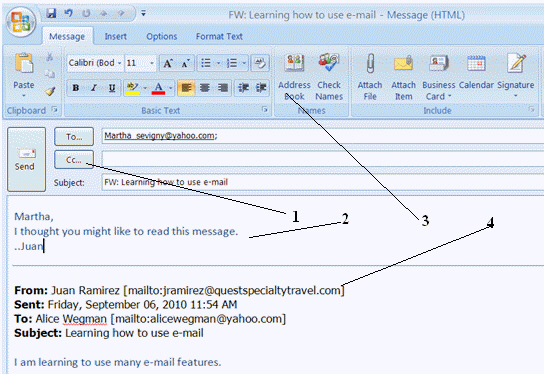 Clicking Item 3 in the figure above will open the ____________________.
Clicking Item 3 in the figure above will open the ____________________.
Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
45
The ____________________ lists the message headers for the e-mail you have received.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
46
Discuss e-mail and networks and list some of the advantages of using e-mail.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
47
What is an e-mail distribution list and what are the benefits of using one?

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
48
Often, when you attach a file to an e-mail message an icon next to each filename indicates the ____ of file that is being attached.
A) speed
B) size
C) type
D) name
A) speed
B) size
C) type
D) name

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
49
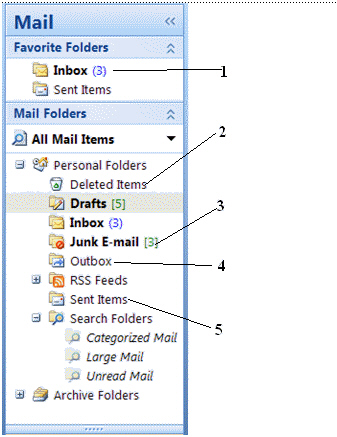 When you remove a message from any folder, it is placed in the folder labeled item number ____ in the figure.
When you remove a message from any folder, it is placed in the folder labeled item number ____ in the figure.A) 1
B) 2
C) 3
D) 4

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
50
Using all capital letters in an e-mail message is the equivalent of ____________________.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
51
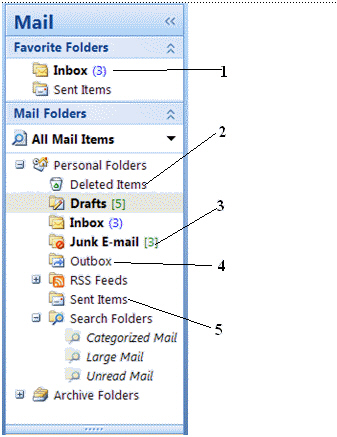 If spam were arrive to your e-mail address, it would most likely go into the folder labeled item number ____ in the figure.
If spam were arrive to your e-mail address, it would most likely go into the folder labeled item number ____ in the figure.A) 1
B) 2
C) 3
D) 4

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
52
Adding a(n) ____________________ to an e-mail Address book saves you time and the risk of error when you have to retype the e-mail address each time.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
53
When composing e-mail messages, why is it important to take extra care in what you say and how you say it?

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
54
A(n) ____________________ is a collection of contacts to whom you regularly send the same messages.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
55
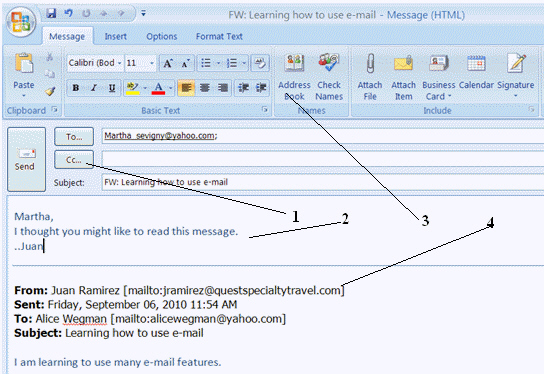 In the figure above, Martha Sevigny is the ____________________ of the e-mail message.
In the figure above, Martha Sevigny is the ____________________ of the e-mail message.
Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
56
The ____________________ Pane can be used to read and scroll through messages without opening them in a new window.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
57
If you want to send a person an image file, you can attach it to the message.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
58
To reply to everyone who has received the same message, click the ____________________ button.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
59
Most e-mail programs allow you to set up an ____ response if you are not going to be able to get your e-mail for a specified period of time.
A) after delay
B) automatic
C) addressable
D) arbitrary
A) after delay
B) automatic
C) addressable
D) arbitrary

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
60
When you forward a message, the subject line remains the same and is preceded by " CC :"

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
61
Match between columns

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
62
Jennifer Westin works as an administrative assistant at the local bank. She is setting up her e-mail folders. It is important that she learn how to sort and organize her mail because she will be handling all the incoming mail for the branch. Which folder will all mail that she receives first arrive in?

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
63
Jennifer Westin works as an administrative assistant at the local bank. She is setting up her e-mail folders. It is important that she learn how to sort and organize her mail because she will be handling all the incoming mail for the branch. If Jennifer wants to see all the mail that arrived last week, what is the best way for her to sort her mail?

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
64
If you click the flag icon next to the message, it is marked by default with a red Quick envelope .

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck
65
Jennifer Westin works as an administrative assistant at the local bank. She is setting up her e-mail folders. It is important that she learn how to sort and organize her mail because she will be handling all the incoming mail for the branch. Jennifer will be sending many people the same messages. The best way for her to do this is to set up a ____.

Unlock Deck
Unlock for access to all 65 flashcards in this deck.
Unlock Deck
k this deck


