Deck 8: Security Issues and Ethics in Education
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/103
Play
Full screen (f)
Deck 8: Security Issues and Ethics in Education
1
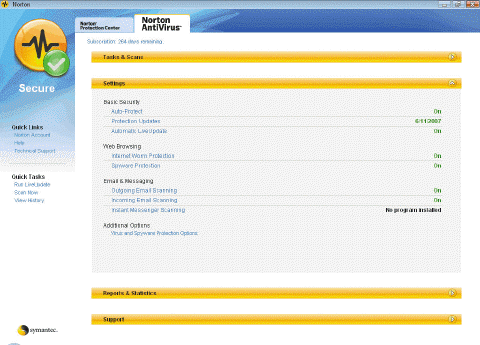 A(n) ____ disc is normally a CD that contains an uninfected copy of key operating system commands and startup information that enables the computer to restart correctly; this kind of disc may be required in some circumstances by the program in the accompanying figure.
A(n) ____ disc is normally a CD that contains an uninfected copy of key operating system commands and startup information that enables the computer to restart correctly; this kind of disc may be required in some circumstances by the program in the accompanying figure.A) antivirus
B) rescue
C) fix-it
D) virus fix
B
2
____ is the use of a computer system without permission.
A) Access controls
B) Unauthorized use
C) Unauthorized access
D) Biometric trespass
A) Access controls
B) Unauthorized use
C) Unauthorized access
D) Biometric trespass
C
3
A ____ virus replaces the program that is used to start the computer system with a modified, infected version of the startup program.
A) boot sector
B) file
C) Trojan horse
D) macro
A) boot sector
B) file
C) Trojan horse
D) macro
A
4
The most common type of software theft is ____.
A) stealing a CD
B) stealing a flash drive
C) software piracy
D) all of the above
A) stealing a CD
B) stealing a flash drive
C) software piracy
D) all of the above

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
5
A computer security risk is defined as any event or action that could cause loss of, or damage to, ____.
A) computer equipment
B) software
C) data and information
D) all of the above
A) computer equipment
B) software
C) data and information
D) all of the above

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
6
____ is the use of a computer or data for unapproved or possibly illegal activities.
A) Access control
B) Unauthorized use
C) Unauthorized access
D) Biometic trespass
A) Access control
B) Unauthorized use
C) Unauthorized access
D) Biometic trespass

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
7
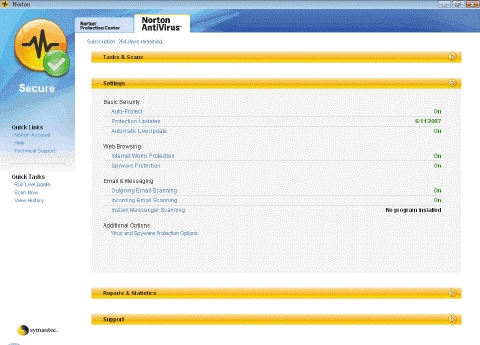 In addition to detecting viruses and inoculating against them, antivirus programs like the one in the accompanying figure can ____.
In addition to detecting viruses and inoculating against them, antivirus programs like the one in the accompanying figure can ____.A) repair infected programs and files
B) protect against power surges
C) protect against unauthorized access
D) all of the above

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
8
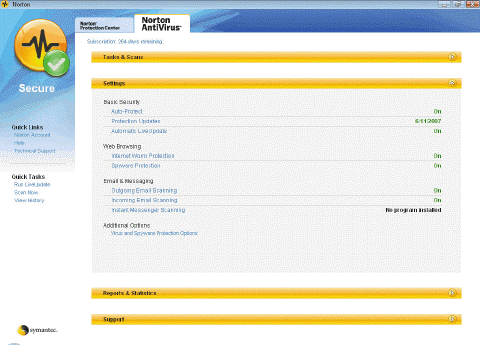 Antivirus programs like the one in the accompanying figure also are called ____.
Antivirus programs like the one in the accompanying figure also are called ____.A) vaccines
B) computer medicine
C) virus remedy
D) virus fixers

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
9
A ____ is a program that is activated when a certain condition is detected.
A) logic bomb
B) worm
C) time bomb
D) macro virus
A) logic bomb
B) worm
C) time bomb
D) macro virus

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
10
A security system consisting of hardware and/or software that prevents unauthorized access to data and information on a network is called a(n) ____.
A) proxy
B) firewall
C) blocker
D) defender
A) proxy
B) firewall
C) blocker
D) defender

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
11
A ____ is a program that is activated on a specific date.
A) logic bomb
B) worm
C) time bomb
D) macro virus
A) logic bomb
B) worm
C) time bomb
D) macro virus

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
12
Any item that you must carry to gain access to a computer or computer facility is called a(n) ____.
A) proxy object
B) possessed object
C) access object
D) smart object
A) proxy object
B) possessed object
C) access object
D) smart object

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
13
A ____ virus inserts virus code into program files.
A) boot sector
B) file
C) Trojan horse
D) macro
A) boot sector
B) file
C) Trojan horse
D) macro

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
14
All of the following are tips for creating passwords EXCEPT ____.
A) join two words together
B) use a close relative or your child's name
C) choose words from other languages
D) use a combination of letters and numbers
A) join two words together
B) use a close relative or your child's name
C) choose words from other languages
D) use a combination of letters and numbers

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
15
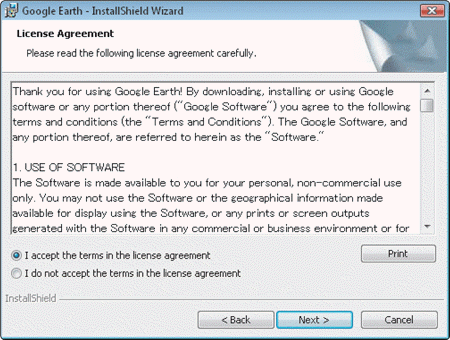 Software licenses like the one in the accompanying figure are agreements that ____.
Software licenses like the one in the accompanying figure are agreements that ____.A) provide specific conditions for use of the software
B) users must accept before using the software
C) outline the rights to use the software
D) all of the above

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
16
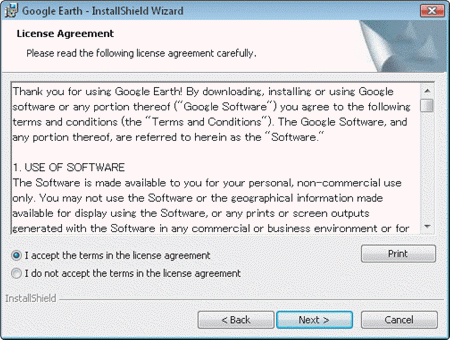 An antipiracy technology designed to verify that software products have been legitimately licensed by licenses like the one in the accompanying figure is called ____.
An antipiracy technology designed to verify that software products have been legitimately licensed by licenses like the one in the accompanying figure is called ____.A) product activation
B) software activation
C) software verification
D) product verification

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
17
A well-known time bomb virus is the ____ virus, which destroys files on March 6.
A) da Vinci
B) Michelangelo
C) Spring Fever
D) Green Caterpillar
A) da Vinci
B) Michelangelo
C) Spring Fever
D) Green Caterpillar

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
18
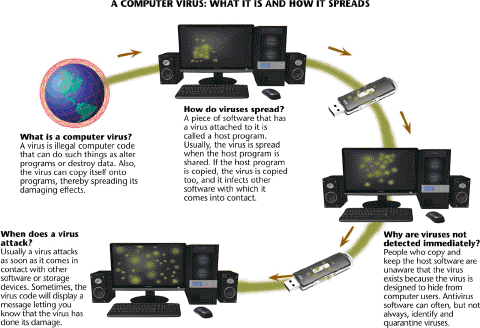 All of the following are true concerning viruses like those described in the accompanying figure EXCEPT ____.
All of the following are true concerning viruses like those described in the accompanying figure EXCEPT ____.A) viruses are potentially damaging computer programs
B) a virus is a segment of a program
C) many viruses are generated by chance
D) damage caused by a virus is called the virus payload

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
19
A ____ virus hides within or is designed to look like a legitimate program.
A) boot sector
B) file
C) Trojan horse
D) macro
A) boot sector
B) file
C) Trojan horse
D) macro

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
20
A ____ virus hides virus code within an application such as a word processing or spreadsheet document.
A) malicious
B) file
C) Trojan horse
D) macro
A) malicious
B) file
C) Trojan horse
D) macro

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
21
____ applies to all creative works and provides certain rights to authors.
A) Codes of conduct
B) Creative Works Act of 1976
C) Copyright
D) Computer ethics
A) Codes of conduct
B) Creative Works Act of 1976
C) Copyright
D) Computer ethics

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
22
A ____ gives an entire region or state the right to install an unlimited number of educational copies of a software program.
A) community/state site license
B) network site license
C) site license
D) single-user license
A) community/state site license
B) network site license
C) site license
D) single-user license

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
23
A(n) ____ is an injury or disorder of the muscles, nerves, tendons, ligaments, and joints.
A) CSB
B) RSB
C) BSC
D) MSD
A) CSB
B) RSB
C) BSC
D) MSD

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
24
A(n) ____ occurs when the incoming electrical power increases significantly above the normal 120 volts.
A) overvoltage
B) blackout
C) brownout
D) undervoltage
A) overvoltage
B) blackout
C) brownout
D) undervoltage

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
25
A(n) ____ is a prolonged undervoltage.
A) overvoltage
B) blackout
C) brownout
D) undervoltage
A) overvoltage
B) blackout
C) brownout
D) undervoltage

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
26
____ is a scam in which a perpetrator sends an official-looking e-mail that attempts to obtain personal and financial information from the recipient.
A) Spam
B) Spim
C) Phishing
D) Split
A) Spam
B) Spim
C) Phishing
D) Split

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
27
____ computing involves reducing the use of electricity and the production of environmental waste while using a computer.
A) Green
B) Environmental
C) Productive
D) Ethical
A) Green
B) Environmental
C) Productive
D) Ethical

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
28
____ prevents your browser from displaying materials from targeted sites or sites that contain certain keywords or phrases.
A) Controlling software
B) Preventing software
C) Filtering software
D) Monitoring software
A) Controlling software
B) Preventing software
C) Filtering software
D) Monitoring software

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
29
Copyright laws ____.
A) protect original materials created by students and teachers posted on the Web
B) apply to all creative works
C) are contained in the Copyright Act of 1976 and its numerous amendments
D) all of the above
A) protect original materials created by students and teachers posted on the Web
B) apply to all creative works
C) are contained in the Copyright Act of 1976 and its numerous amendments
D) all of the above

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
30
____ is a service that blocks e-mail messages from designated sources.
A) E-mail filtering
B) Antispam filtering
C) Electronic filtering
D) Computer filtering
A) E-mail filtering
B) Antispam filtering
C) Electronic filtering
D) Computer filtering

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
31
Surge protectors ____.
A) smooth out minor voltages
B) provide a stable current flow
C) keep overvoltages from damaging computer equipment
D) all of the above
A) smooth out minor voltages
B) provide a stable current flow
C) keep overvoltages from damaging computer equipment
D) all of the above

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
32
A(n) ____ is a complete power failure.
A) overvoltage
B) blackout
C) brownout
D) undervoltage
A) overvoltage
B) blackout
C) brownout
D) undervoltage

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
33
Fair use guidelines allow ____.
A) individuals to make unlimited copies of copyrighted works
B) educators to use certain copyrighted works for nonprofit educational purposes
C) information on the Web to be copyright free
D) all of the above
A) individuals to make unlimited copies of copyrighted works
B) educators to use certain copyrighted works for nonprofit educational purposes
C) information on the Web to be copyright free
D) all of the above

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
34
A(n) ____ occurs when the electrical power supply drops.
A) overvoltage
B) blackout
C) power surge
D) undervoltage
A) overvoltage
B) blackout
C) power surge
D) undervoltage

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
35
A(n) ____ is a teacher-created document or Web page that contains hyperlinks.
A) Acceptable Use Policy (AUP)
B) MS Word document
C) student learning page
D) curriculum resource page
A) Acceptable Use Policy (AUP)
B) MS Word document
C) student learning page
D) curriculum resource page

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
36
A ____ allows network users to share a single copy of the software.
A) community site license
B) network site license
C) site license
D) single-user license
A) community site license
B) network site license
C) site license
D) single-user license

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
37
A(n) ____ is a set of rules that govern the use of school and school district computers, networks, and the Internet.
A) Acceptable Use Policy (AUP)
B) Code of Conduct (COC)
C) public domain
D) School Protection Policy (SPP)
A) Acceptable Use Policy (AUP)
B) Code of Conduct (COC)
C) public domain
D) School Protection Policy (SPP)

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
38
Software that is distributed free for a trial use period is called ____.
A) shareware
B) freeware
C) limited use software
D) all of the above
A) shareware
B) freeware
C) limited use software
D) all of the above

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
39
Software that is provided at no cost to a user by an individual or company is called ____.
A) shareware
B) freeware
C) limited use software
D) all of the above
A) shareware
B) freeware
C) limited use software
D) all of the above

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
40
____ studies have shown that using the correct type and configuration of chair, keyboard, display device and worksurface helps users work comfortably and efficiently, and helps protect their health.
A) Green
B) Environmental
C) Ergonomic
D) Musculoskeletal
A) Green
B) Environmental
C) Ergonomic
D) Musculoskeletal

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
41
By acquiring data from public and other sources, national marketing organizations can create an electronic profile of an individual.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
42
Any illegal act involving a computer generally is referred to as a computer crime.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
43
Spam is a scam in which a perpetrator sends an official-looking e-mail that attempts to obtain personal and financial information from the recipient.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
44
Modified Multiple Choice An area of computer ethics frequently discussed includes ____.
A) information privacy
B) copyright issues
C) software theft
D) phishing
A) information privacy
B) copyright issues
C) software theft
D) phishing

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
45
A worm is a malicious software program that hides within a legitimate program.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
46
Modified Multiple Choice A single-user license typically includes the following condition: ____.
A) users may give copies to friends
B) users may make one backup copy of the software
C) users may not give copies to friends
D) users may install the software on only one computer
A) users may give copies to friends
B) users may make one backup copy of the software
C) users may not give copies to friends
D) users may install the software on only one computer

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
47
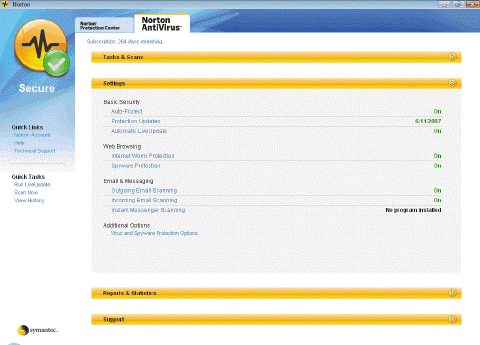 Antivirus programs like those in the accompanying figure work by looking for programs that attempt to modify the boot program, the operating system, and other programs.
Antivirus programs like those in the accompanying figure work by looking for programs that attempt to modify the boot program, the operating system, and other programs.
Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
48
Modified Multiple Choice Objectionable materials located on the Internet include ____.
A) racist literature
B) Word documents
C) obscene videos
D) obscene pictures
A) racist literature
B) Word documents
C) obscene videos
D) obscene pictures

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
49
A community/state site license normally does not provide substantial savings over single-use licenses.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
50
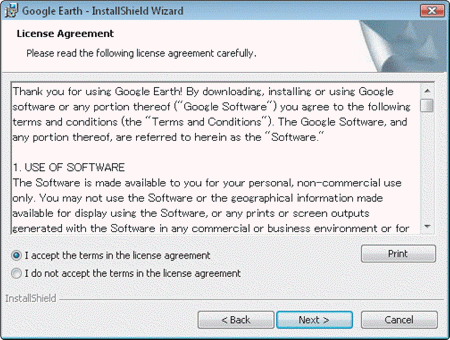 A software license, an example of which is shown in the accompanying figure, is an agreement that provides recommended conditions for use of the software; however, users do not have to accept these recommendations before using the software.
A software license, an example of which is shown in the accompanying figure, is an agreement that provides recommended conditions for use of the software; however, users do not have to accept these recommendations before using the software.
Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
51
Unauthorized access is the use of a computer system or data for unapproved purposes.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
52
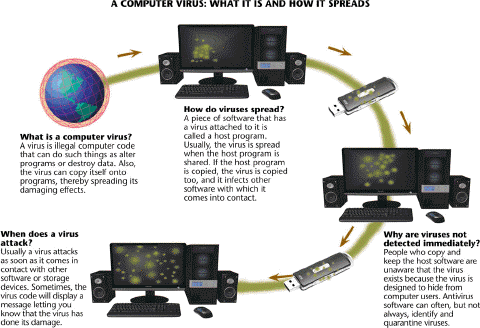 Most viruses like those described in the accompanying figure are harmless pranks that cause no permanent damage.
Most viruses like those described in the accompanying figure are harmless pranks that cause no permanent damage.
Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
53
A proxy server screens all incoming and outgoing messages.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
54
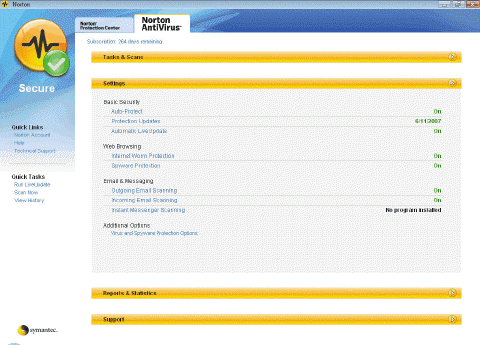 An antivirus program like the one in the accompanying figure also is called a serum.
An antivirus program like the one in the accompanying figure also is called a serum.
Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
55
A logic bomb virus is activated on a particular date.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
56
Schools should never store backup copies at an off-site location.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
57
A backup is a duplicate of a file, program, or disk that can be used if the original is lost, damaged, or destroyed.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
58
Modified Multiple Choice A person who tries to break into a computer system is called a ____.
A) cracker
B) hacker
C) cookie
D) snoop
A) cracker
B) hacker
C) cookie
D) snoop

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
59
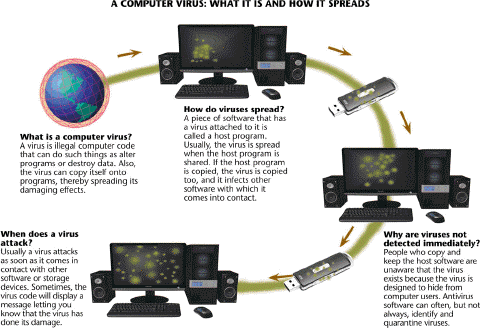 Viruses like those described in the accompanying figure commonly infect computers through e-mail attachments.
Viruses like those described in the accompanying figure commonly infect computers through e-mail attachments.
Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
60
Modified Multiple Choice Computer vandalism includes ____.
A) a student cutting a computer cable
B) a student deleting important computer files
C) stealing a CD
D) individuals breaking into a school and smashing computers
A) a student cutting a computer cable
B) a student deleting important computer files
C) stealing a CD
D) individuals breaking into a school and smashing computers

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
61
Spam sent via Internet Telephony is called split.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
62
The Copyright Act of 1976 established legal use and provided the guidelines that allow educators to use and copy certain copyrighted materials. _________________________

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
63
Copyright laws protect original materials created by students and teachers and published on the Web.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
64
Fair use guidelines allow teachers to use any copyrighted works for educational purposes without any restrictions.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
65
A(n) ____________________ is a type of logic bomb that is activated on a particular date.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
66
Product registration is an antipiracy technology designed to verify that software products have been licensed legitimately. _________________________

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
67
 Cryptogram is the process of converting readable data into unreadable characters by applying a formula that uses a code as shown in the accompanying figure. _________________________
Cryptogram is the process of converting readable data into unreadable characters by applying a formula that uses a code as shown in the accompanying figure. _________________________
Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
68
Filtering software programs prevent access to all objectionable and inappropriate materials.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
69
Biometrics is an applied science devoted to incorporating comfort, efficiency, and safety into the design of items in the workplace. _________________________

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
70
The largest job-related injury and illness problems in the United States today are repetitive strain injuries (RSI).

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
71
A(n) ____________________ replaces the program used to start the computer system with an infected version.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
72
Many display devices and keyboards have features that help address ergonomic issues.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
73
While an outstanding educational tool, curriculum resource pages will not significantly reduce the chances that students will view inappropriate Web sites.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
74
CVS has serious and long-term consequences.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
75
Due to emerging technologies (primarily wireless technologies, tablet computers, and apps) public education is undergoing profound and fundamental changes.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
76
A(n) ____________________ is defined as any event or action that could cause loss or damage to computer capabilities.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
77
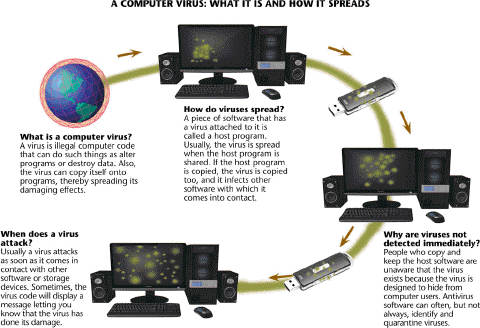 A(n) ____________________ is designed to detect, disinfect, and protect computers and networks from viruses like those in the accompanying figure.
A(n) ____________________ is designed to detect, disinfect, and protect computers and networks from viruses like those in the accompanying figure.
Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
78
The daVinci virus destroys data on March 6, the date of the artist's birthday. _________________________

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
79
Teachers always must protect the identity of their students on student and teacher Web pages.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck
80
False warnings about viruses that often spread via e-mail and over the Internet are known as ____________________.

Unlock Deck
Unlock for access to all 103 flashcards in this deck.
Unlock Deck
k this deck


