Exam 8: Security Issues and Ethics in Education
Exam 1: Integrating Educational Technology Into the Curriculum102 Questions
Exam 2: Communications Networks the Internet and the World Wide Web103 Questions
Exam 3: Software for Educators102 Questions
Exam 4: Hardware for Educators103 Questions
Exam 5: Technology Digital Media and Curriculum Integration103 Questions
Exam 6: The Changing Face of Education 2d Teaching Online103 Questions
Exam 7: Evaluating Educational Technology and Integration Strategies103 Questions
Exam 8: Security Issues and Ethics in Education103 Questions
Select questions type
A(n) ____________________ program attempts to remove spam before it reaches your inbox.
Free
(Short Answer)
4.9/5  (44)
(44)
Correct Answer:
antispam
A ____ gives an entire region or state the right to install an unlimited number of educational copies of a software program.
Free
(Multiple Choice)
4.9/5  (35)
(35)
Correct Answer:
A
Modified Multiple Choice A single-user license typically includes the following condition: ____.
Free
(Multiple Choice)
4.9/5  (30)
(30)
Correct Answer:
B,C,D
Software that is distributed free for a trial use period is called ____.
(Multiple Choice)
4.8/5  (32)
(32)
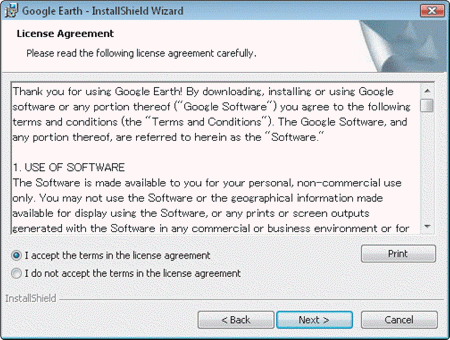 A software license, an example of which is shown in the accompanying figure, is an agreement that provides recommended conditions for use of the software; however, users do not have to accept these recommendations before using the software.
A software license, an example of which is shown in the accompanying figure, is an agreement that provides recommended conditions for use of the software; however, users do not have to accept these recommendations before using the software.
(True/False)
4.7/5  (35)
(35)
Due to emerging technologies (primarily wireless technologies, tablet computers, and apps) public education is undergoing profound and fundamental changes.
(True/False)
4.8/5  (34)
(34)
A(n) ____ is a teacher-created document or Web page that contains hyperlinks.
(Multiple Choice)
4.8/5  (33)
(33)
A ____ virus hides within or is designed to look like a legitimate program.
(Multiple Choice)
4.8/5  (39)
(39)
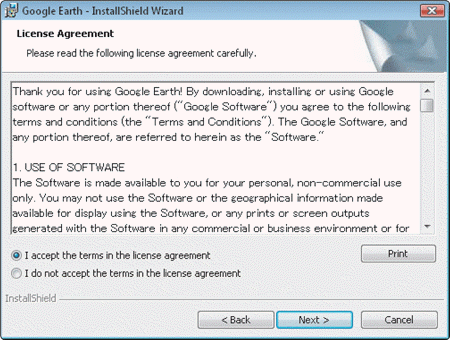 As shown in the accompanying figure, a(n) ____________________ is an agreement that provides specific conditions for use of the software, which users must accept before using the software.
As shown in the accompanying figure, a(n) ____________________ is an agreement that provides specific conditions for use of the software, which users must accept before using the software.
(Short Answer)
4.8/5  (39)
(39)
A computer security risk is defined as any event or action that could cause loss of, or damage to, ____.
(Multiple Choice)
4.9/5  (33)
(33)
A backup is a duplicate of a file, program, or disk that can be used if the original is lost, damaged, or destroyed.
(True/False)
4.8/5  (36)
(36)
All of the following are tips for creating passwords EXCEPT ____.
(Multiple Choice)
4.8/5  (35)
(35)
A(n) ____________________ is defined as any event or action that could cause loss or damage to computer capabilities.
(Short Answer)
4.9/5  (24)
(24)
A(n) ____________________ gives the buyer the right to install software on multiple computers at a single site.
(Short Answer)
4.8/5  (30)
(30)
Possessed objects are often used in combination with a(n) ____________________ that is a numeric password that provides an additional level of security.
(Short Answer)
4.8/5  (31)
(31)
Software that is provided at no cost to a user by an individual or company is called ____.
(Multiple Choice)
4.7/5  (27)
(27)
Filtering software programs prevent access to all objectionable and inappropriate materials.
(True/False)
4.9/5  (28)
(28)
Showing 1 - 20 of 103
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)