Deck 11: Computer Security, Ethics, and Privacy
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/191
Play
Full screen (f)
Deck 11: Computer Security, Ethics, and Privacy
1
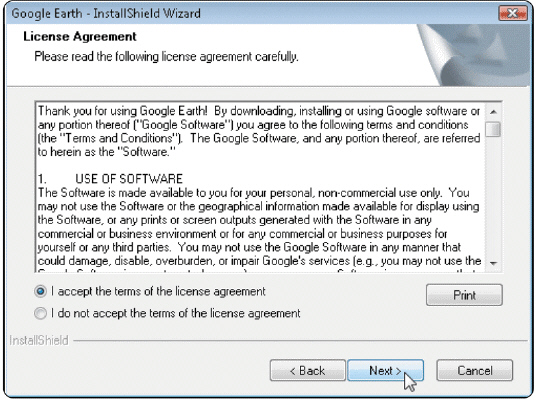 Figure 11-5 When users purchase software, a single-user license agreement like the one in Figure 11-5 does not permit users to do any of the following except ____.
Figure 11-5 When users purchase software, a single-user license agreement like the one in Figure 11-5 does not permit users to do any of the following except ____.A) install the software on a network
B) give copies to friends and colleagues
C) make one copy of the software as backup
D) export the software
C
2
Some viruses are hidden in ____, which are instructions saved in an application such as a word processing or spreadsheet program.
A) macros
B) logs
C) cookies
D) spikes
A) macros
B) logs
C) cookies
D) spikes
A
3
 Figure 11-3 To ____ a program file, a program like the one in Figure 11-3 records information such as the file size and file creation date in a separate file.
Figure 11-3 To ____ a program file, a program like the one in Figure 11-3 records information such as the file size and file creation date in a separate file.A) quarantine
B) decrypt
C) blackout
D) inoculate
D
4
Computer viruses, worms, and Trojan horses deliver their payload on a computer when a user ____.
A) opens an infected file
B) runs an infected program
C) boots the computer with an infected disk in a disk drive
D) all of the above
A) opens an infected file
B) runs an infected program
C) boots the computer with an infected disk in a disk drive
D) all of the above

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
5
To prevent unauthorized access and use, at a minimum a company should have a written ____ that outlines the computer activities for which a computer or network may and may not be used.
A) acceptable use policy (AUP)
B) universal procedures standard (UPS)
C) performance guarantee policy (PGP)
D) maintenance security dictum (MSD)
A) acceptable use policy (AUP)
B) universal procedures standard (UPS)
C) performance guarantee policy (PGP)
D) maintenance security dictum (MSD)

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
6
A ____ is a program that copies itself repeatedly in memory or on a network, using up resources and possibly shutting down the computer or network.
A) computer virus
B) worm
C) Trojan horse
D) all of the above
A) computer virus
B) worm
C) Trojan horse
D) all of the above

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
7
To help reduce the chance of ____, physical controls such as locked doors and cables usually are adequate to protect equipment.
A) software piracy
B) hardware theft
C) system failure
D) unauthorized access
A) software piracy
B) hardware theft
C) system failure
D) unauthorized access

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
8
A honeypot is a program designed to ____.
A) negatively affect the way a computer works
B) entice an intruder to hack into a computer
C) identify and remove computer viruses found in memory
D) secretly collect information about a user
A) negatively affect the way a computer works
B) entice an intruder to hack into a computer
C) identify and remove computer viruses found in memory
D) secretly collect information about a user

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
9
The term ____ refers to online or Internet-based illegal acts.
A) malicious-logic program
B) computer crime
C) cybercrime
D) system failure
A) malicious-logic program
B) computer crime
C) cybercrime
D) system failure

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
10
In its simplest form, a(n) ____ is a programmed formula that the recipient of encrypted data uses to decrypt the ciphertext.
A) encryption key
B) virus signature
C) digital certificate
D) session cookie
A) encryption key
B) virus signature
C) digital certificate
D) session cookie

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
11
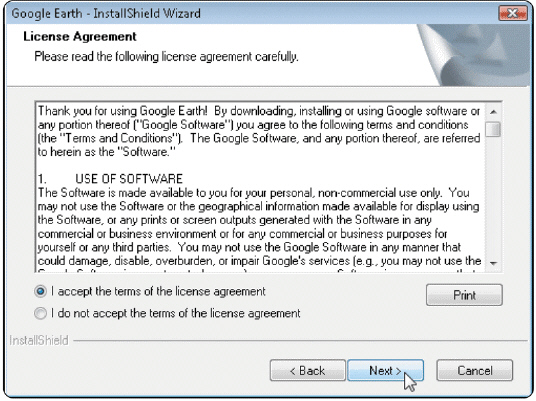 Figure 11-5 When users purchase software, a single-user license agreement like the one in Figure 11-5 permits users to do any of the following except ____.
Figure 11-5 When users purchase software, a single-user license agreement like the one in Figure 11-5 permits users to do any of the following except ____.A) install the software on only one computer
B) rent or lease the software
C) make one copy of the software as backup
D) give or sell the software to another individual if the software is removed from the user's computer first

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
12
Each character added to a password significantly ____ it might take for someone or for a hacker's computer to guess the password.
A) reduces the number of combinations and the length of time
B) reduces the number of combinations but increases the length of time
C) increases the number of combinations but reduces the length of time
D) increases the number of combinations and the length of time
A) reduces the number of combinations and the length of time
B) reduces the number of combinations but increases the length of time
C) increases the number of combinations but reduces the length of time
D) increases the number of combinations and the length of time

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
13
Examples of biometric devices and systems include all of the following except ____.
A) fingerprint scanners and hand geometry systems
B) face recognition systems and voice recognition systems
C) signature verification systems and iris recognition systems
D) personal identification numbers and password systems
A) fingerprint scanners and hand geometry systems
B) face recognition systems and voice recognition systems
C) signature verification systems and iris recognition systems
D) personal identification numbers and password systems

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
14
Some notebook computers use ____ as methods of security.
A) passwords
B) possessed objects
C) biometrics
D) all of the above
A) passwords
B) possessed objects
C) biometrics
D) all of the above

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
15
The computer that a hacker uses to execute a DoS or DDoS attack, known as a ____, is completely unaware that it is being used to attack other systems.
A) cookie
B) proxy
C) zombie
D) standby
A) cookie
B) proxy
C) zombie
D) standby

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
16
A ____ is a malicious-logic program that hides within or looks like a legitimate program and usually is triggered by a certain condition or action.
A) computer virus
B) worm
C) Trojan horse
D) all of the above
A) computer virus
B) worm
C) Trojan horse
D) all of the above

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
17
The ____ is the destructive event or prank a malicious-logic program is intended to deliver.
A) zombie
B) hash
C) cracker
D) payload
A) zombie
B) hash
C) cracker
D) payload

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
18
To promote a better understanding of software piracy problems and, if necessary, to take legal action, a number of major worldwide software companies formed the ____.
A) Computer Emergency Response Team (CERT)
B) Business Software Alliance (BSA)
C) Underwriters Laboratory (UL)
D) Virtual Private Network (VPN)
A) Computer Emergency Response Team (CERT)
B) Business Software Alliance (BSA)
C) Underwriters Laboratory (UL)
D) Virtual Private Network (VPN)

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
19
A ____ is a separate area of a hard disk that holds an infected file until the infection can be removed.
A) quarantine
B) payload
C) firewall
D) honeypot
A) quarantine
B) payload
C) firewall
D) honeypot

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
20
Software piracy continues for all of the following reasons except ____.
A) software piracy drives down the price of software for all users
B) in some countries, legal protection for software does not exist
C) software piracy is a fairly simple crime to commit
D) many buyers believe they have the right to copy software they have paid for
A) software piracy drives down the price of software for all users
B) in some countries, legal protection for software does not exist
C) software piracy is a fairly simple crime to commit
D) many buyers believe they have the right to copy software they have paid for

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
21
____, which provides encryption of all data that passes between a client and an Internet server, requires only that the client has a digital certificate.
A) Secure Sockets Layer (SSL)
B) Secure HTTP (S-HTTP)
C) Secure Electronics Transactions (SET) Specifications
D) Pretty Good Privacy (PGP)
A) Secure Sockets Layer (SSL)
B) Secure HTTP (S-HTTP)
C) Secure Electronics Transactions (SET) Specifications
D) Pretty Good Privacy (PGP)

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
22
Web sites use a ____ to keep track of items in a user's shopping cart.
A) session cookie
B) zombie
C) adware
D) shopping bot
A) session cookie
B) zombie
C) adware
D) shopping bot

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
23
With a three-generation backup policy, the parent is the ____.
A) most recent copy of the file
B) second oldest copy of the file
C) oldest copy of the file
D) original file
A) most recent copy of the file
B) second oldest copy of the file
C) oldest copy of the file
D) original file

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
24
A(n) ____ copies all of the files in a computer.
A) full backup
B) incremental backup
C) differential backup
D) selective backup
A) full backup
B) incremental backup
C) differential backup
D) selective backup

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
25
A ____ is a small text file that a Web server stores on a user's computer.
A) worm
B) spike
C) cookie
D) payload
A) worm
B) spike
C) cookie
D) payload

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
26
One of the more common causes of ____ is an electrical power variation.
A) hardware vandalism
B) system failure
C) unauthorized access
D) software theft
A) hardware vandalism
B) system failure
C) unauthorized access
D) software theft

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
27
Some perpetrators use a technique called ____ in which they attempt to connect to wireless networks via their notebook computers while driving a vehicle through areas they suspect have a wireless network.
A) cyberforensics
B) war driving
C) war flying
D) wire cruising
A) cyberforensics
B) war driving
C) war flying
D) wire cruising

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
28
Internet advertising firms often use ____ to collect information about users Web browsing habits.
A) comware
B) postware
C) adware
D) billware
A) comware
B) postware
C) adware
D) billware

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
29
When a mobile user connects to a main office using a standard Internet connection, a ____ provides the mobile user with a secure connection to the company network server.
A) value added network (VAN)
B) local area network (LAN)
C) virtual private network (VPN)
D) wide area network (WAN)
A) value added network (VAN)
B) local area network (LAN)
C) virtual private network (VPN)
D) wide area network (WAN)

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
30
____, which allows users to choose an encryption scheme that passes between a client and a server, requires that both the client and server have digital certificates.
A) Secure Sockets Layer (SSL)
B) Secure HTTP (S-HTTP)
C) Secure Electronics Transactions (SET) Specifications
D) Pretty Good Privacy (PGP)
A) Secure Sockets Layer (SSL)
B) Secure HTTP (S-HTTP)
C) Secure Electronics Transactions (SET) Specifications
D) Pretty Good Privacy (PGP)

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
31
A UPS connects between a computer and a ____.
A) peripheral device
B) disk drive
C) communications device
D) power source
A) peripheral device
B) disk drive
C) communications device
D) power source

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
32
With a three-generation backup policy, the child is the ____.
A) most recent copy of the file
B) second oldest copy of the file
C) oldest copy of the file
D) original file
A) most recent copy of the file
B) second oldest copy of the file
C) oldest copy of the file
D) original file

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
33
____ is/are not considered spyware because a user knows it/they exist(s).
A) Adware
B) Cookies
C) A Web bug
D) Spam
A) Adware
B) Cookies
C) A Web bug
D) Spam

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
34
With a three-generation backup policy, the grandparent is the ____.
A) most recent copy of the file
B) second oldest copy of the file
C) oldest copy of the file
D) original file
A) most recent copy of the file
B) second oldest copy of the file
C) oldest copy of the file
D) original file

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
35
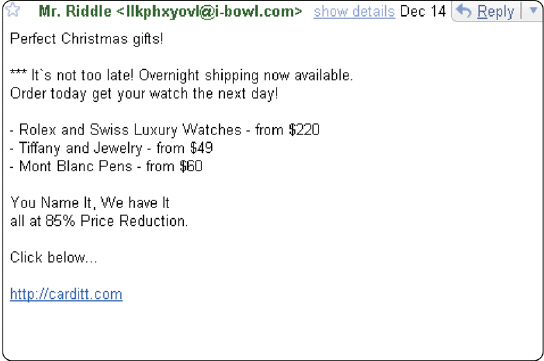 Figure 11-1 ____, like that shown in Figure 11-1, is an unsolicited e-mail message or newsgroup posting sent to many recipients or newsgroups at once.
Figure 11-1 ____, like that shown in Figure 11-1, is an unsolicited e-mail message or newsgroup posting sent to many recipients or newsgroups at once.A) Hash
B) Spam
C) Worm
D) Spike

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
36
A momentary overvoltage, called a ____, occurs when the increase in power lasts for less than one millisecond (one thousandth of a second).
A) Joule
B) spike
C) hash
D) macro
A) Joule
B) spike
C) hash
D) macro

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
37
A ____ is the unit of energy a surge protection device can absorb before it can be damaged.
A) Joule
B) spike
C) hash
D) macro
A) Joule
B) spike
C) hash
D) macro

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
38
With a(n) ____, users choose which folders and files to include in a backup.
A) full backup
B) incremental backup
C) differential backup
D) selective backup
A) full backup
B) incremental backup
C) differential backup
D) selective backup

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
39
A ____ is a mathematical formula that generates a code from the contents of an e-mail message.
A) spike
B) macro
C) password
D) hash
A) spike
B) macro
C) password
D) hash

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
40
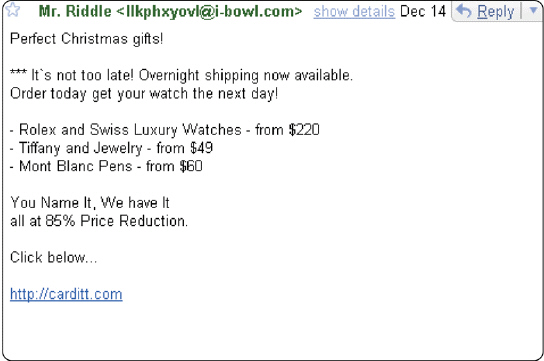 Figure 11-1 To avoid items like that shown in Figure 11-1, users can sign up for ____, which is a service from an Internet service provider that blocks e-mail messages from designated sources.
Figure 11-1 To avoid items like that shown in Figure 11-1, users can sign up for ____, which is a service from an Internet service provider that blocks e-mail messages from designated sources.A) an anti-spam program
B) e-mail encryption
C) an antivirus program
D) e-mail filtering

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
41
In addition to access controls, a computer should maintain a(n) ____ trail that records both successful and unsuccessful access attempts.
A) audit
B) signature
C) object
D) index
A) audit
B) signature
C) object
D) index

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
42
A virus ____ is a known specific pattern of virus code.
A) index
B) signature
C) glossary
D) master
A) index
B) signature
C) glossary
D) master

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
43
____ is an applied science devoted to incorporating comfort, efficiency, and safety into the design of items in the workplace.
A) Ergonomics
B) Eurhythmics
C) Epidemics
D) Econometrics
A) Ergonomics
B) Eurhythmics
C) Epidemics
D) Econometrics

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
44
A(n) ____ is a program or set of instructions in a program that allow users to bypass security controls when accessing a program, computer, or network.
A) signature
B) service
C) backdoor
D) integrated server
A) signature
B) service
C) backdoor
D) integrated server

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
45
One approach to content filtering is through a rating system of ____, which is similar to those used for movies and videos.
A) ICRA
B) AOL
C) MSN
D) BSA
A) ICRA
B) AOL
C) MSN
D) BSA

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
46
____ access is the use of a computer or network without permission.
A) Unauthorized
B) Unidentified
C) Unaudited
D) Biometric
A) Unauthorized
B) Unidentified
C) Unaudited
D) Biometric

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
47
A(n) ____ server is a server outside a company's network that controls which communications pass into the company's network.
A) integrated
B) access
C) zombie
D) proxy
A) integrated
B) access
C) zombie
D) proxy

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
48
A(n) ____ control is a security measure that defines who can access a computer, when they can access it, and what actions they can take while accessing the computer.
A) maintenance
B) access
C) possession
D) audit
A) maintenance
B) access
C) possession
D) audit

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
49
The 1986 ____ provides the same protection that covers mail and telephone communications to electronic communications such as voice mail.
A) Electronic Communications Privacy Act (ECPA)
B) Fair Credit Reporting Act
C) Computer Fraud and Abuse Act
D) Computer Matching and Privacy Protection Act
A) Electronic Communications Privacy Act (ECPA)
B) Fair Credit Reporting Act
C) Computer Fraud and Abuse Act
D) Computer Matching and Privacy Protection Act

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
50
____ is a scam in which a perpetrator sends an official looking e-mail that attempts to obtain a user's personal and financial information.
A) Spam
B) Spit
C) Phishing
D) Spyware
A) Spam
B) Spit
C) Phishing
D) Spyware

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
51
A computer ____ is a potentially damaging computer program that affects, or infects, a computer negatively by altering the way the computer works without the user's knowledge or permission.
A) signature
B) virus
C) definition
D) spim
A) signature
B) virus
C) definition
D) spim

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
52
The 1988 ____ regulates the use of government data to determine the eligibility of individuals for federal benefits.
A) Electronic Communications Privacy Act (ECPA)
B) Fair Credit Reporting Act
C) Computer Fraud and Abuse Act
D) Computer Matching and Privacy Protection Act
A) Electronic Communications Privacy Act (ECPA)
B) Fair Credit Reporting Act
C) Computer Fraud and Abuse Act
D) Computer Matching and Privacy Protection Act

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
53
A(n) ____ attack is an assault whose purpose is to disrupt computer access to an Internet service such as the Web or e-mail.
A) signature
B) service
C) DoS
D) IMP
A) signature
B) service
C) DoS
D) IMP

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
54
A(n) ____ is someone who accesses a computer or network illegally but has the intent of destroying data, stealing information, or other malicious action.
A) cracker
B) cyberterrorist
C) cyberstalker
D) script kiddie
A) cracker
B) cyberterrorist
C) cyberstalker
D) script kiddie

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
55
Many businesses use ____ to limit employees' Web access.
A) content filtering
B) Web bugs
C) honeypots
D) spyware
A) content filtering
B) Web bugs
C) honeypots
D) spyware

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
56
Personal computers, display devices, and printers should comply with guidelines of the ____ program.
A) ENERGY STAR
B) SECURE ELECTRONICS
C) ACCEPTABLE USE
D) GREEN COMPUTING
A) ENERGY STAR
B) SECURE ELECTRONICS
C) ACCEPTABLE USE
D) GREEN COMPUTING

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
57
The term ____, although originally a complimentary word for a computer enthusiast, now has a derogatory meaning and refers to someone who accesses a computer or network illegally.
A) hacker
B) cyberterrorist
C) script kiddie
D) cyberstalker
A) hacker
B) cyberterrorist
C) script kiddie
D) cyberstalker

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
58
Symptoms of a user with computer addiction include all of the following except ____.
A) craves computer time
B) unable to stop computer activity
C) neglects family and friends
D) irritable when at the computer
A) craves computer time
B) unable to stop computer activity
C) neglects family and friends
D) irritable when at the computer

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
59
Computer forensics is used by ____.
A) military intelligence
B) insurance agencies
C) law enforcement
D) all of the above
A) military intelligence
B) insurance agencies
C) law enforcement
D) all of the above

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
60
To prevent repetitive strain injury, take all of the following precautions except ____.
A) place a wrist rest between the keyboard and the edge of the desk
B) use the heel of the hand as a pivot point while typing or using the mouse
C) place the mouse at least six inches from the edge of the desk
D) minimize the number of switches between the mouse and the keyboard
A) place a wrist rest between the keyboard and the edge of the desk
B) use the heel of the hand as a pivot point while typing or using the mouse
C) place the mouse at least six inches from the edge of the desk
D) minimize the number of switches between the mouse and the keyboard

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
61
A(n) ____ gives authors and artists exclusive rights to duplicate, publish, and sell their materials.
A) intellectual property deed
B) content license
C) access right
D) copyright
A) intellectual property deed
B) content license
C) access right
D) copyright

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
62
A(n) ____ certificate is a notice that guarantees a user or Web site is legitimate.
A) assigned
B) secure
C) protected
D) digital
A) assigned
B) secure
C) protected
D) digital

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
63
A Web site that uses encryption techniques to secure its data is known as a(n) ____ site.
A) assigned
B) master
C) secure
D) encrypted
A) assigned
B) master
C) secure
D) encrypted

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
64
One of the more popular e-mail encryption programs is called ____, which is freeware for personal, noncommercial users.
A) IMP
B) TCP
C) DoS
D) PGP
A) IMP
B) TCP
C) DoS
D) PGP

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
65
One type of spyware, called a(n) ____, is hidden on Web pages or in e-mail messages in the form of graphical images.
A) Web bug
B) forensic element
C) content filter
D) integrated bot
A) Web bug
B) forensic element
C) content filter
D) integrated bot

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
66
____ is the process of converting readable data into unreadable characters to prevent unauthorized access.
A) Decryption
B) PGP
C) Encryption
D) Digital signing
A) Decryption
B) PGP
C) Encryption
D) Digital signing

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
67
A(n) ____ is an injury or disorder of the muscles, nerves, tendons, ligaments, and joints.
A) DoS
B) ISP
C) PGP
D) RSI
A) DoS
B) ISP
C) PGP
D) RSI

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
68
Content ____ is the process of restricting access to certain material on the Web.
A) remastering
B) filtering
C) indexing
D) masking
A) remastering
B) filtering
C) indexing
D) masking

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
69
A certificate ____ is an authorized person or company that issues and verifies digital certificates.
A) authority
B) agency
C) office
D) bureau
A) authority
B) agency
C) office
D) bureau

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
70
____ refers to unique and original works such as ideas, inventions, writings, art, processes, company and product names, and logos.
A) PGP
B) DoS
C) IP
D) TCP
A) PGP
B) DoS
C) IP
D) TCP

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
71
The most common type of license included with software purchased by individual users is a(n) ____.
A) EULA
B) DoS
C) activated license
D) encrypted license
A) EULA
B) DoS
C) activated license
D) encrypted license

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
72
A(n) ____ is a device that contains surge protection circuits and one or more batteries that can provide power during a temporary or permanent loss of power.
A) PGP
B) DoS
C) UPS
D) DDos
A) PGP
B) DoS
C) UPS
D) DDos

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
73
A(n) ____ is a duplicate of a file, program, or disk that can be used if the original is lost, damaged, or destroyed.
A) restored file
B) bot
C) IP file
D) backup
A) restored file
B) bot
C) IP file
D) backup

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
74
A(n) ____ device authenticates a person's identity by translating a personal characteristic into a digital code that then is compared with a digital code stored in the computer verifying a physical or behavioral characteristic.
A) authenticating
B) possessed
C) biometric
D) identifying
A) authenticating
B) possessed
C) biometric
D) identifying

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
75
A(n) ____ network, the most recent network standard, conforms to the government security standards and uses more sophisticated encryption techniques than WPA or WEP.
A) 802.11a
B) 802.11i
C) 802.11b
D) 802.11k
A) 802.11a
B) 802.11i
C) 802.11b
D) 802.11k

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
76
A(n) ____ signature is an encryption code that a person, Web site, or company attaches to an electronic message to verify the identity of the message sender.
A) secure
B) digital
C) certifying
D) assigned
A) secure
B) digital
C) certifying
D) assigned

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
77
 Figure 11-4 A(n) ____ object, an example of which is shown in Figure 11-4, is any item that must be carried to gain access to a computer or computer facility.
Figure 11-4 A(n) ____ object, an example of which is shown in Figure 11-4, is any item that must be carried to gain access to a computer or computer facility.A) access
B) possessed
C) master
D) license

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
78
Computer ____ is the discovery, collection, and analysis of evidence found on computers and networks.
A) anthropology
B) epistemology
C) forensics
D) reduction
A) anthropology
B) epistemology
C) forensics
D) reduction

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
79
A(n) ____ agreement is the right to use software.
A) user
B) master
C) authenticating
D) license
A) user
B) master
C) authenticating
D) license

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck
80
During product ____, which is conducted either online or by telephone, users provide a software product's 25-character identification number to receive an installation identification number unique to the computer on which the software is installed.
A) concatenation
B) activation
C) termination
D) encryption
A) concatenation
B) activation
C) termination
D) encryption

Unlock Deck
Unlock for access to all 191 flashcards in this deck.
Unlock Deck
k this deck


