Exam 11: Computer Security, Ethics, and Privacy
Exam 1: Introduction to Computers191 Questions
Exam 2: The Internet and World Wide Web191 Questions
Exam 3: Application Software191 Questions
Exam 4: The Components of the System Unit191 Questions
Exam 5: Input181 Questions
Exam 6: Output191 Questions
Exam 7: Storage191 Questions
Exam 8: Operating Systems and Utility Programs191 Questions
Exam 9: Communications and Networks181 Questions
Exam 10: Database Management191 Questions
Exam 11: Computer Security, Ethics, and Privacy191 Questions
Exam 12: Information System Development191 Questions
Exam 13: Programming Languages and Program Development191 Questions
Exam 14: Enterprise Computing191 Questions
Exam 15: Computer Careers and Certification191 Questions
Select questions type
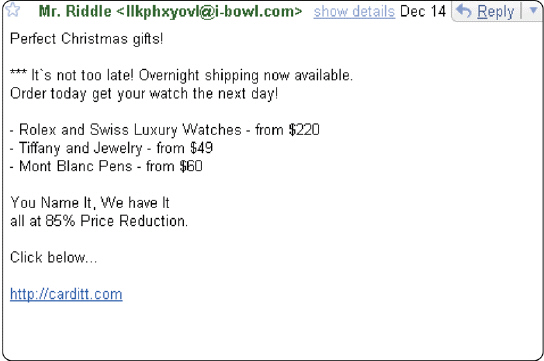 Figure 11-1 Spim is messages like those in Figure 11-1, but sent via Internet telephony.
Figure 11-1 Spim is messages like those in Figure 11-1, but sent via Internet telephony.
Free
(True/False)
4.8/5  (32)
(32)
Correct Answer:
False
____________________ is a program that restricts access to specified Web sites.
Free
(Short Answer)
4.9/5  (35)
(35)
Correct Answer:
Web filtering software
Critics contend that the information in an electronic profile reveals more about an individual than anyone has the right to know.
Free
(True/False)
4.9/5  (40)
(40)
Correct Answer:
True
One suggestion to safeguard personal information is to avoid shopping clubs and buyer cards.
(True/False)
4.9/5  (39)
(39)
____________________ is a technique intruders use to make their network or Internet transmission appear legitimate to a victim computer or network.
(Short Answer)
5.0/5  (32)
(32)
An employee using an organization's computer to track his or her child's soccer league scores is an example of unauthorized access.
(True/False)
4.9/5  (26)
(26)
Thieves often target notebook computers of company executives, so they can use the stolen computer to access confidential company information illegally.
(True/False)
4.7/5  (41)
(41)
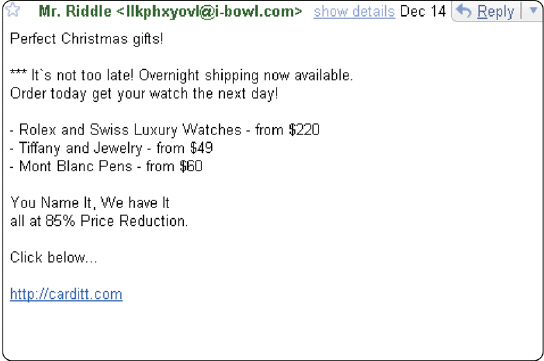 Figure 11-1 ____, like that shown in Figure 11-1, is an unsolicited e-mail message or newsgroup posting sent to many recipients or newsgroups at once.
Figure 11-1 ____, like that shown in Figure 11-1, is an unsolicited e-mail message or newsgroup posting sent to many recipients or newsgroups at once.
(Multiple Choice)
5.0/5  (28)
(28)
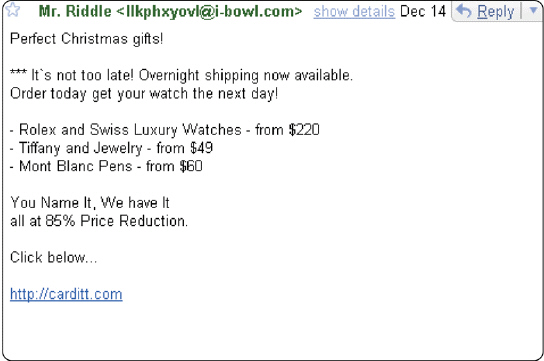 Figure 11-1 To avoid items like that shown in Figure 11-1, users can sign up for ____, which is a service from an Internet service provider that blocks e-mail messages from designated sources.
Figure 11-1 To avoid items like that shown in Figure 11-1, users can sign up for ____, which is a service from an Internet service provider that blocks e-mail messages from designated sources.
(Multiple Choice)
5.0/5  (39)
(39)
To prevent repetitive strain injury, take all of the following precautions except ____.
(Multiple Choice)
4.9/5  (31)
(31)
During product ____, which is conducted either online or by telephone, users provide a software product's 25-character identification number to receive an installation identification number unique to the computer on which the software is installed.
(Multiple Choice)
4.8/5  (35)
(35)
In the case of system failure or the discovery of corrupted files, users ____________________ the files by copying the backed up files to their original location on a computer.
(Short Answer)
4.9/5  (33)
(33)
The National Photographers Association believes that allowing even the slightest alteration could lead to misrepresentations in photographs.
(True/False)
4.7/5  (33)
(33)
Identify the letter of the choice that best matches the phrase or definition.
Correct Answer:
Premises:
Responses:
(Matching)
4.9/5  (38)
(38)
Software piracy continues for all of the following reasons except ____.
(Multiple Choice)
4.9/5  (37)
(37)
A surge protector absorbs small overvoltages - generally without damage to the computer or equipment.
(True/False)
4.8/5  (41)
(41)
 Figure 11-4 Biometric objects, like the one shown in Figure 11-4, often are used in combination with personal identification numbers.
Figure 11-4 Biometric objects, like the one shown in Figure 11-4, often are used in combination with personal identification numbers.
(True/False)
4.8/5  (41)
(41)
A(n) ____ gives authors and artists exclusive rights to duplicate, publish, and sell their materials.
(Multiple Choice)
4.9/5  (37)
(37)
Showing 1 - 20 of 191
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)