Deck 10: E-Mail Security
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/86
Play
Full screen (f)
Deck 10: E-Mail Security
1
A(n) host address resource record associates a particular TCP/IP service to a server.
False
2
Apple Mail uses PGP for security and enables you to specify use of SSL for security over Internet links to e-mail.
True
3
When using only SMTP, no line can be longer than 1000 characters.
True
4
PKCS is a proprietary encryption method developed by RSA Security as an alternative to DES.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
5
EBlock works with Microsoft's Internet Mail Service to create a list of sources from which to refuse e-mail.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
6
GPG is a security method that is designed to be compatible with PGP.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
7
PGP enables the use of X.509 or PGP digital certificates, which are essentially public keys given to the recipient of the e-mail communication.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
8
SMTP was proposed in 1982 by Jon Postel and began, in part, as an alternative to FTP for sending a file from one computer system to another.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
9
In terms of encryption, the original S/MIME version used a 56-bit encryption method, called RC3.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
10
MIME is designed for the exchange of electronic mail between networked systems, particularly via the Internet.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
11
When e-mail is accessed on an e-mail server using POP3, only the message headers are initially downloaded to the client.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
12
A local delivery agent is used to transmit an e-mail message.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
13
A valuable security feature of Apple Mail is that you can create rules to reject mail from unwanted or unknown sources.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
14
SMTP is a client and server process.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
15
Authenticating e-mail is one of the most effective ways to ensure the privacy of messages while they are in transit and after they arrive at an SMTP server.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
16
The MIME extensions are provided to enable 8-bit binary encoding, and they enable the sending of multipart messages.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
17
CAST was developed by Xuejia Lai and James Massey and uses a 128-bit key.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
18
One way to help control UCE is for an organization to ensure that its mail servers are not configured as open SMTP relay servers.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
19
POP3 is popular among many ISPs because it is designed so that messages are downloaded to an inbox on the client's computer, rather than being stored on the e-mail server after they are accessed.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
20
A common way to attack SMTP is an indirect attack through a DNS server.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
21
When an e-mail message is sent, what type of program is used to place a new message into a particular user's mailbox?
A) Message transfer agent
B) Mail user agent
C) Local delivery agent
D) Message placement agent
A) Message transfer agent
B) Mail user agent
C) Local delivery agent
D) Message placement agent

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
22
When an e-mail message is sent, what type of program is used to compose and read an e-mail message?
A) Mail user agent
B) Message transfer agent
C) Local delivery agent
D) Mail reader agent
A) Mail user agent
B) Message transfer agent
C) Local delivery agent
D) Mail reader agent

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
23
Which TCP port is used for POP2?
A) 23
B) 109
C) 110
D) 125
A) 23
B) 109
C) 110
D) 125

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
24
Which of the following information is contained in an SMTP message header?
A) To:
B) From:
C) Date:
D) Subject:
E) All of the above
A) To:
B) From:
C) Date:
D) Subject:
E) All of the above

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
25
SMTP was proposed in _____ by Jon Postel and began, in part, as an alternative to FTP for sending a file from one computer system to another.
A) 1972
B) 1982
C) 1992
D) 2002
A) 1972
B) 1982
C) 1992
D) 2002

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
26
What TCP port does IMAP use?
A) 25
B) 109
C) 110
D) 143
A) 25
B) 109
C) 110
D) 143

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
27
In an SMTP address header, the _____ is the dotted-decimal address of the SMTP server.
A) envelope
B) message header
C) host names
D) domain literal
A) envelope
B) message header
C) host names
D) domain literal

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
28
What command does an attacker use to send the contents of a malicious file into the port-scanning software, directing the port scanner to send it to the target SMTP server on port 25?
A) send
B) post
C) grep
D) pipe
A) send
B) post
C) grep
D) pipe

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
29
To look up a computer name on the basis of its IP address, a DNS _____ is configured on the DNS server.
A) location resource record
B) host address resource record
C) service locator record
D) pointer resource record
A) location resource record
B) host address resource record
C) service locator record
D) pointer resource record

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
30
What is the most current version of IMAP?
A) 2
B) 3
C) 4
D) 5
A) 2
B) 3
C) 4
D) 5

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
31
A _____ associates a particular TCP/IP service to a server along with the domain of the server and its protocol.
A) pointer resource record
B) host address resource record
C) service locator record
D) server locator record
A) pointer resource record
B) host address resource record
C) service locator record
D) server locator record

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
32
SMTP processes e-mail through a queue that serves as a _____ for users that connect to that server.
A) home base
B) resource center
C) post office
D) library
A) home base
B) resource center
C) post office
D) library

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
33
What type of encoding is used by SMTP?
A) 7-bit ASCII
B) 7-bit binary
C) 11-bit ASCII
D) 11-bit binary
A) 7-bit ASCII
B) 7-bit binary
C) 11-bit ASCII
D) 11-bit binary

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
34
How many parts does each SMTP message have?
A) 1
B) 2
C) 3
D) 4
A) 1
B) 2
C) 3
D) 4

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
35
Looking up a computer on the basis of its name and then associating that name with an IP address is accomplished by defining a DNS _____ .
A) host address resource record
B) service locator record
C) pointer resource record
D) location resource record
A) host address resource record
B) service locator record
C) pointer resource record
D) location resource record

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
36
In an SMTP address header, the _____ is the name of the SMTP post office server used to transmit and receive the e-mail.
A) domain name
B) server name
C) host name
D) post office name
A) domain name
B) server name
C) host name
D) post office name

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
37
When an e-mail message is sent, what type of program is used to transmit the e-mail message?
A) Message transmission agent
B) Message transfer agent
C) Local delivery agent
D) Mail user agent
A) Message transmission agent
B) Message transfer agent
C) Local delivery agent
D) Mail user agent

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
38
Which of the following ports is required for a user to send e-mail via SMTP?
A) 25
B) 23
C) 110
D) 443
A) 25
B) 23
C) 110
D) 443

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
39
Which TCP port is used for POP3?
A) 25
B) 100
C) 109
D) 110
A) 25
B) 100
C) 109
D) 110

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
40
Which protocol enables e-mail to be received and stored on an SMTP server and allows clients to obtain their messages?
A) MIME
B) S/MIME
C) X.400
D) IMAP
A) MIME
B) S/MIME
C) X.400
D) IMAP

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
41
Does SMTP support the transmission of ASCII text as well as binary file?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
42
Is unsolicited commercial e-mail very expensive for organizations?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
43
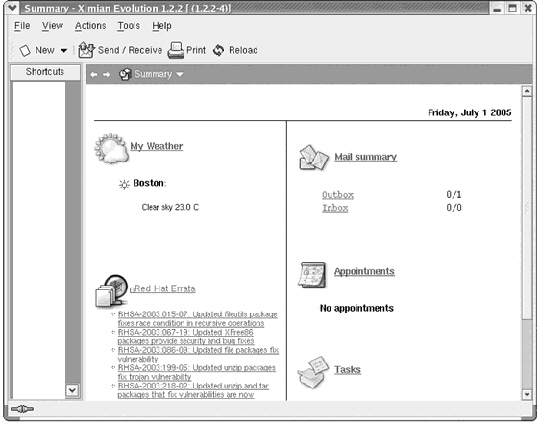 What is displayed in the figure above?
What is displayed in the figure above?A) Outlook Express
B) Apple Mail
C) Evolution Mail configuration options
D) Evolution Mail Summary view

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
44
Which of the following e-mail security features offered by Microsoft Outlook are proprietary to Microsoft exchange?
A) V1 Exchange Server Security certificates
B) X2 Exchange Server Security certificates
C) Digital signatures encrypted using the Security Hash Algorithm 1
D) 168-bit Exchange Server mail encryption services
A) V1 Exchange Server Security certificates
B) X2 Exchange Server Security certificates
C) Digital signatures encrypted using the Security Hash Algorithm 1
D) 168-bit Exchange Server mail encryption services

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
45
What is the name of the e-mail tools used in Mac OS X?
A) Ximian
B) Pine
C) MailX
D) Mail
A) Ximian
B) Pine
C) MailX
D) Mail

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
46
Which of the following encryption methods are supported by GPG?
A) Twofish
B) Blowfish
C) IDEA
D) Both a and b
E) Both b and c
A) Twofish
B) Blowfish
C) IDEA
D) Both a and b
E) Both b and c

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
47
Which of the following is an example of a Commercial CA?
A) GCFN
B) GTE CyberTrust
C) Thawte
D) All of the above
A) GCFN
B) GTE CyberTrust
C) Thawte
D) All of the above

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
48
Which of the following is unrequested e-mail that is sent to hundreds, thousands, or even millions of users?
A) USE
B) Spam
C) Trash
D) Crud
A) USE
B) Spam
C) Trash
D) Crud

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
49
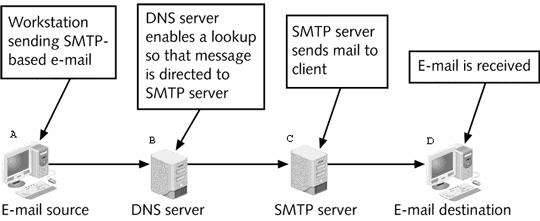 In the figure above, where is an attacker most likely to attempt to intercept e-mail transmissions?
In the figure above, where is an attacker most likely to attempt to intercept e-mail transmissions?A) Between A and B
B) Between B and C
C) Between C and D
D) At D

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
50
What is the maximum length of a message line when using SMTP only?
A) 100 characters
B) 256 characters
C) 500 characters
D) 1000 characters
A) 100 characters
B) 256 characters
C) 500 characters
D) 1000 characters

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
51
In 2002, which type of security was added to S/MIME?
A) 40-bit DES
B) 56-bit DES
C) 128-bit key triple DES
D) 168-bit key triple DES
A) 40-bit DES
B) 56-bit DES
C) 128-bit key triple DES
D) 168-bit key triple DES

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
52
In Microsoft Outlook, into which file types can you import messages?
A) Text file
B) Microsoft Access file
C) Microsoft Word file
D) Both a and b
E) Both b and c
A) Text file
B) Microsoft Access file
C) Microsoft Word file
D) Both a and b
E) Both b and c

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
53
Is the goal of SMTP to provide reliable and guaranteed message transport?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
54
Which of the following e-mail encryption method is recommended by many security professionals?
A) S/MIME
B) PGP
C) MIME
D) Both a and b
E) Both b and c
A) S/MIME
B) PGP
C) MIME
D) Both a and b
E) Both b and c

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
55
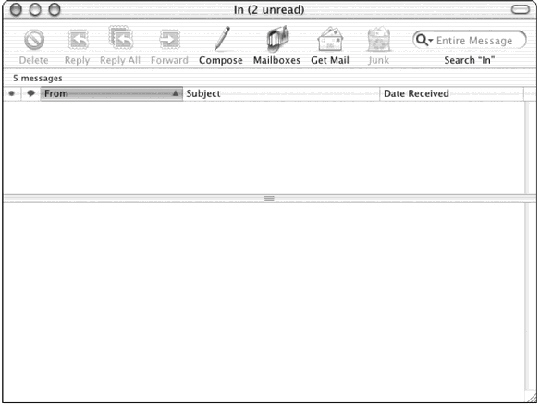 What is displayed in the figure above?
What is displayed in the figure above?A) Evolution Mail Summary view
B) Apple Mail
C) Outlook Express
D) Eudora

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
56
_____ provides extensions to the original SMTP address header information so that many different types of message content can be encoded for transport over the Internet.
A) MIME
B) POP3
C) PGP
D) PPL
A) MIME
B) POP3
C) PGP
D) PPL

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
57
What type of encoding is used with MIME?
A) Base16
B) Base32
C) Base64
D) Base128
A) Base16
B) Base32
C) Base64
D) Base128

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
58
Do direct attacks on SMTP typically come from client e-mail software such as Outlook, Evolution, or Apple Mail?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
59
In PGP, what CAST variable key length is available?
A) 32 bits
B) 56 bits
C) 128 bits
D) Both a and b
E) Both b and c
A) 32 bits
B) 56 bits
C) 128 bits
D) Both a and b
E) Both b and c

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
60
Does a DNS server convert a computer or domain name to an IP address, or an IP address to a computer or domain name, in a process called resolution?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
61
Using POP3 can be a disadvantage for ____________________, because messages are not previewed before they are downloaded.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
62
In an SMTP message, are the address header and the message text both encoded in 15-bit ASCII format?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
63
When an e-mail message is sent, a(n) ____________________ is used to place a new message into a particular user's mailbox.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
64
Sending a malicious SMTP message from a UNIX/Linux operating system is easier, because the attacker simply uses e-mail ____________________ options already built into UNIX/Linux.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
65
List four popular e-mail tools that are in use today.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
66
What six pieces of information are contained in a PGP digital certificate?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
67
Is IDEA well respected as a very secure patented block cipher encryption method?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
68
List five ways users can protect themselves from malicious e-mail attachments.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
69
Does PGP security rely strictly on the use of X.509 digital certificates?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
70
Does POP work through TCP port 109 for POP2 to enable an SMTP server to receive, store, and allow clients to retrieve their messages?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
71
When a computer sends e-mail, the message goes to a(n) ____________________ server that looks up the SMTP server on its network and enables the message to be directed to that server.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
72
When using IMAP, the ____________________ command chooses a folder from which to determine the available messages.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
73
In 1998, 40-bit and 56-bit DES encryption techniques were added to ____________________.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
74
E-mail encryption reduces the chance that someone can forge an e-mail, because both the sender and the recipient must be using the same encryption ____________________ and the same encryption method.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
75
An SMTP address header ____________________ contains the source and destination e-mail addresses.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
76
What are three e-mail security measures that organizations can take to protect its users and computers?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
77
If an organization decides to use an e-mail gateway with virus scanning software, what four features should they look for in the software?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
78
POP and IMAP are designed to enable ____________________ and retrieval of e-mail messages.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
79
Does all software that sends e-mail through the Internet use SMTP?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
80
SMTP does not require use of a(n) ____________________ and password for the remote system.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck


