Exam 10: E-Mail Security
Exam 1: Operating Systems Security: Keeping Computers and Networks Secure86 Questions
Exam 2: Viruses, Worms, and Malicious Software86 Questions
Exam 3: Security Through Authentication and Encryption86 Questions
Exam 4: Account-Based Security86 Questions
Exam 6: Firewalls and Border Security86 Questions
Exam 7: Physical and Network Topology Security86 Questions
Exam 8: Wireless Security86 Questions
Exam 9: Web, Remote Access, and VPN Security86 Questions
Exam 10: E-Mail Security86 Questions
Exam 11: Security Through Disaster Recovery86 Questions
Exam 12: Security Through Monitoring and Auditing86 Questions
Select questions type
POP and IMAP are designed to enable ____________________ and retrieval of e-mail messages.
Free
(Short Answer)
4.9/5  (31)
(31)
Correct Answer:
storage
In an SMTP address header, the _____ is the dotted-decimal address of the SMTP server.
Free
(Multiple Choice)
4.7/5  (35)
(35)
Correct Answer:
D
When an e-mail message is sent, what type of program is used to compose and read an e-mail message?
Free
(Multiple Choice)
4.8/5  (36)
(36)
Correct Answer:
A
In 1998, 40-bit and 56-bit DES encryption techniques were added to ____________________.
(Short Answer)
4.9/5  (41)
(41)
Using POP3 can be a disadvantage for ____________________, because messages are not previewed before they are downloaded.
(Short Answer)
4.9/5  (23)
(23)
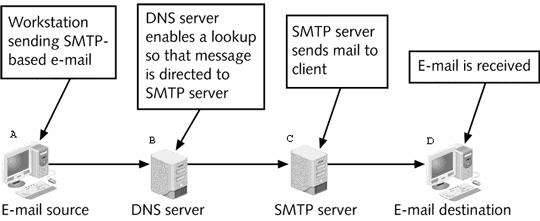 In the figure above, where is an attacker most likely to attempt to intercept e-mail transmissions?
In the figure above, where is an attacker most likely to attempt to intercept e-mail transmissions?
(Multiple Choice)
4.7/5  (42)
(42)
SMTP processes e-mail through a queue that serves as a _____ for users that connect to that server.
(Multiple Choice)
4.8/5  (38)
(38)
PGP enables the use of X.509 or PGP digital certificates, which are essentially public keys given to the recipient of the e-mail communication.
(True/False)
4.8/5  (34)
(34)
SMTP was proposed in 1982 by Jon Postel and began, in part, as an alternative to FTP for sending a file from one computer system to another.
(True/False)
4.7/5  (34)
(34)
Does all software that sends e-mail through the Internet use SMTP?
(True/False)
4.8/5  (37)
(37)
Which of the following encryption methods are supported by GPG?
(Multiple Choice)
4.9/5  (31)
(31)
Does a DNS server convert a computer or domain name to an IP address, or an IP address to a computer or domain name, in a process called resolution?
(True/False)
4.8/5  (37)
(37)
What four authentication methods can Apple Mail use for verifying access to an e-mail account?
(Essay)
4.7/5  (33)
(33)
List five pieces of information that an SMTP address header may contain.
(Essay)
4.7/5  (44)
(44)
SMTP does not require use of a(n) ____________________ and password for the remote system.
(Short Answer)
5.0/5  (38)
(38)
Which of the following is unrequested e-mail that is sent to hundreds, thousands, or even millions of users?
(Multiple Choice)
4.9/5  (29)
(29)
When using only SMTP, no line can be longer than 1000 characters.
(True/False)
4.9/5  (35)
(35)
What command does an attacker use to send the contents of a malicious file into the port-scanning software, directing the port scanner to send it to the target SMTP server on port 25?
(Multiple Choice)
4.8/5  (37)
(37)
Showing 1 - 20 of 86
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)