Deck 4: CIW v5 Security Essentials
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/48
Play
Full screen (f)
Deck 4: CIW v5 Security Essentials
1
Which of the following errors most commonly occurs when responding to a security breach?
A) Shutting down network access using the firewall, rather than the network router
B) Adhering to the company policy rather than determining actions based on the IT manager's input
C) Making snap judgments based on emotions, as opposed to company policy
D) Taking too much time to document the attack
A) Shutting down network access using the firewall, rather than the network router
B) Adhering to the company policy rather than determining actions based on the IT manager's input
C) Making snap judgments based on emotions, as opposed to company policy
D) Taking too much time to document the attack
C
2
You have determined that the company Web server has several vulnerabilities, including a buffer overflow that has resulted in an attack. The Web server uses PHP and has direct connections to an Oracle database server. It also uses many CGI scripts. Which of the following is the most effective way to respond to this attack?
A) Installing software updates for the Web server daemon
B) Using the POST method instead of the GET method for a Web form
C) Installing an intrusion detection service to monitor logins
D) Using the GET method instead of the POST method for a Web form
A) Installing software updates for the Web server daemon
B) Using the POST method instead of the GET method for a Web form
C) Installing an intrusion detection service to monitor logins
D) Using the GET method instead of the POST method for a Web form
A
3
What is the primary drawback of using symmetric-key encryption?
A) Key transport across a network
B) Speed of encryption
C) Denial-of-service attacks
D) Inability to support convergence traffic
A) Key transport across a network
B) Speed of encryption
C) Denial-of-service attacks
D) Inability to support convergence traffic
A
4
A new server has been placed on the network. You have been assigned to protect this server using a packet-filtering firewall. To comply with this request, you have enabled the following ruleset: 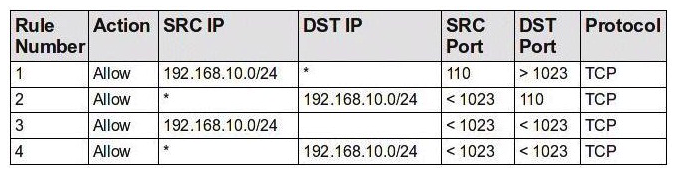 Which choice describes the next step to take now that this ruleset has been enabled?
Which choice describes the next step to take now that this ruleset has been enabled?
A) From the internal network, use your Web browser to determine whether all internal users can access the Web server.
B) From the internal network, use your e-mail client to determine whether all internal users can access the e-mail server.
C) From the external network, use your Web browser to determine whether all external users can access the Web server.
D) From the external network, use your e-mail client to determine whether all external users can access the e-mail server.
 Which choice describes the next step to take now that this ruleset has been enabled?
Which choice describes the next step to take now that this ruleset has been enabled?A) From the internal network, use your Web browser to determine whether all internal users can access the Web server.
B) From the internal network, use your e-mail client to determine whether all internal users can access the e-mail server.
C) From the external network, use your Web browser to determine whether all external users can access the Web server.
D) From the external network, use your e-mail client to determine whether all external users can access the e-mail server.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
5
A CGI application on the company's Web server has a bug written into it. This particular bug allows the application to write data into an area of memory that has not been properly allocated to the application. An attacker has created an application that takes advantage of this bug to obtain credit card information. Which of the following security threats is the attacker exploiting, and what can be done to solve the problem?
A) - Buffer overflow - Work with the Web developer to solve the problem
B) - SQL injection - Work with a database administrator to solve the problem
C) - Denial of service - Contact the organization that wrote the code for the Web server
D) - Man-in-the-middle attack - Contact the company auditor
A) - Buffer overflow - Work with the Web developer to solve the problem
B) - SQL injection - Work with a database administrator to solve the problem
C) - Denial of service - Contact the organization that wrote the code for the Web server
D) - Man-in-the-middle attack - Contact the company auditor

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
6
A security breach has occurred involving the company e-commerce server. Customer credit card data has been released to unauthorized third parties. Which of the following lists the appropriate parties to inform?
A) Shareholders, law enforcement agencies and company employees
B) Affected customers, credit card companies and law enforcement agencies
C) The Internet Service Provider, ICANN and company shareholders
D) External security consultants, company board members and affected customers
A) Shareholders, law enforcement agencies and company employees
B) Affected customers, credit card companies and law enforcement agencies
C) The Internet Service Provider, ICANN and company shareholders
D) External security consultants, company board members and affected customers

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
7
Which of the following is a typical target of a trojan on a Linux system?
A) Kernel modules
B) Shared libraries
C) Boot sector files
D) System32 DLL files
A) Kernel modules
B) Shared libraries
C) Boot sector files
D) System32 DLL files

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
8
A security breach has occurred in which a third party was able to obtain and misuse legitimate authentication information. After investigation, you determined that the specific cause for the breach was that end users have been placing their passwords underneath their keyboards. Which step will best help you resolve this problem?
A) Discipline specific end users as object lessons to the rest of the staff and reset passwords on all systems immediately.
B) Change all passwords on the company servers immediately and inform end users that their passwords will be changing on a regular basis.
C) Set passwords to expire at specific intervals and establish mandatory continual training sessions.
D) Inform end users that their passwords will be changing on a regular basis and require more complex passwords.
A) Discipline specific end users as object lessons to the rest of the staff and reset passwords on all systems immediately.
B) Change all passwords on the company servers immediately and inform end users that their passwords will be changing on a regular basis.
C) Set passwords to expire at specific intervals and establish mandatory continual training sessions.
D) Inform end users that their passwords will be changing on a regular basis and require more complex passwords.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
9
You have implemented a version of the Kerberos protocol for your network. What service does Kerberos primarily offer?
A) Authentication
B) Encryption
C) Non-repudiation
D) Data integrity
A) Authentication
B) Encryption
C) Non-repudiation
D) Data integrity

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
10
Which of the following is the most likely first step to enable a server to recover from a denial-of-service attack in which all hard disk data is lost?
A) Enable virtualization
B) Contact the backup service
C) Contact a disk recovery service
D) Rebuild your RAID 0 array
A) Enable virtualization
B) Contact the backup service
C) Contact a disk recovery service
D) Rebuild your RAID 0 array

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
11
A disgruntled employee has discovered that the company Web server is not protected against a particular buffer overflow vulnerability. The disgruntled employee has created an application to take advantage of this vulnerability and secretly obtain sensitive data from the Web server's hard disk. This application sends a set of packets to the Web server that causes it to present an unauthenticated terminal with root privileges. What is the name for this particular type of attack?
A) Man-in-the-middle attack
B) Trojan
C) Denial of service
D) Zero-day attack
A) Man-in-the-middle attack
B) Trojan
C) Denial of service
D) Zero-day attack

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
12
You are using a PKI solution that is based on Secure Sockets Layer (SSL). Which of the following describes the function of the asymmetric-key-encryption algorithm used?
A) It encrypts the symmetric key.
B) It encrypts all of the data.
C) It encrypts the hash code used for data integrity.
D) It encrypts the X.509 key.
A) It encrypts the symmetric key.
B) It encrypts all of the data.
C) It encrypts the hash code used for data integrity.
D) It encrypts the X.509 key.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
13
The most popular types of proxy-oriented firewalls operate at which layer of the OSI/RM?
A) Application layer
B) Network layer
C) Session layer
D) Transport layer
A) Application layer
B) Network layer
C) Session layer
D) Transport layer

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
14
You want to create a quick solution that allows you to obtain real-time login information for the administrative account on an LDAP server that you feel may become a target. Which of the following will accomplish this goal?
A) Reinstall the LDAP service on the server so that it is updated and more secure.
B) Install an application that creates checksums of the contents on the hard disk.
C) Create a login script for the administrative account that records logins to a separate server.
D) Create a dummy administrator account on the system so that a potential hacker is distracted from the real login account.
A) Reinstall the LDAP service on the server so that it is updated and more secure.
B) Install an application that creates checksums of the contents on the hard disk.
C) Create a login script for the administrative account that records logins to a separate server.
D) Create a dummy administrator account on the system so that a potential hacker is distracted from the real login account.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
15
At the beginning of an IPsec session, which activity occurs during the Internet Key Exchange (IKE)?
A) Determining the number of security associations
B) Negotiating the authentication method
C) Determining the network identification number
D) Negotiating the version of IP to be used
A) Determining the number of security associations
B) Negotiating the authentication method
C) Determining the network identification number
D) Negotiating the version of IP to be used

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
16
You purchased a network scanner six months ago. In spite of regularly conducting scans using this software, you have noticed that attackers have been able to compromise your servers over the last month. Which of the following is the most likely explanation for this problem?
A) The network scanner needs to be replaced.
B) The network scanner is no substitute for scans conducted by an individual.
C) The network scanner has a trojan.
D) The network scanner needs an update.
A) The network scanner needs to be replaced.
B) The network scanner is no substitute for scans conducted by an individual.
C) The network scanner has a trojan.
D) The network scanner needs an update.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
17
What is the primary use of hash (one-way) encryption in networking?
A) Signing files, for data integrity
B) Encrypting files, for data confidentiality
C) Key exchange, for user authentication
D) User authentication, for non-repudiation
A) Signing files, for data integrity
B) Encrypting files, for data confidentiality
C) Key exchange, for user authentication
D) User authentication, for non-repudiation

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
18
You have implemented a service on a Linux system that allows a user to read and edit resources. What is the function of this service?
A) Authentication
B) Data integrity
C) Access control
D) Intrusion detection
A) Authentication
B) Data integrity
C) Access control
D) Intrusion detection

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
19
Consider the following series of commands from a Linux system: iptables -A input -p icmp -s 0/0 -d 0/0 -j REJECT Which explanation best describes the impact of the resulting firewall ruleset?
A) Individuals on remote networks will no longer be able to use SSH to control internal network resources.
B) Internal hosts will not be able to ping each other using ICMP.
C) Stateful multi-layer inspection has been enabled.
D) Individuals on remote networks will not be able to use ping to troubleshoot connections.
A) Individuals on remote networks will no longer be able to use SSH to control internal network resources.
B) Internal hosts will not be able to ping each other using ICMP.
C) Stateful multi-layer inspection has been enabled.
D) Individuals on remote networks will not be able to use ping to troubleshoot connections.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
20
Which of the following will best help you ensure a database server can withstand a recently discovered vulnerability?
A) Updating the company vulnerability scanner and conducting a new scan
B) Adding a buffer overflow rule to the intrusion detection system
C) Reconfiguring the firewall
D) Installing a system update
A) Updating the company vulnerability scanner and conducting a new scan
B) Adding a buffer overflow rule to the intrusion detection system
C) Reconfiguring the firewall
D) Installing a system update

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
21
Which of the following can help you authoritatively trace a network flooding attack?
A) Your ISP
B) Firewall logs
C) Router logs
D) Ping
A) Your ISP
B) Firewall logs
C) Router logs
D) Ping

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
22
Which tool is best suited for identifying applications and code on a Web server that can lead to a SQL injection attack?
A) A vulnerability scanner
B) A packet sniffer
C) An intrusion-detection system
D) A network switch
A) A vulnerability scanner
B) A packet sniffer
C) An intrusion-detection system
D) A network switch

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
23
You want to create a certificate for use in a Secure Sockets Layer (SSL) session. Which of the following is responsible for verifying the identity of an individual and also issuing the certificate?
A) Kerberos server
B) Certificate authority
C) Certificate revocation entity
D) Certificate repository
A) Kerberos server
B) Certificate authority
C) Certificate revocation entity
D) Certificate repository

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
24
Which of the following applications can help determine whether a denial-of-service attack is occurring against a network host?
A) The netstat command and a packet sniffer
B) The ps command and a network scanner
C) The ping command and User Manager
D) The iptables command and Windows desktop firewall
A) The netstat command and a packet sniffer
B) The ps command and a network scanner
C) The ping command and User Manager
D) The iptables command and Windows desktop firewall

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
25
Your organization has made a particularly unpopular policy decision. Your supervisor fears that a series of attacks may occur as a result. You have been assigned to increase automated auditing on a server. When fulfilling this request, which of the following resources should you audit the most aggressively?
A) Authentication databases, including directory servers
B) Intrusion detection systems, especially those placed on sensitive networks
C) Log files on firewall systems
D) Firewall settings for desktop systems
A) Authentication databases, including directory servers
B) Intrusion detection systems, especially those placed on sensitive networks
C) Log files on firewall systems
D) Firewall settings for desktop systems

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
26
Which of the following is a common problem, yet commonly overlooked, in regards to physical security in server rooms?
A) Firewalls that do not have a dedicated backup
B) False ceilings
C) Logic bombs
D) Biometric malfunctions
A) Firewalls that do not have a dedicated backup
B) False ceilings
C) Logic bombs
D) Biometric malfunctions

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
27
Which of the following is the primary weakness of symmetric-key encryption?
A) Data encrypted using symmetric-key encryption is subject to corruption during transport.
B) Symmetric-key encryption operates slower than asymmetric-key encryption.
C) Symmetric-key encryption does not provide the service of data confidentiality.
D) Keys created using symmetric-key encryption are difficult to distribute securely.
A) Data encrypted using symmetric-key encryption is subject to corruption during transport.
B) Symmetric-key encryption operates slower than asymmetric-key encryption.
C) Symmetric-key encryption does not provide the service of data confidentiality.
D) Keys created using symmetric-key encryption are difficult to distribute securely.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
28
You are creating an information security policy for your company. Which of the following activities will help you focus on creating policies for the most important resources?
A) Auditing the firewall
B) Implementing non-repudiation
C) Logging users
D) Classifying systems
A) Auditing the firewall
B) Implementing non-repudiation
C) Logging users
D) Classifying systems

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
29
Which choice lists typical firewall functions?
A) Creating a VLAN and configuring the intrusion-detection system
B) Issuing alerts and limiting host access
C) Logging traffic and creating a choke point
D) Implementing the security policy and scanning the internal network
A) Creating a VLAN and configuring the intrusion-detection system
B) Issuing alerts and limiting host access
C) Logging traffic and creating a choke point
D) Implementing the security policy and scanning the internal network

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
30
A new video conferencing device has been installed on the network. You have been assigned to troubleshoot a connectivity problem between remote workers and the central company. Specifically, remote workers are having problems making any connection at all. Which technique will most likely help you solve this problem while retaining the existing level of security at the firewall?
A) Deny all use of UDP above Port 1024.
B) Configure the firewall to provide VPN access.
C) Configure a second network connection directly to the video conferencing device.
D) Allow all use of UDP below Port 1024.
A) Deny all use of UDP above Port 1024.
B) Configure the firewall to provide VPN access.
C) Configure a second network connection directly to the video conferencing device.
D) Allow all use of UDP below Port 1024.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
31
Which of the following describes the practice of stateful multi-layer inspection?
A) Using a VLAN on a firewall to enable masquerading of private IP addresses
B) Prioritizing voice and video data to reduce congestion
C) Inspecting packets in all layers of the OSI/RM with a packet filter
D) Using Quality of Service (QoS) on a proxy-oriented firewall
A) Using a VLAN on a firewall to enable masquerading of private IP addresses
B) Prioritizing voice and video data to reduce congestion
C) Inspecting packets in all layers of the OSI/RM with a packet filter
D) Using Quality of Service (QoS) on a proxy-oriented firewall

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
32
Which of the following details should be included in documentation of an attack?
A) An overview of the security policy and suggestions for the next response plan
B) Estimates of how much the attack cost the company, and a list of the applications used by the attacker
C) The time and date of the attack, and the names of employees who were contacted during the response
D) The network resources involved in the attack, and recommendations for thwarting future attacks
A) An overview of the security policy and suggestions for the next response plan
B) Estimates of how much the attack cost the company, and a list of the applications used by the attacker
C) The time and date of the attack, and the names of employees who were contacted during the response
D) The network resources involved in the attack, and recommendations for thwarting future attacks

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
33
Jason is attempting to gain unauthorized access to a corporate server by running a program that enters passwords from a long list of possible passwords. Which type of attack is this?
A) Brute force
B) Denial of service
C) Botnet
D) Buffer overflow
A) Brute force
B) Denial of service
C) Botnet
D) Buffer overflow

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
34
You have determined that an attack is currently underway on your database server. An attacker is currently logged in, modifying data. You want to preserve logs, caching and other data on this affected server. Which of the following actions will best allow you to stop the attack and still preserve data?
A) Pull the server network cable
B) Shut down the server
C) Back up the system logs
D) Force an instant password reset
A) Pull the server network cable
B) Shut down the server
C) Back up the system logs
D) Force an instant password reset

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
35
Which of the following activities is the most effective at keeping the actions of nae end users from putting the company's physical and logicalWhich of the following activities is the most effective at keeping the actions of na?e end users from putting the company's physical and logical resources at risk?
A) Configuring network intrusion-detection software to monitor end user activity
B) Conducting a training session at the time of hire
C) Reconfiguring the network firewall
D) Assembling a team of security professionals to monitor the network
A) Configuring network intrusion-detection software to monitor end user activity
B) Conducting a training session at the time of hire
C) Reconfiguring the network firewall
D) Assembling a team of security professionals to monitor the network

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
36
You have just deployed an application that uses hash-based checksums to monitor changes in the configuration scripts of a database server that is accessible via the Internet. Which of the following is a primary concern for this solution?
A) The extra hard disk space required to store the database of checksums
B) The amount of memory remaining now that the checksum-based application is running
C) The possibility of a buffer overflow attack leading to a security breach
D) The security of the checksum database on a read-only media format
A) The extra hard disk space required to store the database of checksums
B) The amount of memory remaining now that the checksum-based application is running
C) The possibility of a buffer overflow attack leading to a security breach
D) The security of the checksum database on a read-only media format

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
37
Which of the following is a primary auditing activity?
A) Encrypting data files
B) Changing login accounts
C) Checking log files
D) Configuring the firewall
A) Encrypting data files
B) Changing login accounts
C) Checking log files
D) Configuring the firewall

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
38
Which algorithm can use a 128-bit key, and has been adopted as a standard by various governments and corporations?
A) MARS
B) RC2
C) Advanced Encryption Standard (AES)
D) International Data Encryption Algorithm (IDEA)
A) MARS
B) RC2
C) Advanced Encryption Standard (AES)
D) International Data Encryption Algorithm (IDEA)

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
39
Consider the following image of a packet capture: 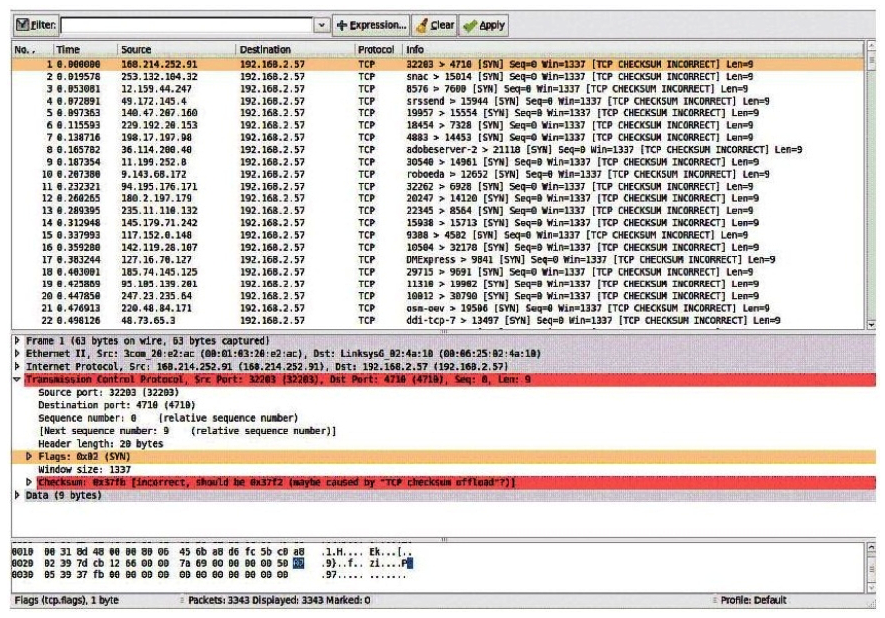 This packet capture has recorded two types of attacks. Which choice lists both attack types?
This packet capture has recorded two types of attacks. Which choice lists both attack types?
A) A dictionary attack and a worm-based attackA.A dictionary attack and a worm-based attack
B) A syn flood attack and a spoofing attackB.A syn flood attack and a spoofing attack
C) A worm attack and a botnet attack C.A worm attack and a botnet attack
D) A SQL injection attack and a virus attackD.A SQL injection attack and a virus attack
 This packet capture has recorded two types of attacks. Which choice lists both attack types?
This packet capture has recorded two types of attacks. Which choice lists both attack types?A) A dictionary attack and a worm-based attackA.A dictionary attack and a worm-based attack
B) A syn flood attack and a spoofing attackB.A syn flood attack and a spoofing attack
C) A worm attack and a botnet attack C.A worm attack and a botnet attack
D) A SQL injection attack and a virus attackD.A SQL injection attack and a virus attack

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
40
Consider the following image: 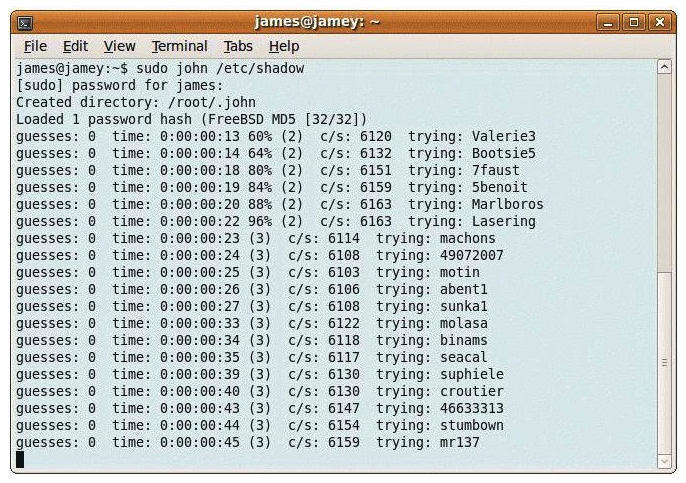 From the information in this image, what type of attack is occurring?
From the information in this image, what type of attack is occurring?
A) A man-in-the-middle attack
B) A brute-force attack
C) A connection-hijacking attackC.A connection-hijacking attack
D) A spoofing attackD.A spoofing attack
 From the information in this image, what type of attack is occurring?
From the information in this image, what type of attack is occurring?A) A man-in-the-middle attack
B) A brute-force attack
C) A connection-hijacking attackC.A connection-hijacking attack
D) A spoofing attackD.A spoofing attack

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
41
Which of the following is a primary weakness of asymmetric-key encryption?
A) It is slow because it requires extensive calculations by the computer.
B) It can lead to the corruption of encrypted data during network transfer.
C) It is reliant on the Secure Sockets Layer (SSL) standard, which has been compromised.
D) It is difficult to transfer any portion of an asymmetric key securely.
A) It is slow because it requires extensive calculations by the computer.
B) It can lead to the corruption of encrypted data during network transfer.
C) It is reliant on the Secure Sockets Layer (SSL) standard, which has been compromised.
D) It is difficult to transfer any portion of an asymmetric key securely.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
42
At what layer of the OSI/RM does a packet filter operate?
A) Layer 1
B) Layer 3
C) Layer 5
D) Layer 7
A) Layer 1
B) Layer 3
C) Layer 5
D) Layer 7

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
43
What is the primary strength of symmetric-key encryption?
A) It allows easy and secure exchange of the secret key.
B) It creates a ash?of a text, enabling data integrity.It creates a ?ash?of a text, enabling data integrity.
C) It can encrypt large amounts of data very quickly.
D) It provides non-repudiation services more efficiently than asymmetric-key encryption.
A) It allows easy and secure exchange of the secret key.
B) It creates a ash?of a text, enabling data integrity.It creates a ?ash?of a text, enabling data integrity.
C) It can encrypt large amounts of data very quickly.
D) It provides non-repudiation services more efficiently than asymmetric-key encryption.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
44
Consider the following diagram: 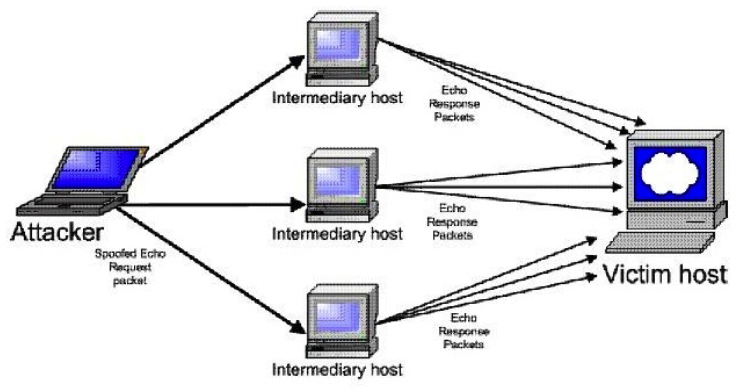 Which type of attack is occurring?
Which type of attack is occurring?
A) Polymorphic virus-based attack
B) Denial-of-service attack
C) Distributed denial-of-service attack
D) Man-in-the-middle attack using a packet sniffer
 Which type of attack is occurring?
Which type of attack is occurring?A) Polymorphic virus-based attack
B) Denial-of-service attack
C) Distributed denial-of-service attack
D) Man-in-the-middle attack using a packet sniffer

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
45
Which of the following is most likely to address a problem with an operating system's ability to withstand an attack that attempts to exploit a buffer overflow?
A) Firewall
B) Software update
C) Intrusion detection system
D) Network scanner
A) Firewall
B) Software update
C) Intrusion detection system
D) Network scanner

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
46
Consider the following diagram involving two firewall-protected networks: 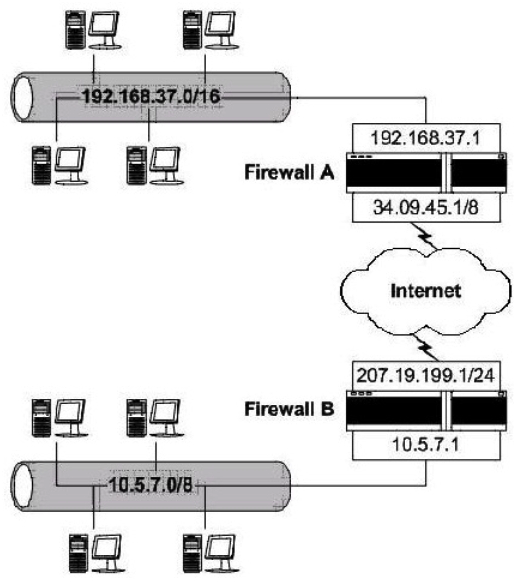 Which of the following is necessary for each of the firewalls to allow private IP addresses to be passed on to the Internet?
Which of the following is necessary for each of the firewalls to allow private IP addresses to be passed on to the Internet?
A) Chargeback
B) Stateful multi-layer inspection
C) Masquerading
D) DMZ creation
 Which of the following is necessary for each of the firewalls to allow private IP addresses to be passed on to the Internet?
Which of the following is necessary for each of the firewalls to allow private IP addresses to be passed on to the Internet?A) Chargeback
B) Stateful multi-layer inspection
C) Masquerading
D) DMZ creation

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
47
You have been assigned to provide security measures for your office's reception area. Although the company needs to provide security measures, costs must be kept to a minimum. Which of the following tools is the most appropriate choice?
A) Firewall
B) Intrusion-detection system
C) Camera
D) Security guard
A) Firewall
B) Intrusion-detection system
C) Camera
D) Security guard

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
48
Consider the following image of a packet capture: 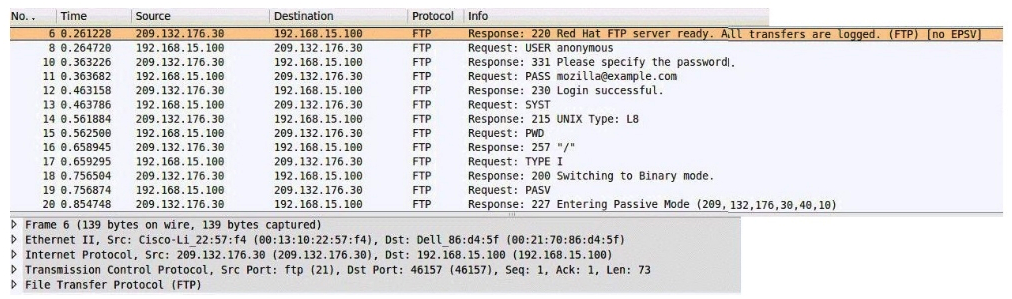
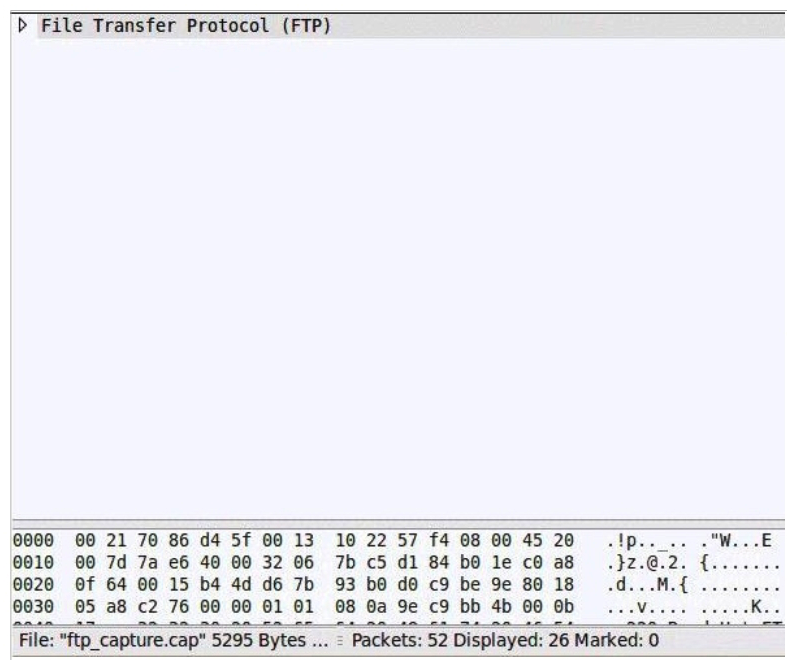 Which of the following best describes the protocol used, along with its primary benefit?
Which of the following best describes the protocol used, along with its primary benefit?
A) It is a passive FTP session, which is easier for firewalls to process.
B) It is an active FTP session, which is necessary in order to support IPv6.
C) It is an extended passive FTP session, which is necessary to support IPv6.
D) It is an active FTP session, which is supported by all FTP clients.

 Which of the following best describes the protocol used, along with its primary benefit?
Which of the following best describes the protocol used, along with its primary benefit?A) It is a passive FTP session, which is easier for firewalls to process.
B) It is an active FTP session, which is necessary in order to support IPv6.
C) It is an extended passive FTP session, which is necessary to support IPv6.
D) It is an active FTP session, which is supported by all FTP clients.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck


