Exam 4: CIW v5 Security Essentials
Exam 1: CIW v5 Site Designer83 Questions
Exam 2: CIW E-Commerce Designer86 Questions
Exam 3: CIW v5 Database Design Specialist75 Questions
Exam 4: CIW v5 Security Essentials48 Questions
Exam 5: CIW Web Foundations Associate138 Questions
Exam 6: CIW Internet Business Associate14 Questions
Exam 7: CIW Site Development Associate15 Questions
Exam 8: CIW Network Technology Associate8 Questions
Exam 9: CIW User Interface Designer49 Questions
Exam 10: CIW JavaScript Specialist30 Questions
Select questions type
Which of the following will best help you ensure a database server can withstand a recently discovered vulnerability?
Free
(Multiple Choice)
4.7/5  (30)
(30)
Correct Answer:
D
Which of the following can help you authoritatively trace a network flooding attack?
Free
(Multiple Choice)
4.8/5  (34)
(34)
Correct Answer:
A
You have just deployed an application that uses hash-based checksums to monitor changes in the configuration scripts of a database server that is accessible via the Internet. Which of the following is a primary concern for this solution?
Free
(Multiple Choice)
4.8/5  (29)
(29)
Correct Answer:
D
A disgruntled employee has discovered that the company Web server is not protected against a particular buffer overflow vulnerability. The disgruntled employee has created an application to take advantage of this vulnerability and secretly obtain sensitive data from the Web server's hard disk. This application sends a set of packets to the Web server that causes it to present an unauthenticated terminal with root privileges. What is the name for this particular type of attack?
(Multiple Choice)
4.9/5  (36)
(36)
Consider the following image: 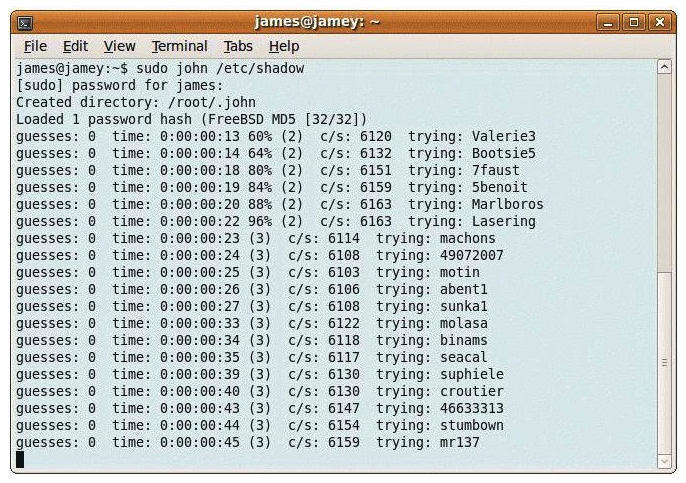 From the information in this image, what type of attack is occurring?
From the information in this image, what type of attack is occurring?
(Multiple Choice)
4.8/5  (28)
(28)
The most popular types of proxy-oriented firewalls operate at which layer of the OSI/RM?
(Multiple Choice)
4.7/5  (27)
(27)
Consider the following series of commands from a Linux system: iptables -A input -p icmp -s 0/0 -d 0/0 -j REJECT Which explanation best describes the impact of the resulting firewall ruleset?
(Multiple Choice)
4.8/5  (30)
(30)
Which of the following is a primary weakness of asymmetric-key encryption?
(Multiple Choice)
4.7/5  (30)
(30)
Which of the following details should be included in documentation of an attack?
(Multiple Choice)
4.7/5  (37)
(37)
You have implemented a version of the Kerberos protocol for your network. What service does Kerberos primarily offer?
(Multiple Choice)
4.8/5  (43)
(43)
Consider the following image of a packet capture: 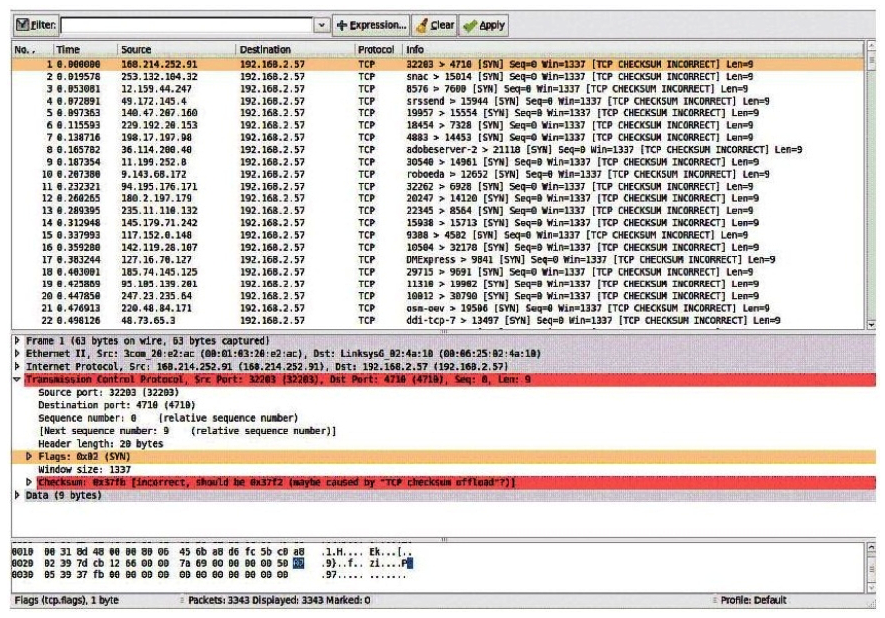 This packet capture has recorded two types of attacks. Which choice lists both attack types?
This packet capture has recorded two types of attacks. Which choice lists both attack types?
(Multiple Choice)
4.9/5  (30)
(30)
Which of the following errors most commonly occurs when responding to a security breach?
(Multiple Choice)
4.8/5  (35)
(35)
Which of the following activities is the most effective at keeping the actions of nae end users from putting the company's physical and logicalWhich of the following activities is the most effective at keeping the actions of na?e end users from putting the company's physical and logical resources at risk?
(Multiple Choice)
4.8/5  (36)
(36)
Which algorithm can use a 128-bit key, and has been adopted as a standard by various governments and corporations?
(Multiple Choice)
4.9/5  (44)
(44)
Your organization has made a particularly unpopular policy decision. Your supervisor fears that a series of attacks may occur as a result. You have been assigned to increase automated auditing on a server. When fulfilling this request, which of the following resources should you audit the most aggressively?
(Multiple Choice)
4.8/5  (41)
(41)
At the beginning of an IPsec session, which activity occurs during the Internet Key Exchange (IKE)?
(Multiple Choice)
4.8/5  (33)
(33)
You are creating an information security policy for your company. Which of the following activities will help you focus on creating policies for the most important resources?
(Multiple Choice)
4.8/5  (30)
(30)
Showing 1 - 20 of 48
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)