Deck 6: Isilon Solutions and Design Specialist for Technology Architects
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/62
Play
Full screen (f)
Deck 6: Isilon Solutions and Design Specialist for Technology Architects
1
LUNs belonging to an ESXi cluster were encapsulated behind VPLEX. What information must be shared with the ESXi administrator so that they can re-discover the datastore and the RDM LUNs?
A) Virtual volume VPD
B) UUID of back-end LUN
C) VML ID
D) WWN: WWPN
A) Virtual volume VPD
B) UUID of back-end LUN
C) VML ID
D) WWN: WWPN
Virtual volume VPD
2
What is a VPLEX RAID-0 device?
A) Device that stripes data beneath a top-level device
B) Device that concatenates data on a top-level device
C) Extent that concatenates data on a top-level device
D) Extent that stripes data beneath a top-level device
A) Device that stripes data beneath a top-level device
B) Device that concatenates data on a top-level device
C) Extent that concatenates data on a top-level device
D) Extent that stripes data beneath a top-level device
Device that stripes data beneath a top-level device
3
What is a feature of GeoSynchrony 6.0 with respect to service account login to the VPlexcli?
A) Service account requires authentication to the Linux shell VPlexcli requires an RSA token
B) Service account requires no authentication to the Linux shell VPlexcli requires certificate authority
C) VPlexcli requires authentication through LDAP
D) Service account requires authentication only to the Linux shell VPlexcli does not require an extra authentication step
A) Service account requires authentication to the Linux shell VPlexcli requires an RSA token
B) Service account requires no authentication to the Linux shell VPlexcli requires certificate authority
C) VPlexcli requires authentication through LDAP
D) Service account requires authentication only to the Linux shell VPlexcli does not require an extra authentication step
Service account requires authentication only to the Linux shell VPlexcli does not require an extra authentication step
4
Which type of VPLEX statistic provides an instantaneous value that displays CPU utilization and memory utilization?
A) Buckets
B) Counters
C) Readings
D) Journal Lag
A) Buckets
B) Counters
C) Readings
D) Journal Lag

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
5
What condition would prevent volume expansion?
A) Migration occurring on the volume
B) Volume not belonging to a consistency group
C) Metadata volume being backed up
D) Logging volume in re-synchronization state
A) Migration occurring on the volume
B) Volume not belonging to a consistency group
C) Metadata volume being backed up
D) Logging volume in re-synchronization state

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
6
What is a consideration for using a VPLEX logging volume?
A) Must be created on each VPLEX cluster before creating a distributed device
B) Automatically provisioned at each VPLEX cluster when the distributed device is created
C) A distributed device must be created before a logging volume can be created
D) VIAS can be used to create a logging volume at each cluster
A) Must be created on each VPLEX cluster before creating a distributed device
B) Automatically provisioned at each VPLEX cluster when the distributed device is created
C) A distributed device must be created before a logging volume can be created
D) VIAS can be used to create a logging volume at each cluster

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
7
What is a supported geometry for a VPLEX device?
A) JBOD
B) RAID-5
C) RAID-C
D) 2-1 mapping
A) JBOD
B) RAID-5
C) RAID-C
D) 2-1 mapping

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
8
Which protocol does the service laptop use to communicate with and maintain an EMC VPLEX environment?
A) SSH
B) SNMP
C) Telnet
D) UDP
A) SSH
B) SNMP
C) Telnet
D) UDP

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
9
A company has deployed a VPLEX Metro protecting two applications without Cluster Witness: -App1 distributed virtual volumes are added to CG1, which has detach-rule set cluster-1 as winner -App2 distributed virtual volumes are added to CG2, which has detach-rule set cluster-2 as winner What should be the consequence if there is a WAN COM failure for an extended period?
A) I/O for CG1 is suspended at cluster -1; I/O is serviced at cluster-2 I/O for CG2 is serviced at cluster -1; I/O is suspended at cluster-2
B) I/O for CG2 is serviced at cluster -2; I/O is suspended at cluster-1
C) I/O for CG1 is detached at cluster -1; I/O is serviced at cluster-2 I/O for CG2 is detached at cluster -2; I/O is serviced at cluster-1
D) I/O for CG1 is serviced at cluster -1; I/O is suspended at cluster-2 I/O is serviced for CG2 at cluster -2; I/O is suspended at cluster-1
A) I/O for CG1 is suspended at cluster -1; I/O is serviced at cluster-2 I/O for CG2 is serviced at cluster -1; I/O is suspended at cluster-2
B) I/O for CG2 is serviced at cluster -2; I/O is suspended at cluster-1
C) I/O for CG1 is detached at cluster -1; I/O is serviced at cluster-2 I/O for CG2 is detached at cluster -2; I/O is serviced at cluster-1
D) I/O for CG1 is serviced at cluster -1; I/O is suspended at cluster-2 I/O is serviced for CG2 at cluster -2; I/O is suspended at cluster-1

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
10
What is the maximum number of virtual volumes that can be placed into a single consistency group?
A) 800
B) 900
C) 1000
D) 1100
A) 800
B) 900
C) 1000
D) 1100

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
11
Refer to the exhibit. 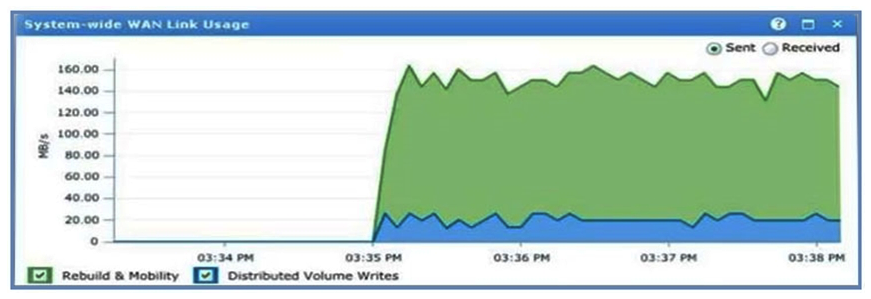 A virtual volume created on a distributed device is experiencing performance problems. The virtual volume is in a storage view in Cluster-1. What could be the issue?
A virtual volume created on a distributed device is experiencing performance problems. The virtual volume is in a storage view in Cluster-1. What could be the issue?
A) There is storage volume contention on Cluster-2
B) A WAN COM failure has occurred
C) Distributed device I/O is exceeding WAN COM bandwidth
D) Device mobility jobs are moving data across the WAN COM
 A virtual volume created on a distributed device is experiencing performance problems. The virtual volume is in a storage view in Cluster-1. What could be the issue?
A virtual volume created on a distributed device is experiencing performance problems. The virtual volume is in a storage view in Cluster-1. What could be the issue?A) There is storage volume contention on Cluster-2
B) A WAN COM failure has occurred
C) Distributed device I/O is exceeding WAN COM bandwidth
D) Device mobility jobs are moving data across the WAN COM

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
12
What steps are performed during extent and device migration?
A) Start, commit, clean, and remove
B) Start, commit, clean, and terminate
C) Create, commit, clean, and terminate
D) Create, clean, commit, and remove
A) Start, commit, clean, and remove
B) Start, commit, clean, and terminate
C) Create, commit, clean, and terminate
D) Create, clean, commit, and remove

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
13
How can a VPLEX storage administrator manage array-based attributes?
A) Device tiers
B) Storage tiers
C) Volume tiers
D) Extent tiers
A) Device tiers
B) Storage tiers
C) Volume tiers
D) Extent tiers

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
14
What is required before a host can detect the virtual volumes presented by the VPLEX?
A) Virtual volumes can only be detected after a reboot
B) RAID configuration must be enabled for Virtual volumes
C) EZ Provisioning wizard must be run on the host
D) Host must initiate a bus-scan of the HBAs
A) Virtual volumes can only be detected after a reboot
B) RAID configuration must be enabled for Virtual volumes
C) EZ Provisioning wizard must be run on the host
D) Host must initiate a bus-scan of the HBAs

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
15
In addition to Active Directory, which other directory service can VPLEX integrate with for user authentication?
A) LDAP
B) NIS
C) NDS
D) PAM
A) LDAP
B) NIS
C) NDS
D) PAM

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
16
Why is it EMC best practice that each back-end LUN has a connection to all the A-directors and to all the B-directors in the VPLEX cluster?
A) Prevents data unavailability during a non-disruptive upgrade
B) Reduces the number of ITLs
C) Ensures writes are mirrored on director local cache
D) Optimizes global read cache
A) Prevents data unavailability during a non-disruptive upgrade
B) Reduces the number of ITLs
C) Ensures writes are mirrored on director local cache
D) Optimizes global read cache

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
17
To which VPLEX component does the SNMP management station connect to gather statistics?
A) VPLEX Witness
B) Management server
C) Director-A
D) Director-B
A) VPLEX Witness
B) Management server
C) Director-A
D) Director-B

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
18
What is the purpose of issuing the batch-migrate check-plan command?
A) Determines if there is currently enough back-end bandwidth
B) Determines if the front-end IO rate is below the predetermined threshold
C) Verifies that the target devices have no virtual volumes configured
D) Verifies that the source devices are not in a storage view
A) Determines if there is currently enough back-end bandwidth
B) Determines if the front-end IO rate is below the predetermined threshold
C) Verifies that the target devices have no virtual volumes configured
D) Verifies that the source devices are not in a storage view

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
19
What can be used to monitor VPLEX performance parameters?
A) VPLEX Cluster Witness
B) Unisphere Performance Monitor Dashboard
C) EMC SolVe Desktop
D) EMCREPORTS utility
A) VPLEX Cluster Witness
B) Unisphere Performance Monitor Dashboard
C) EMC SolVe Desktop
D) EMCREPORTS utility

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
20
A storage administrator wants to view additional performance metrics for their VPLEX cluster. The administrator runs the report create-monitors command to help with this task.
A) Disks, ports, and volumes
B) Disks, volumes, and hosts
C) Disks, storage views, and ports
D) Disks, initiators, and storage volumes
A) Disks, ports, and volumes
B) Disks, volumes, and hosts
C) Disks, storage views, and ports
D) Disks, initiators, and storage volumes

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
21
You meet a customer for the first time. They explain that their current environment for NAS does not meet their needs. You want to make sure that Isilon is a good fit for their needs. What would be a good prequalifying question to ask?
A) What protocols are accessing your NAS?
B) What application are you using to create directories?
C) Is your datacenter ISO9001 compliant?
D) How many users are in your Directory Services?
A) What protocols are accessing your NAS?
B) What application are you using to create directories?
C) Is your datacenter ISO9001 compliant?
D) How many users are in your Directory Services?

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
22
When is expanding a virtual volume using the Storage Volume expansion method a valid option?
A) Virtual volume previously expanded by adding extents or devices
B) Virtual volume is mapped 1:1 to the underlying storage volume
C) Virtual volume is a metadata volume
D) Virtual volume has minor problems, as reported by health-check
A) Virtual volume previously expanded by adding extents or devices
B) Virtual volume is mapped 1:1 to the underlying storage volume
C) Virtual volume is a metadata volume
D) Virtual volume has minor problems, as reported by health-check

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
23
How are physical ports numbered for each I/O module in VS6 VPLEX hardware?
A) Director-A: 0 to 3 from the top Director-B: 0 to 3 from the bottom
B) Director-A: 1 to 4 from the bottom Director-B: 1 to 4 from the top
C) Director-A: 0 to 3 from the bottom Director-B: 0 to 3 from the top
D) Director-A: 1 to 4 from the top Director-B:1 to 4 from the bottom
A) Director-A: 0 to 3 from the top Director-B: 0 to 3 from the bottom
B) Director-A: 1 to 4 from the bottom Director-B: 1 to 4 from the top
C) Director-A: 0 to 3 from the bottom Director-B: 0 to 3 from the top
D) Director-A: 1 to 4 from the top Director-B:1 to 4 from the bottom

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
24
A company has just installed a new VPLEX cluster into their storage environment with numerous existing storage arrays. They need to present the host's existing data from the VPLEX cluster. Which method should be used to perform this operation?
A) Encapsulate
B) Distribute
C) Stripe
D) Concatenate
A) Encapsulate
B) Distribute
C) Stripe
D) Concatenate

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
25
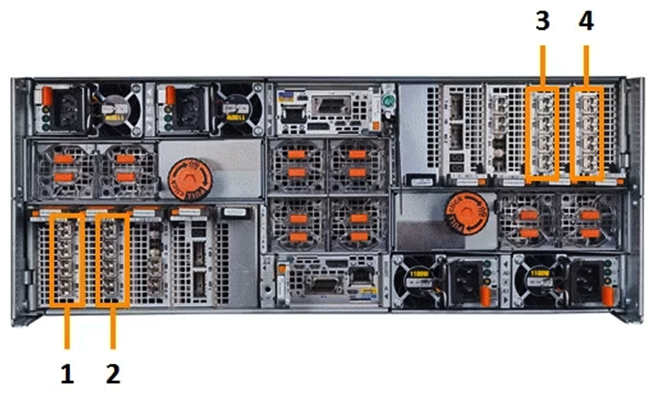 Which number in the exhibit highlights the Director-B front-end ports?
Which number in the exhibit highlights the Director-B front-end ports?A) 1
B) 2
C) 3
D) 4

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
26
Which command is used to display available statistics for monitoring VPLEX?
A) monitor stat-list
B) monitor add-sink
C) monitor collect
D) monitor create
A) monitor stat-list
B) monitor add-sink
C) monitor collect
D) monitor create

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
27
Which statement applies to a VPLEX device?
A) Application of a RAID topology to one or more extents
B) An extent from a claimed LUN
C) Claimed LUN from an array
D) Storage presented to one or more hosts
A) Application of a RAID topology to one or more extents
B) An extent from a claimed LUN
C) Claimed LUN from an array
D) Storage presented to one or more hosts

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
28
At which layer of the director IO stack are local and distributed mirroring managed?
A) Coherent Cache
B) Storage Volume
C) Device Virtualization
D) Storage View
A) Coherent Cache
B) Storage Volume
C) Device Virtualization
D) Storage View

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
29
A storage administrator has been tasked with migrating a Microsoft SQL Server and its native EMC VNX LUNs behind a VPLEX Local cluster. However, in planning for future application growth, the database administrator wants to be able to expand the storage volumes. Based on this information, which geometry should be selected during encapsulation?
A) Stripped MetaLUN
B) 1:1 Mapping
C) RAID-0
D) RAID-C
A) Stripped MetaLUN
B) 1:1 Mapping
C) RAID-0
D) RAID-C

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
30
Which type of mobility is used to move data to a remote cluster in a VPLEX Metro?
A) Device
B) Extent
C) MetroPoint
D) Virtual volume
A) Device
B) Extent
C) MetroPoint
D) Virtual volume

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
31
What is a valid target for a device data migration in VPLEX?
A) Distributed device
B) Device with no existing virtual volume
C) Device with an existing virtual volume
D) Extent
A) Distributed device
B) Device with no existing virtual volume
C) Device with an existing virtual volume
D) Extent

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
32
What is a consideration when using VPLEX RecoverPoint enabled consistency groups?
A) Repository volume and journal volumes must be in different consistency groups.
B) Local virtual volumes and distributed virtual volumes can be in the same consistency group.
C) Local copy volumes and production volumes must reside in separate consistency groups.
D) Production and local copy journals must be in different consistency groups.
A) Repository volume and journal volumes must be in different consistency groups.
B) Local virtual volumes and distributed virtual volumes can be in the same consistency group.
C) Local copy volumes and production volumes must reside in separate consistency groups.
D) Production and local copy journals must be in different consistency groups.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
33
You set up a meeting to gather information on a new project with the IT manager and plan to use a workflow profile assessment (WPA) to document the requirements. Why is it recommended to talk to as many stakeholders as possible?
A) Helps downstream personnel, such as implementation and delivery, to have a clearer understanding of the requirements.
B) Completing this document gives sales a list of who the stakeholders are at customer site.
C) Using workflow profile enables sales to take this information to EMC consulting for review to validate the configuration.
D) Using the WPA tool will give you the best "big picture" to see things such as block size, de-dupe, file size and volumes.
A) Helps downstream personnel, such as implementation and delivery, to have a clearer understanding of the requirements.
B) Completing this document gives sales a list of who the stakeholders are at customer site.
C) Using workflow profile enables sales to take this information to EMC consulting for review to validate the configuration.
D) Using the WPA tool will give you the best "big picture" to see things such as block size, de-dupe, file size and volumes.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
34
What is required to add a RecoverPoint cluster to VPLEX?
A) RecoverPoint cluster ID
B) RecoverPoint cluster name
C) RecoverPoint cluster Management IP address
D) RecoverPoint cluster license number
A) RecoverPoint cluster ID
B) RecoverPoint cluster name
C) RecoverPoint cluster Management IP address
D) RecoverPoint cluster license number

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
35
Refer to the exhibit. 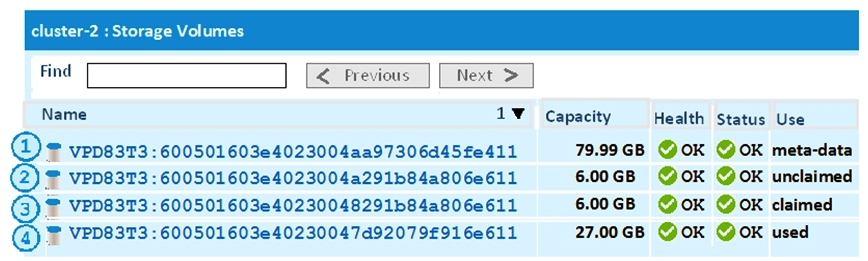 Which displayed storage volume is available to be used for the creation of an extent?
Which displayed storage volume is available to be used for the creation of an extent?
A) 1
B) 2
C) 3
D) 4
 Which displayed storage volume is available to be used for the creation of an extent?
Which displayed storage volume is available to be used for the creation of an extent?A) 1
B) 2
C) 3
D) 4

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
36
Which VPLEX model is recommended for VPLEX for All Flash (VAF)?
A) VS2 and VS6
B) VS6 only
C) VS2 only
D) VS1
A) VS2 and VS6
B) VS6 only
C) VS2 only
D) VS1

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
37
What happens to global cache size if a director fails and is removed from the cluster?
A) Suspends
B) Increases
C) Decreases
D) Remains as-is
A) Suspends
B) Increases
C) Decreases
D) Remains as-is

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
38
You are helping a customer create a cost-effective Isilon solution. The customer environment includes high IOPS-intensive, random access file-based applications. Which Isilon storage node type will meet the customer's needs?
A) S-Series
B) NL-Series
C) X-Series
D) Performance Accelerator
A) S-Series
B) NL-Series
C) X-Series
D) Performance Accelerator

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
39
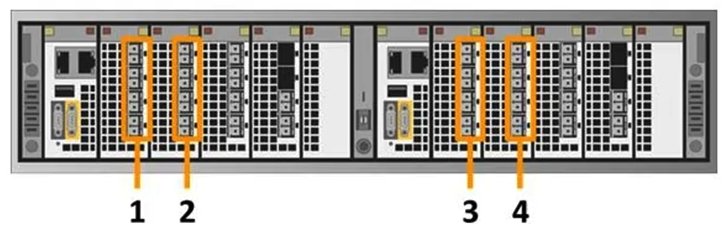 Which number in the exhibit highlights the Director-A back-end ports?
Which number in the exhibit highlights the Director-A back-end ports?A) 1
B) 2
C) 3
D) 4

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
40
Which command collects the most recent performance statistics from all VPLEX directors?
A) SNMPGETBULK
B) monitor stat-list
C) SNMPGET
D) monitor collect
A) SNMPGETBULK
B) monitor stat-list
C) SNMPGET
D) monitor collect

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
41
Which type of statistics is used to track latencies, determine median, mode, percentiles, minimums, and maximums?
A) Buckets
B) Monitors
C) Readings
D) Counters
A) Buckets
B) Monitors
C) Readings
D) Counters

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
42
VPLEX Metro has been added to an existing HP OpenView network monitoring environment. The VPLEX SNMP agent and other integration information have been added to assist in the implementation. After VPLEX is added to SNMP monitoring, only the remote VPLEX cluster is reporting performance statistics. What is the cause of this issue?
A) Local VPLEX Witness has a misconfigured SNMP agent.
B) HP OpenView is running SNMP version 2C, which may cause reporting that does not contain the performance statistics.
C) TCP Port 443 is blocked at the local site's firewall.
D) Local VPLEX cluster management server has a misconfigured SNMP agent.
A) Local VPLEX Witness has a misconfigured SNMP agent.
B) HP OpenView is running SNMP version 2C, which may cause reporting that does not contain the performance statistics.
C) TCP Port 443 is blocked at the local site's firewall.
D) Local VPLEX cluster management server has a misconfigured SNMP agent.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
43
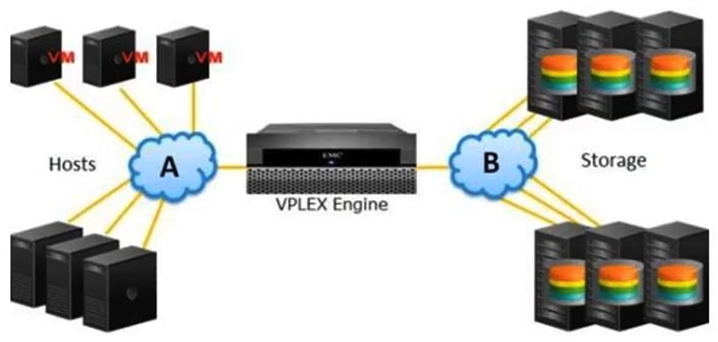 Which protocol is presented by "B" in the exhibit?
Which protocol is presented by "B" in the exhibit?A) FC
B) iSCSI
C) FCoE
D) IPFC

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
44
You get a call from a customer that has just added 200 user connections to the cluster. They want to know how fast they are writing data with these new users. What tool would you use to gather this information?
A) InsightIQ
B) Network Monitor
C) Wireshark
D) Watch4net
A) InsightIQ
B) Network Monitor
C) Wireshark
D) Watch4net

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
45
Your customer is looking for a storage solution that will be able to store seven million 3 MB files which are written and seldom accessed. Read and write operations are both completed by a web-based application, which requires 1.3 Gbps throughput. The customer's network has not been upgraded in many years, so the network interfaces are 1 Gbps. What would be the best solution for this network configuration?
A) Use LACP to aggregate the network ports on each node.
B) Use jumbo frames to compensate for the 1GB Core network.
C) Aggregate Infiniband (IB) ports across all nodes.
D) Bond EXT-0 across all nodes.
A) Use LACP to aggregate the network ports on each node.
B) Use jumbo frames to compensate for the 1GB Core network.
C) Aggregate Infiniband (IB) ports across all nodes.
D) Bond EXT-0 across all nodes.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
46
Which type of volumes has individual synchronized copies of data (mirrors) in more than one cluster?
A) Distributed device
B) Extent
C) Storage volume
D) Virtual volume
A) Distributed device
B) Extent
C) Storage volume
D) Virtual volume

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
47
What is a characteristic of global commands in the VPlexcli?
A) Executable from any director
B) Control tasks running on all directors
C) Run exclusively from the root context
D) Accessible from all contexts
A) Executable from any director
B) Control tasks running on all directors
C) Run exclusively from the root context
D) Accessible from all contexts

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
48
LUNs are being provisioned from an ALUA-capable back-end array to VPLEX. What is the path requirement for each VPLEX director when connecting to this type of array?
A) At least two paths to every back-end array and storage volume
B) At least two paths to both the active and passive array controllers
C) A least two paths to both the active and non-preferred array controllers
D) At least two paths to the active array controller only
A) At least two paths to every back-end array and storage volume
B) At least two paths to both the active and passive array controllers
C) A least two paths to both the active and non-preferred array controllers
D) At least two paths to the active array controller only

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
49
Which method of virtual volume expansion requires the volume to be expanded on the array first?
A) Extent expansion
B) Storage volume
C) RAID-C expansion
D) Concatenation
A) Extent expansion
B) Storage volume
C) RAID-C expansion
D) Concatenation

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
50
In a VPLEX Metro, what factor has a direct impact on VPLEX performance with respect to WAN bandwidth?
A) Thin pool rebalances
B) Read rate on distributed volumes
C) Raid rebuild on array
D) Write rate on distributed volumes
A) Thin pool rebalances
B) Read rate on distributed volumes
C) Raid rebuild on array
D) Write rate on distributed volumes

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
51
A new VPLEX system has been installed that uses ESRS. The firewall administrator has opened ports 25, 9010, and 5901 between VPLEX and ESRS. A support ticket is logged. While trying to troubleshoot, the technical support engineer cannot access the GUI of VPLEX. Which port needs to be opened on the firewall?
A) 21
B) 443
C) 3268
D) 8080
A) 21
B) 443
C) 3268
D) 8080

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
52
-- Exhibit -- A large manufacturing company is an existing Isilon customer with a cluster consisting of four NL400 nodes with 4TB drives. The cluster is using N+2:1 protection level and the file system shows that it is 60% utilized. Home directories and file shares comprise 75% of the existing content and the remainder is inactive deep archive. The company has 1,000 employees using Windows and Mac clients participating in a single Active Directory (AD) forest. During a meeting with the CIO and Director of IT you discuss the company's recent acquisition - an engineering firm that specializes in Computer Aided Design (CAD). The engineering firm has 400 UNIX workstations that produce technical drawings which are currently stored on another vendor's SAN solution. The all UNIX environment uses NIS for authentication and name resolution. They do not currently use DNS or LDAP. The engineering company has an old storage system that has been experiencing problems and the CIO would like you to migrate the data onto the Isilon cluster. The CIO would like to eliminate all tape and recover the data onto disk. The CIO is concerned about security of the company's intellectual property, especially with the rapid adoption of mobile devices and external cloud content sharing services such as DropBox, Egnyte, and SugarSync. They would like to implement an alternative that provides external file sharing and mobile device synchronization while maintaining security control over the company's data. The Director of IT reports that users are storing non-work related content on the Isilon cluster. They would like to limit the amount of capacity that each user can consume in their home directory and want to ensure you provide the capability to easily visualize which users are over their allotment.The company's Windows users currently leverage Windows Shadow Copy to recover files that have been accidentally deleted. The IT department wants to ensure that Mac and incoming UNIX clients have the same functionality. The Director of IT also mentions that users are reporting slow response times when browsing their home directories and shared folders. They are concerned that Isilon cannot scale to support their combined requirements. Based on the meeting with the customer, which Isilon cluster configuration would you recommend?
A) 4 x X400 nodes with 2 x SSD and 34 x 4TB drives 1 x Additional NL400
B) 6 x X400 nodes with 36 x 4TB drives 1 x Backup Accelerator
C) 4 x NL400 nodes with 36 x 4TB drives
D) 9 x S200 nodes with 2 x SSD and 22 x 900GB SAS
A) 4 x X400 nodes with 2 x SSD and 34 x 4TB drives 1 x Additional NL400
B) 6 x X400 nodes with 36 x 4TB drives 1 x Backup Accelerator
C) 4 x NL400 nodes with 36 x 4TB drives
D) 9 x S200 nodes with 2 x SSD and 22 x 900GB SAS

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
53
A storage administrator has created a VPLEX distributed device. The administrator is performing application tests on the host utilizing the distributed virtual volumes. During testing, some of the write response times appear to be elongated. What is a characteristic of distributed devices that explains this issue?
A) Writes need to be written locally to multiple VPLEX Directors before sending a host acknowledgement.
B) Writes need to be written to both clusters before sending a host acknowledgement.
C) Writes need to be journaled in the VPLEX Witness logging volumes before sending a host acknowledgement.
D) Writes need to be protected on the remote disk arrays only before sending a host acknowledgement.
A) Writes need to be written locally to multiple VPLEX Directors before sending a host acknowledgement.
B) Writes need to be written to both clusters before sending a host acknowledgement.
C) Writes need to be journaled in the VPLEX Witness logging volumes before sending a host acknowledgement.
D) Writes need to be protected on the remote disk arrays only before sending a host acknowledgement.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
54
You have 1000 users for an application that reads and writes files averaging between one and four MB in size. Each user requires 24 MB of RAM. You want to add another 1000 users for this application, and in preparation for them, you run the isi statistics command. You discover that the average CPU utilization is 20%; aggregate throughput averages 700 MB/s and the disk QueueD average is 1.5. Your cluster currently has five X200 (12 GB RAM, 1 TB drive) nodes, uses N+2:1 protection and 1 GigE networking. What should you do to accommodate the next 1000 users?
A) Add five additional X200 (12 GB, 1 TB drive) nodes
B) Upgrade each X200 node to a total of 24 GB of RAM.
C) Upgrade two of the 1 GigE NICs to 10 GigE on each node.
D) Add five A100 (24 GB RAM) accelerator nodes.
A) Add five additional X200 (12 GB, 1 TB drive) nodes
B) Upgrade each X200 node to a total of 24 GB of RAM.
C) Upgrade two of the 1 GigE NICs to 10 GigE on each node.
D) Add five A100 (24 GB RAM) accelerator nodes.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
55
What is the maximum number of synchronous consistency groups supported by VPLEX?
A) 256
B) 512
C) 1024
D) 2048
A) 256
B) 512
C) 1024
D) 2048

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
56
At which stage of configuring a virtual volume on VPLEX is the RAID level defined?
A) Claimed volume
B) Device
C) Storage volume
D) Extent
A) Claimed volume
B) Device
C) Storage volume
D) Extent

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
57
Which VPLEX component can determine the difference between a partition and a site failure of a VPLEX Metro configuration?
A) VPLEX Witness
B) Management Server
C) Distributed device
D) Consistency group
A) VPLEX Witness
B) Management Server
C) Distributed device
D) Consistency group

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
58
What is the relationship between a storage volume and an extent?
A) A storage volume can be split into multiple extents
B) An extent must map to an entire storage volume
C) A storage volume can be created out of multiple extents
D) An extent can span multiple storage volumes
A) A storage volume can be split into multiple extents
B) An extent must map to an entire storage volume
C) A storage volume can be created out of multiple extents
D) An extent can span multiple storage volumes

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
59
When using VPLEX Metro, what is the supported round trip time between clusters?
A) 5 ms
B) 15 ms
C) 20 ms
D) 30 ms
A) 5 ms
B) 15 ms
C) 20 ms
D) 30 ms

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
60
Which mobility operation must be used to perform storage volume defragmentation?
A) Virtual volume mobility
B) Data mobility
C) Device mobility
D) Extent mobility
A) Virtual volume mobility
B) Data mobility
C) Device mobility
D) Extent mobility

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
61
Which data mobility operation removes the pointer to the source leg of a RAID-1 device?
A) Clean
B) Commit
C) Start
D) Remove
A) Clean
B) Commit
C) Start
D) Remove

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
62
In preparing a host to access its storage from VPLEX, what is considered a best practice when zoning?
A) Ports on host HBA should be zoned to either an A director or a B director.
B) Each host should have at least one path to an A director and at least one path to a B director on each fabric, for a total of four logical paths.
C) Dual fabrics should be merged into a single fabric to ensure all zones are in a single zoneset.
D) Each host should have either one path to an A director or one path to a B director on each fabric, for a minimum of two logical paths.
A) Ports on host HBA should be zoned to either an A director or a B director.
B) Each host should have at least one path to an A director and at least one path to a B director on each fabric, for a total of four logical paths.
C) Dual fabrics should be merged into a single fabric to ensure all zones are in a single zoneset.
D) Each host should have either one path to an A director or one path to a B director on each fabric, for a minimum of two logical paths.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck


