Deck 5: Automation and DevOps, Associate
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/79
Play
Full screen (f)
Deck 5: Automation and DevOps, Associate
1
Which two statements are correct about global security policies? (Choose two.)
A) Global-based policies can reference the destination zone.
B) Global-based policies can reference the source zone.
C) Global-based policies must reference a dynamic application.
D) Global-based policies must reference the source and destination zones.
A) Global-based policies can reference the destination zone.
B) Global-based policies can reference the source zone.
C) Global-based policies must reference a dynamic application.
D) Global-based policies must reference the source and destination zones.
Global-based policies can reference the destination zone.
Global-based policies can reference the source zone.
Global-based policies can reference the source zone.
2
Which two statements are true about Junos Space Security Director? (Choose two.)
A) Security Director supports creation and maintenance of metadata-based policies.
B) Security Director can deploy enforcement policies automatically to firewalls and switches.
C) Security Director can perform deep-packet analysis.
D) Security Director is preinstalled on SRX Series devices.
A) Security Director supports creation and maintenance of metadata-based policies.
B) Security Director can deploy enforcement policies automatically to firewalls and switches.
C) Security Director can perform deep-packet analysis.
D) Security Director is preinstalled on SRX Series devices.
Security Director supports creation and maintenance of metadata-based policies.
Security Director can deploy enforcement policies automatically to firewalls and switches.
Security Director can deploy enforcement policies automatically to firewalls and switches.
3
Which two statements describe IPsec VPNs? (Choose two.)
A) IPsec VPN traffic is always authenticated.
B) IPsec VPNs are dedicated physical connections between two private networks.
C) IPsec VPN traffic is always encrypted.
D) IPsec VPNs use security measures to secure traffic over a public network between two remote sites.
A) IPsec VPN traffic is always authenticated.
B) IPsec VPNs are dedicated physical connections between two private networks.
C) IPsec VPN traffic is always encrypted.
D) IPsec VPNs use security measures to secure traffic over a public network between two remote sites.
IPsec VPN traffic is always authenticated.
IPsec VPNs use security measures to secure traffic over a public network between two remote sites.
IPsec VPNs use security measures to secure traffic over a public network between two remote sites.
4
Click the Exhibit button. 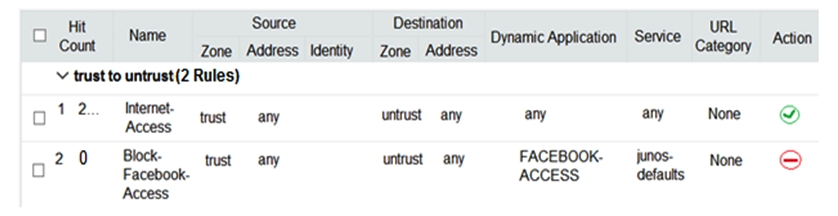 Users should not have access to Facebook, however, a recent examination of the security logs show that users are accessing Facebook. Referring to the exhibit, what should you do to solve this problem?
Users should not have access to Facebook, however, a recent examination of the security logs show that users are accessing Facebook. Referring to the exhibit, what should you do to solve this problem?
A) Change the source address for the Block-Facebook-Access rule to the prefix of the users.
B) Change the Block-Facebook-Access rule from a zone policy to a global policy.
C) Move the Block-Facebook-Access rule before the Internet-Access rule.
D) Change the Internet-Access rule from a zone policy to a global policy.
 Users should not have access to Facebook, however, a recent examination of the security logs show that users are accessing Facebook. Referring to the exhibit, what should you do to solve this problem?
Users should not have access to Facebook, however, a recent examination of the security logs show that users are accessing Facebook. Referring to the exhibit, what should you do to solve this problem?A) Change the source address for the Block-Facebook-Access rule to the prefix of the users.
B) Change the Block-Facebook-Access rule from a zone policy to a global policy.
C) Move the Block-Facebook-Access rule before the Internet-Access rule.
D) Change the Internet-Access rule from a zone policy to a global policy.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
5
Your company has been assigned one public IP address. You want to enable Internet traffic to reach multiple servers in your DMZ that are configured with private IP addresses. In this scenario, which type of NAT would be used to accomplish this task?
A) source NAT
B) destination NAT
C) NAT without PAT
D) static NAT
A) source NAT
B) destination NAT
C) NAT without PAT
D) static NAT

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
6
Which type of traffic is analyzed by an SRX Series device configured to use an antispam UTM policy?
A) IMAP
B) POP3
C) SMTP
D) HTTP
A) IMAP
B) POP3
C) SMTP
D) HTTP

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
7
What is the definition of a zone on an SRX Series device?
A) a collection of one or more network segments sharing similar security requirements
B) an individual logical interface with a public IP address
C) a collection of one or more network segments with different security requirements
D) an individual logical interface with a private IP address
A) a collection of one or more network segments sharing similar security requirements
B) an individual logical interface with a public IP address
C) a collection of one or more network segments with different security requirements
D) an individual logical interface with a private IP address

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
8
You have created a zone-based security policy that permits traffic to a specific webserver for the marketing team. Other groups in the company are not permitted to access the webserver. When marketing users attempt to access the server they are unable to do so. What are two reasons for this access failure? (Choose two.)
A) You failed to position the policy before the policy that denies access to the webserver.
B) You failed to position the policy after the policy that denies access to the webserver.
C) You failed to commit the policy change.
D) You failed to change the source zone to include any source zone.
A) You failed to position the policy before the policy that denies access to the webserver.
B) You failed to position the policy after the policy that denies access to the webserver.
C) You failed to commit the policy change.
D) You failed to change the source zone to include any source zone.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
9
You want to deploy, manage, and configure multiple SRX Series devices without an on-premises software solution. Which solution would satisfy this requirement?
A) Junos Space Network Director
B) Juniper Sky Enterprise
C) Juniper SKY ATP
D) Juniper Advanced Threat Prevention
A) Junos Space Network Director
B) Juniper Sky Enterprise
C) Juniper SKY ATP
D) Juniper Advanced Threat Prevention

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
10
Click the Exhibit button. 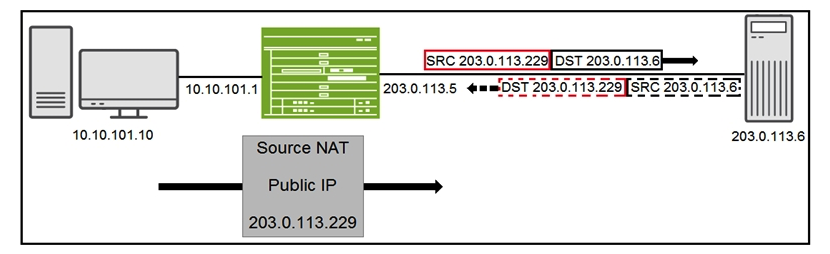 You have configured source NAT using an address pool as shown in the exhibit. Traffic is reaching the 203.0.113.6 server but return traffic is not being received by the SRX Series device. Which feature must be configured to allow return traffic to be accepted by the SRX Series device?
You have configured source NAT using an address pool as shown in the exhibit. Traffic is reaching the 203.0.113.6 server but return traffic is not being received by the SRX Series device. Which feature must be configured to allow return traffic to be accepted by the SRX Series device?
A) proxy ARP
B) destination NAT
C) port forwarding
D) reverse static NAT
 You have configured source NAT using an address pool as shown in the exhibit. Traffic is reaching the 203.0.113.6 server but return traffic is not being received by the SRX Series device. Which feature must be configured to allow return traffic to be accepted by the SRX Series device?
You have configured source NAT using an address pool as shown in the exhibit. Traffic is reaching the 203.0.113.6 server but return traffic is not being received by the SRX Series device. Which feature must be configured to allow return traffic to be accepted by the SRX Series device?A) proxy ARP
B) destination NAT
C) port forwarding
D) reverse static NAT

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
11
Click the Exhibit button. 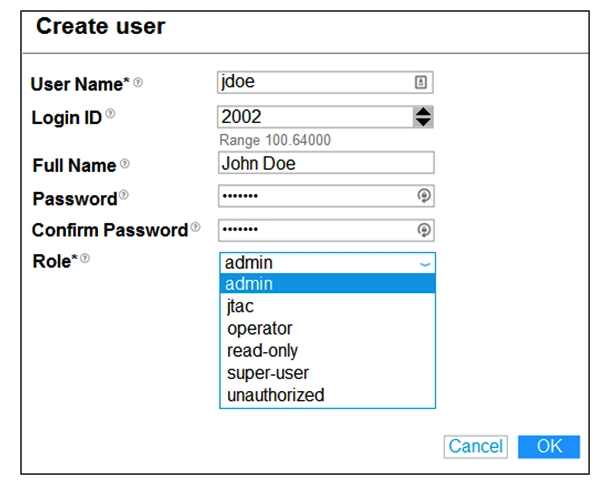 Which two user roles shown in the exhibit are available by default? (Choose two.)
Which two user roles shown in the exhibit are available by default? (Choose two.)
A) super-user
B) operator
C) jtac
D) admin
 Which two user roles shown in the exhibit are available by default? (Choose two.)
Which two user roles shown in the exhibit are available by default? (Choose two.)A) super-user
B) operator
C) jtac
D) admin

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
12
Which type of security policy protects restricted services from running on non-standard ports?
A) application firewall
B) IDP
C) Sky ATP
D) antivirus
A) application firewall
B) IDP
C) Sky ATP
D) antivirus

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
13
Which method do VPNs use to prevent outside parties from viewing packets in clear text?
A) integrity
B) authentication
C) encryption
D) NAT-T
A) integrity
B) authentication
C) encryption
D) NAT-T

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
14
What is the correct order of processing when configuring NAT rules and security policies?
A) destination NAT > policy lookup > source NAT > static NAT
B) policy lookup > source NAT > static NAT > destination NAT
C) source NAT > static NAT > destination NAT > policy lookup
D) static NAT > destination NAT > policy lookup > source NAT
A) destination NAT > policy lookup > source NAT > static NAT
B) policy lookup > source NAT > static NAT > destination NAT
C) source NAT > static NAT > destination NAT > policy lookup
D) static NAT > destination NAT > policy lookup > source NAT

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
15
By default, revenue interfaces are placed into which system-defined security zone on an SRX Series device?
A) junos-trust
B) untrust
C) trust
D) null
A) junos-trust
B) untrust
C) trust
D) null

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
16
Users in your network are downloading files with file extensions that you consider to be unsafe for your network. You must prevent files with specific file extensions from entering your network. Which UTM feature should be enabled on an SRX Series device to accomplish this task?
A) content filtering
B) antispam
C) Web filtering
D) URL filtering
A) content filtering
B) antispam
C) Web filtering
D) URL filtering

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
17
Which statement is correct about address books for security policies on SRX Series devices?
A) Address sets can contain addresses from different security zones.
B) A zone can only use one address book at a time.
C) NAT rules can use address objects only from the global address book.
D) Addresses in the global address book are preferred over addresses in a zone-based address book.
A) Address sets can contain addresses from different security zones.
B) A zone can only use one address book at a time.
C) NAT rules can use address objects only from the global address book.
D) Addresses in the global address book are preferred over addresses in a zone-based address book.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
18
Which two statements are correct about using global-based policies over zone-based policies? (Choose two.)
A) With global-based policies, you do not need to specify a source address in the match criteria.
B) With global-based policies, you do not need to specify a destination zone in the match criteria.
C) With global-based policies, you do not need to specify a destination address in the match criteria.
D) With global-based policies, you do not need to specify a source zone in the match criteria.
A) With global-based policies, you do not need to specify a source address in the match criteria.
B) With global-based policies, you do not need to specify a destination zone in the match criteria.
C) With global-based policies, you do not need to specify a destination address in the match criteria.
D) With global-based policies, you do not need to specify a source zone in the match criteria.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
19
Which statement is correct about Junos security zones?
A) User-defined security zones must contain at least one interface.
B) Logical interfaces are added to user-defined security zones.
C) Security policies are referenced within a user-defined security zone.
D) User-defined security zones must contain the key word "zone".
A) User-defined security zones must contain at least one interface.
B) Logical interfaces are added to user-defined security zones.
C) Security policies are referenced within a user-defined security zone.
D) User-defined security zones must contain the key word "zone".

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
20
Which zone is considered a functional zone?
A) junos host
B) null
C) trust
D) management
A) junos host
B) null
C) trust
D) management

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
21
What must you do first to use the Monitor/Events workspace in the J-Web interface?
A) You must enable security logging that uses the TLS transport mode.
B) You must enable security logging that uses the SD-Syslog format.
C) You must enable stream mode security logging on the SRX Series device.
D) You must enable event mode security logging on the SRX Series device.
A) You must enable security logging that uses the TLS transport mode.
B) You must enable security logging that uses the SD-Syslog format.
C) You must enable stream mode security logging on the SRX Series device.
D) You must enable event mode security logging on the SRX Series device.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
22
Which two actions are performed on an incoming packet matching an existing session? (Choose two.)
A) security policy evaluation
B) service ALG processing
C) screens processing
D) zones processing
A) security policy evaluation
B) service ALG processing
C) screens processing
D) zones processing

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
23
You want to automatically generate the encryption and authentication keys during IPsec VPN tunnel establishment. What would be used to accomplish this task?
A) main mode
B) aggressive mode
C) IPsec
D) Diffie-Hellman
A) main mode
B) aggressive mode
C) IPsec
D) Diffie-Hellman

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
24
Which two statements are correct about security zones? (Choose two.)
A) Security zones use address books to link usernames to IP addresses.
B) Security zones use a stateful firewall to provide secure network connections.
C) Security zones use packet filters to prevent communication between management ports.
D) Security zones use security policies that enforce rules for the transit traffic.
A) Security zones use address books to link usernames to IP addresses.
B) Security zones use a stateful firewall to provide secure network connections.
C) Security zones use packet filters to prevent communication between management ports.
D) Security zones use security policies that enforce rules for the transit traffic.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
25
What is a type of security feed that Sky ATP provides to a vSRX Series device by default?
A) RSS feeds
B) C&C feeds
C) ACL feeds
D) malware feeds
A) RSS feeds
B) C&C feeds
C) ACL feeds
D) malware feeds

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
26
What is the purpose of the Shadow Policies workspace in J-Web?
A) The Shadow Policies workspace shows unused security policies due to policy overlap.
B) The Shadow Policies workspace shows used security policies due to policy overlap.
C) The Shadow Policies workspace shows unused IPS policies due to policy overlap.
D) The Shadow Policies workspace shows used IPS policies due to policy overlap.
A) The Shadow Policies workspace shows unused security policies due to policy overlap.
B) The Shadow Policies workspace shows used security policies due to policy overlap.
C) The Shadow Policies workspace shows unused IPS policies due to policy overlap.
D) The Shadow Policies workspace shows used IPS policies due to policy overlap.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
27
You verify that the SSH service is configured correctly on your SRX Series device, yet administrators attempting to connect through a revenue port are not able to connect. In this scenario, what must be configured to solve this problem?
A) a host-inbound-traffic setting on the incoming zone
B) an MTU value larger than the default value
C) a screen on the internal interface
D) a security policy allowing SSH traffic
A) a host-inbound-traffic setting on the incoming zone
B) an MTU value larger than the default value
C) a screen on the internal interface
D) a security policy allowing SSH traffic

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
28
You are asked to run a report to find the top talkers on your network in the past 48 hours. In this scenario, the report will be in which format when the J-Web UI delivers it to you?
A) JPG
B) HTML
C) xls
D) CSV
A) JPG
B) HTML
C) xls
D) CSV

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
29
What should you configure if you want to translate private source IP addresses to a single public IP address?
A) source NAT
B) destination NAT
C) content filtering
D) Security Director
A) source NAT
B) destination NAT
C) content filtering
D) Security Director

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
30
Which two statements are true about virtualized SRX Series devices? (Choose two.)
A) vSRX cannot be deployed in transparent mode.
B) cSRX can be deployed in routed mode.
C) cSRX cannot be deployed in routed mode.
D) vSRX can be deployed in transparent mode.
A) vSRX cannot be deployed in transparent mode.
B) cSRX can be deployed in routed mode.
C) cSRX cannot be deployed in routed mode.
D) vSRX can be deployed in transparent mode.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
31
Click the Exhibit button. 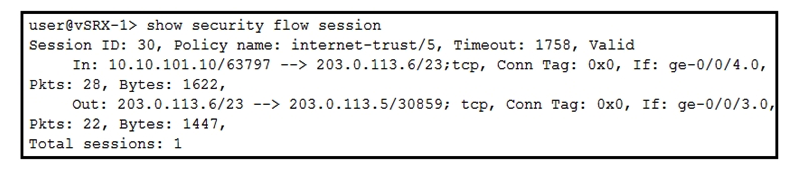 Referring to the exhibit, which type of NAT is being performed?
Referring to the exhibit, which type of NAT is being performed?
A) source NAT without PAT
B) destination NAT without PAT
C) source NAT with PAT
D) destination NAT with PAT
 Referring to the exhibit, which type of NAT is being performed?
Referring to the exhibit, which type of NAT is being performed?A) source NAT without PAT
B) destination NAT without PAT
C) source NAT with PAT
D) destination NAT with PAT

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
32
Which two statements are true about security policies in the factory-default configuration of an SRX340? (Choose two.)
A) All traffic from the trust zone to the untrust zone is allowed.
B) All interzone traffic is denied.
C) All interzone traffic is allowed.
D) All traffic from the untrust zone to the trust zone is denied.
A) All traffic from the trust zone to the untrust zone is allowed.
B) All interzone traffic is denied.
C) All interzone traffic is allowed.
D) All traffic from the untrust zone to the trust zone is denied.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
33
You are designing a new security policy on an SRX Series device. You must block an application silently and log all occurrences of the application access attempts. In this scenario, which two actions must be enabled in the security policy? (Choose two.)
A) Log the session initiations.
B) Enable a reject action.
C) Log the session closures.
D) Enable a deny action.
A) Log the session initiations.
B) Enable a reject action.
C) Log the session closures.
D) Enable a deny action.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
34
Which statement is correct about IKE?
A) IKE phase 1 is used to establish the data path.
B) IKE phase 1 only supports aggressive mode.
C) IKE phase 1 establishes the tunnel between devices.
D) IKE phase 1 negotiates a secure channel between gateways.
A) IKE phase 1 is used to establish the data path.
B) IKE phase 1 only supports aggressive mode.
C) IKE phase 1 establishes the tunnel between devices.
D) IKE phase 1 negotiates a secure channel between gateways.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
35
Which UTM feature uses MIME pattern filters to identify traffic in HTTP and e-mail protocols?
A) antispam
B) antivirus
C) Web filtering
D) content filtering
A) antispam
B) antivirus
C) Web filtering
D) content filtering

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
36
On an SRX Series device, how should you configure your IKE gateway if the remote endpoint is a branch office using a dynamic IP address?
A) Configure the IPsec policy to use MD5 authentication.
B) Configure the IKE policy to use aggressive mode.
C) Configure the IPsec policy to use aggressive mode.
D) Configure the IKE policy to use a static IP address.
A) Configure the IPsec policy to use MD5 authentication.
B) Configure the IKE policy to use aggressive mode.
C) Configure the IPsec policy to use aggressive mode.
D) Configure the IKE policy to use a static IP address.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
37
When configuring IPsec VPNs, setting a hash algorithm solves which security concern?
A) availability
B) encryption
C) redundancy
D) integrity
A) availability
B) encryption
C) redundancy
D) integrity

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
38
You have configured a Web filtering UTM policy. Which action must be performed before the Web filtering UTM policy takes effect?
A) The UTM policy must be configured as a routing next hop.
B) The UTM policy must be linked to an ingress interface.
C) The UTM policy must be linked to an egress interface.
D) The UTM policy must be linked to a security policy.
A) The UTM policy must be configured as a routing next hop.
B) The UTM policy must be linked to an ingress interface.
C) The UTM policy must be linked to an egress interface.
D) The UTM policy must be linked to a security policy.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
39
Which statement is correct about global security policies?
A) Global policies eliminate the need to assign logical interfaces to security zones.
B) Global security policies require you to identify a source and destination zone.
C) Traffic matching global policies is not added to the session table.
D) Global policies allow you to regulate traffic with addresses and applications, regardless of their security zones.
A) Global policies eliminate the need to assign logical interfaces to security zones.
B) Global security policies require you to identify a source and destination zone.
C) Traffic matching global policies is not added to the session table.
D) Global policies allow you to regulate traffic with addresses and applications, regardless of their security zones.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
40
Which statement describes stateless firewalls on SRX Series devices?
A) Each packet is analyzed based on source zone.
B) Each packet is analyzed based on Application Layer security.
C) Each packet is analyzed as part of a session.
D) Each packet is analyzed by firewall filters.
A) Each packet is analyzed based on source zone.
B) Each packet is analyzed based on Application Layer security.
C) Each packet is analyzed as part of a session.
D) Each packet is analyzed by firewall filters.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
41
Which statement describes the AppTrack module in AppSecure?
A) The AppTrack module provides enforcement with the ability to block traffic, based on specific applications.
B) The AppTrack module provides control by the routing of traffic, based on the application.
C) The AppTrack module identifies the applications that are present in network traffic.
D) The AppTrack module provides visibility and volumetric reporting of application usage on the network.
A) The AppTrack module provides enforcement with the ability to block traffic, based on specific applications.
B) The AppTrack module provides control by the routing of traffic, based on the application.
C) The AppTrack module identifies the applications that are present in network traffic.
D) The AppTrack module provides visibility and volumetric reporting of application usage on the network.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
42
Which feature supports sandboxing of zero-day attacks?
A) Sky ATP
B) SSL proxy
C) ALGs
D) high availability
A) Sky ATP
B) SSL proxy
C) ALGs
D) high availability

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
43
What is the default session timeout value for ICMP and UDP traffic?
A) 30 seconds
B) 30 minutes
C) 60 seconds
D) 5 minutes
A) 30 seconds
B) 30 minutes
C) 60 seconds
D) 5 minutes

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
44
You are configuring a client-protection SSL proxy profile. Which statement is correct in this scenario?
A) A server certificate is not used but a root certificate authority is used.
B) A server certificate and root certificate authority are not used.
C) A server certificate is used but a root certificate authority is not used.
D) A server certificate and a root certificate authority are both used.
A) A server certificate is not used but a root certificate authority is used.
B) A server certificate and root certificate authority are not used.
C) A server certificate is used but a root certificate authority is not used.
D) A server certificate and a root certificate authority are both used.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
45
The AppQoE module of AppSecure provides which function?
A) The AppQoE module provides application-based routing.
B) The AppQoE module prioritizes important applications.
C) The AppQoE module provides routing, based on network conditions.
D) The AppQoE module blocks access to risky applications.
A) The AppQoE module provides application-based routing.
B) The AppQoE module prioritizes important applications.
C) The AppQoE module provides routing, based on network conditions.
D) The AppQoE module blocks access to risky applications.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
46
What is the default timeout period for a TCP session in the session table of a Junos security device?
A) 1 minute
B) 60 minutes
C) 15 minutes
D) 30 minutes
A) 1 minute
B) 60 minutes
C) 15 minutes
D) 30 minutes

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
47
What information does JIMS collect from domain event log sources? (Choose two.)
A) For user login events, JIMS collects the username and group membership information.
B) For device login events. JIMS collects the devide IP address and operating system version.
C) For device login events, JIMS collects the device IP address and machine name information.
D) For user login events, JIMS collects the login source IP address and username information.
A) For user login events, JIMS collects the username and group membership information.
B) For device login events. JIMS collects the devide IP address and operating system version.
C) For device login events, JIMS collects the device IP address and machine name information.
D) For user login events, JIMS collects the login source IP address and username information.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
48
Click the Exhibit button. 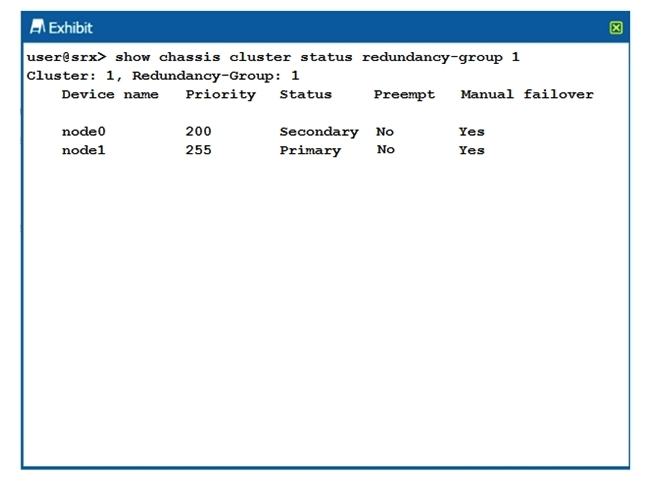 Which two statements describe the output shown in the exhibit? (Choose two.)
Which two statements describe the output shown in the exhibit? (Choose two.)
A) Node 0 is passing traffic for redundancy group 1.
B) Redundancy group 1 experienced an operational failure.
C) Redundancy group 1 was administratively failed over.
D) Node 1 is passing traffic for redundancy group1.
 Which two statements describe the output shown in the exhibit? (Choose two.)
Which two statements describe the output shown in the exhibit? (Choose two.)A) Node 0 is passing traffic for redundancy group 1.
B) Redundancy group 1 experienced an operational failure.
C) Redundancy group 1 was administratively failed over.
D) Node 1 is passing traffic for redundancy group1.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
49
Which security log message format reduces the consumption of CPU and storage?
A) WELF
B) BSD syslog
C) binary
D) structured syslog
A) WELF
B) BSD syslog
C) binary
D) structured syslog

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
50
Which two statements describe how rules are used with Juniper Secure Analytics? (Choose two.)
A) When a rule is triggered, JSA can respond by sending an e-mail to JSA administrators.
B) Rules are defined on Junos Space Security Director, and then pushed to JSA log collectors.
C) A rule defines matching criteria and actions that should be taken when an events matches the rule.
D) When a rule is triggered, JSA can respond by blocking all traffic from a specific source address.
A) When a rule is triggered, JSA can respond by sending an e-mail to JSA administrators.
B) Rules are defined on Junos Space Security Director, and then pushed to JSA log collectors.
C) A rule defines matching criteria and actions that should be taken when an events matches the rule.
D) When a rule is triggered, JSA can respond by blocking all traffic from a specific source address.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
51
What are two valid JIMS event log sources? (Choose two.)
A) Microsoft Windows Server 2012 audit logs
B) Microsoft Active Directory server event logs
C) Microsoft Exchange Server event logs
D) Microsoft Active Directory audit logs
A) Microsoft Windows Server 2012 audit logs
B) Microsoft Active Directory server event logs
C) Microsoft Exchange Server event logs
D) Microsoft Active Directory audit logs

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
52
Which two statements describe application-layer gateways (ALGs)? (Choose two.)
A) ALGs are designed for specific protocols that require multiple sessions.
B) ALGs are used with protocols that use multiple ports.
C) ALGs can only be configured using Security Director.
D) ALGs are designed for specific protocols that use a single TCP session.
A) ALGs are designed for specific protocols that require multiple sessions.
B) ALGs are used with protocols that use multiple ports.
C) ALGs can only be configured using Security Director.
D) ALGs are designed for specific protocols that use a single TCP session.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
53
You must ensure that all encrypted traffic passing through your SRX device uses strong protocols and ciphers. Which feature should you implement to satisfy this requirement?
A) SSL proxy
B) AppSecure
C) JIMS
D) JATP
A) SSL proxy
B) AppSecure
C) JIMS
D) JATP

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
54
Which solution should you use if you want to detect known attacks using signature-based methods?
A) SSL proxy
B) JIMS
C) IPS
D) ALGs
A) SSL proxy
B) JIMS
C) IPS
D) ALGs

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
55
You must configure JSA to accept events from an unsupported third-party log source. In this scenario, what should you do?
A) Separate event collection and flow collection on separate collectors.
B) Configure an RPM for a third-party device service module.
C) Configure JSA to silently discard unsupported log types.
D) Configure a universal device service module.
A) Separate event collection and flow collection on separate collectors.
B) Configure an RPM for a third-party device service module.
C) Configure JSA to silently discard unsupported log types.
D) Configure a universal device service module.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
56
Click the Exhibit button. 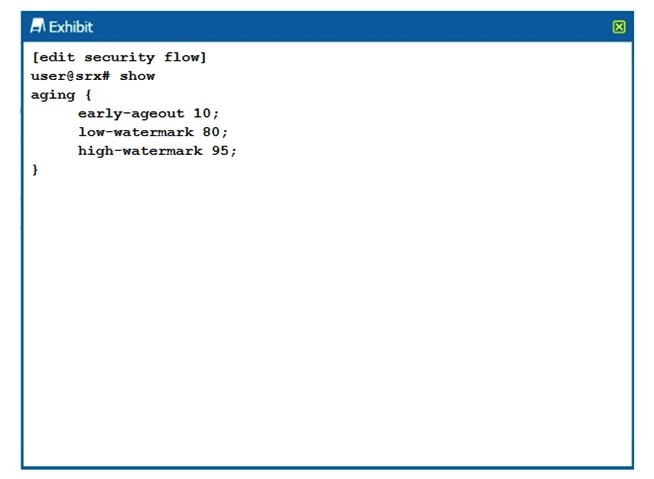 Which two statements are true about the configuration shown in the exhibit? (Choose two.)
Which two statements are true about the configuration shown in the exhibit? (Choose two.)
A) The session is removed from the session table after 10 seconds of inactivity.
B) The session is removed from the session table after 10 milliseconds of inactivity.
C) Aggressive aging is triggered if the session table reaches 95% capacity.
D) Aggressive aging is triggered if the session table reaches 80% capacity.
 Which two statements are true about the configuration shown in the exhibit? (Choose two.)
Which two statements are true about the configuration shown in the exhibit? (Choose two.)A) The session is removed from the session table after 10 seconds of inactivity.
B) The session is removed from the session table after 10 milliseconds of inactivity.
C) Aggressive aging is triggered if the session table reaches 95% capacity.
D) Aggressive aging is triggered if the session table reaches 80% capacity.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
57
Click the Exhibit button. 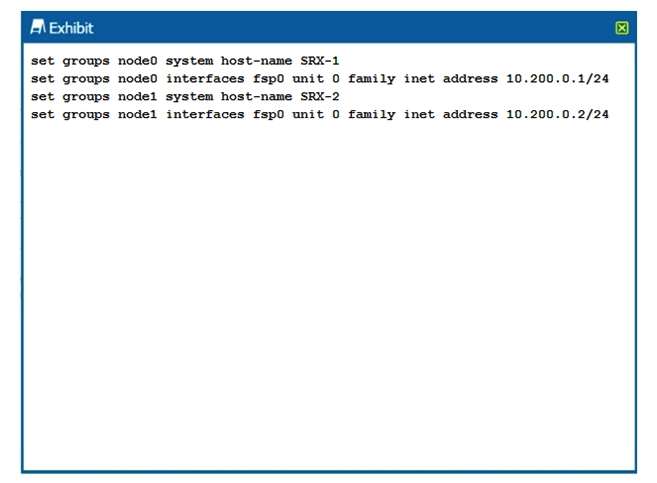 You are configuring an SRX chassis cluster with the node-specific hostname and management address. Referring to the exhibit, which configuration completes this requirement?
You are configuring an SRX chassis cluster with the node-specific hostname and management address. Referring to the exhibit, which configuration completes this requirement?
A)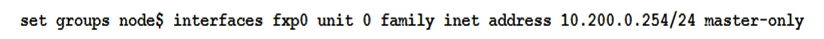
B)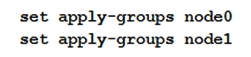
C)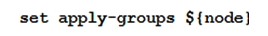
D)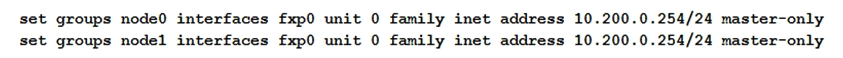
 You are configuring an SRX chassis cluster with the node-specific hostname and management address. Referring to the exhibit, which configuration completes this requirement?
You are configuring an SRX chassis cluster with the node-specific hostname and management address. Referring to the exhibit, which configuration completes this requirement?A)
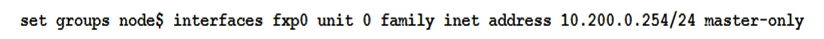
B)
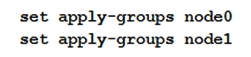
C)
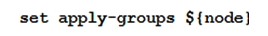
D)
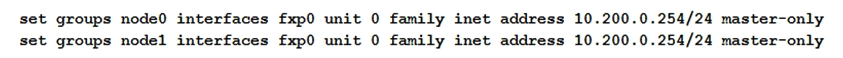

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
58
Which statement is true about JATP incidents?
A) Incidents have an associated threat number assigned to them.
B) Incidents are sorted by category, followed by severity.
C) Incidents consist of all the events associated with a single threat.
D) Incidents are always automatically mitigated.
A) Incidents have an associated threat number assigned to them.
B) Incidents are sorted by category, followed by severity.
C) Incidents consist of all the events associated with a single threat.
D) Incidents are always automatically mitigated.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
59
You want to deploy vSRX in Amazon Web Services (AWS) virtual private clouds (VPCs). Which two statements are true in this scenario? (Choose two.)
A) The vSRX devices serving as local enforcement points for VPCs can be managed by a centralized Junos Space Network Director instance.
B) MPLS LSPs can be used to connect vSRXs in different VPCs.
C) IPsec tunnels can be used to connect vSRX in different VPCs.
D) The vSRX devices serving as local enforcement points for VPCs can be managed by a centralized Junos Space Security Director instance.
A) The vSRX devices serving as local enforcement points for VPCs can be managed by a centralized Junos Space Network Director instance.
B) MPLS LSPs can be used to connect vSRXs in different VPCs.
C) IPsec tunnels can be used to connect vSRX in different VPCs.
D) The vSRX devices serving as local enforcement points for VPCs can be managed by a centralized Junos Space Security Director instance.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
60
A routing change occurs on an SRX Series device that involves choosing a new egress interface. In this scenario, which statement is true for all affected current sessions?
A) The current session are torn dowm only if the policy-rematch option has been enabled. The current session are torn dowm only if the policy-rematch option has been enabled.
B) The current sessions do not change.
C) The current sessions are torn down and go through first path processing based on the new route.
D) The current sessions might change based on the corresponding security policy.
A) The current session are torn dowm only if the policy-rematch option has been enabled. The current session are torn dowm only if the policy-rematch option has been enabled.
B) The current sessions do not change.
C) The current sessions are torn down and go through first path processing based on the new route.
D) The current sessions might change based on the corresponding security policy.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
61
You want to use Sky ATP to protect your network; however, company policy does not allow you to send any files to the cloud. Which Sky ATP feature should you use in this situation?
A) Only use on-premises local Sky ATP server anti-malware file scanning.
B) Only use cloud-based Sky ATP file hash lookups.
C) Only use on-box SRX anti-malware file scanning.
D) Only use cloud-based Sky ATP file blacklists.
A) Only use on-premises local Sky ATP server anti-malware file scanning.
B) Only use cloud-based Sky ATP file hash lookups.
C) Only use on-box SRX anti-malware file scanning.
D) Only use cloud-based Sky ATP file blacklists.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
62
Click the Exhibit button. 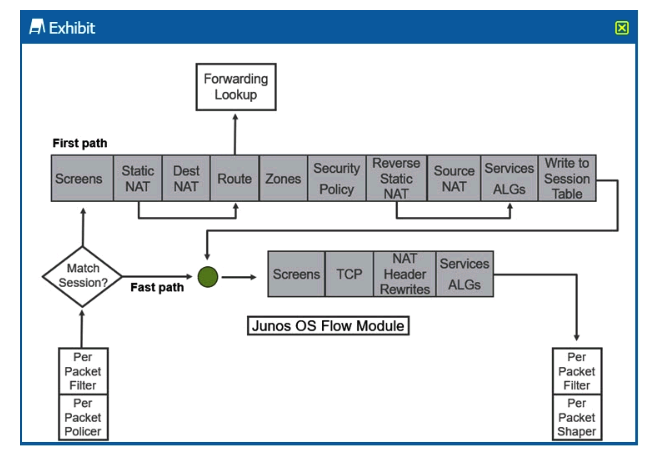 Referring to the SRX Series flow module diagram shown in the exhibit, where is IDP/IPS processed?
Referring to the SRX Series flow module diagram shown in the exhibit, where is IDP/IPS processed?
A) Forwarding Lookup
B) Services ALGs
C) Screens
D) Security Policy
 Referring to the SRX Series flow module diagram shown in the exhibit, where is IDP/IPS processed?
Referring to the SRX Series flow module diagram shown in the exhibit, where is IDP/IPS processed?A) Forwarding Lookup
B) Services ALGs
C) Screens
D) Security Policy

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
63
What is the maximum number of supported interfaces on a vSRX hosted in a VMware environment?
A) 4
B) 10
C) 3
D) 12
A) 4
B) 10
C) 3
D) 12

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
64
The DNS ALG performs which three functions? (Choose three.)
A) The DNS ALG performs the IPv4 and IPV6 address transformations.
B) The DNS ALG performs DNS doctoring.
C) The DNS ALG modifies the DNS payload in NAT mode.
D) The DNS ALG performs DNSSEC.
E) The DNS ALG performs DNS load balancing.
A) The DNS ALG performs the IPv4 and IPV6 address transformations.
B) The DNS ALG performs DNS doctoring.
C) The DNS ALG modifies the DNS payload in NAT mode.
D) The DNS ALG performs DNSSEC.
E) The DNS ALG performs DNS load balancing.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
65
Which two functions are performed by Juniper Identity Management Service (JIMS)? (Choose two.)
A) JIMS synchronizes Active Directory authentication information between a primary and secondary JIMS server.
B) JIMS forwards Active Directory authentication information to SRX Series client devices.
C) JIMS collects and maintains a database of authentication information from Active Directory domains.
D) JIMS replicates Active Directory authentication information to non-trusted Active Directory domain controllers.
A) JIMS synchronizes Active Directory authentication information between a primary and secondary JIMS server.
B) JIMS forwards Active Directory authentication information to SRX Series client devices.
C) JIMS collects and maintains a database of authentication information from Active Directory domains.
D) JIMS replicates Active Directory authentication information to non-trusted Active Directory domain controllers.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
66
Click the Exhibit button. 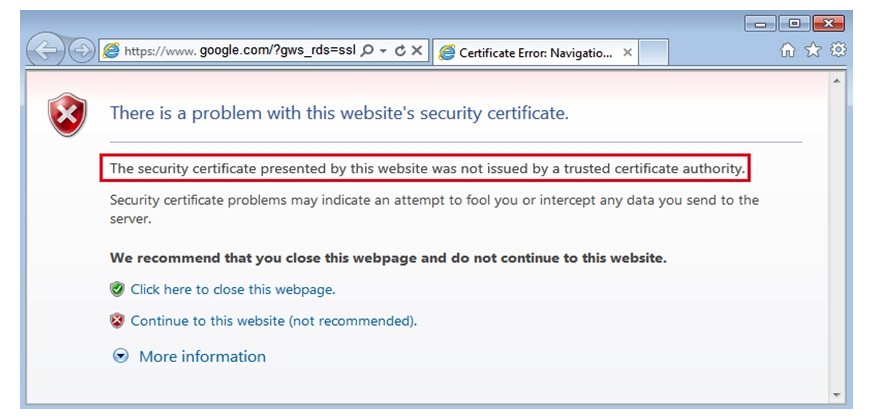 You have implemented SSL proxy client protection. After implementing this feature, your users are complaining about the warning message shown in the exhibit. Which action must you perform to eliminate the warning message?
You have implemented SSL proxy client protection. After implementing this feature, your users are complaining about the warning message shown in the exhibit. Which action must you perform to eliminate the warning message?
A) Configure the SRX Series device as a trusted site in the client Web browsers.
B) Regenerate the SRX self-signed CA certificate and include the correct organization name.
C) Import the SRX self-signed CA certificate into the client Web browsers.
D) Import the SRX self-signed CA certificate into the SRX certificate public store.
 You have implemented SSL proxy client protection. After implementing this feature, your users are complaining about the warning message shown in the exhibit. Which action must you perform to eliminate the warning message?
You have implemented SSL proxy client protection. After implementing this feature, your users are complaining about the warning message shown in the exhibit. Which action must you perform to eliminate the warning message?A) Configure the SRX Series device as a trusted site in the client Web browsers.
B) Regenerate the SRX self-signed CA certificate and include the correct organization name.
C) Import the SRX self-signed CA certificate into the client Web browsers.
D) Import the SRX self-signed CA certificate into the SRX certificate public store.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
67
Which two statements describe JSA? (Choose two.)
A) Security Director must be used to view third-party events rom JSA flow collectors.
B) JSA supports events and flows from Junos devices, including third-party devices.
C) JSA events must be manually imported into Security Directory using an SSH connection.
D) JSA can be used as a log node with Security Director or as a standalone solution.
A) Security Director must be used to view third-party events rom JSA flow collectors.
B) JSA supports events and flows from Junos devices, including third-party devices.
C) JSA events must be manually imported into Security Directory using an SSH connection.
D) JSA can be used as a log node with Security Director or as a standalone solution.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
68
Click the Exhibit button. 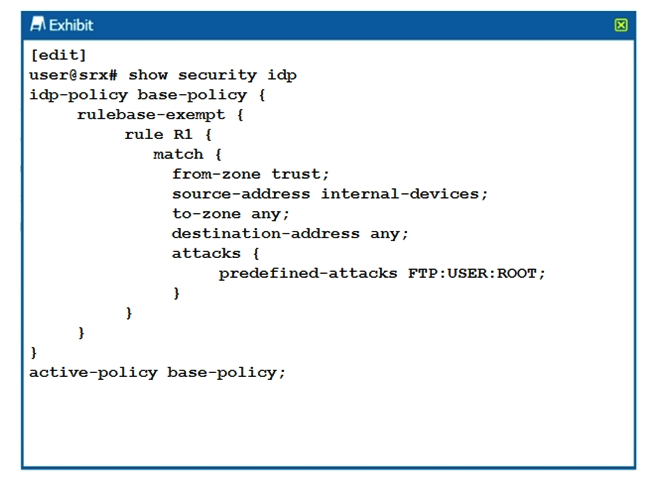 Referring to the exhibit, which statement is true?
Referring to the exhibit, which statement is true?
A) IDP blocks root users. IDP blocks root users.
B) IDP closes the connection on matched sessions.
C) IDP ignores the connection on matched sessions.
D) IDP blocks all users.
 Referring to the exhibit, which statement is true?
Referring to the exhibit, which statement is true?A) IDP blocks root users. IDP blocks root users.
B) IDP closes the connection on matched sessions.
C) IDP ignores the connection on matched sessions.
D) IDP blocks all users.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
69
Click the Exhibit button. 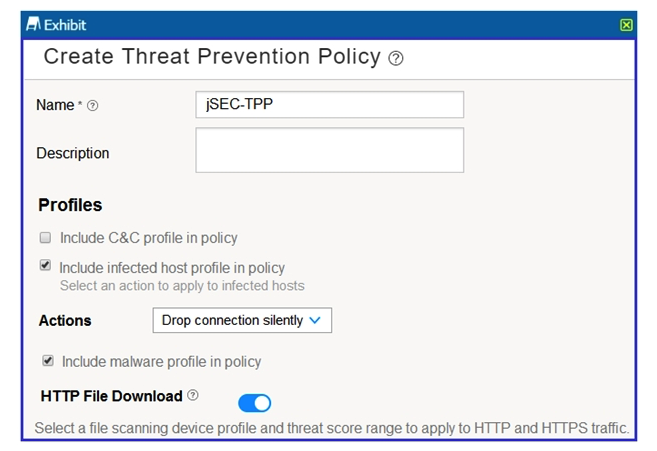 Referring to the exhibit, which statement is true?
Referring to the exhibit, which statement is true?
A) Hosts are always able to communicate through the SRX Series device no matter the threat score assigned to them on the infected host feed.
B) Hosts are unable to communicate through the SRX Series device after being placed on the infected host feed with a high enough threat score.
C) Malicious HTTP file downloads are never blocked.
D) Malicious HTTP file downloads are always blocked.
 Referring to the exhibit, which statement is true?
Referring to the exhibit, which statement is true?A) Hosts are always able to communicate through the SRX Series device no matter the threat score assigned to them on the infected host feed.
B) Hosts are unable to communicate through the SRX Series device after being placed on the infected host feed with a high enough threat score.
C) Malicious HTTP file downloads are never blocked.
D) Malicious HTTP file downloads are always blocked.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
70
You must fine tune an IPS security policy to eliminate false positives. You want to create exemptions to the normal traffic examination for specific traffic. Which two parameters are required to accomplish this task? (Choose two.)
A) source IP address
B) destination IP address
C) destination port
D) source port
A) source IP address
B) destination IP address
C) destination port
D) source port

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
71
Which two settings must be enabled on the hypervisor in a vSRX deployment to ensure proper chassis cluster operation? (Choose two.)
A) Control links must operate in promiscuous mode.
B) Control links must have an MTU of 9000.
C) Fabric links must operate in promiscuous mode.
D) Fabric links must have an MTU of 9000.
A) Control links must operate in promiscuous mode.
B) Control links must have an MTU of 9000.
C) Fabric links must operate in promiscuous mode.
D) Fabric links must have an MTU of 9000.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
72
You are asked to enable AppTrack to monitor application traffic from hosts in the User zone destined to hosts in the Internet zone. In this scenario, which statement is true?
A) You must enable the AppTrack feature within the Internet zone configuration.
B) You must enable the AppTrack feature within the ingress interface configuration associated with the Internet zone.
C) You must enable the AppTrack feature within the interface configuration associated with the User zone.
D) You must enable the AppTrack feature within the User zone configuration.
A) You must enable the AppTrack feature within the Internet zone configuration.
B) You must enable the AppTrack feature within the ingress interface configuration associated with the Internet zone.
C) You must enable the AppTrack feature within the interface configuration associated with the User zone.
D) You must enable the AppTrack feature within the User zone configuration.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
73
You want to collect events and flows from third-party vendors. Which solution should you deploy to accomplish this task?
A) Log Director
B) JSA
C) Policy Enforcer
D) Contrail
A) Log Director
B) JSA
C) Policy Enforcer
D) Contrail

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
74
Which feature is used when you want to permit traffic on an SRX Series device only at specific times?
A) scheduler
B) pass-through authentication
C) ALGs
D) counters
A) scheduler
B) pass-through authentication
C) ALGs
D) counters

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
75
When referencing a SSL proxy profile in a security policy, which two statements are correct? (Choose two.)
A) A security policy can reference both a client-protection SSL proxy profile and a server-protection proxy profile.
B) If you apply an SSL proxy profile to a security policy and forget to apply any Layer7 services to the security policy, any encrypted traffic that matches the security policy is not decrypted.
C) A security policy can only reference a client-protection SSL proxy profile or a server-protection SSL proxy profile.
D) If you apply an SSL proxy profile to a security policy and forget to apply any Layer7 services to the security policy, any encrypted traffic that matches the security policy is decrypted.
A) A security policy can reference both a client-protection SSL proxy profile and a server-protection proxy profile.
B) If you apply an SSL proxy profile to a security policy and forget to apply any Layer7 services to the security policy, any encrypted traffic that matches the security policy is not decrypted.
C) A security policy can only reference a client-protection SSL proxy profile or a server-protection SSL proxy profile.
D) If you apply an SSL proxy profile to a security policy and forget to apply any Layer7 services to the security policy, any encrypted traffic that matches the security policy is decrypted.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
76
How many nodes are configurable in a chassis cluster using SRX Series devices?
A) 2
B) 4
C) 6
D) 8
A) 2
B) 4
C) 6
D) 8

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
77
Click the Exhibit button. 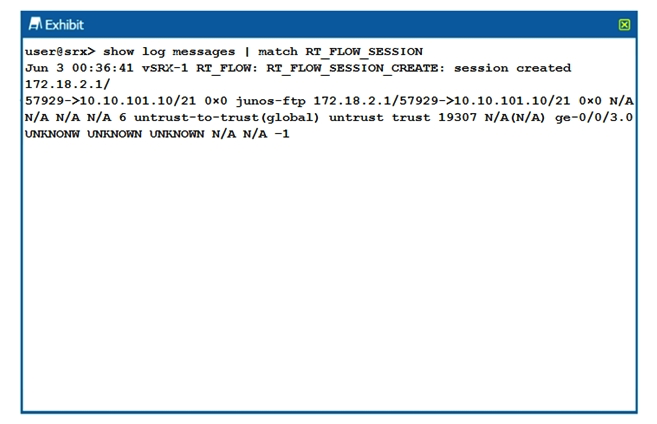 The output shown in the exhibit is displayed in which format?
The output shown in the exhibit is displayed in which format?
A) syslog
B) sd-syslog
C) binary
D) WELF
 The output shown in the exhibit is displayed in which format?
The output shown in the exhibit is displayed in which format?A) syslog
B) sd-syslog
C) binary
D) WELF

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
78
You must block the lateral spread of Remote Administration Tools (RATs) that use SMB to propagate within the network, using the JATP solution. Which action would accomplish this task?
A) Configure a new anti-virus configuration rule.
B) Configure whitelist rules
C) Configure YARA rules.
D) Configure the SAML settings.
A) Configure a new anti-virus configuration rule.
B) Configure whitelist rules
C) Configure YARA rules.
D) Configure the SAML settings.

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck
79
You have deployed JSA and you need to view events and network activity that match rule criteria. You must view this data using a single interface. Which JSA feature should you use in this scenario?
A) Log Collector
B) Assets
C) Network Activity
D) Offense Manager
A) Log Collector
B) Assets
C) Network Activity
D) Offense Manager

Unlock Deck
Unlock for access to all 79 flashcards in this deck.
Unlock Deck
k this deck


