Exam 5: Automation and DevOps, Associate
Exam 1: Junos, Associate (JNCIA-Junos)193 Questions
Exam 2: Data Center Design, Specialist (JNCDS-DC)74 Questions
Exam 3: Security Design, Specialist (JNCDS-SEC)69 Questions
Exam 4: Cloud, Associate33 Questions
Exam 5: Automation and DevOps, Associate79 Questions
Exam 6: Security, Associate (JNCIA-SEC)93 Questions
Exam 7: Mist AI, Associate (JNCIA-MistAI)131 Questions
Exam 8: Security, Specialist38 Questions
Exam 9: Enterprise Routing and Switching, Specialist39 Questions
Exam 10: Service Provider Routing and Switching, Specialist78 Questions
Exam 11: JCloud, Specialist (JNCIS-Cloud)46 Questions
Exam 12: Mist AI, Specialist93 Questions
Exam 13: Security, Professional57 Questions
Exam 14: Enterprise Routing and Switching, Professional (JNCIP-ENT)39 Questions
Exam 15: Service Provider Routing and Switching, Professional (JNCIP-SP)30 Questions
Exam 16: New Data Center, Professional39 Questions
Select questions type
Which zone is considered a functional zone?
Free
(Multiple Choice)
4.8/5  (36)
(36)
Correct Answer:
B
Which two statements are correct about using global-based policies over zone-based policies? (Choose two.)
Free
(Multiple Choice)
4.8/5  (40)
(40)
Correct Answer:
B,D
What must you do first to use the Monitor/Events workspace in the J-Web interface?
Free
(Multiple Choice)
4.8/5  (35)
(35)
Correct Answer:
B
When configuring IPsec VPNs, setting a hash algorithm solves which security concern?
(Multiple Choice)
5.0/5  (33)
(33)
Which two statements are correct about global security policies? (Choose two.)
(Multiple Choice)
4.7/5  (39)
(39)
Which feature is used when you want to permit traffic on an SRX Series device only at specific times?
(Multiple Choice)
4.7/5  (32)
(32)
Click the Exhibit button. 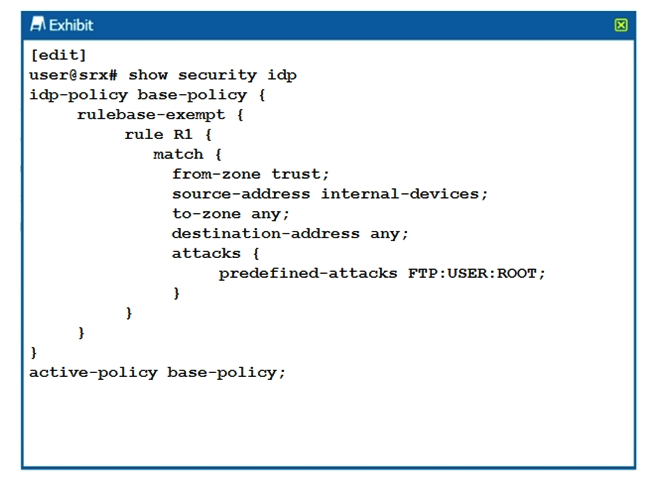 Referring to the exhibit, which statement is true?
Referring to the exhibit, which statement is true?
(Multiple Choice)
4.7/5  (32)
(32)
Which two statements are true about virtualized SRX Series devices? (Choose two.)
(Multiple Choice)
4.9/5  (28)
(28)
Users in your network are downloading files with file extensions that you consider to be unsafe for your network. You must prevent files with specific file extensions from entering your network. Which UTM feature should be enabled on an SRX Series device to accomplish this task?
(Multiple Choice)
4.9/5  (33)
(33)
Click the Exhibit button. 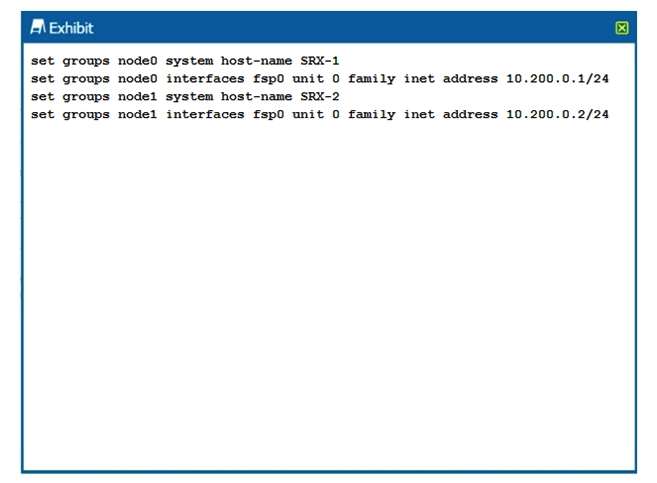 You are configuring an SRX chassis cluster with the node-specific hostname and management address. Referring to the exhibit, which configuration completes this requirement?
You are configuring an SRX chassis cluster with the node-specific hostname and management address. Referring to the exhibit, which configuration completes this requirement?
(Multiple Choice)
4.9/5  (39)
(39)
On an SRX Series device, how should you configure your IKE gateway if the remote endpoint is a branch office using a dynamic IP address?
(Multiple Choice)
4.8/5  (28)
(28)
Click the Exhibit button. 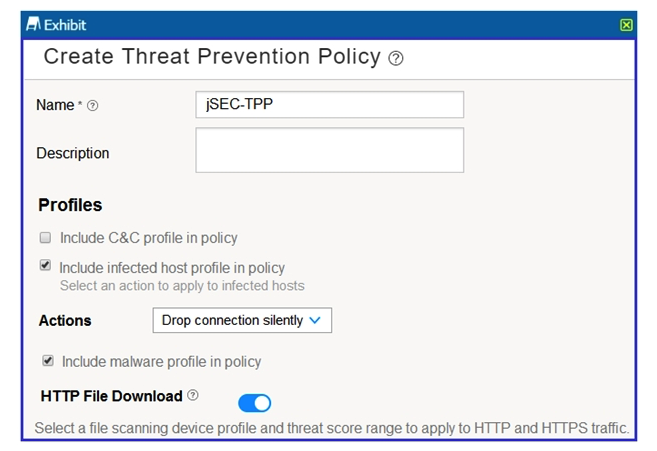 Referring to the exhibit, which statement is true?
Referring to the exhibit, which statement is true?
(Multiple Choice)
4.9/5  (28)
(28)
Which two statements describe how rules are used with Juniper Secure Analytics? (Choose two.)
(Multiple Choice)
4.9/5  (34)
(34)
Which statement describes the AppTrack module in AppSecure?
(Multiple Choice)
4.9/5  (28)
(28)
Click the Exhibit button. 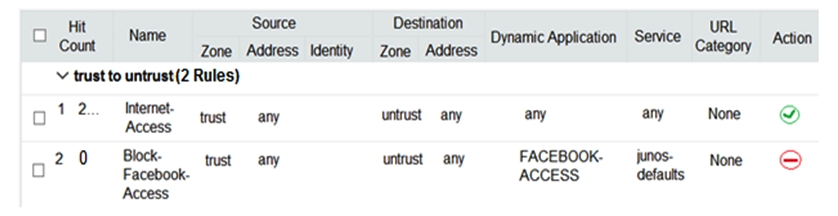 Users should not have access to Facebook, however, a recent examination of the security logs show that users are accessing Facebook. Referring to the exhibit, what should you do to solve this problem?
Users should not have access to Facebook, however, a recent examination of the security logs show that users are accessing Facebook. Referring to the exhibit, what should you do to solve this problem?
(Multiple Choice)
4.9/5  (39)
(39)
You must block the lateral spread of Remote Administration Tools (RATs) that use SMB to propagate within the network, using the JATP solution. Which action would accomplish this task?
(Multiple Choice)
4.8/5  (28)
(28)
Showing 1 - 20 of 79
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)