Deck 44: Deploying Cisco Unified Contact Center Express
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/660
Play
Full screen (f)
Deck 44: Deploying Cisco Unified Contact Center Express
1
As part of a new network design, you are helping the Network Management Team to develop a proactive report to identify places in the network where problems may happen. The network management tool can poll the network devices only via SNMP GET operations. Which two threshold- crossing metrics should you include in this report? (Choose two.)
A) packet loss
B) CPU utilization
C) heat dissipation
D) IP reachability
E) energy consumption
F) link bandwidth utilization
A) packet loss
B) CPU utilization
C) heat dissipation
D) IP reachability
E) energy consumption
F) link bandwidth utilization
CPU utilization
link bandwidth utilization
link bandwidth utilization
2
A company wants to connect two data center sites using a hub-and-spoke design with 2000 remote sites. One design consideration is the requirement to transfer MPLS packets over the public Internet. In addition, one router at each site should be used, and the MPLS packets must be encapsulated inside IP packets because the public Internet cannot transfer native MPLS packets. Which feature can be used to simplify the network design?
A) GET VPN can be used to encrypt the MPLS packets with IPsec.
B) DMVPN can be used to build up GRE tunnels dynamically with MPLS encapsulation inside.
C) L2TPv3 can be used to encapsulate the MPLS packets.
D) Site-to-site IPsec without GRE can be used to encapsulate the MPLS packets.
E) PPPoE can be used to encapsulate the MPLS packets.
A) GET VPN can be used to encrypt the MPLS packets with IPsec.
B) DMVPN can be used to build up GRE tunnels dynamically with MPLS encapsulation inside.
C) L2TPv3 can be used to encapsulate the MPLS packets.
D) Site-to-site IPsec without GRE can be used to encapsulate the MPLS packets.
E) PPPoE can be used to encapsulate the MPLS packets.
DMVPN can be used to build up GRE tunnels dynamically with MPLS encapsulation inside.
3
You are identifying performance management requirements for a VoIP migration. What three key performance indicators would you use to track media quality? (Choose three.)
A) delay
B) trunk group usage
C) jitter
D) packet loss
E) call processing (call detail records)
F) call processing (performance counters)
G) echo
H) crosstalk
A) delay
B) trunk group usage
C) jitter
D) packet loss
E) call processing (call detail records)
F) call processing (performance counters)
G) echo
H) crosstalk
delay
jitter
packet loss
jitter
packet loss
4
When creating a network design that routes an IGP over L2VPNs, with which device does the remote CE router form an IGP adjacency?
A) the hub site PE router
B) the hub site CE router
C) the directly connected PE router
D) The IGP will not establish adjacency over the MPLS network.
A) the hub site PE router
B) the hub site CE router
C) the directly connected PE router
D) The IGP will not establish adjacency over the MPLS network.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
5
A company plans to include Nonstop Forwarding and Bidirectional Forwarding Detection as a part of their network redundancy plan. In which two ways do NSF and BFD work together when different hardware platforms are compared? (Choose two.)
A) During supervisor engine or routing engine failover, the NSF feature will always ensure that the BFD at the peer router will not trigger a link down independent of the used hardware platform.
B) At some hardware platforms, BFD and NSF are not supported together. During supervisor engine or routing engine failover, the BFD at the peer router will trigger a link down.
C) To ensure that BFD at the peer router will not trigger a link down during NSF, the BFD packets must be processed fast enough, and, during supervisor engine or routing engine failover, by processing the BFD independent from the supervisor engine or routing engine.
D) Because BFD is always processed at the line cards (not at the supervisor engine or routing engine), a supervisor engine or routing engine failover will not affect the BFD peer router.
E) Because BFD is always processed at the supervisor engine or routing engine, a supervisor engine or routing engine failover will always trigger a link down at the peer router.
A) During supervisor engine or routing engine failover, the NSF feature will always ensure that the BFD at the peer router will not trigger a link down independent of the used hardware platform.
B) At some hardware platforms, BFD and NSF are not supported together. During supervisor engine or routing engine failover, the BFD at the peer router will trigger a link down.
C) To ensure that BFD at the peer router will not trigger a link down during NSF, the BFD packets must be processed fast enough, and, during supervisor engine or routing engine failover, by processing the BFD independent from the supervisor engine or routing engine.
D) Because BFD is always processed at the line cards (not at the supervisor engine or routing engine), a supervisor engine or routing engine failover will not affect the BFD peer router.
E) Because BFD is always processed at the supervisor engine or routing engine, a supervisor engine or routing engine failover will always trigger a link down at the peer router.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
6
Company X will be integrating an IPv6 application into their network and wants to develop a test environment to evaluate application performance across the network. This application will require both unicast and multicast communications. The company can do this implementation only in certain areas of its existing IPv4-only network, but wants all areas to communicate with each other. When developing the design to provide connectivity between these testing locations, what tunneling technology would work in this scenario?
A) ISATAP
B) 6to4
C) DMVPN
D) 6vPE
E) 6PE
A) ISATAP
B) 6to4
C) DMVPN
D) 6vPE
E) 6PE

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
7
You are designing a network using multipoint GRE tunnels and need to be able to detect when connectivity between the GRE tunnel endpoints is broken. Which statement is true about configuring keepalives for multipoint GRE tunnels?
A) The keepalive timer values on the routers must have the same value.
B) Both routers must support GRE tunnel keepalives.
C) No configuration is required to detect when connectivity is broken between the GRE tunnel endpoints.
D) GRE tunnel keepalives will not detect when connectivity is broken between the GRE tunnel endpoints.
A) The keepalive timer values on the routers must have the same value.
B) Both routers must support GRE tunnel keepalives.
C) No configuration is required to detect when connectivity is broken between the GRE tunnel endpoints.
D) GRE tunnel keepalives will not detect when connectivity is broken between the GRE tunnel endpoints.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
8
Your enterprise customer has asked where they should deploy flow monitoring in their network to monitor traffic between branch offices. What is your design recommendation?
A) at the edge of the network so that user traffic will be seen
B) at the central site, because all traffic from the remotes will be seen there.
C) in the core, because all traffic will be seen there
D) in the data center, because all user traffic will be seen there
A) at the edge of the network so that user traffic will be seen
B) at the central site, because all traffic from the remotes will be seen there.
C) in the core, because all traffic will be seen there
D) in the data center, because all user traffic will be seen there

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
9
You are working on a network design plan for a company with approximately 2000 sites. The sites will be connected using the public Internet. You plan to use private IP addressing in the network design, which will be routed without NAT through an encrypted WAN network. Some sites will be connected to the Internet with dynamic public IP addresses, and these addresses may change occasionally. Which VPN solution will support these design requirements?
A) GET VPN must be used, because DMVPN does not scale to 2000 sites.
B) DMVPN must be used, because GET VPN does not scale to 2000 sites.
C) GET VPN must be used, because private IP addresses cannot be transferred with DMVPN through the public Internet.
D) DMVPN must be used, because private IP addresses cannot be transferred with GET VPN through the public Internet.
E) GET VPN must be used, because DMVPN does not support dynamic IP addresses for some sites.
F) DMVPN must be used, because GET VPN does not support dynamic IP addresses for some sites.
A) GET VPN must be used, because DMVPN does not scale to 2000 sites.
B) DMVPN must be used, because GET VPN does not scale to 2000 sites.
C) GET VPN must be used, because private IP addresses cannot be transferred with DMVPN through the public Internet.
D) DMVPN must be used, because private IP addresses cannot be transferred with GET VPN through the public Internet.
E) GET VPN must be used, because DMVPN does not support dynamic IP addresses for some sites.
F) DMVPN must be used, because GET VPN does not support dynamic IP addresses for some sites.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
10
You are tasked with implementing a 1000-phone remote access solution, where phones will traverse a WAN edge router. Assuming all of the following features are supported in a hardware-assisted manner, which of the following will have the most detrimental impact on the delay of the packet?
A) encryption
B) stateful firewall
C) MPLS encapsulation
D) GRE encapsulation
A) encryption
B) stateful firewall
C) MPLS encapsulation
D) GRE encapsulation

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
11
You have been hired to redesign a network due to issues with congestion. How will a router function if the QoS mechanism of congestion avoidance is integrated into the existing network design?
A) the router handles the overflow of traffic by using FIFO
B) the router handles the possible buildup of congestion by using WRED
C) the router forces inbound and outbound traffic to stay within a defined profile by using rate limiting
D) the router separates packets based on certain characteristics by using NBAR
E) the router marks packets based on certain characteristics by using PBR
A) the router handles the overflow of traffic by using FIFO
B) the router handles the possible buildup of congestion by using WRED
C) the router forces inbound and outbound traffic to stay within a defined profile by using rate limiting
D) the router separates packets based on certain characteristics by using NBAR
E) the router marks packets based on certain characteristics by using PBR

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
12
You are a network designer and have been asked to consult with your server operations team to further enhance the security of the network. The operations team provides you with these details about the network: Which technology would you recommend to enhance security by limiting traffic that could originate from a hacker compromising a workstation and redirecting flows at the servers?
A) Access control lists to limit sources of traffic that exits the server-facing interface of the firewall cluster
B) Poison certain subnets by adding static routes to Null0 on the server farm core switches.
C) Unicast Reverse Path Forwarding in strict mode
D) Unicast Reverse Path Forwarding in loose mode
A) Access control lists to limit sources of traffic that exits the server-facing interface of the firewall cluster
B) Poison certain subnets by adding static routes to Null0 on the server farm core switches.
C) Unicast Reverse Path Forwarding in strict mode
D) Unicast Reverse Path Forwarding in loose mode

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
13
You are the lead network designer hired by Service Provider XYZ to deploy CoS functionality on the core MPLS network (P routers). The goal of the network design is to provide a complete CoS solution to all customers that purchase services such as dedicated internet access, MPLS L3VPN, and L2VPN (pseudowire). Service Provider XYZ has these design requirements: How would you design your solution to map the DSCP value properly so that the traffic is assigned to the respective queues in the Service Provider XYZ MPLS core network?
A) Classify traffic according to DSCP value into appropriate P router queues.
B) Map the appropriate DSCP value into the EXP field based on the number of queues in the MPLS P routers.
C) Map the appropriate DSCP value into the EXP field based on the number of queues in the MPLS PE routers.
D) Based on the DSCP value, traffic is mapped automatically into appropriate queues in the MPLS CE routers.
A) Classify traffic according to DSCP value into appropriate P router queues.
B) Map the appropriate DSCP value into the EXP field based on the number of queues in the MPLS P routers.
C) Map the appropriate DSCP value into the EXP field based on the number of queues in the MPLS PE routers.
D) Based on the DSCP value, traffic is mapped automatically into appropriate queues in the MPLS CE routers.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
14
In which two ways is IPv4 and IPv6 traffic handled in a network design that uses QoS deployment options? (Choose two.)
A) IPv6 and IPv4 traffic is treated in the same way by using a single QoS policy that classifies and matches on both protocols.
B) IPv6 traffic is treated differently than IPv4 by using the flow-label field, which is built into the IPv6 packet header.
C) IPv6 traffic does not require QoS because it uses to the flow-label field, which classifies and matches on the IPv6 protocol.
D) IPv6 traffic is treated differently than IPv4 by using two different QoS policies.
E) IPv6 traffic is treated differently than IPv4 because it uses only the DSCP value and not the IP precedence.
A) IPv6 and IPv4 traffic is treated in the same way by using a single QoS policy that classifies and matches on both protocols.
B) IPv6 traffic is treated differently than IPv4 by using the flow-label field, which is built into the IPv6 packet header.
C) IPv6 traffic does not require QoS because it uses to the flow-label field, which classifies and matches on the IPv6 protocol.
D) IPv6 traffic is treated differently than IPv4 by using two different QoS policies.
E) IPv6 traffic is treated differently than IPv4 because it uses only the DSCP value and not the IP precedence.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
15
You have been hired by Acme Corporation to evaluate their existing network and determine if the current network design is secure enough to prevent man-in-the-middle attacks. When evaluating the network, which switch security option should you investigate to ensure that authorized ARP responses take place according to known IP-to-MAC address mapping?
A) ARP rate limiting
B) DHCP snooping
C) Dynamic ARP Inspections
D) IP Source Guard
A) ARP rate limiting
B) DHCP snooping
C) Dynamic ARP Inspections
D) IP Source Guard

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
16
Service provider XYZ plans to provide dedicated Internet access and MPLS L3VPN services to business customers. XYZ has these design specifications: In what two ways can the MP-BGP be removed from the MPLS P core routers and still provide dedicated Internet access and MPLS L3VPN services? (Choose two.)
A) Disable BGP from the MPLS core P routers and have the MPLS core P routers run OSPF and LDP.
B) Enable separate BGP control plane routers using a route reflector server concept that will be fully meshed with peer route reflector servers and have clients as MPLS PE routers and EBGP peering routers.
C) Enable all EBGP routers as route reflector servers and MPLS PE routers as their clients.
D) It is not possible to disable BGP from the MPLS core P routers without impacting the dedicated Internet access and MPLS L3VPN services.
A) Disable BGP from the MPLS core P routers and have the MPLS core P routers run OSPF and LDP.
B) Enable separate BGP control plane routers using a route reflector server concept that will be fully meshed with peer route reflector servers and have clients as MPLS PE routers and EBGP peering routers.
C) Enable all EBGP routers as route reflector servers and MPLS PE routers as their clients.
D) It is not possible to disable BGP from the MPLS core P routers without impacting the dedicated Internet access and MPLS L3VPN services.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
17
You are designing a Group Encrypted Transport virtual private network solution for an existing branch network. The existing network has the following characteristics: Which additional routing protocol would you use for the overlay routing between the group members?
A) Open Shortest Path First (with a different process ID)
B) Enhanced Interior Gateway Routing Protocol
C) No additional protocol is necessary.
D) External Border Gateway Protocol
E) Routing Information Protocol Version 2
F) Next Hop Resolution Protocol
A) Open Shortest Path First (with a different process ID)
B) Enhanced Interior Gateway Routing Protocol
C) No additional protocol is necessary.
D) External Border Gateway Protocol
E) Routing Information Protocol Version 2
F) Next Hop Resolution Protocol

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
18
Refer to the exhibit. 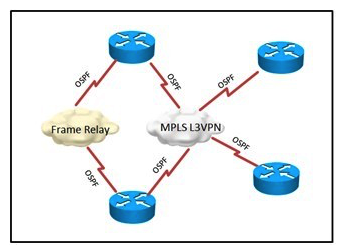 An enterprise is migrating its single-area OSPF network from a Frame Relay WAN service to an MPLS L3VPN service. Frame Relay will remain in only a few sites that require increased resiliency via two different WAN connections. Which feature could be used in the ?MPLS VPN service provider network to support the design requirement by ensuring that during normal operation, intersite traffic will only use the MPLS VPN service and not the old Frame Relay service?
An enterprise is migrating its single-area OSPF network from a Frame Relay WAN service to an MPLS L3VPN service. Frame Relay will remain in only a few sites that require increased resiliency via two different WAN connections. Which feature could be used in the ?MPLS VPN service provider network to support the design requirement by ensuring that during normal operation, intersite traffic will only use the MPLS VPN service and not the old Frame Relay service?
A) virtual links
B) sham links
C) multiple stub areas
D) super backbone
 An enterprise is migrating its single-area OSPF network from a Frame Relay WAN service to an MPLS L3VPN service. Frame Relay will remain in only a few sites that require increased resiliency via two different WAN connections. Which feature could be used in the ?MPLS VPN service provider network to support the design requirement by ensuring that during normal operation, intersite traffic will only use the MPLS VPN service and not the old Frame Relay service?
An enterprise is migrating its single-area OSPF network from a Frame Relay WAN service to an MPLS L3VPN service. Frame Relay will remain in only a few sites that require increased resiliency via two different WAN connections. Which feature could be used in the ?MPLS VPN service provider network to support the design requirement by ensuring that during normal operation, intersite traffic will only use the MPLS VPN service and not the old Frame Relay service?A) virtual links
B) sham links
C) multiple stub areas
D) super backbone

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
19
Refer to the exhibit. 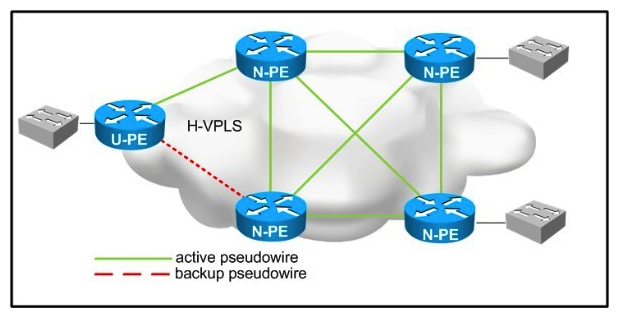 You are designing a loop-free hierarchical VPLS service. Which two design considerations should be implemented for the pseudowires between the N-PE and U-PE routers? (Choose two.)
You are designing a loop-free hierarchical VPLS service. Which two design considerations should be implemented for the pseudowires between the N-PE and U-PE routers? (Choose two.)
A) Disable split horizon toward the N-PE routers.
B) Disable split horizon toward the U-PE router.
C) Enable split horizon toward the U-PE router.
D) Enable split horizon toward the N-PE routers.
E) Disable MAC learning on the U-PE route.
F) Disable MAC learning on the N-PE routers.
 You are designing a loop-free hierarchical VPLS service. Which two design considerations should be implemented for the pseudowires between the N-PE and U-PE routers? (Choose two.)
You are designing a loop-free hierarchical VPLS service. Which two design considerations should be implemented for the pseudowires between the N-PE and U-PE routers? (Choose two.)A) Disable split horizon toward the N-PE routers.
B) Disable split horizon toward the U-PE router.
C) Enable split horizon toward the U-PE router.
D) Enable split horizon toward the N-PE routers.
E) Disable MAC learning on the U-PE route.
F) Disable MAC learning on the N-PE routers.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
20
A network designer has provisioned a router to use IPsec to encrypt the traffic over a GRE tunnel going to a web server at a remote location. From the router, the network designer can ping the web server, although the users in the office comment that they are unable to reach it. (Note: The DF bit is not set.) Which aspect should be changed in the design of the virtual connection?
A) IP addresses of the GRE tunnel endpoints
B) IPsec configuration
C) MTU size on the GRE tunnel
D) encapsulation of the GRE tunnel
A) IP addresses of the GRE tunnel endpoints
B) IPsec configuration
C) MTU size on the GRE tunnel
D) encapsulation of the GRE tunnel

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
21
You are designing an optical network. Your goal is to ensure that your design contains the highest degree of resiliency. In which two ways will you leverage a wavelength-switched optical network solution in your network design? (Choose two.)
A) a wavelength-switched optical network assigns routing and wavelength information
B) a wavelength-switched optical network takes linear and nonlinear optical impairment calculation into account
C) a wavelength-switched optical network guarantees restoration based strictly on the shortest path available
D) a wavelength-switched optical network eliminates the need for dispersion compensating units in a network
A) a wavelength-switched optical network assigns routing and wavelength information
B) a wavelength-switched optical network takes linear and nonlinear optical impairment calculation into account
C) a wavelength-switched optical network guarantees restoration based strictly on the shortest path available
D) a wavelength-switched optical network eliminates the need for dispersion compensating units in a network

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
22
If a network design must support rapid convergence on half-duplex interfaces, which IEEE 802.1w capability should be used?
A) root guard
B) proposal-agreement handshake
C) loop guard
D) UplinkFast
A) root guard
B) proposal-agreement handshake
C) loop guard
D) UplinkFast

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
23
Which mechanism should be added to a network design to identify unidirectional Spanning Tree Protocol failures through BPDU loss?
A) UDLD
B) loop guard
C) BPDU guard?
D) root guard
A) UDLD
B) loop guard
C) BPDU guard?
D) root guard

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
24
When creating a design plan for IPv6 integration, you decide to use stateless encapsulation of IPv6 packets into IPv4 tunnels between subscriber CPEs and a border relay. Which deployment technique allows for this functionality?
A) 6rd
B) Dual-Stack Lite
C) 4rd
D) DSTM
A) 6rd
B) Dual-Stack Lite
C) 4rd
D) DSTM

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
25
You are the SAN designer for the ABC Company. Due to budget constraints, there is increased pressure by management to further optimize server utilization by implementing virtualization technologies on all servers and increase virtual machines density. Faced with some SAN challenges, the server team requests your help in the design and implementation of the SAN in the new virtualized environment. In which two ways can NPIV be used in your proposed design? (Choose two.)
A) NPIV is used to assign multiple FCIDs to a single N Port.
B) NPIV is used to define and bind multiple virtual WWNs (VIs) to a single physical pWWN.
C) You recommend NPIV so that hosts can be members of different zones.
D) NPIV can be used to allow multiple applications on the same port to use different IDs in the same VSAN.
A) NPIV is used to assign multiple FCIDs to a single N Port.
B) NPIV is used to define and bind multiple virtual WWNs (VIs) to a single physical pWWN.
C) You recommend NPIV so that hosts can be members of different zones.
D) NPIV can be used to allow multiple applications on the same port to use different IDs in the same VSAN.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
26
When developing an MVPN design, which performance and scalability consideration must be taken into account?
A) CE end-to-end PIM adjacency establishment
B) multicast data sent to all PE routers on the default MDT
C) RP placement in the multicast VRF
D) RP placement in the customer network
A) CE end-to-end PIM adjacency establishment
B) multicast data sent to all PE routers on the default MDT
C) RP placement in the multicast VRF
D) RP placement in the customer network

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
27
You are designing a wireless LAN with the following components: Site survey results show negligible foreign WiFi and non-WiFi interference. What is the best method to decrease duty cycle (radio frequency utilization) and increase overall wireless LAN client performance for this design?
A) Disable all data rates below 12 Mb/s on all access points.
B) Decrease radio transmit power on all access points that report a high duty cycle.
C) Increase radio transmit power on all access points that report a high duty cycle.
D) Disable all data rates above 12 Mb/s on all access points.
E) Increase radio transmit power on all access points.
A) Disable all data rates below 12 Mb/s on all access points.
B) Decrease radio transmit power on all access points that report a high duty cycle.
C) Increase radio transmit power on all access points that report a high duty cycle.
D) Disable all data rates above 12 Mb/s on all access points.
E) Increase radio transmit power on all access points.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
28
A metro service provider is planning Resilient Ethernet Protocol for his backbone. Which two aspects must be considered before the network design is finalized? (Choose two.)
A) Two Resilient Ethernet Protocol segments can be connected redundantly at two points. One connection will be blocked, using the Spanning Tree Protocol defined in IEEE 802.1D.
B) UniDirectional Link Detection Protocol can be enabled on Resilient Ethernet Protocol interfaces to detect unidirectional failures.
C) The guaranteed convergence recovery time is less than 50 ms for the local segment.
D) A Resilient Ethernet Protocol segment is limited to a maximum of seven devices.
E) VLAN load balancing for optimal bandwidth usage is supported in any Resilient Ethernet Protocol segment.
A) Two Resilient Ethernet Protocol segments can be connected redundantly at two points. One connection will be blocked, using the Spanning Tree Protocol defined in IEEE 802.1D.
B) UniDirectional Link Detection Protocol can be enabled on Resilient Ethernet Protocol interfaces to detect unidirectional failures.
C) The guaranteed convergence recovery time is less than 50 ms for the local segment.
D) A Resilient Ethernet Protocol segment is limited to a maximum of seven devices.
E) VLAN load balancing for optimal bandwidth usage is supported in any Resilient Ethernet Protocol segment.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
29
Tesla Radio GmbH is going to build a new research lab network based on a set of switches that would connect to their existing enterprise network. They are considering a design that would guarantee loop- free behavior within the set of switches. The design would also allow the group of switches to seem like a single switch to the enterprise network, because it is owned by a separate administrative group. Which Spanning Tree Protocol should be used to support the design requirements?
A) IEEE 802.1w
B) IEEE 802.1D
C) IEEE 802.1s
D) IEEE 802.1p
A) IEEE 802.1w
B) IEEE 802.1D
C) IEEE 802.1s
D) IEEE 802.1p

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
30
A company wants to use SSM as the multicast routing protocol inside its network. Some of its multicast applications do not support IGMPv3. In which two ways can the mapping be done when these applications send IGMPv2 join messages? (Choose two.)
A) The Layer 2 switches can send a request to a DNS server.
B) The Layer 3 multicast routers can send a request to a DNS server.
C) The mapping can be done statically at the Layer 2 switches.
D) The mapping can be done statically at the Layer 3 multicast routers.
E) The Layer 2 switches can transform the IGMPv2 join to an IGMPv3lite join.
F) The Layer 3 multicast routers can transform the IGMPv2 join to an IGMPv3lite join.
A) The Layer 2 switches can send a request to a DNS server.
B) The Layer 3 multicast routers can send a request to a DNS server.
C) The mapping can be done statically at the Layer 2 switches.
D) The mapping can be done statically at the Layer 3 multicast routers.
E) The Layer 2 switches can transform the IGMPv2 join to an IGMPv3lite join.
F) The Layer 3 multicast routers can transform the IGMPv2 join to an IGMPv3lite join.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
31
A company plans to use BFD between its routers to detect a connectivity problem inside the switched network. An IPS is transparently installed between the switches. Which packets should the IPS forward for BFD to work under all circumstances?
A) IP packets with broadcast IP source addresses
B) IP packets with identical source and destination IP addresses
C) fragmented packets with the do-not-fragment bit set
D) IP packets with the multicast IP source address
E) IP packets with the multicast IP destination address
F) IP packets with the destination IP address 0.0.0.0
A) IP packets with broadcast IP source addresses
B) IP packets with identical source and destination IP addresses
C) fragmented packets with the do-not-fragment bit set
D) IP packets with the multicast IP source address
E) IP packets with the multicast IP destination address
F) IP packets with the destination IP address 0.0.0.0

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
32
You are designing a Group Encrypted Transport Virtual Private Network solution consisting of 30 group members. Which measure helps protect encrypted user traffic from replay attacks?
A) counter-based anti-replay
B) time-based anti-replay
C) nonce payload
D) RSA-encrypted nonce
E) digital certificates
A) counter-based anti-replay
B) time-based anti-replay
C) nonce payload
D) RSA-encrypted nonce
E) digital certificates

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
33
A company has these requirements for access to their wireless and wired corporate LANs using 802.1x: Which solution meets these requirements?
A) Protected Extensible Authentication Protocol/Microsoft Challenge Handshake Authentication Protocol Version 2 with user authentication
B) Extensible Authentication Protocol-Transport Layer Security with machine authentication
C) Extensible Authentication Protocol-Transport Layer Security with user authentication
D) Protected Extensible Authentication Protocol/Microsoft Challenge Handshake Authentication Protocol Version 2 with machine authentication
A) Protected Extensible Authentication Protocol/Microsoft Challenge Handshake Authentication Protocol Version 2 with user authentication
B) Extensible Authentication Protocol-Transport Layer Security with machine authentication
C) Extensible Authentication Protocol-Transport Layer Security with user authentication
D) Protected Extensible Authentication Protocol/Microsoft Challenge Handshake Authentication Protocol Version 2 with machine authentication

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
34
You are designing a network for a branch office. In order to improve convergence time, you are required to use the BFD feature. Which four routing protocols can you use to facilitate this? (Choose four.)
A) EIGRP
B) IS-IS
C) BGP
D) static
E) RIP
A) EIGRP
B) IS-IS
C) BGP
D) static
E) RIP

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
35
In an MPLS-VPN environment, what is the effect of configuring an identical set of route targets for a particular VRF, but then configuring nonidentical route distinguisher across multiple PE devices?
A) The routes will be correctly handled by the control plane, but there will be instances where routes take up twice as much memory.
B) The routes will propagate to the remote PE, but the PE will never install them in its forwarding table.
C) The routes will be rejected by the remote PE because they have a different RD than its routes.
D) The routes will not even be sent to any remote PE with a different RD.
A) The routes will be correctly handled by the control plane, but there will be instances where routes take up twice as much memory.
B) The routes will propagate to the remote PE, but the PE will never install them in its forwarding table.
C) The routes will be rejected by the remote PE because they have a different RD than its routes.
D) The routes will not even be sent to any remote PE with a different RD.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
36
You are the lead IP/MPLS network designer of a service provider called XYZ. You are leading a design discussion regarding IPv6 implementation in the XYZ MPLS network, using MPLS 6PE/6VPE techniques. Currently, XYZ provides IPv4 multicast services over an MPLS network by using MVPN, and would like to provide parallel IPv6 multicast services. Which three multicast solutions should be enabled? (Choose three.)
A) native IPv6, only for multicast services
B) MPLS 6PE/6VPE, because it provides IPv6 multicast support by default
C) an overlay model using Layer 2 MPLS tunnels
D) PIM-DM to enable IPv6 multicast in conjunction with MPLS 6PE/6VPE
E) MVPN for IPv6 multicast service
A) native IPv6, only for multicast services
B) MPLS 6PE/6VPE, because it provides IPv6 multicast support by default
C) an overlay model using Layer 2 MPLS tunnels
D) PIM-DM to enable IPv6 multicast in conjunction with MPLS 6PE/6VPE
E) MVPN for IPv6 multicast service

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
37
ACME Corporation is integrating IPv6 into their network, which relies heavily on multicast distribution of data. Which two IPv6 integration technologies support IPv6 multicast? (Choose two.)
A) 6VPE
B) 6PE
C) dual stack
D) ISATAP
E) 6to4
F) IPv6INIP
A) 6VPE
B) 6PE
C) dual stack
D) ISATAP
E) 6to4
F) IPv6INIP

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
38
Network designers plan to interconnect two geographically separated data centers using an Ethernet- over-MPLS pseudowire. Within that design, the link between the sites is stable, there are no apparent loops in the topology, and the root bridges for the respective VLANs are stable and unchanging. What additional aspect of the design should be adjusted to mitigate the chance of connectivity issues to the peer data center when the connection takes place?
A) Enable 802.1d on one data center, and 802.1w on the other.
B) Ensure that the spanning tree diameter for one or more VLANs is not too large.
C) Enable UDLD on the link between the data centers.
D) Enable root guard on the link between the data centers.
A) Enable 802.1d on one data center, and 802.1w on the other.
B) Ensure that the spanning tree diameter for one or more VLANs is not too large.
C) Enable UDLD on the link between the data centers.
D) Enable root guard on the link between the data centers.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
39
What is a design aspect regarding multicast transport for MPLS Layer 3 VPNs using the Rosen Draft implementation?
A) LDP is the multicast control plane protocol.
B) Multicast traffic is forwarded over GRE tunnels.
C) Multicast traffic is forwarded over LDP or RSVP signaled LSPs.
D) Using the MDT SAFI in BGP ensures that PIM can be disabled in the core.
A) LDP is the multicast control plane protocol.
B) Multicast traffic is forwarded over GRE tunnels.
C) Multicast traffic is forwarded over LDP or RSVP signaled LSPs.
D) Using the MDT SAFI in BGP ensures that PIM can be disabled in the core.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
40
In order to meet your service level agreement, your network designer created a design solution that includes interface dampening. In which two ways will interface dampening benefit your overall network design? (Choose two.)
A) Interface dampening uses an exponential backoff algorithm to suppress event reporting to the upper- level protocols.
B) When the interface is dampened, further link events are not reported to the upper protocol modules.
C) When the interface is dampened, further link events are reported to the upper protocol module.
D) Periodic interface flapping that affects the routing system as a whole should have a period shorter than the system convergence time.
A) Interface dampening uses an exponential backoff algorithm to suppress event reporting to the upper- level protocols.
B) When the interface is dampened, further link events are not reported to the upper protocol modules.
C) When the interface is dampened, further link events are reported to the upper protocol module.
D) Periodic interface flapping that affects the routing system as a whole should have a period shorter than the system convergence time.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
41
After the recent implementation of a new design that incorporated GRE tunnels into the network, the network operations staff is seeing the following syslog message in multiple routers on the network - %TUN-5-RECURDOWN: Tunnel0 temporarily disabled due to recursive routing. From a design perspective, what was not taken into account prior to implementing the solution?
A) The neighboring routers cannot respond within the specified hold time.
B) The interface on the router that is the source of the tunnel is down.
C) The interface on the neighboring router that is the source of the tunnel is down.
D) The router is learning the route to the tunnel destination address using the tunnel interface.
E) The tunnel interface on the router is not receiving any keepalives within the specified hold time.
A) The neighboring routers cannot respond within the specified hold time.
B) The interface on the router that is the source of the tunnel is down.
C) The interface on the neighboring router that is the source of the tunnel is down.
D) The router is learning the route to the tunnel destination address using the tunnel interface.
E) The tunnel interface on the router is not receiving any keepalives within the specified hold time.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
42
A company wants a design that would support OSPF through a service provider ATM network. Which two OSPF network types should the designer use to establish OSPF neighborship between OSPF routers through the ATM network? (Choose two.)
A) A broadcast network will always work through ATM networks.
B) A broadcast network will work when the broadcast support is explicitly configured at the ATM network.
C) Explicit neighbor statements are required when a nonbroadcast network is configured.
D) Explicit neighbor statements are required when a point-to-multipoint network is configured.
E) A nonbroadcast network does not require DR selection.
A) A broadcast network will always work through ATM networks.
B) A broadcast network will work when the broadcast support is explicitly configured at the ATM network.
C) Explicit neighbor statements are required when a nonbroadcast network is configured.
D) Explicit neighbor statements are required when a point-to-multipoint network is configured.
E) A nonbroadcast network does not require DR selection.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
43
Which two features can be used to extend VRFs across a campus? (Choose two.)
A) 802.1q trunks
B) LDP
C) MPLS TE
D) GRE
E) port channels
A) 802.1q trunks
B) LDP
C) MPLS TE
D) GRE
E) port channels

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
44
Refer to the exhibit. 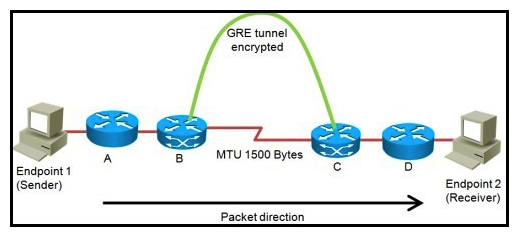 You are planning the design of an encrypted WAN. IP packets will be transferred over encrypted GRE tunnels between routers B and C. The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C. If endpoint 1 tries to send 1500-byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations? (Choose three.)
You are planning the design of an encrypted WAN. IP packets will be transferred over encrypted GRE tunnels between routers B and C. The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C. If endpoint 1 tries to send 1500-byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations? (Choose three.)
A) When router B fragments packets after the encryption, router C must reassemble these fragmented packets.
B) When router B fragments packets before the encryption, router C must reassemble these fragmented packets.
C) When router B fragments packets after the encryption, the endpoint 2 must reassemble these fragmented packets.
D) When router B fragments packets before the encryption, endpoint 2 must reassemble these fragmented packets.
E) When router A fragments packets, router C must reassemble these fragmented packets.
F) When router A fragments packets, endpoint 2 must reassemble these fragmented packets.
 You are planning the design of an encrypted WAN. IP packets will be transferred over encrypted GRE tunnels between routers B and C. The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C. If endpoint 1 tries to send 1500-byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations? (Choose three.)
You are planning the design of an encrypted WAN. IP packets will be transferred over encrypted GRE tunnels between routers B and C. The packet size is limited to a maximum of 1500 bytes inside the WAN between routers B and C. If endpoint 1 tries to send 1500-byte IP packets to endpoint 2, in what three ways will the network design handle the fragmentation in three different possible network configurations? (Choose three.)A) When router B fragments packets after the encryption, router C must reassemble these fragmented packets.
B) When router B fragments packets before the encryption, router C must reassemble these fragmented packets.
C) When router B fragments packets after the encryption, the endpoint 2 must reassemble these fragmented packets.
D) When router B fragments packets before the encryption, endpoint 2 must reassemble these fragmented packets.
E) When router A fragments packets, router C must reassemble these fragmented packets.
F) When router A fragments packets, endpoint 2 must reassemble these fragmented packets.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
45
You are designing a multisite VPN solution for a customer and you are concerned with the additional overhead of point-to-point tunnels and the associated overlay routing with DMVPN. How does a GDOI-based VPN eliminate the additional tunnel and routing overhead found in DMVPN?
A) The GDOI-based VPN requires overlaying a secondary routing infrastructure through the tunnels.
B) In a GDOI-based VPN, all group members share a common security association.
C) The GDOI-based VPN requires the provisioning of a complex connectivity mesh.
D) The GDOI-based VPN leverages the routing protocol to find its peer for tunnel setup.
A) The GDOI-based VPN requires overlaying a secondary routing infrastructure through the tunnels.
B) In a GDOI-based VPN, all group members share a common security association.
C) The GDOI-based VPN requires the provisioning of a complex connectivity mesh.
D) The GDOI-based VPN leverages the routing protocol to find its peer for tunnel setup.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
46
A many-to-many enterprise messaging application is using multicast as a transport mechanism. As part of the network design for this application, which multicast address should be used, according to best practices outlined in RFC 2365?
A) 224.0.0.60
B) 232.192.0.60
C) 239.128.0.60
D) 239.193.0.60
A) 224.0.0.60
B) 232.192.0.60
C) 239.128.0.60
D) 239.193.0.60

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
47
A company plans to establish a new network using Cisco Catalyst switches for its multicast applications. What is the disadvantage when two multicast applications are using the multicast IP addresses 234.17.4.5 and 234.145.4.5 inside the same network?
A) Multicast packets from both applications are flooded to all Layer 2 ports in a segment where a multicast receiver is located.
B) Multicast packets from both applications are flooded to ports where one multicast receiver from one application is located.
C) Only one multicast stream is received at the port where the receivers from both applications are located.
D) Both multicast senders will always receive the multicast packets from the other multicast application.
E) The routers doing PIM-SM cannot distinguish between the two multicast applications.
A) Multicast packets from both applications are flooded to all Layer 2 ports in a segment where a multicast receiver is located.
B) Multicast packets from both applications are flooded to ports where one multicast receiver from one application is located.
C) Only one multicast stream is received at the port where the receivers from both applications are located.
D) Both multicast senders will always receive the multicast packets from the other multicast application.
E) The routers doing PIM-SM cannot distinguish between the two multicast applications.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
48
What is a key design aspect to be considered when designing an IP network that will be carrying real- time VoIP traffic?
A) Minimizing total bidirectional end-to-end delay to 0-150 ms
B) Minimizing total unidirectional end-to-end delay to 150-500 ms
C) Minimizing total bidirectional end-to-end delay to 0-50 ms
D) Minimizing total unidirectional end-to-end delay to 0-150 ms
A) Minimizing total bidirectional end-to-end delay to 0-150 ms
B) Minimizing total unidirectional end-to-end delay to 150-500 ms
C) Minimizing total bidirectional end-to-end delay to 0-50 ms
D) Minimizing total unidirectional end-to-end delay to 0-150 ms

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
49
What is a key role for the access layer in a hierarchical network design?
A) The access layer provides a security, QoS, and policy trust boundary.
B) The access layer provides an aggregation point for services and applications.
C) The access layer serves as a distribution point for services and applications.
D) The access layer can be used to aggregate remote users.
A) The access layer provides a security, QoS, and policy trust boundary.
B) The access layer provides an aggregation point for services and applications.
C) The access layer serves as a distribution point for services and applications.
D) The access layer can be used to aggregate remote users.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
50
A company is planning to connect its 30 sites with a VPLS WAN backbone. A router at each site should establish neighborships with all other routers using the OSPF routing protocol. Which three points must be considered regarding DR and BDR when different router platforms are used? (Choose three.)
A) It is a best practice that the routers with the most powerful hardware should take the role of the DR and BDR.
B) If the IP OSPF priority is the same for all routers, the highest loopback IP address and router ID will decide which routers will take the DR and BDR role during the selection process.
C) To select the DR and BDR, the IP OSPF priority must be set to a higher value than the default value at the DR and BDR during the selection process.
D) To select the DR and BDR, the IP OSPF priority must be set to a lower value than the default value at the DR and BDR during the selection process.
E) The role for the DR and BDR will be selected when a new OSPF router comes up.
F) To force two routers to become a DR and a BDR, the IP OSPF priority can be set to zero at all other OSPF routers.
A) It is a best practice that the routers with the most powerful hardware should take the role of the DR and BDR.
B) If the IP OSPF priority is the same for all routers, the highest loopback IP address and router ID will decide which routers will take the DR and BDR role during the selection process.
C) To select the DR and BDR, the IP OSPF priority must be set to a higher value than the default value at the DR and BDR during the selection process.
D) To select the DR and BDR, the IP OSPF priority must be set to a lower value than the default value at the DR and BDR during the selection process.
E) The role for the DR and BDR will be selected when a new OSPF router comes up.
F) To force two routers to become a DR and a BDR, the IP OSPF priority can be set to zero at all other OSPF routers.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
51
Which restriction prevents a designer from using a GDOI-based VPN to secure traffic that traverses the Internet?
A) Enterprise host IP addresses are typically not routable.
B) GDOI is less secure than traditional IPsec.
C) Network address translation functions interfere with tunnel header preservation.
D) The use of public addresses is not supported with GDOI.
A) Enterprise host IP addresses are typically not routable.
B) GDOI is less secure than traditional IPsec.
C) Network address translation functions interfere with tunnel header preservation.
D) The use of public addresses is not supported with GDOI.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
52
You have been tasked to create a Layer 2 network design that uses vPC to provide resiliency and avoid loops. vPC removes Layer 2 loops while providing redundancy through which mechanism?
A) dual-active detection
B) address synchronization
C) strict forwarding rules
D) Bridge Assurance
A) dual-active detection
B) address synchronization
C) strict forwarding rules
D) Bridge Assurance

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
53
When a design calls for spanning VLANs across a campus network, what are two issues that need to be addressed in the design? (Choose two.)
A) network convergence
B) network accessibility
C) fault isolation
D) application scalability
E) user experience
A) network convergence
B) network accessibility
C) fault isolation
D) application scalability
E) user experience

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
54
A green data center is being deployed and a design requirement is to be able to readily scale server virtualization. Which IETF standard technology can provide this requirement?
A) Transparent Interconnection of Lots of Links
B) fabric path
C) data center bridging
D) unified fabric
A) Transparent Interconnection of Lots of Links
B) fabric path
C) data center bridging
D) unified fabric

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
55
Refer to the exhibit. 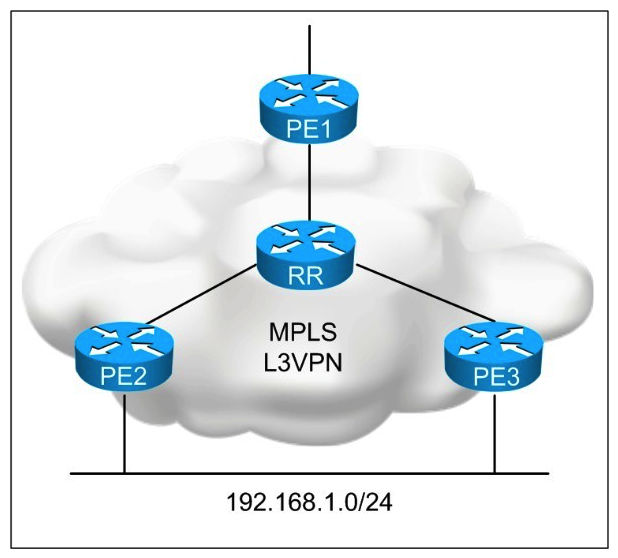 You are designing an IPv4 unicast Layer 3 VPN load-balancing solution. Which L3VPN feature needs to be configured on the PE routers to support the design requirement?
You are designing an IPv4 unicast Layer 3 VPN load-balancing solution. Which L3VPN feature needs to be configured on the PE routers to support the design requirement?
A) nonmatching route distinguishers
B) matching route target values
C) disable split horizon on PE2 and PE3
D) matching route distinguishers
 You are designing an IPv4 unicast Layer 3 VPN load-balancing solution. Which L3VPN feature needs to be configured on the PE routers to support the design requirement?
You are designing an IPv4 unicast Layer 3 VPN load-balancing solution. Which L3VPN feature needs to be configured on the PE routers to support the design requirement?A) nonmatching route distinguishers
B) matching route target values
C) disable split horizon on PE2 and PE3
D) matching route distinguishers

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
56
You are designing the QoS features for a large enterprise network that includes DMVPN. When would you need to configure QoS preclassify?
A) when you are marking packets with the DSCP bits
B) when you are marking packets with the TOS bits
C) when your service provider requires the DSCP bits be set
D) when the QoS policy cannot be based on DSCP ToS bits
A) when you are marking packets with the DSCP bits
B) when you are marking packets with the TOS bits
C) when your service provider requires the DSCP bits be set
D) when the QoS policy cannot be based on DSCP ToS bits

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
57
A network administrator is in charge of multiple IPsec VPN headend devices that service thousands of remote connectivity, point-to-point, IPsec/GRE tunnels. During a recent power outage, in which it was found that a backup power supply in one of those headend devices was faulty, one of the headend routers suffered a complete shutdown event. When the router was successfully recovered, remote users found intermittent connectivity issues that went away after several hours. Network operations staff accessed the headend devices and found that the recently recovered unit was near 100% CPU for a long period of time. How would you redesign the network VPN headend devices to prevent this from happening again in the future?
A) Move the tunnels more evenly across the headend devices.
B) Implement Call Admission Control.
C) Use the scheduler allocate command to curb CPU usage.
D) Change the tunnels to DMVPN.
A) Move the tunnels more evenly across the headend devices.
B) Implement Call Admission Control.
C) Use the scheduler allocate command to curb CPU usage.
D) Change the tunnels to DMVPN.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
58
You are asked to design a large campus network that will be using multicast for data transport. Which feature should be enabled at the Layer 2 access edge for host-only ports?
A) PortFast
B) BPDU guard
C) PIM-SM
D) PIM query interval
A) PortFast
B) BPDU guard
C) PIM-SM
D) PIM query interval

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
59
Which technique can you use to detect forwarding path failures at a uniform rate, and reconvergence times will be consistent and predictable when your routers are in the same broadcast domain?
A) Enable BFD on your routers.
B) Configure your routers with IP-SLA to ping the peer router.
C) Configure your routers with IP-SLA and track to ping the peer and switch to a default route if the pings fail.
D) Tune your routing protocol timers.
A) Enable BFD on your routers.
B) Configure your routers with IP-SLA to ping the peer router.
C) Configure your routers with IP-SLA and track to ping the peer and switch to a default route if the pings fail.
D) Tune your routing protocol timers.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
60
Which design concern should be accounted for in all Layer 3 virtualization technologies?
A) Layer 3 redundancy
B) packet sizing
C) application usage
D) Layer 3 stability
A) Layer 3 redundancy
B) packet sizing
C) application usage
D) Layer 3 stability

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
61
You are tasked to design a QoS policy for a service provider so they can include it in the design of their MPLS core network. If the design must support an MPLS network with six classes, and CEs will be managed by the service provider, which QoS policy should be recommended?
A) map DSCP bits into the Exp field
B) map IP precedence bits into the DSCP field
C) map flow-label bits into the Exp field
D) map IP CoS bits into the IP Precedence field
E) map IP ToS bits into the Exp field
A) map DSCP bits into the Exp field
B) map IP precedence bits into the DSCP field
C) map flow-label bits into the Exp field
D) map IP CoS bits into the IP Precedence field
E) map IP ToS bits into the Exp field

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
62
As part of the network design, ACME Corporation requires the ability to export IPv6 information to better manage its network. Which version of NetFlow records is required to export this information?
A) 5
B) 6
C) 7
D) 8
E) 9
A) 5
B) 6
C) 7
D) 8
E) 9

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
63
You are the lead network designer hired by Service Provider XYZ to deploy CoS functionality on the core MPLS network (P routers). The goal of the network design is to provide a complete CoS solution to all customers that purchase services such as dedicated Internet access, MPLS L3VPN, and L2VPN (pseudowire). Service Provider XYZ has these design requirements: If your design includes eight CoS queues on the Service Provider XYZ MPLS PE router ingress (CE facing) interface, how will customer traffic be classified as it enters the MLS P routers?
A) The eight CoS queues in the MPLS P router are remapped to the eight CoS queues.
B) Traffic is classified on the MPLS PE routers on core facing interface. The DSCP value is mapped into EXP field where multiple EXP settings (2+) will be assigned to a single queue throughout the MPLS P routers.
C) Discard the traffic from the eight CoS queues that does not match the four CoS queues of the MPLS P routers.
D) The 8 CoS queues in the MPLS P router are remapped to four 4 flow-label queues.
A) The eight CoS queues in the MPLS P router are remapped to the eight CoS queues.
B) Traffic is classified on the MPLS PE routers on core facing interface. The DSCP value is mapped into EXP field where multiple EXP settings (2+) will be assigned to a single queue throughout the MPLS P routers.
C) Discard the traffic from the eight CoS queues that does not match the four CoS queues of the MPLS P routers.
D) The 8 CoS queues in the MPLS P router are remapped to four 4 flow-label queues.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
64
You are creating a network design that will influence the traffic path across the MPLS core on a virtual private LAN. Which parameter is included in your design to manage the traffic?
A) Deploy MPLS traffic engineering and modify the path using the preferred path.
B) Deploy MPLS traffic engineering and modify the path using auto-route, static routing, or PBR.
C) Create an MPLS traffic engineering tunnel and modify the path using a static route.
D) Create an MPLS traffic engineering tunnel and modify the path using auto-route announce.
A) Deploy MPLS traffic engineering and modify the path using the preferred path.
B) Deploy MPLS traffic engineering and modify the path using auto-route, static routing, or PBR.
C) Create an MPLS traffic engineering tunnel and modify the path using a static route.
D) Create an MPLS traffic engineering tunnel and modify the path using auto-route announce.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
65
Your company is designing a service provider network management solution in which customers are billed for 95th percentile network utilization. The service provider requires that an IETF standard be utilized to collect the data. Which method should be used to collect the data?
A) IPFIX
B) NETFLOW
C) RMON
D) IPFLOW
E) NBAR
A) IPFIX
B) NETFLOW
C) RMON
D) IPFLOW
E) NBAR

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
66
When network summaries are created for access networks in a network design, how does it change the behavior of the Shortest Path First (SPF) running in a backbone area?
A) There would be fewer incremental SPFs.
B) There would be fewer partial SPFs.
C) There would be fewer full SPFs.
D) There would be no change with the SPFs.
A) There would be fewer incremental SPFs.
B) There would be fewer partial SPFs.
C) There would be fewer full SPFs.
D) There would be no change with the SPFs.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
67
A designer is working with a large bank to redesign their network. The designer wants to minimize complaints regarding slow application response times across the WAN. It is suspected that currently traffic is not being classified and marked correctly somewhere in the network. Which tool should the designer recommend to validate quality of service mappings and use?
A) SNMP
B) IPFIX
C) IP SLA
D) protocol analyzer
E) NBAR
A) SNMP
B) IPFIX
C) IP SLA
D) protocol analyzer
E) NBAR

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
68
AS100 and AS200 each have two peering points in different parts of their network. AS100 would like to use one of the links and keep the other link as backup. What should be changed for the design inside AS100 for prefixes received from AS200?
A) MED
B) weight
C) AS-PATH
D) local preference
A) MED
B) weight
C) AS-PATH
D) local preference

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
69
A network design includes a long signaling delay in notifying the Layer 3 control plane that an interface has failed. Which two of these actions would reduce that delay? (Choose two.)
A) Enable lower data link layer recovery systems to have an opportunity to restore the interface.
B) Increase the notification of interface flaps.
C) Reduce the time for the network to reconverge.
D) Increase network stability.
A) Enable lower data link layer recovery systems to have an opportunity to restore the interface.
B) Increase the notification of interface flaps.
C) Reduce the time for the network to reconverge.
D) Increase network stability.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
70
Which two OSPF design considerations should you implement to support the eventual growth of a network, so that CPU and memory are unaffected by the size and complexity of the link-state database in a large service provider network? (Choose two.)
A) Turn on route dampening.
B) Create network summaries.
C) Turn on the Incremental SPF feature.
D) Add more memory.
E) Turn on packet pacing.
F) Add redundancy between critical locations.
A) Turn on route dampening.
B) Create network summaries.
C) Turn on the Incremental SPF feature.
D) Add more memory.
E) Turn on packet pacing.
F) Add redundancy between critical locations.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
71
Refer to the exhibit. 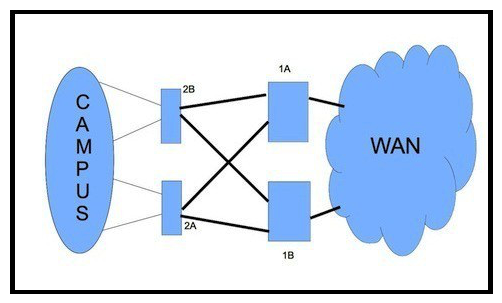 How would you redesign the network to improve availability of the routers 1A and 1B at the core site?
How would you redesign the network to improve availability of the routers 1A and 1B at the core site?
A) Enable Graceful Restart Helper for OSPF
B) Use link bundles over multiple slots
C) Use APS Ethernet circuits and redundant interfaces
D) Create a multichassis system with the two routers
 How would you redesign the network to improve availability of the routers 1A and 1B at the core site?
How would you redesign the network to improve availability of the routers 1A and 1B at the core site?A) Enable Graceful Restart Helper for OSPF
B) Use link bundles over multiple slots
C) Use APS Ethernet circuits and redundant interfaces
D) Create a multichassis system with the two routers

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
72
Refer to the exhibit. 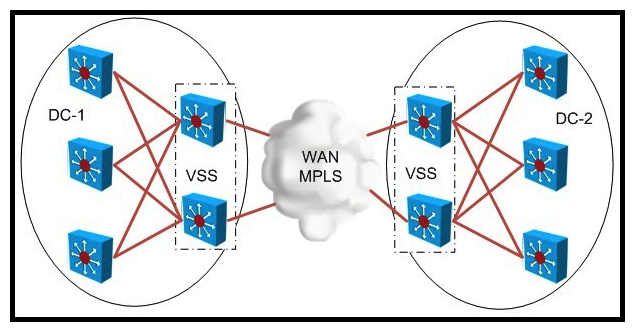 When designing an MPLS-based LAN extension between DC-1 and DC-2, what are three advantages of deploying VSS? (Choose three.)
When designing an MPLS-based LAN extension between DC-1 and DC-2, what are three advantages of deploying VSS? (Choose three.)
A) Layers 2, 3, and 4 flow-based load balancing
B) native VSS and MEC failover without using scripts
C) sub-second failover
D) required to configure VPLS
E) failover time depends on Cisco IOS EEM and STP convergence
F) limited VLAN-based VPLS traffic hashing
 When designing an MPLS-based LAN extension between DC-1 and DC-2, what are three advantages of deploying VSS? (Choose three.)
When designing an MPLS-based LAN extension between DC-1 and DC-2, what are three advantages of deploying VSS? (Choose three.)A) Layers 2, 3, and 4 flow-based load balancing
B) native VSS and MEC failover without using scripts
C) sub-second failover
D) required to configure VPLS
E) failover time depends on Cisco IOS EEM and STP convergence
F) limited VLAN-based VPLS traffic hashing

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
73
You are designing a network that includes IP QoS. Which two architectures could be used to ensure that IP QoS is implemented properly? (Choose two.)
A) Differentiated Services, where the user, with the assistance of the RSVP signaling protocol, reserves the resources end to end before sending the data
B) Integrated Services, where the user, with the assistance of the RSVP signaling protocol, reserves the resources end to end before sending the data
C) Integrated Services, which relies on the information carried within each packet to make resource- allocation decisions at each network node
D) Differentiated Services, which relies on the information carried within each packet to make resource-allocation decisions at each network node
E) Integrated Services, where the user, with the assistance of the DSCP signaling protocol, reserves the resources end to end before sending the data
A) Differentiated Services, where the user, with the assistance of the RSVP signaling protocol, reserves the resources end to end before sending the data
B) Integrated Services, where the user, with the assistance of the RSVP signaling protocol, reserves the resources end to end before sending the data
C) Integrated Services, which relies on the information carried within each packet to make resource- allocation decisions at each network node
D) Differentiated Services, which relies on the information carried within each packet to make resource-allocation decisions at each network node
E) Integrated Services, where the user, with the assistance of the DSCP signaling protocol, reserves the resources end to end before sending the data

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
74
How should multiple OSPF areas be designed when deployed on a classic three-layer (core/distribution/access) network hierarchy?
A) The OSPF flooding domain boundary should be at the edge of the core layer.
B) The OSPF flooding domain boundary should be within the distribution layer.
C) OSPF should generally be deployed in a three-layer domain hierarchy to align with the physical three-layer hierarchy.
D) OSPF flooding domain boundaries should be placed with route aggregation in mind.
A) The OSPF flooding domain boundary should be at the edge of the core layer.
B) The OSPF flooding domain boundary should be within the distribution layer.
C) OSPF should generally be deployed in a three-layer domain hierarchy to align with the physical three-layer hierarchy.
D) OSPF flooding domain boundaries should be placed with route aggregation in mind.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
75
Your company requires two diverse multihop External Border Gateway Protocol peerings to a partner network. Which two methods would you use to improve lost peer detection? (Choose two.)
A) Use Bidirectional Forwarding Detection for the peers.
B) Use Selective Address Tracking and match the peers.
C) Use subsecond keepalives for the peers.
D) Use subsecond hold timers for the peers.
E) Use Fast Peering Session Deactivation for the peers.
F) Use subsecond minimum route advertisement Interval timers for the peers.
A) Use Bidirectional Forwarding Detection for the peers.
B) Use Selective Address Tracking and match the peers.
C) Use subsecond keepalives for the peers.
D) Use subsecond hold timers for the peers.
E) Use Fast Peering Session Deactivation for the peers.
F) Use subsecond minimum route advertisement Interval timers for the peers.

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
76
Your customer asks you to assist with their traffic policy design. They want to guarantee a minimum amount of bandwidth to certain traffic classes. Which technique would you advise them to implement?
A) Modular QoS CLI
B) committed accessrRate
C) policy-based routing
D) traffic shaping
A) Modular QoS CLI
B) committed accessrRate
C) policy-based routing
D) traffic shaping

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
77
ACME Corporation is deploying a new HR application that requires the network infrastructure to monitor and react to certain conditions in the network. Which feature should be used to meet this design requirement?
A) Cisco IOS Embedded Event Manager
B) IP SLA
C) reflexive ACLs
D) route maps
E) SOAP
F) exit status
A) Cisco IOS Embedded Event Manager
B) IP SLA
C) reflexive ACLs
D) route maps
E) SOAP
F) exit status

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
78
Your company needs to baseline web traffic on a per-session basis for network application reporting. Which two mechanisms, when combined, fulfill the requirement? (Choose two.)
A) Flexible Netflow
B) Remote Monitoring
C) Cisco IOS IP Service Level Agreement
D) Class-Based Quality of Service Management Information Base
E) Network-Based Application Recognition
A) Flexible Netflow
B) Remote Monitoring
C) Cisco IOS IP Service Level Agreement
D) Class-Based Quality of Service Management Information Base
E) Network-Based Application Recognition

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
79
You are designing a traffic monitoring and analysis system for a customer. Which traffic monitoring technique would you recommend to place the least amount of burden on the network infrastructure?
A) SPAN monitor ports
B) NetFlow
C) IP NBAR
D) passive taps
A) SPAN monitor ports
B) NetFlow
C) IP NBAR
D) passive taps

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck
80
Refer to the exhibit.  What limitations exist in this design, given that the access layer devices are expected to steadily increase by two devices per week for the next year?
What limitations exist in this design, given that the access layer devices are expected to steadily increase by two devices per week for the next year?
A) scalability
B) serviceability
C) redundancy
D) resiliency
 What limitations exist in this design, given that the access layer devices are expected to steadily increase by two devices per week for the next year?
What limitations exist in this design, given that the access layer devices are expected to steadily increase by two devices per week for the next year?A) scalability
B) serviceability
C) redundancy
D) resiliency

Unlock Deck
Unlock for access to all 660 flashcards in this deck.
Unlock Deck
k this deck


