Exam 44: Deploying Cisco Unified Contact Center Express
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
Which three techniques can be used to improve fault isolation in an enterprise network design? (Choose three.)
Free
(Multiple Choice)
4.7/5  (34)
(34)
Correct Answer:
A,D,E
What are three key design principles when using a classic hierarchical network model? (Choose three.)
Free
(Multiple Choice)
4.7/5  (28)
(28)
Correct Answer:
B,D,F
Refer to the exhibit. You are planning a migration to a dual-stack IPv4/IPv6 campus environment while providing a flexible and scalable design with fault isolation. The design must allow IPv6 devices to tunnel over portions of the campus that are not yet natively IPv6-enabled, including wireless and voice endpoints. Your plan requires an interim approach that allows for a faster introduction of new services without requiring a network wide hot cutover. Which two services block functions meet these requirements? (Choose two.) 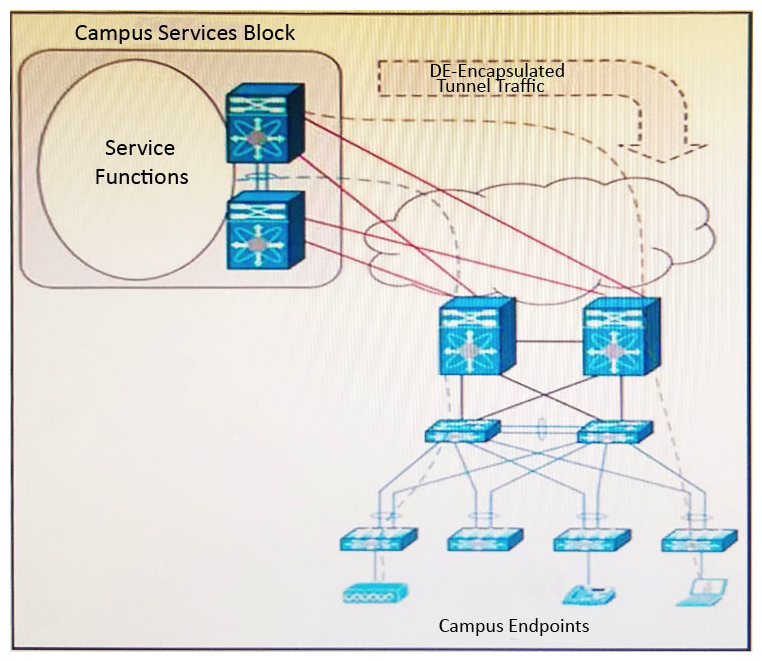
Free
(Multiple Choice)
4.9/5  (35)
(35)
Correct Answer:
A,C
What is the reason that you want to synchronize IGP and BGP convergence by advertising an infinite metric in OSPF or setting the overload bit in IS-IS?
(Multiple Choice)
4.7/5  (27)
(27)
Study the following exhibit carefully. A service provider with a multi-area OSPF environment would like to deploy MPLS TE tunnels among PE routers across area boundaries. Configure the LSPs with bandwidth constraints and explicit loose route hops as indicated by the arrows in the following path: PE1 -> ABR1 -> ABR2 -> PE2 Which two items identify devices that will execute constraint-based SPF in order to set up LSP from PE1 to PE2? (Choose two.) 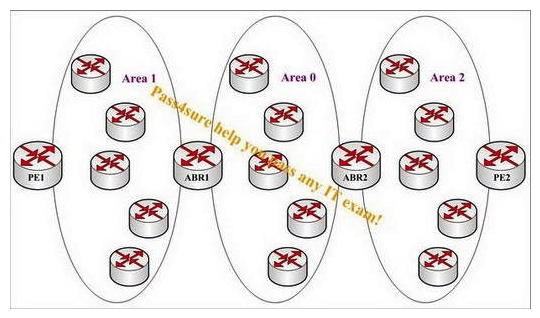
(Multiple Choice)
4.7/5  (37)
(37)
According to the network provided in the following exhibit, all routers are performing OSPF on all links and all links have the same cost. OSPF timers have not been modified on any router. Which network will converge faster, and why, if the link between 10.1.1.0/24 and router P4S-RA fails? 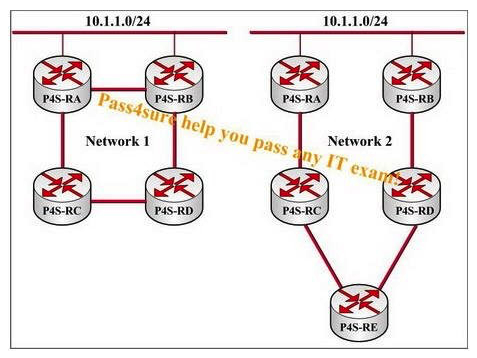
(Multiple Choice)
4.7/5  (31)
(31)
A large enterprise customer has more than 300 worldwide locations, each with at least two different WAN connections to their five regional data centers across US, Europe, and Asia. These data centers offer different application services and work as primary, with a remote data center as backup. You must provide a solution to securely select the traffic path for specific applications based on an IT policy. Which solution allows the easiest management of the path decision from the data center sites?
(Multiple Choice)
4.9/5  (44)
(44)
A service provider creates a network design that runs MPLS in its WAN backbone using OSPF as the IGP routing protocol. What would be two effects of additionally implementing MPLS-TE? (Choose two.)
(Multiple Choice)
4.9/5  (36)
(36)
Which main IoT migration aspect must be reviewed for a manufacturing plant?
(Multiple Choice)
4.9/5  (34)
(34)
To ensure voice packets are kept within the Committed Information Rate (CIR) of a Frame Relay link, what should be used in the CPE?
(Multiple Choice)
4.8/5  (35)
(35)
You work as a network technician for an IT company, you are tasked to deploy BGP across a satellite link system to a small number of retail stores. What must be done in order to successfully deploy BGP in this situation?
(Multiple Choice)
4.9/5  (34)
(34)
Refer to the exhibit. 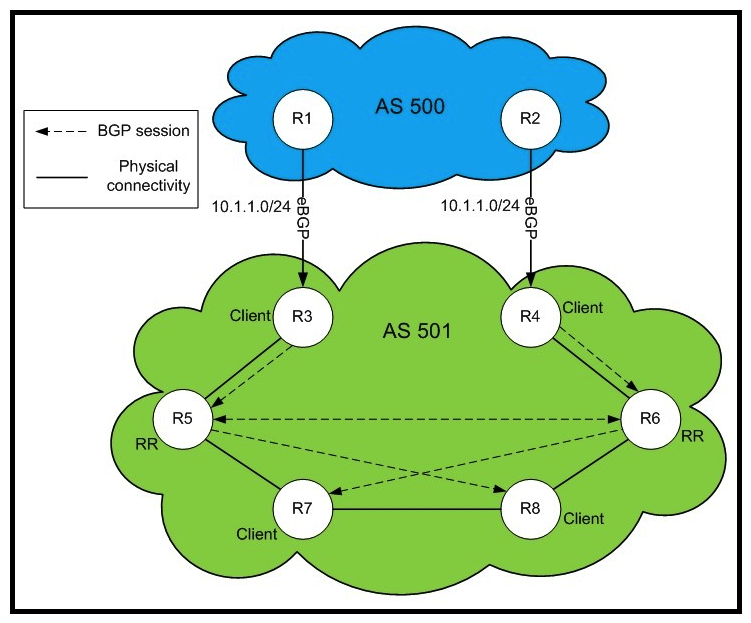 In this BGP design, what is the next hop for 10.1.1.0/24 on R8 and R7?
In this BGP design, what is the next hop for 10.1.1.0/24 on R8 and R7?
(Multiple Choice)
4.8/5  (35)
(35)
A company wants a design that would support OSPF through a service provider ATM network. Which two OSPF network types should the designer use to establish OSPF neighborship between OSPF routers through the ATM network? (Choose two.)
(Multiple Choice)
4.8/5  (29)
(29)
A network is designed to use OSPF to reach eBGP peers. Which condition should be avoided in the design to potentially prevent the eBGP peers to flap continuously in case of link failure?
(Multiple Choice)
4.9/5  (36)
(36)
Which three methods allow storage access across an IP network? (Choose three.)
(Multiple Choice)
4.8/5  (30)
(30)
At all sites provided in the following exhibit. OSPF is used as the PE-CE protocol Which path is preferred from CE1 to CE3? 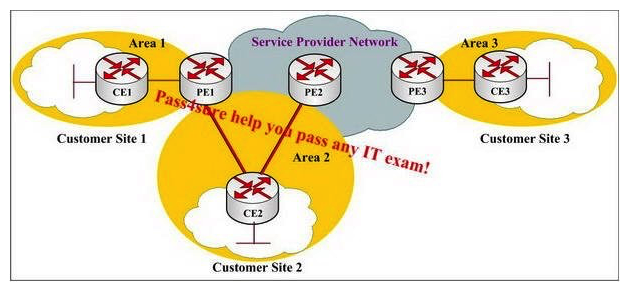
(Multiple Choice)
4.9/5  (28)
(28)
You work as a network administrator for the P4S company. Study the exhibit carefully, the network is running EIGRP. You need traffic from P4S-R5 destined for 172.30.1.0/24 to be routed through P4S-R4. You should complete which two actions combined? (Choose two.) 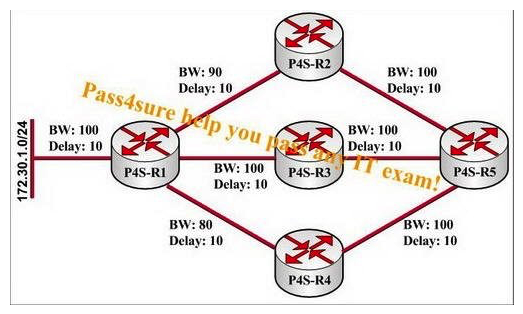
(Multiple Choice)
4.8/5  (47)
(47)
You have been hired by Acme Corporation to evaluate their existing network and determine if the current network design is secure enough to prevent man-in-the-middle attacks. When evaluating the network, which switch security option should you investigate to ensure that authorized ARP responses take place according to known IP-to-MAC address mapping?
(Multiple Choice)
4.9/5  (40)
(40)
Which advantage is of creating an in-band instead of an out-of-band management network?
(Multiple Choice)
4.9/5  (35)
(35)
Showing 1 - 20 of 660
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)