Deck 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/24
Play
Full screen (f)
Deck 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints
1
What occurs when a configuration change is made to an MX network that is bound to a configuration template?
A) The configuration change in the bound network is combined with the template configuration inside the template.
B) The more restrictive configuration is preferred.
C) The configuration change in the bound network overrides the template configuration.
D) The template configuration overrides the configuration change in the bound network.
A) The configuration change in the bound network is combined with the template configuration inside the template.
B) The more restrictive configuration is preferred.
C) The configuration change in the bound network overrides the template configuration.
D) The template configuration overrides the configuration change in the bound network.
The configuration change in the bound network is combined with the template configuration inside the template.
2
Air Marshal has contained a malicious SSID. What are two effects on connectivity? (Choose two.)
A) Currently associated clients stay connected.
B) New clients can connect.
C) Currently associated clients are affected by restrictive traffic shaping rules.
D) New clients cannot connect.
E) Currently associated clients are disconnected.
A) Currently associated clients stay connected.
B) New clients can connect.
C) Currently associated clients are affected by restrictive traffic shaping rules.
D) New clients cannot connect.
E) Currently associated clients are disconnected.
New clients cannot connect.
Currently associated clients are disconnected.
Currently associated clients are disconnected.
3
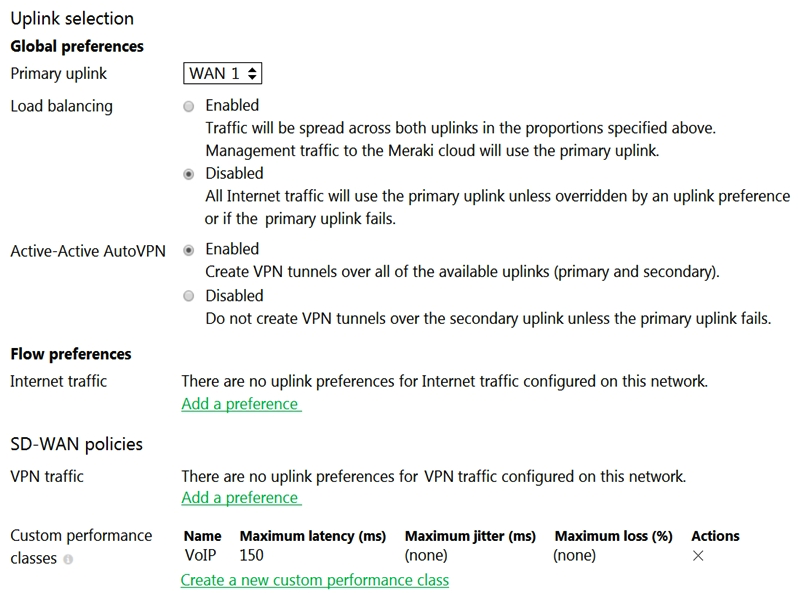 Refer to the exhibit. What does the MX Security Appliance send to determine whether VPN traffic exceeds the configured latency threshold in the VoIP custom performance class?
Refer to the exhibit. What does the MX Security Appliance send to determine whether VPN traffic exceeds the configured latency threshold in the VoIP custom performance class?A) 1000-byte TCP probes every second, through VPN tunnels that are established over the primary WAN link.
B) 100-byte UDP probes every second, through VPN tunnels that are established over every WAN link.
C) 100-byte UDP probes every second, through VPN tunnels that are established over the primary WAN link.
D) 1000-byte TCP probes every second, through VPN tunnels that are established over every WAN link.
1000-byte TCP probes every second, through VPN tunnels that are established over every WAN link.
4
Where should a network admin navigate to investigate wireless mesh information between Meraki APs?
A) Wireless > Monitor > Access Points > AP > RF
B) Wireless > Configure > Radio Settings
C) Wireless > Monitor > Wireless Health
D) Wireless > Monitor > RF Spectrum
A) Wireless > Monitor > Access Points > AP > RF
B) Wireless > Configure > Radio Settings
C) Wireless > Monitor > Wireless Health
D) Wireless > Monitor > RF Spectrum

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
5
Which two Systems Manager Live tools are available only for Apple Macs and Windows PCs and cannot be used on iOS or Android mobile devices? (Choose two.)
A) OS updates
B) Send notification
C) Selective wipe
D) Screenshot
E) Remote Desktop
A) OS updates
B) Send notification
C) Selective wipe
D) Screenshot
E) Remote Desktop

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
6
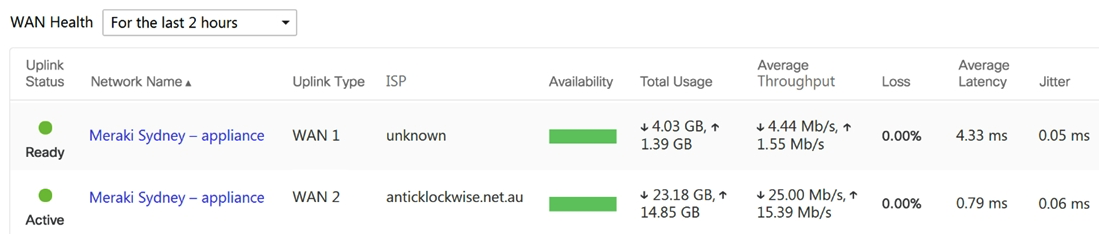 Refer to the exhibit. What are the Loss and Average Latency statistics based on?
Refer to the exhibit. What are the Loss and Average Latency statistics based on?A) responses that the MX appliance receives on the connectivity-testing hostnames on the Insight > Web App Health page
B) responses that the MX appliance receives on the connectivity-testing IP addresses on the Security & SD-WAN > Firewall page
C) responses that the MX appliance receives on the connectivity-testing IP address that is configured on the Security & SD-WAN > SD-WAN & Traffic Shaping page
D) responses that the MX appliance receives on the connectivity-testing IP addresses on the Help > Firewall info page

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
7
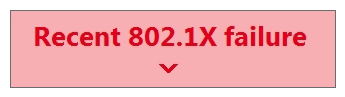 Refer to the exhibit. For an AP that displays this alert, which network access control method must be in use?
Refer to the exhibit. For an AP that displays this alert, which network access control method must be in use?A) preshared key
B) WPA2-enterprise with my RADIUS server
C) splash page with my RADIUS server
D) MAC-based access control with RADIUS server

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
8
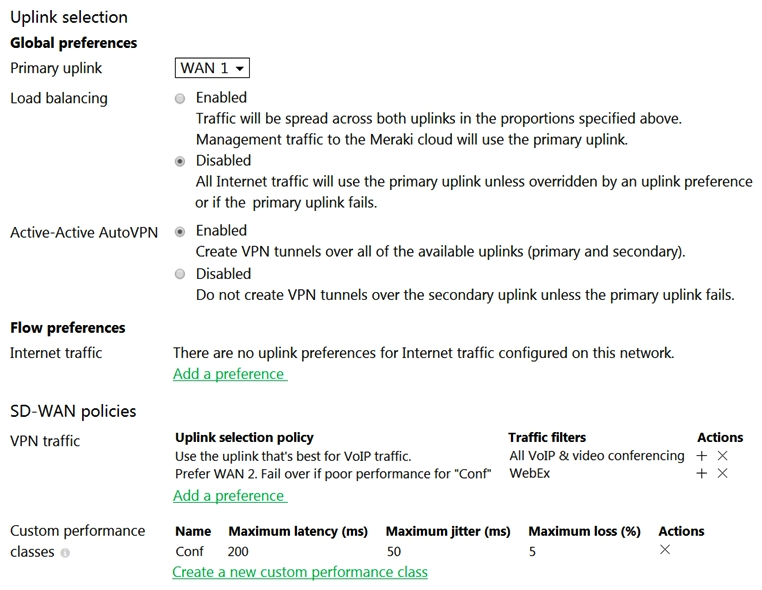 Refer to the exhibit. Assuming this MX has established a full tunnel with its VPN peer, how will the MX route the WebEx traffic?
Refer to the exhibit. Assuming this MX has established a full tunnel with its VPN peer, how will the MX route the WebEx traffic?A) WebEx traffic will prefer WAN 2 as long as it meets the thresholds in the "Conf" performance class.
B) WebEx traffic will prefer WAN 1 as it is the primary uplink.
C) WebEx traffic will prefer WAN 2 as long as it is up.
D) WebEx traffic will be load-balanced between both active WAN links.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
9
For which two reasons can an organization become "Out of License"? (Choose two.)
A) licenses that are in the wrong network
B) more hardware devices than device licenses
C) expired device license
D) licenses that do not match the serial numbers in the organization
E) MR licenses that do not match the MR models in the organization
A) licenses that are in the wrong network
B) more hardware devices than device licenses
C) expired device license
D) licenses that do not match the serial numbers in the organization
E) MR licenses that do not match the MR models in the organization

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
10
Which order is accurate for a firmware upgrade on MX appliances in a high-availability configuration?
A) starts on the secondary MX appliance and then occurs on the primary MX appliance
B) starts on both MX appliances at the same time and then reboots both appliances after traffic on the primary MX appliance ceases
C) starts on both MX appliances at the same time and then immediately reboots both appliances
D) starts on the primary MX appliance and then occurs on the secondary MX appliance
A) starts on the secondary MX appliance and then occurs on the primary MX appliance
B) starts on both MX appliances at the same time and then reboots both appliances after traffic on the primary MX appliance ceases
C) starts on both MX appliances at the same time and then immediately reboots both appliances
D) starts on the primary MX appliance and then occurs on the secondary MX appliance

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
11
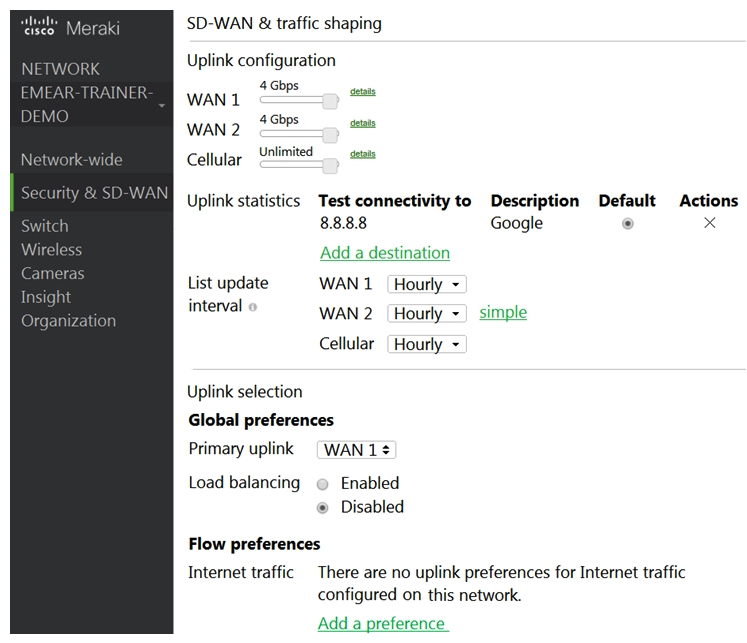 Refer to the exhibit. Which two actions are required to optimize load balancing asymmetrically with a 4:1 ratio between links? (Choose two.)
Refer to the exhibit. Which two actions are required to optimize load balancing asymmetrically with a 4:1 ratio between links? (Choose two.)A) Change the primary uplink to "none".
B) Add an internet traffic preference that defines the load-balancing ratio as 4:1.
C) Enable load balancing.
D) Set the speed of the cellular uplink to zero.
E) Change the assigned speeds of WAN 1 and WAN 2 so that the ratio is 4:1.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
12
How is high-availability supported for Cisco Meraki devices?
A) Only the MX Security Appliances that use VRRP support high availability.
B) An active/active high-availability pair is recommended for MX Security Appliances.
C) The MX Security Appliances and MS Series Switches that use VRRP support an active/passive high-availability pair.
D) The MX Security Appliances and MS Series Switches that use HSRP support an active/passive high-availability pair.
A) Only the MX Security Appliances that use VRRP support high availability.
B) An active/active high-availability pair is recommended for MX Security Appliances.
C) The MX Security Appliances and MS Series Switches that use VRRP support an active/passive high-availability pair.
D) The MX Security Appliances and MS Series Switches that use HSRP support an active/passive high-availability pair.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
13
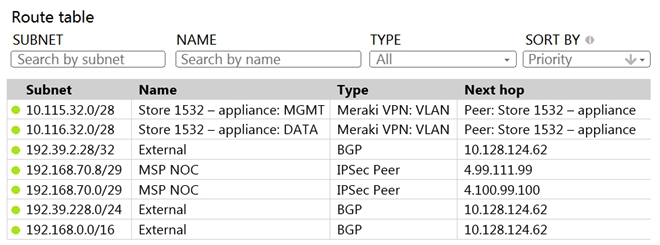 Refer to the exhibit. A packet arrives on the VPN concentrator with source IP 10.168.70.3 and destined for IP 10.116.32.4. What is the next hop for the packet, based on this concentrator routing table?
Refer to the exhibit. A packet arrives on the VPN concentrator with source IP 10.168.70.3 and destined for IP 10.116.32.4. What is the next hop for the packet, based on this concentrator routing table?A) The concentrator gateway (10.128.124.62) is the next hop.
B) Not enough detail is available to determine the next hop.
C) The packet is stopped.
D) The Auto VPN peer "Store 1532 - appliance" is the next hop.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
14
What happens to an unsupervised iOS device when the "Meraki management" profile is removed?
A) The "Meraki management" profile is removed. All configuration profiles that Systems Manager pushed remain.
B) The "Meraki management" profile is removed. All configuration profiles that Systems Manager pushed are also removed.
C) The "Meraki management" profile is removed and then pushed automatically by Systems Manager.
D) The "Meraki management" profile cannot be removed.
A) The "Meraki management" profile is removed. All configuration profiles that Systems Manager pushed remain.
B) The "Meraki management" profile is removed. All configuration profiles that Systems Manager pushed are also removed.
C) The "Meraki management" profile is removed and then pushed automatically by Systems Manager.
D) The "Meraki management" profile cannot be removed.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
15
When an SSID is configured with Sign-On Splash page enabled, which two settings must be configured for unauthenticated clients to have full network access and not be allow listed? (Choose two.)
A) Controller disconnection behavior
B) Captive Portal strength
C) Simultaneous logins
D) Firewall & traffic shaping
E) RADIUS for splash page settings
A) Controller disconnection behavior
B) Captive Portal strength
C) Simultaneous logins
D) Firewall & traffic shaping
E) RADIUS for splash page settings

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
16
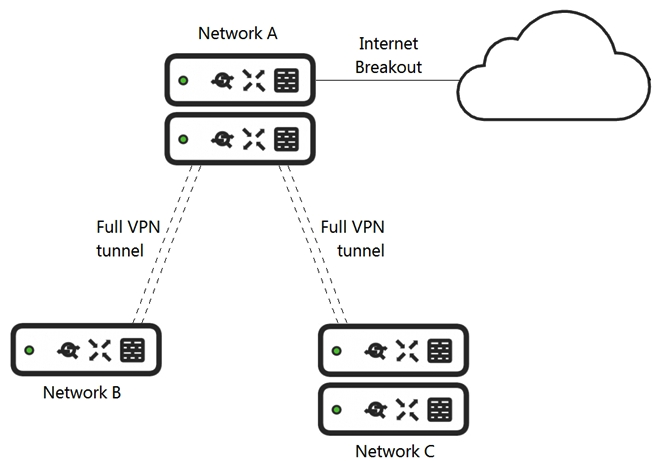 Refer to the exhibit. What is the minimal Cisco Meraki Insight licensing requirement?
Refer to the exhibit. What is the minimal Cisco Meraki Insight licensing requirement?A) A single Meraki Insight license must be configured on network A to gain Web App Health visibility on network B
B) A single Meraki Insight license must be configured on network B to gain Web App Health visibility on network B
C) A single Meraki Insight license must be configured on network A, and a single license must be configured on network B, to gain Web App Health visibility on network B
D) Two Meraki Insight licenses must be configured on network A to gain Web App Health visibility on network B
E) Two Meraki Insight licenses must be configured on network A and a single license must be configured on network B, to gain Web App Health visibility on network B

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
17
When wireless SSIDs are configured in Dashboard, which setting on the Access Control page affects the ability of a 2.4 GHz only client device from associating to the WLAN for the first time?
A) Content filtering
B) Bridge mode
C) 802.11r
D) Dual band operating with Band Steering
A) Content filtering
B) Bridge mode
C) 802.11r
D) Dual band operating with Band Steering

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
18
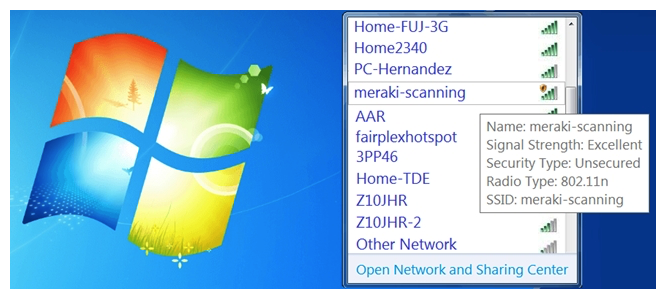 Refer to the exhibit. During a Meraki AP deployment, the default SSID that the exhibit shows is broadcast. What causes this behavior?
Refer to the exhibit. During a Meraki AP deployment, the default SSID that the exhibit shows is broadcast. What causes this behavior?A) An AP does not have a wired connection to the network.
B) An AP cannot connect to the default gateway.
C) An AP has never connected to the Meraki Cloud Controller.
D) An AP has Site Survey mode enabled.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
19
What are two ways peers interact with ports that Auto VPN uses? (Choose two.)
A) For IPsec tunneling, peers use high UDP ports within the 32768 to 61000 range.
B) Peers contact the VPN registry at UDP port 9350.
C) For IPsec tunneling, peers use high TCP ports within the 32768 to 61000 range.
D) Peers contact the VPN registry at TCP port 9350.
E) For IPsec tunneling, peers use UDP ports 500 and 4500.
A) For IPsec tunneling, peers use high UDP ports within the 32768 to 61000 range.
B) Peers contact the VPN registry at UDP port 9350.
C) For IPsec tunneling, peers use high TCP ports within the 32768 to 61000 range.
D) Peers contact the VPN registry at TCP port 9350.
E) For IPsec tunneling, peers use UDP ports 500 and 4500.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
20
One thousand concurrent users stream video to their laptops. A 30/70 split between 2.4 GHz and 5 GHz is used. Based on client count, how many APs (rounded to the nearest whole number) are needed?
A) 26
B) 28
C) 30
D) 32
A) 26
B) 28
C) 30
D) 32

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
21
Which Cisco Meraki product must be deployed in addition to Systems Manager so that Systems Manager Sentry enrollment can be used?
A) MS Switch
B) Meraki Insight
C) MR Access Point
D) MV Smart Camera
A) MS Switch
B) Meraki Insight
C) MR Access Point
D) MV Smart Camera

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
22
Which configuration step is necessary when automatic updating is required of iOS apps provisioned through Systems Manager that are found in the App Store?
A) No configuration step is necessary; automatic updating is the default behavior.
B) Configure automatic updating of iOS devices in the Meraki installed profile.
C) Create a security policy that enables automatic updates.
D) Create a profile with automatic update enabled and apply it to iOS devices.
A) No configuration step is necessary; automatic updating is the default behavior.
B) Configure automatic updating of iOS devices in the Meraki installed profile.
C) Create a security policy that enables automatic updates.
D) Create a profile with automatic update enabled and apply it to iOS devices.

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
23
Which VLAN is used to source pings across the site-to-site VPN when using the MX Live tools?
A) highest VLAN ID that is configured and set to NO to use VPN
B) lowest VLAN ID that is configured and set to YES to use VPN
C) highest VLAN ID that is configured and set to YES to use VPN
D) lowest VLAN ID configured and set to NO to use VPN
A) highest VLAN ID that is configured and set to NO to use VPN
B) lowest VLAN ID that is configured and set to YES to use VPN
C) highest VLAN ID that is configured and set to YES to use VPN
D) lowest VLAN ID configured and set to NO to use VPN

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck
24
A Cisco Meraki MV camera is monitoring an office and its field of vision currently captures work desks and employee computer screens. However, recording employee computer screens is prohibited by local regulation. Which feature in Dashboard can be used to preserve the current position of the camera while also meeting regulation requirements?
A) zone exclusion
B) privacy window
C) area or interest
D) sensor crop
E) restricted mode
A) zone exclusion
B) privacy window
C) area or interest
D) sensor crop
E) restricted mode

Unlock Deck
Unlock for access to all 24 flashcards in this deck.
Unlock Deck
k this deck


