Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints
Exam 1: Supporting Cisco Data Center System Devices (DCTECH)128 Questions
Exam 2: Cisco Certified Technician Routing & Switching (RSTECH)48 Questions
Exam 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)141 Questions
Exam 4: Cisco Certified Network Associate (CCNA)411 Questions
Exam 5: Managing Industrial Networks with Cisco Networking Technologies (IMINS)36 Questions
Exam 6: DevNet Associate (DEVASC)134 Questions
Exam 7: Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)25 Questions
Exam 8: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)114 Questions
Exam 9: Implementing Cisco SD-WAN Solutions (ENSDWI)147 Questions
Exam 10: Designing Cisco Enterprise Networks (ENSLD)109 Questions
Exam 11: Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)106 Questions
Exam 12: Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)101 Questions
Exam 13: Automating Cisco Enterprise Solutions (ENAUTO)84 Questions
Exam 14: Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)74 Questions
Exam 15: Implementing Cisco Service Provider VPN Services (SPVI)49 Questions
Exam 16: Designing Cisco Data Center Infrastructure (DCID)73 Questions
Exam 17: Troubleshooting Cisco Data Center Infrastructure (DCIT)84 Questions
Exam 18: Implementing Cisco Application Centric Infrastructure (DCACI)101 Questions
Exam 19: Configuring Cisco MDS 9000 Series Switches (DCSAN)65 Questions
Exam 20: Implementing Cisco Application Centric Infrastructure - Advanced36 Questions
Exam 21: Automating Cisco Data Center Solutions (DCAUTO)36 Questions
Exam 22: Securing Networks with Cisco Firepower (300-710 SNCF)65 Questions
Exam 23: Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)130 Questions
Exam 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)65 Questions
Exam 25: Securing the Web with Cisco Web Security Appliance (300-725 SWSA)75 Questions
Exam 26: Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)49 Questions
Exam 27: Automating Cisco Security Solutions (SAUTO)75 Questions
Exam 28: Implementing Cisco Collaboration Applications (CLICA)39 Questions
Exam 29: Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)86 Questions
Exam 30: Implementing Cisco Collaboration Cloud and Edge Solutions90 Questions
Exam 31: Implementing Cisco Collaboration Conferencing65 Questions
Exam 32: Automating Cisco Collaboration Solutions (CLAUTO)27 Questions
Exam 33: Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)66 Questions
Exam 34: Developing Solutions Using Cisco IoT and Edge Platforms (DEVIOT)33 Questions
Exam 35: Developing Applications for Cisco Webex and Webex Devices (DEVWBX)41 Questions
Exam 36: Performing CyberOps Using Core Security Technologies (CBRCOR)37 Questions
Exam 37: Implementing Cisco Enterprise Network Core Technologies (ENCOR)106 Questions
Exam 38: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)260 Questions
Exam 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)116 Questions
Exam 40: Implementing and Operating Cisco Security Core Technologies208 Questions
Exam 41: Implementing Cisco Collaboration Core Technologies (CLCOR)213 Questions
Exam 42: Developing Applications using Cisco Core Platforms and APIs (DEVCOR)131 Questions
Exam 43: CCDE Design Written145 Questions
Exam 44: Deploying Cisco Unified Contact Center Express660 Questions
Exam 45: Cisco Meraki Solutions Specialist101 Questions
Exam 46: Securing Cisco Networks with Sourcefire FireAMP Endpoints24 Questions
Exam 47: Designing Cisco Unified Contact Center Enterprise (UCCED)227 Questions
Exam 48: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)55 Questions
Exam 49: Cisco Collaboration SaaS Authorization Exam47 Questions
Exam 50: Cisco Security Architecture for System Engineers56 Questions
Exam 51: Adopting The Cisco Business Architecture Approach (DTBAA)239 Questions
Exam 52: Cisco Customer Success Manager (CSM)44 Questions
Exam 53: Mastering The Cisco Business Architecture Discipline (DTBAD)36 Questions
Select questions type
When an SSID is configured with Sign-On Splash page enabled, which two settings must be configured for unauthenticated clients to have full network access and not be allow listed? (Choose two.)
Free
(Multiple Choice)
4.8/5  (45)
(45)
Correct Answer:
A,B
Air Marshal has contained a malicious SSID. What are two effects on connectivity? (Choose two.)
Free
(Multiple Choice)
4.9/5  (32)
(32)
Correct Answer:
D,E
Which configuration step is necessary when automatic updating is required of iOS apps provisioned through Systems Manager that are found in the App Store?
Free
(Multiple Choice)
4.8/5  (36)
(36)
Correct Answer:
C
Where should a network admin navigate to investigate wireless mesh information between Meraki APs?
(Multiple Choice)
4.8/5  (40)
(40)
A Cisco Meraki MV camera is monitoring an office and its field of vision currently captures work desks and employee computer screens. However, recording employee computer screens is prohibited by local regulation. Which feature in Dashboard can be used to preserve the current position of the camera while also meeting regulation requirements?
(Multiple Choice)
4.7/5  (34)
(34)
 Refer to the exhibit. What is the minimal Cisco Meraki Insight licensing requirement?
Refer to the exhibit. What is the minimal Cisco Meraki Insight licensing requirement?
(Multiple Choice)
4.8/5  (37)
(37)
One thousand concurrent users stream video to their laptops. A 30/70 split between 2.4 GHz and 5 GHz is used. Based on client count, how many APs (rounded to the nearest whole number) are needed?
(Multiple Choice)
4.8/5  (38)
(38)
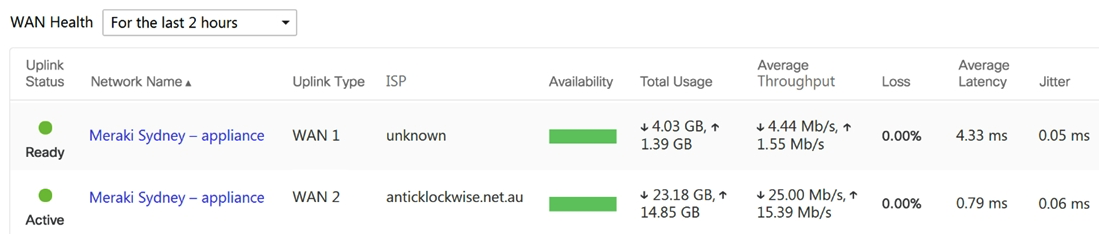 Refer to the exhibit. What are the Loss and Average Latency statistics based on?
Refer to the exhibit. What are the Loss and Average Latency statistics based on?
(Multiple Choice)
4.8/5  (32)
(32)
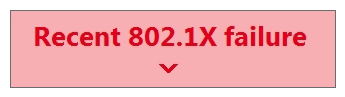 Refer to the exhibit. For an AP that displays this alert, which network access control method must be in use?
Refer to the exhibit. For an AP that displays this alert, which network access control method must be in use?
(Multiple Choice)
4.8/5  (32)
(32)
What happens to an unsupervised iOS device when the "Meraki management" profile is removed?
(Multiple Choice)
5.0/5  (35)
(35)
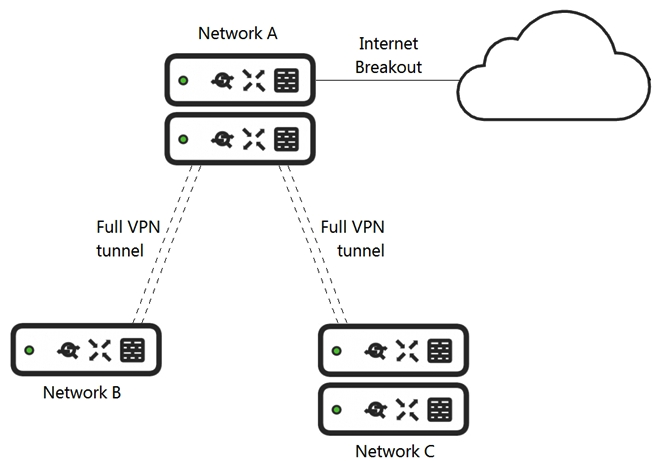
 Refer to the exhibit. Assuming this MX has established a full tunnel with its VPN peer, how will the MX route the WebEx traffic?
Refer to the exhibit. Assuming this MX has established a full tunnel with its VPN peer, how will the MX route the WebEx traffic?
(Multiple Choice)
4.8/5  (34)
(34)
What are two ways peers interact with ports that Auto VPN uses? (Choose two.)
(Multiple Choice)
4.8/5  (33)
(33)
How is high-availability supported for Cisco Meraki devices?
(Multiple Choice)
4.8/5  (37)
(37)
Which VLAN is used to source pings across the site-to-site VPN when using the MX Live tools?
(Multiple Choice)
4.8/5  (29)
(29)
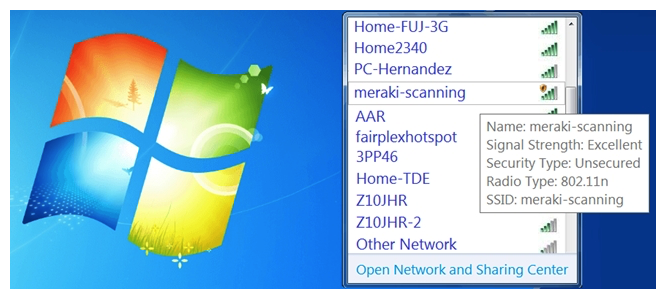 Refer to the exhibit. During a Meraki AP deployment, the default SSID that the exhibit shows is broadcast. What causes this behavior?
Refer to the exhibit. During a Meraki AP deployment, the default SSID that the exhibit shows is broadcast. What causes this behavior?
(Multiple Choice)
4.9/5  (31)
(31)
What occurs when a configuration change is made to an MX network that is bound to a configuration template?
(Multiple Choice)
4.8/5  (22)
(22)
When wireless SSIDs are configured in Dashboard, which setting on the Access Control page affects the ability of a 2.4 GHz only client device from associating to the WLAN for the first time?
(Multiple Choice)
4.9/5  (34)
(34)
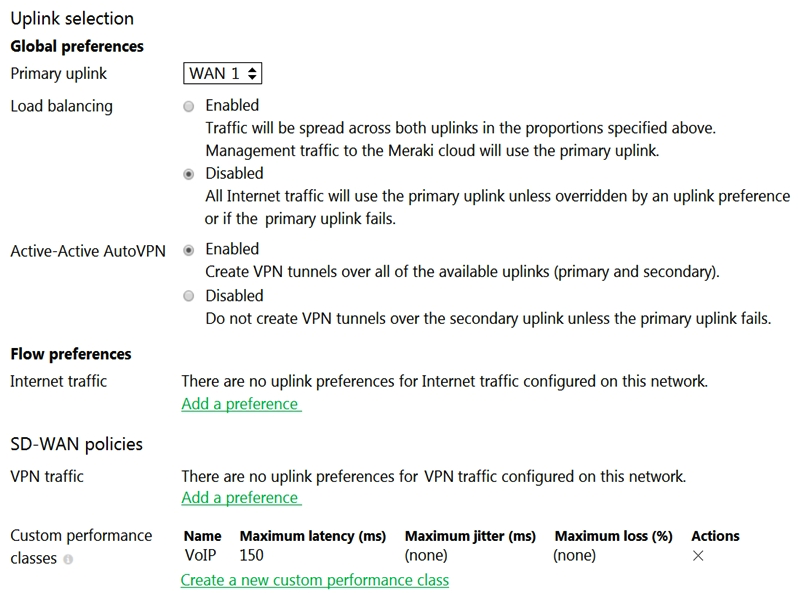 Refer to the exhibit. What does the MX Security Appliance send to determine whether VPN traffic exceeds the configured latency threshold in the VoIP custom performance class?
Refer to the exhibit. What does the MX Security Appliance send to determine whether VPN traffic exceeds the configured latency threshold in the VoIP custom performance class?
(Multiple Choice)
4.9/5  (39)
(39)
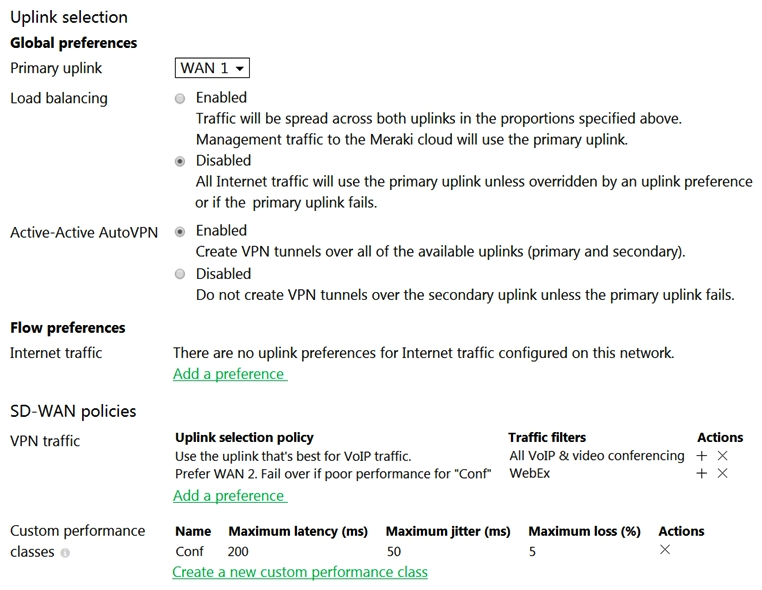
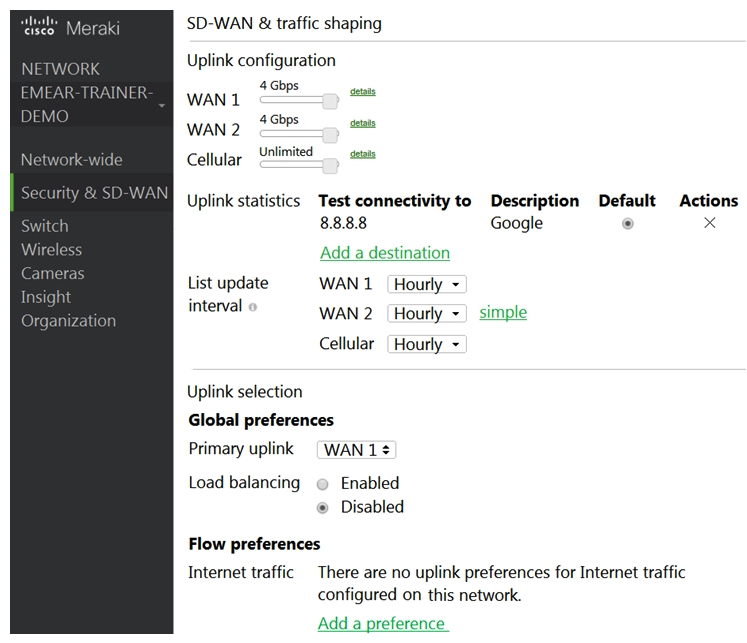 Refer to the exhibit. Which two actions are required to optimize load balancing asymmetrically with a 4:1 ratio between links? (Choose two.)
Refer to the exhibit. Which two actions are required to optimize load balancing asymmetrically with a 4:1 ratio between links? (Choose two.)
(Multiple Choice)
4.8/5  (28)
(28)
Which order is accurate for a firmware upgrade on MX appliances in a high-availability configuration?
(Multiple Choice)
4.9/5  (37)
(37)
Showing 1 - 20 of 24
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)