Deck 8: Cybersecurity: Threats
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/23
Play
Full screen (f)
Deck 8: Cybersecurity: Threats
1
Think of a normally-functioning video game program that has a hiding malware. A user can download and install the video game program from a website and enjoy it. But, at the same time, this also result in the secret installation of the malware, creating a hidden backdoor on the victim computer. Then, the malware must be
A) virus
B) spyware
C) ransomware
D) worm
E) Trojan
A) virus
B) spyware
C) ransomware
D) worm
E) Trojan
E
2
The following figure depicts the general structure of the ________ 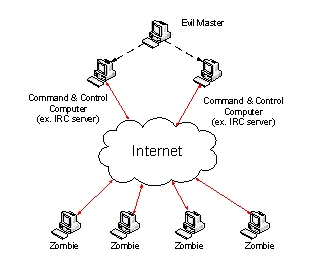
A) trojan network
B) worm network
C) spam network
D) botnet
E) darknet

A) trojan network
B) worm network
C) spam network
D) botnet
E) darknet
D
3
Which may NOT be a 'major' security threat for the WiFi LAN?
A) wardriving
B) hash attack
C) denial of service attack
D) rogue wireless access point
E) man-in-the-middle attack
A) wardriving
B) hash attack
C) denial of service attack
D) rogue wireless access point
E) man-in-the-middle attack
B
4
This attack using an evil twin AP is a type of ______. 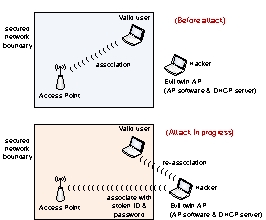
A) man-in-the-middle
B) rogue access point
C) denial of service
D) wardriving
E) social engineering

A) man-in-the-middle
B) rogue access point
C) denial of service
D) wardriving
E) social engineering

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
5
The evil twin WAP is a form of the _____ attack by cybercriminals.
A) denial of service
B) man-in-the-middle
C) brute force
D) social engineering
E) wardriving
A) denial of service
B) man-in-the-middle
C) brute force
D) social engineering
E) wardriving

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
6
The 'denial of service (DOS)' attack is a type of threat that negatively affects ________ of a system.
A) Confidentiality
B) Data integrity
C) Authentication
D) Authorization
E) Availability
A) Confidentiality
B) Data integrity
C) Authentication
D) Authorization
E) Availability

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
7
The ransomware is a type of malware that negatively affects ________ of a system.
A) Confidentiality
B) Data integrity
C) Authentication
D) Authorization
E) Availability
A) Confidentiality
B) Data integrity
C) Authentication
D) Authorization
E) Availability

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
8
In downloading software from the Internet, its integrity should be examined to ensure that it does not contain a code/program secretly planted by an attacker. This validation is called ______.
A) filtering
B) signifying
C) scanning
D) sniffing
E) fingerprinting
A) filtering
B) signifying
C) scanning
D) sniffing
E) fingerprinting

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
9
MAC address flooding by an attacker is a form of ___________ attack.
A) denial of service
B) spoofing
C) malware
D) password cracking
E) hashing
A) denial of service
B) spoofing
C) malware
D) password cracking
E) hashing

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
10
Which is CORRECTLY paired between security functions and available technologies?
A) Biometric solutions
B) Passwords and passphrases
C) Checksum/frame check sequence (FCS)
D) Firewall
E) Access Control List(ACL)
A) Biometric solutions
B) Passwords and passphrases
C) Checksum/frame check sequence (FCS)
D) Firewall
E) Access Control List(ACL)

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
11
Three primary malware types are:
A) Keystroke logger, spyware, and adware
B) Virus, worm, and spyware
C) Spyware, Trojan, and adware
D) Spyware, Trojan, and worm
E) Virus, worm, and Trojan
A) Keystroke logger, spyware, and adware
B) Virus, worm, and spyware
C) Spyware, Trojan, and adware
D) Spyware, Trojan, and worm
E) Virus, worm, and Trojan

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
12
Which CANNOT be spoofed for cyberattacks in a normal situation?
A) Sender's IP address
B) Sender's MAC address
C) Sender's Email address
D) Clickable web site address
E) Receiver's private key
A) Sender's IP address
B) Sender's MAC address
C) Sender's Email address
D) Clickable web site address
E) Receiver's private key

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
13
One key attribute that separates worms from other malware is:
A) It generally results in mild annoyance to infected system users.
B) It is designed to replicate itself without interventions.
C) It is designed to monitor system usage.
D) It is designed to create a backdoor to an infected system.
E) It destroys a computer's hardware.
A) It generally results in mild annoyance to infected system users.
B) It is designed to replicate itself without interventions.
C) It is designed to monitor system usage.
D) It is designed to create a backdoor to an infected system.
E) It destroys a computer's hardware.

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
14
Zenmap (or nmap) is a popular program for:
A) spamming
B) port scanning
C) packet sniffing
D) fingerprinting
E) man-in-the-middle
A) spamming
B) port scanning
C) packet sniffing
D) fingerprinting
E) man-in-the-middle

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
15
Wireshark is a popular program for:
A) spamming
B) port scanning
C) packet sniffing
D) fingerprinting
E) man-in-the-middle
A) spamming
B) port scanning
C) packet sniffing
D) fingerprinting
E) man-in-the-middle

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
16
A Free Video Player program comes with a hidden code that, in infected, changes the victim computer's DNS setup (ex. DNS server's IP address), then the hidden code must be
A) Virus
B) Spyware
C) Pot
D) Worm
E) Trojan
A) Virus
B) Spyware
C) Pot
D) Worm
E) Trojan

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
17
The following figure is an indication of the ___________ attack. 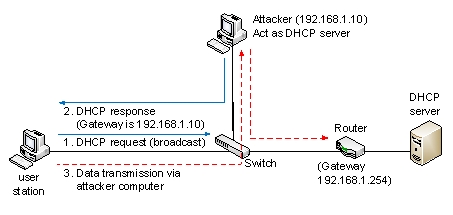
A) port scanning
B) packet sniffing
C) man-in-the-middle
D) social engineering
E) denial of service

A) port scanning
B) packet sniffing
C) man-in-the-middle
D) social engineering
E) denial of service

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
18
What can be a method used for triggering Denial of Service attacks on a target server?
A) SYN request
B) Web spoofing
C) Worm malware
D) Port scanning
E) Man-in-the-middle
A) SYN request
B) Web spoofing
C) Worm malware
D) Port scanning
E) Man-in-the-middle

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
19
Choose an INCORRECT statement on the virus malware.
A) The virus, in its narrow definition, is an executable program.
B) The virus spreads to other computers mostly by attaching itself to another program called a host program.
C) When the host program is executed, the virus code is executed as well.
D) Virus mainly affects data link layer standards.
E) If infected, the virus can cause from mild annoyance to more serious damages.
A) The virus, in its narrow definition, is an executable program.
B) The virus spreads to other computers mostly by attaching itself to another program called a host program.
C) When the host program is executed, the virus code is executed as well.
D) Virus mainly affects data link layer standards.
E) If infected, the virus can cause from mild annoyance to more serious damages.

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
20
Choose an INCORRECT statement about the worm malware.
A) The worm is a program designed to replicate itself.
B) When the worm spreads to other computers, this generally requires human interventions.
C) The worm can spread itself without attaching to another program.
D) The worm frequently takes advantage of known/unknown vulnerabilities of a target operating system.
E) The worm could result in significant consumption of network bandwidth.
A) The worm is a program designed to replicate itself.
B) When the worm spreads to other computers, this generally requires human interventions.
C) The worm can spread itself without attaching to another program.
D) The worm frequently takes advantage of known/unknown vulnerabilities of a target operating system.
E) The worm could result in significant consumption of network bandwidth.

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
21
Which may NOT be a popular form of spoofing used by malicious hackers?
A) IP address spoofing
B) MAC address spoofing
C) Email address spoofing
D) WEB spoofing
E) Port spoofing
A) IP address spoofing
B) MAC address spoofing
C) Email address spoofing
D) WEB spoofing
E) Port spoofing

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
22
The 'backdoor' is often created when a system is infected with a _________.
A) virus
B) spyware
C) keyboard logger
D) worm
E) Trojan
A) virus
B) spyware
C) keyboard logger
D) worm
E) Trojan

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck
23
The 'dictionary method" is used to ______.
A) crack passwords
B) spoof web addresses
C) trigger denial of service attacks
D) trigger man-in-the-middle attacks
E) sniff packets
A) crack passwords
B) spoof web addresses
C) trigger denial of service attacks
D) trigger man-in-the-middle attacks
E) sniff packets

Unlock Deck
Unlock for access to all 23 flashcards in this deck.
Unlock Deck
k this deck


