Exam 8: Cybersecurity: Threats
Exam 1: Networking: Fundamental Concepts33 Questions
Exam 2: Cybersecurity: Fundamentals13 Questions
Exam 3: Essential Layers of Computer Networking40 Questions
Exam 4: Ip Address Planning and Management38 Questions
Exam 5: Intermediary Devices31 Questions
Exam 6: Wi-Fi and Cellular Network43 Questions
Exam 7: Ethernet Lan24 Questions
Exam 8: Cybersecurity: Threats23 Questions
Exam 9: Cybersecurity: Network and Host Protection19 Questions
Exam 10: Cybersecurity: Data Protection24 Questions
Exam 11: Fundamentals of Packet Routing29 Questions
Exam 12: Wide Area Network33 Questions
Exam 13: Physical Layer Data Transmissions19 Questions
Exam 14: Enterprise Network: LAN Topology, Routing, and Connectivity30 Questions
Select questions type
The 'backdoor' is often created when a system is infected with a _________.
Free
(Multiple Choice)
4.7/5  (35)
(35)
Correct Answer:
E
Zenmap (or nmap) is a popular program for:
Free
(Multiple Choice)
4.8/5  (39)
(39)
Correct Answer:
B
The ransomware is a type of malware that negatively affects ________ of a system.
Free
(Multiple Choice)
4.8/5  (32)
(32)
Correct Answer:
E
The evil twin WAP is a form of the _____ attack by cybercriminals.
(Multiple Choice)
5.0/5  (42)
(42)
Which may NOT be a popular form of spoofing used by malicious hackers?
(Multiple Choice)
4.8/5  (40)
(40)
A Free Video Player program comes with a hidden code that, in infected, changes the victim computer's DNS setup (ex. DNS server's IP address), then the hidden code must be
(Multiple Choice)
4.9/5  (37)
(37)
Think of a normally-functioning video game program that has a hiding malware. A user can download and install the video game program from a website and enjoy it. But, at the same time, this also result in the secret installation of the malware, creating a hidden backdoor on the victim computer. Then, the malware must be
(Multiple Choice)
4.9/5  (31)
(31)
MAC address flooding by an attacker is a form of ___________ attack.
(Multiple Choice)
4.8/5  (48)
(48)
Which is CORRECTLY paired between security functions and available technologies? Security functions Technology Solutions Data confidentiality A) Biometric solutions Data integrity B) Passwords and passphrases Access control C) Checksum/frame check sequence (FCS) D) Firewall Authentication E) Access Control List(ACL)
(Multiple Choice)
4.8/5  (38)
(38)
In downloading software from the Internet, its integrity should be examined to ensure that it does not contain a code/program secretly planted by an attacker. This validation is called ______.
(Multiple Choice)
4.8/5  (28)
(28)
The 'denial of service (DOS)' attack is a type of threat that negatively affects ________ of a system.
(Multiple Choice)
5.0/5  (31)
(31)
Which CANNOT be spoofed for cyberattacks in a normal situation?
(Multiple Choice)
4.8/5  (27)
(27)
One key attribute that separates worms from other malware is:
(Multiple Choice)
4.9/5  (38)
(38)
The following figure is an indication of the ___________ attack. 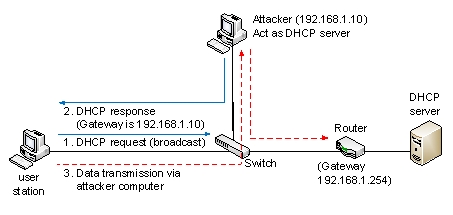
(Multiple Choice)
4.9/5  (38)
(38)
Which may NOT be a 'major' security threat for the WiFi LAN?
(Multiple Choice)
4.7/5  (39)
(39)
Showing 1 - 20 of 23
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)