Exam 12: CompTIA PenTest+ Certification Exam
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
During an internal penetration test, several multicast and broadcast name resolution requests are observed traversing the network. Which of the following tools could be used to impersonate network resources and collect authentication requests?
Free
(Multiple Choice)
4.9/5  (29)
(29)
Correct Answer:
C
After a recent penetration test, a company has a finding regarding the use of dictionary and seasonal passwords by its employees. Which of the following is the BEST control to remediate the use of common dictionary terms?
Free
(Multiple Choice)
4.7/5  (32)
(32)
Correct Answer:
A
A software development team recently migrated to new application software on the on-premises environment. Penetration test findings show that multiple vulnerabilities exist. If a penetration tester does not have access to a live or test environment, a test might be better to create the same environment on the VM. Which of the following is MOST important for confirmation?
Free
(Multiple Choice)
5.0/5  (32)
(32)
Correct Answer:
A
A penetration tester is checking a script to determine why some basic math errors are persisting. The expected result was the program outputting "True". 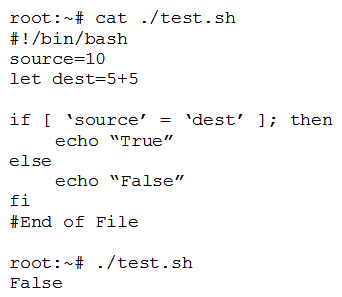 Given the output from the console above, which of the following explains how to correct the errors in the script? (Choose two.)
Given the output from the console above, which of the following explains how to correct the errors in the script? (Choose two.)
(Multiple Choice)
4.8/5  (32)
(32)
Which of the following commands will allow a tester to enumerate potential unquoted service paths on a host?
(Multiple Choice)
4.8/5  (27)
(27)
A client has voiced concern about the number of companies being breached by remote attackers, who are looking for trade secrets. Which of the following BEST describes the type of adversaries this would identify?
(Multiple Choice)
4.8/5  (30)
(30)
A company planned for and secured the budget to hire a consultant to perform a web application penetration test. Upon discovering vulnerabilities, the company asked the consultant to perform the following tasks: Code review Updates to firewall settings Which of the following has occurred in this situation?
(Multiple Choice)
4.9/5  (39)
(39)
Joe, an attacker, intends to transfer funds discreetly from a victim's account to his own. Which of the following URLs can he use to accomplish this attack?
(Multiple Choice)
4.9/5  (28)
(28)
At the information gathering stage, a penetration tester is trying to passively identify the technology running on a client's website. Which of the following approached should the penetration tester take?
(Multiple Choice)
4.8/5  (34)
(34)
Which of the following is an example of a spear phishing attack?
(Multiple Choice)
4.8/5  (37)
(37)
A penetration tester wants to check manually if a "ghost" vulnerability exists in a system. Which of the following methods is the correct way to validate the vulnerability?
(Multiple Choice)
4.8/5  (34)
(34)
An assessor begins an internal security test of the Windows domain internal.comptia.net . The assessor is given network access via DHCP, but is not given any network maps or target IP addresses. Which of the following commands can the assessor use to find any likely Windows domain controllers?
(Multiple Choice)
4.8/5  (46)
(46)
A penetration tester reviews the scan results of a web application. Which of the following vulnerabilities is MOST critical and should be prioritized for exploitation?
(Multiple Choice)
4.9/5  (35)
(35)
Joe, a penetration tester, is asked to assess a company's physical security by gaining access to its corporate office. Joe is looking for a method that will enable him to enter the building during business hours or when there are no employees on-site. Which of the following would be the MOST effective in accomplishing this?
(Multiple Choice)
4.7/5  (36)
(36)
A penetration tester has a full shell to a domain controller and wants to discover any user account that has not authenticated to the domain in 21 days. Which of the following commands would BEST accomplish this?
(Multiple Choice)
4.8/5  (27)
(27)
A client has scheduled a wireless penetration test. Which of the following describes the scoping target information MOST likely needed before testing can begin?
(Multiple Choice)
4.7/5  (27)
(27)
A security analyst was provided with a detailed penetration report, which was performed against the organization's DMZ environment. It was noted on the report that a finding has a CVSS base score of 10.0. Which of the following levels of difficulty would be required to exploit this vulnerability?
(Multiple Choice)
4.9/5  (28)
(28)
A penetration tester wants to script out a way to discover all the RPTR records for a range of IP addresses. Which of the following is the MOST efficient to utilize?
(Multiple Choice)
4.9/5  (34)
(34)
A penetration tester observes that the content security policy header is missing during a web application penetration test. Which of the following techniques would the penetration tester MOST likely perform?
(Multiple Choice)
4.8/5  (37)
(37)
During a penetration test, a tester runs a phishing campaign and receives a shell from an internal PC running Windows 10 OS. The tester wants to perform credential harvesting with Mimikatz. Which of the following registry changes would allow for credential caching in memory?
(Multiple Choice)
4.8/5  (39)
(39)
Showing 1 - 20 of 165
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)