Exam 18: CompTIA Linux+
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/252
Play
Full screen (f)
Exam 18: CompTIA Linux+
1
A junior Linux administrator is updating local name resolution to support IPv6. The administrator issues the command cat /etc/hosts and receives the following output: 127.0.0.1 localhost Which of the following actions should the administrator perform to accomplish this task?
A) Modify the /etc/hosts file, and add the ipv6 localhost entry to the file. Modify the /etc/hosts file, and add the ipv6 localhost entry to the file.
B) Modify the /etc/hosts file, and add the ::1 localhost entry to the file. ::1 localhost
C) Modify the /etc/hosts file, and add the ipv4 localhost entry to the file. ipv4 localhost
D) Modify the /etc/hosts file, and add the 0.0.0.0 localhost entry to the file. 0.0.0.0 localhost
A) Modify the /etc/hosts file, and add the ipv6 localhost entry to the file. Modify the /etc/hosts file, and add the ipv6 localhost entry to the file.
B) Modify the /etc/hosts file, and add the ::1 localhost entry to the file. ::1 localhost
C) Modify the /etc/hosts file, and add the ipv4 localhost entry to the file. ipv4 localhost
D) Modify the /etc/hosts file, and add the 0.0.0.0 localhost entry to the file. 0.0.0.0 localhost
Modify the /etc/hosts file, and add the ::1 localhost entry to the file. ::1 localhost
2
A Linux systems administrator wants the ability to access systems remotely over SSH using RSA authentication. To which of the following files should the RSA token be added to allow this access?
A) authorized_keys
B) ~/.ssh/ssh_config
C) id_rsa.pub
D) known_hosts
A) authorized_keys
B) ~/.ssh/ssh_config
C) id_rsa.pub
D) known_hosts
id_rsa.pub
3
A junior Linux administrator is installing a new application with CPU architecture requirements that have the following specifications: x64 bit 3.0GHz speed Minimum quad core The administrator wants to leverage existing equipment but is unsure whether the requirements of these systems are adequate. The administrator issues the following command cat /proc/cpuinfo . The output of the command is as follows: 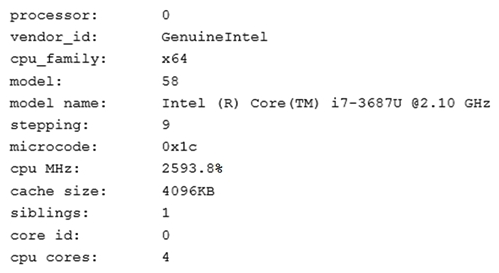 Which of the following is the recommended course of action the administrator should take based on this output?
Which of the following is the recommended course of action the administrator should take based on this output?
A) Install the application, as the system meets the application requirements
B) Procure new equipment that matches the recommended specifications
C) Recompile the Linux kernel to support the installation.
D) Reconfigure lib modules to support the new application. Reconfigure lib modules to support the new application.
 Which of the following is the recommended course of action the administrator should take based on this output?
Which of the following is the recommended course of action the administrator should take based on this output?A) Install the application, as the system meets the application requirements
B) Procure new equipment that matches the recommended specifications
C) Recompile the Linux kernel to support the installation.
D) Reconfigure lib modules to support the new application. Reconfigure lib modules to support the new application.
Install the application, as the system meets the application requirements
4
A Linux administrator needs to switch from text mode to GUI. Which of the following runlevels will start the GUI by default?
A) Runlevel 3
B) Runlevel 4
C) Runlevel 5
D) Runlevel 6
A) Runlevel 3
B) Runlevel 4
C) Runlevel 5
D) Runlevel 6

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
5
A Linux systems administrator needs to provision multiple web servers into separate regional datacenters. The systems architect has instructed the administrator to define the server infrastructure using a specific tool that consumes a text-based file. Which of the following is the BEST reason to do this?
A) To document the infrastructure so it can be included in the system security plan
B) To ensure the administrator follows the planning phase of the systems development life cycle
C) To define the infrastructure so it can be provisioned consistently with minimal manual tasks
D) To validate user requirements have been met within each regional datacenter for compliance
A) To document the infrastructure so it can be included in the system security plan
B) To ensure the administrator follows the planning phase of the systems development life cycle
C) To define the infrastructure so it can be provisioned consistently with minimal manual tasks
D) To validate user requirements have been met within each regional datacenter for compliance

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
6
An administrator receives a warning about a filesystem filling up, and then identifies a large file located at /tmp/largelogfile . The administrator deletes the file, but no space is recovered on the filesystem. Which of the following commands would BEST assists the administrator in identifying the problem?
A) lsof | grep largelogfile
B) pkill /tmp/largelogfile
C) pgrep largelogfile
D) ps -ef | grep largelogfile
A) lsof | grep largelogfile
B) pkill /tmp/largelogfile
C) pgrep largelogfile
D) ps -ef | grep largelogfile

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
7
A Linux systems administrator needs to copy the contents of a directory named "working" on the local working system to a folder / var/www/html on a server named "corporate-web". Which of the following commands will allow the administrator to copy all the contents to the web server?
A) scp -r working/* webuser@corporate-web:/var/www/html
B) tar working/* webuser@corporate-web:/var/www/html
C) cp -r working/* webuser@corporate-web:/var/www/html
D) mv working webuser@corporate-web:/var/www/html
A) scp -r working/* webuser@corporate-web:/var/www/html
B) tar working/* webuser@corporate-web:/var/www/html
C) cp -r working/* webuser@corporate-web:/var/www/html
D) mv working webuser@corporate-web:/var/www/html

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
8
A Linux administrator is testing a new web application on a local laptop and consistently shows the following 403 errors in the laptop's logs:  The web server starts properly, but an error is generated in the audit log. Which of the following settings should be enabled to prevent this audit message?
The web server starts properly, but an error is generated in the audit log. Which of the following settings should be enabled to prevent this audit message?
A) httpd_can_network_connect = 1
B) httpd_enable_scripting = 1
C) httpd_enable_homedirs = 1
D) httpd_enable_cgi = 1
 The web server starts properly, but an error is generated in the audit log. Which of the following settings should be enabled to prevent this audit message?
The web server starts properly, but an error is generated in the audit log. Which of the following settings should be enabled to prevent this audit message?A) httpd_can_network_connect = 1
B) httpd_enable_scripting = 1
C) httpd_enable_homedirs = 1
D) httpd_enable_cgi = 1

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
9
Which of the following BEST describes containers running on a Linux system?
A) Containers only need the namespaces functionality to run on a Linux system available since kernel 2.6.
B) Containers need a hypervisor to run on a Linux system. Cgroups namespaces are functionalities used for the kernel but not for running containers.
C) Containers only need the cgroups functionality for running on a Linux system. Namespaces is not a Linux kernel functionality needed for creating and managing containers.
D) Containers use the cgroups and namespaces functionalities to isolate processes and assign hardware resources to each of those isolated processes.
A) Containers only need the namespaces functionality to run on a Linux system available since kernel 2.6.
B) Containers need a hypervisor to run on a Linux system. Cgroups namespaces are functionalities used for the kernel but not for running containers.
C) Containers only need the cgroups functionality for running on a Linux system. Namespaces is not a Linux kernel functionality needed for creating and managing containers.
D) Containers use the cgroups and namespaces functionalities to isolate processes and assign hardware resources to each of those isolated processes.

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
10
A technical support engineer receives a ticket from a user who is trying to create a 1KB file in the /tmp directory and is getting the following error: No space left on device . The support engineer checks the directory, and it has 20GB of free space. Which of the following BEST describes a possible cause for this error?
A) The /tmp directory is not mounted. The directory is not mounted.
B) The filesystem is formatted with a 4MB block size.
C) the filesystem ran out of inodes.
D) The /tmp directory has been set with an immutable attribute. directory has been set with an immutable attribute.
A) The /tmp directory is not mounted. The directory is not mounted.
B) The filesystem is formatted with a 4MB block size.
C) the filesystem ran out of inodes.
D) The /tmp directory has been set with an immutable attribute. directory has been set with an immutable attribute.

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
11
A Linux administrator must identify a user with high disk usage. The administrator runs the # du -s /home/* command and gets the following output: 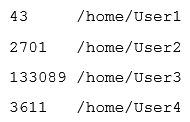 Based on the output, User3 has the largest amount of disk space used. To clean up the file space, the administrator needs to find out more information about the specific files that are using the most disk space. Which of the following commands will accomplish this task?
Based on the output, User3 has the largest amount of disk space used. To clean up the file space, the administrator needs to find out more information about the specific files that are using the most disk space. Which of the following commands will accomplish this task?
A) df -k /home/User3/files.txt
B) du -a /home/User3/*
C) du -sh /home/ User /
D) find . -name /home/User3 -print
 Based on the output, User3 has the largest amount of disk space used. To clean up the file space, the administrator needs to find out more information about the specific files that are using the most disk space. Which of the following commands will accomplish this task?
Based on the output, User3 has the largest amount of disk space used. To clean up the file space, the administrator needs to find out more information about the specific files that are using the most disk space. Which of the following commands will accomplish this task?A) df -k /home/User3/files.txt
B) du -a /home/User3/*
C) du -sh /home/ User /
D) find . -name /home/User3 -print

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
12
An administrator needs to create a shared directory in which all users are able to read, write, and execute its content but none of the regular users are able to delete any content. Which of the following permissions should be applied to this shared directory?
A) rwxrwxrwt
B) rwxrwxrws
C) rwxrwxrwx
D) rwxrwxrw*
A) rwxrwxrwt
B) rwxrwxrws
C) rwxrwxrwx
D) rwxrwxrw*

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
13
An administrator is analyzing a Linux server which was recently hacked. Which of the following will the administrator use to find all unsuccessful login attempts?
A) nsswitch
B) faillock
C) pam_tally2
D) passwd
A) nsswitch
B) faillock
C) pam_tally2
D) passwd

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
14
A systems administrator has received reports of intermittent network connectivity to a particular website. Which of the following is the BEST command to use to characterize the location and type of failure over the course of several minutes?
A) mtr www.comptia.org
B) tracert www.comptia.org
C) ping www.comptia.org
D) netstat www.comptia.org
A) mtr www.comptia.org
B) tracert www.comptia.org
C) ping www.comptia.org
D) netstat www.comptia.org

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
15
Which of the following BEST describes the purpose of the X11 system?
A) X11 provides graphical display capabilities
B) X11 provides command line capabilities
C) X11 provides networking capabilities
D) X11 provides telephony capabilities.
A) X11 provides graphical display capabilities
B) X11 provides command line capabilities
C) X11 provides networking capabilities
D) X11 provides telephony capabilities.

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
16
A new corporate policy states that Bluetooth should be disabled on all company laptops. Which of the following commands would disable the use of Bluetooth?
A) echo "blacklist bluetooth" > /etc/modprobe.d/blacklist-bluetooth
B) echo "kill bluetooth" > /etc/modprobe.d/kill-bluetooth
C) echo "modprobe bluetooth" > /etc/modprobe.d/modporbe-bluetooth
D) echo "rmmod bluetooth" > /etc/modprobe.d/rmmod-bluetooth
A) echo "blacklist bluetooth" > /etc/modprobe.d/blacklist-bluetooth
B) echo "kill bluetooth" > /etc/modprobe.d/kill-bluetooth
C) echo "modprobe bluetooth" > /etc/modprobe.d/modporbe-bluetooth
D) echo "rmmod bluetooth" > /etc/modprobe.d/rmmod-bluetooth

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
17
A junior Linux administrator is trying to verify connectivity to the remote host host1 and display round-trip statistics for ten ICMP requests. Which of the following commands should the administrator execute?
A) ping -c 10 host1
B) traceroute -c 10 host1
C) netstat host1
D) pathping -c 10 host1
A) ping -c 10 host1
B) traceroute -c 10 host1
C) netstat host1
D) pathping -c 10 host1

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
18
A systems administration team has decided to treat their systems as immutable instances. They keep the desired state of each of their systems in version control and apply automation whenever they provision a new instance. If there is an issue with one of their servers, instead of troubleshooting the issue, they terminate the instance and rebuild it using automation. Which of the following is this an example of?
A) Inventory
B) Orchestration
C) Infrastructure as code
D) Agentless deployment
A) Inventory
B) Orchestration
C) Infrastructure as code
D) Agentless deployment

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
19
An administrator needs to change the IP address on a server remotely. After updating the configuration files, a network restart is needed. However, the administrator fears that when the network connection drops, the network restart script will be killed before the new IP address has been set. Which of the following commands would prevent the script from being killed?
A) nohup service network restart
B) service network restart &
C) echo "service network restart" | at now
D) bg service network restart
A) nohup service network restart
B) service network restart &
C) echo "service network restart" | at now
D) bg service network restart

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
20
A Linux server has multiple IPs. A Linux administrator needs to verify if the HTTP server port is bound to the correct IP. Which of the following commands would BEST accomplish this task?
A) route
B) host
C) nslookup
D) netstat
E) ip
A) route
B) host
C) nslookup
D) netstat
E) ip

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
21
In order to comply with new security policies, an administrator needs to prevent the SSH server from using insecure algorithms. Which of the following files should be edited to accomplish this?
A) /etc/ssh/sshd_config
B) /etc/ssh/ssh_config
C) ~/.ssh/ssh_config
D) /etc/ssh/known_hosts
A) /etc/ssh/sshd_config
B) /etc/ssh/ssh_config
C) ~/.ssh/ssh_config
D) /etc/ssh/known_hosts

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
22
Joe, a user, is unable to log in to the server and contracts the systems administrator to look into the issue. The administrator examines the /etc/passwd file and discovers the following entry: joe:x:505:505::/home/joe:/bin/false Which of the following commands should the administrator execute to resolve the problem?
A) usermod -s /bin/bash joe
B) passwd -u joe
C) useradd -s /bin/bash joe
D) chage -E -1 joe
A) usermod -s /bin/bash joe
B) passwd -u joe
C) useradd -s /bin/bash joe
D) chage -E -1 joe

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
23
Two specific users need access to a directory owned by root where backups are located. Which of the following commands would BEST ensure the specified users can access the backup files?
A) umask
B) chcon
C) chmod
D) setfacl
A) umask
B) chcon
C) chmod
D) setfacl

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
24
Which of the following configuration files should be modified to disable Ctrl+Alt+Del in Linux?
A) /etc/inittab
B) ~/.bash_profile
C) /etc/securetty
D) /etc/security/limits.conf
A) /etc/inittab
B) ~/.bash_profile
C) /etc/securetty
D) /etc/security/limits.conf

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
25
A Linux administrator needs to take stock of USB devices attached to the system. Which of the following commands would be BEST to complete this task?
A) lspci
B) lsusb
C) cat /proc/USB
D) modprobe --usb
A) lspci
B) lsusb
C) cat /proc/USB
D) modprobe --usb

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
26
A systems administrator configured a new kernel module, but it stopped working after reboot. Which of the following will allow the systems administrator to check for module problems during server startup?
A) lsmod
B) modprobe
C) modinfo
D) dmesg
A) lsmod
B) modprobe
C) modinfo
D) dmesg

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
27
A systems administrator has finished building a new feature for the monitoring software in a separate Git branch. Which of the following is the BEST method for adding the new feature to the software's master branch?
A) Merge the changes from the feature branch to the master branch.
B) Save the changes to the master branch automatically with each Git commit.
C) Clone the feature branch into the master branch.
D) Pull the changes from the feature branch into the master branch.
A) Merge the changes from the feature branch to the master branch.
B) Save the changes to the master branch automatically with each Git commit.
C) Clone the feature branch into the master branch.
D) Pull the changes from the feature branch into the master branch.

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
28
A Linux administrator needs the "tech" account to have the option to run elevated commands as root. Which of the following commands would BEST meet this goal?
A) $ su - tech -c "/bin/bash"
B) # usermod -aG wheel tech
C) # sudo -i tech
D) # groupadd -u tech -g root
A) $ su - tech -c "/bin/bash"
B) # usermod -aG wheel tech
C) # sudo -i tech
D) # groupadd -u tech -g root

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
29
Which of the following server roles would assign a host IP address?
A) DHCP
B) NTP
C) DNS
D) SSH
A) DHCP
B) NTP
C) DNS
D) SSH

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
30
A systems administrator has deployed a Linux server based on an Anaconda process with all packages and custom configurations necessary to install a web server role. Which of the following could be used to install more Linux servers with the same characteristics?
A) /etc/sysconfig/anaconda.cfg
B) /root/anaconda.auto
C) /root/anaconda-ks.cfg
D) /etc/sysconfig/installation.cfg
A) /etc/sysconfig/anaconda.cfg
B) /root/anaconda.auto
C) /root/anaconda-ks.cfg
D) /etc/sysconfig/installation.cfg

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
31
A junior Linux administrator is installing patches using YUM. The administrator issues the following command: yum list installed The output of the command is as follows: 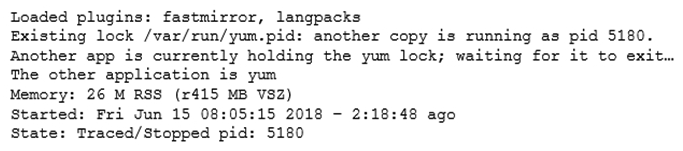 Given this scenario and the output, which of the following should the administrator do to address this issue?
Given this scenario and the output, which of the following should the administrator do to address this issue?
A) renice -n 9 -p 5180
B) killall yum
C) ps -ef | grep yum
D) top | grep yum
 Given this scenario and the output, which of the following should the administrator do to address this issue?
Given this scenario and the output, which of the following should the administrator do to address this issue?A) renice -n 9 -p 5180
B) killall yum
C) ps -ef | grep yum
D) top | grep yum

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
32
A systems administrator must clean up all application files in the directory /var/log/app. However, the company's security policy requires the files to be kept on the backup server for one year. The Linux server has only the tar and bzip2 packages installed. Which of the following commands will package and compress the files?
A) tar -zcvf applicationfiles.tar.bz2 /var/log/app/*
B) tar -jcvf applicationfiles.tar.bz2 /var/log/app/*
C) tar -cvf applicationfiles.tar.bz2 /var/log/app/*
D) tar -xvf applicationfiles.tar.bz2 /var/log/app/*
A) tar -zcvf applicationfiles.tar.bz2 /var/log/app/*
B) tar -jcvf applicationfiles.tar.bz2 /var/log/app/*
C) tar -cvf applicationfiles.tar.bz2 /var/log/app/*
D) tar -xvf applicationfiles.tar.bz2 /var/log/app/*

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
33
A server is almost out of free memory and is becoming unresponsive. Which of the following sets of commands will BEST mitigate the issue?
A) free, fack, partprobe
B) lsof, lvcreate, mdadm
C) df, du, rmmod
D) fdisk, mkswap, swapon -a
A) free, fack, partprobe
B) lsof, lvcreate, mdadm
C) df, du, rmmod
D) fdisk, mkswap, swapon -a

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
34
A junior Linux administrator is optimizing a system in which an application needs to take priority 0 when running the process. The administrator runs the ps command and receives the following output:  Given this scenario, which of the following steps will address this issue?
Given this scenario, which of the following steps will address this issue?
A) Issue the command renice -n 0 -p 8481 Issue the command renice -n 0 -p 8481
B) Issue the command renice -p 8481 renice -p 8481
C) Issue the command renice -p 0 -n 8481 renice -p 0 -n 8481
D) Issue the command renice -n 8481 renice -n 8481
 Given this scenario, which of the following steps will address this issue?
Given this scenario, which of the following steps will address this issue?A) Issue the command renice -n 0 -p 8481 Issue the command renice -n 0 -p 8481
B) Issue the command renice -p 8481 renice -p 8481
C) Issue the command renice -p 0 -n 8481 renice -p 0 -n 8481
D) Issue the command renice -n 8481 renice -n 8481

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
35
Ann, a junior systems administrator, is required to add a line to the /etc/yum.conf file. However, she receives the following error message when she tries to add the line: 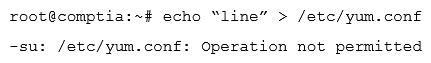 Ann performs some diagnostics to attempt to find the root cause:
Ann performs some diagnostics to attempt to find the root cause: 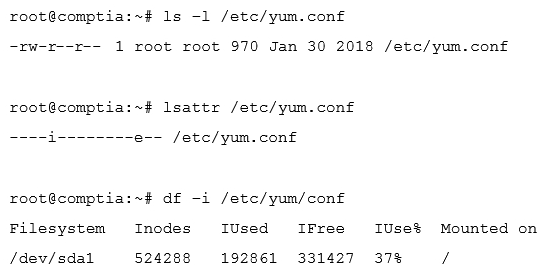 Which of the following commands should Ann execute to write content to /etc/yum ?
Which of the following commands should Ann execute to write content to /etc/yum ?
A) chmod 755 /etc/yum.conf
B) setfacl -m m:rw /etc/yum.conf
C) chattr -i /etc/yum.conf
D) setenforce 0
 Ann performs some diagnostics to attempt to find the root cause:
Ann performs some diagnostics to attempt to find the root cause:  Which of the following commands should Ann execute to write content to /etc/yum ?
Which of the following commands should Ann execute to write content to /etc/yum ?A) chmod 755 /etc/yum.conf
B) setfacl -m m:rw /etc/yum.conf
C) chattr -i /etc/yum.conf
D) setenforce 0

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
36
An administrator reviews the following configuration file provided by a DevOps engineer: 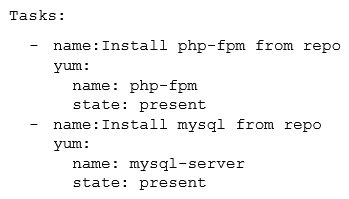 Which of the following would the application parsing this file MOST likely have to support?
Which of the following would the application parsing this file MOST likely have to support?
A) YAML
B) AJAX
C) JSON
D) SOAP
 Which of the following would the application parsing this file MOST likely have to support?
Which of the following would the application parsing this file MOST likely have to support?A) YAML
B) AJAX
C) JSON
D) SOAP

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
37
Which of the following is a difference between YAML and JSON?
A) Users can comment in YAML but not in JSON
B) JSON only uses curly brackets, while YAML only uses square brackets
C) JSON is used in web development, while YAML is used solely in back-end systems.
D) YAML has been deprecated for JSON.
A) Users can comment in YAML but not in JSON
B) JSON only uses curly brackets, while YAML only uses square brackets
C) JSON is used in web development, while YAML is used solely in back-end systems.
D) YAML has been deprecated for JSON.

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
38
Which of the following will provide a list of all flash, external, internal, and SSD drives?
A) lspci
B) lsmod
C) lsblk
D) lsusb
A) lspci
B) lsmod
C) lsblk
D) lsusb

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
39
A Linux administrator is using a Linux system as a router. During the tests, the administrator discovers that IP packets are not being sent between the configured interfaces. Which of the following commands enables this feature for IPv4 networks?
A) cat /proc/sys/net/ipv4/ip_route > 1
B) echo "1" > /proc/sys/net/ipv4/ip_forward
C) echo "1" > /proc/sys/net/ipv4/ip_route
D) echo "1" > /proc/sys/net/ipv4/ip_net
A) cat /proc/sys/net/ipv4/ip_route > 1
B) echo "1" > /proc/sys/net/ipv4/ip_forward
C) echo "1" > /proc/sys/net/ipv4/ip_route
D) echo "1" > /proc/sys/net/ipv4/ip_net

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
40
Which of the following configuration management tools is considered agentless?
A) Puppet
B) Salt
C) Ansible
D) Chef
A) Puppet
B) Salt
C) Ansible
D) Chef

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
41
A company wants to ensure that all newly created files can be modified only by their owners and that all new directory content can be changed only by the creator of the directory. Which of the following commands will help achieve this task?
A) umask 0022
B) umask 0012
C) chmod -R 0644 /
D) chmod -R 0755 /
A) umask 0022
B) umask 0012
C) chmod -R 0644 /
D) chmod -R 0755 /

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
42
A junior systems administrator is upgrading a package that was installed on a Red Hat-based system. The administrator is tasked with the following: Update and install the new package. Verify the new package version is installed. Which of the following should be done to BEST accomplish these task? (Choose two.)
A) yum install
B) yum upgrade
C) rpm -e
D) rpm -qa
E) apt-get
F) apt-get upgrade
A) yum install
B) yum upgrade
C) rpm -e
D) rpm -qa
E) apt-get
F) apt-get upgrade

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
43
A user, jsmith, needs access to database files located on a server. Which of the following will add jsmith to the "dba" group and preserve existing group memberships?
A) usermod -a -G dba jsmith
B) usermod -g dba jsmith
C) useradd -g dba jsmith
D) groupmod dba -u jsmith
A) usermod -a -G dba jsmith
B) usermod -g dba jsmith
C) useradd -g dba jsmith
D) groupmod dba -u jsmith

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
44
A Linux administrator retrieved a repository of files from a Git server using git clone . The administrator wants to see if a configuration file was added to the repository. Which of the following Git arguments should be used to see the recent modifications?
A) fetch
B) log
C) init
D) pull
A) fetch
B) log
C) init
D) pull

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
45
A Linux administrator needs to back up the folder /usr/domain , and the output must be a gzip compressed tar. Which of the following commands should be used?
A) tar -cv domain.tar.gz /usr/domain
B) tar -cvf /usr/domain domain.tar.gz
C) tar -czvf domain.tar.gz /usr/domain
D) tar -cxzv /usr/domain domain.tar.gz
A) tar -cv domain.tar.gz /usr/domain
B) tar -cvf /usr/domain domain.tar.gz
C) tar -czvf domain.tar.gz /usr/domain
D) tar -cxzv /usr/domain domain.tar.gz

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
46
A systems administrator is enabling quotas on the /home directory of a Linux server. The administrator makes the appropriate edits to the /etc/fstab file and attempts to issue the commands to enable quotas on the desired directory. However, the administrator receives an error message stating the filesystem does not support quotas. Which of the following commands should the administrator perform to proceed?
A) mount -o remount /home
B) quotacheck -cg
C) edquota /home
D) quotaon /home
A) mount -o remount /home
B) quotacheck -cg
C) edquota /home
D) quotaon /home

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
47
Given that a company's policy states that users cannot install third-party tools on Window servers, which of the following protocols will allow a Linux GUI to connect to a Windows server?
A) VNC
B) NX
C) RDP
D) X11
A) VNC
B) NX
C) RDP
D) X11

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
48
An administrator needs to see a list of the system user's encrypted passwords. Which of the following Linux files does the administrator need to read?
A) /etc/shadow
B) /etc/skel
C) /etc/passwd
D) /etc/pw
A) /etc/shadow
B) /etc/skel
C) /etc/passwd
D) /etc/pw

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
49
A Linux administrator opens a ticket to have an external hard drive mounted. As a security policy, external storage kernel modules are disabled. Which of the following is the BEST command for adding the proper kernel module to enable external storage modules?
A) rmmod /lib/modules/3.6.12-100-generic/kernel/drivers/usb/storage/usb-storage.ko
B) modinfo /lib/modules/3.6.12-100-generic/kernel/drivers/usb/storage/usb-storage.ko
C) depmod /lib/modules/3.6.12-100-generic/kernel/drivers/usb/storage/usb-storage.ko
D) insmod /lib/modules/3.6.12-100-generic/kernel/drivers/usb/storage/usb-storage.ko
A) rmmod /lib/modules/3.6.12-100-generic/kernel/drivers/usb/storage/usb-storage.ko
B) modinfo /lib/modules/3.6.12-100-generic/kernel/drivers/usb/storage/usb-storage.ko
C) depmod /lib/modules/3.6.12-100-generic/kernel/drivers/usb/storage/usb-storage.ko
D) insmod /lib/modules/3.6.12-100-generic/kernel/drivers/usb/storage/usb-storage.ko

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
50
Which of the following is the template for the grub.cfg file?
A) /etc/default/grub
B) /etc/grub2.cfg
C) /etc/sysct1.conf
D) /boot/efi
A) /etc/default/grub
B) /etc/grub2.cfg
C) /etc/sysct1.conf
D) /boot/efi

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
51
A new HTTPS web service is being deployed on a server. Which of the following commands should the Linux administrator use to ensure traffic is able to flow through the system firewall to the new service?
A) iptables -I OUTPUT -p tcp --sport 443 -j ACCEPT
B) iptables -A INPUT -p tcp --dport 443 -j ACCEPT
C) iptables -I INPUT --dport 443 -j ACCEPT
D) iptables -A OUTPUT -p tcp --dport 443 -j ACCEPT
A) iptables -I OUTPUT -p tcp --sport 443 -j ACCEPT
B) iptables -A INPUT -p tcp --dport 443 -j ACCEPT
C) iptables -I INPUT --dport 443 -j ACCEPT
D) iptables -A OUTPUT -p tcp --dport 443 -j ACCEPT

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
52
An administrator is tasked with increasing the size of the volume /dev/vg/lv to 20GB. Which of the following BEST illustrates the steps the administrator should take?
A) vgextend -L20G /dev/vg/lv; resizelv /dev/vg/lv
B) parted -L20G /dev/vg/lv; remount /dev/vg/lv
C) mkfs -L20G /dev/vg/lv; tune2fs /dev/vg/lv
D) lvextend -L20G /dev/vg/lv; resize2fs /dev/vg/lv
A) vgextend -L20G /dev/vg/lv; resizelv /dev/vg/lv
B) parted -L20G /dev/vg/lv; remount /dev/vg/lv
C) mkfs -L20G /dev/vg/lv; tune2fs /dev/vg/lv
D) lvextend -L20G /dev/vg/lv; resize2fs /dev/vg/lv

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
53
Which of the following statements BEST represents what the term "agentless" means regarding orchestration?
A) Installation of a tool is not required on the remote system to perform orchestration tasks
B) It facilitates version control when using infrastructure as code during orchestration
C) It automatically removes malware from the remote system during orchestration
D) A tool can only be accessed remotely to perform orchestration tasks
A) Installation of a tool is not required on the remote system to perform orchestration tasks
B) It facilitates version control when using infrastructure as code during orchestration
C) It automatically removes malware from the remote system during orchestration
D) A tool can only be accessed remotely to perform orchestration tasks

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
54
A Linux administrator built a GitLab server. Later that day, a software engineer tried to access the server to upload the repository during the final step of installation. The software engineer could not access the website. Which of the following firewall rules would allow access to this site?
A) iptables -A INPUT -p tcp -m multiport --dports 80,443 -m conntrack -cstate NEW, ESTABLISHED -j ACCEPT
B) iptables -A INPUT -p tcp -m multiport --dports 80,443 -m conntrack -cstate ESTABLISHED -j ACCEPT
C) iptables -A INPUT -p tcp -m multiport --dports 80,443 -m conntrack -cstate RELATED, ESTABLISHED -j ACCEPT
D) iptables -A INPUT -p tcp -m multiport --dports 80,443 -m conntrack -cstate NEW, ESTABLISHED -j REJECT
A) iptables -A INPUT -p tcp -m multiport --dports 80,443 -m conntrack -cstate NEW, ESTABLISHED -j ACCEPT
B) iptables -A INPUT -p tcp -m multiport --dports 80,443 -m conntrack -cstate ESTABLISHED -j ACCEPT
C) iptables -A INPUT -p tcp -m multiport --dports 80,443 -m conntrack -cstate RELATED, ESTABLISHED -j ACCEPT
D) iptables -A INPUT -p tcp -m multiport --dports 80,443 -m conntrack -cstate NEW, ESTABLISHED -j REJECT

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
55
Which of the following is modified to reconfigure the boot environment?
A) grub-mkconfig
B) grub.cfg
C) update-grub
D) grub2-mkconfig
A) grub-mkconfig
B) grub.cfg
C) update-grub
D) grub2-mkconfig

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
56
While creating a file on a volume, the Linux administrator receives the following message: No space left on device. Running the df -m command, the administrator notes there is still 50% of usage left. Which of the following is the NEXT step the administrator should take to analyze the issue without losing data?
A) Run the df -i command and notice the inode exhaustion Run the df -i command and notice the inode exhaustion
B) Run the df -h command and notice the space exhaustion df -h command and notice the space exhaustion
C) Run the df -B command and notice the block size df -B command and notice the block size
D) Run the df -k command and notice the storage exhaustion df -k command and notice the storage exhaustion
A) Run the df -i command and notice the inode exhaustion Run the df -i command and notice the inode exhaustion
B) Run the df -h command and notice the space exhaustion df -h command and notice the space exhaustion
C) Run the df -B command and notice the block size df -B command and notice the block size
D) Run the df -k command and notice the storage exhaustion df -k command and notice the storage exhaustion

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
57
A systems administrator is unable to reach other devices on the network and the Internet. The server is configured with the IP address 192.169.1.50/24 on eth0 . The server's router is 192.168.1.1. The administrator reviews the output of route -n : 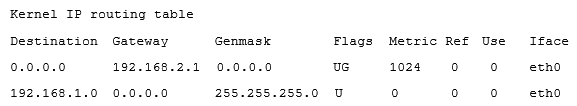 Which of the following commands should the administrator run to correct the issue?
Which of the following commands should the administrator run to correct the issue?
A) route del default gw 192.168.2.1 eth0; route add default gw 192.168.1.1 eth0
B) route add -net 192.168.10.0 netmask 255.255.255.0 gw 192.168.2.1 eth0
C) route add 192.168.1.1 default 192.168.1.50 eth0
D) route host gw 192.168.1.1 eth0
 Which of the following commands should the administrator run to correct the issue?
Which of the following commands should the administrator run to correct the issue?A) route del default gw 192.168.2.1 eth0; route add default gw 192.168.1.1 eth0
B) route add -net 192.168.10.0 netmask 255.255.255.0 gw 192.168.2.1 eth0
C) route add 192.168.1.1 default 192.168.1.50 eth0
D) route host gw 192.168.1.1 eth0

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
58
An administrator has modified the configuration file for a service. The service is still running but is not using the new configured values. Which of the following will BEST remediate this issue?
A) kill -HUP
B) init 0
C) service start
D) renice -10
A) kill -HUP
B) init 0
C) service start
D) renice -10

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
59
A Linux administrator needs every new file created on a directory to maintain the group permissions of the same directory. Which of the following commands would satisfy this requirement?
A) chmod o+s
B) chmod u+s
C) chmod +s
D) chmod g+s
A) chmod o+s
B) chmod u+s
C) chmod +s
D) chmod g+s

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
60
A systems administrator needs to install a new piece of hardware that requires a new driver. The driver should be manually installed. Which of the following describes the order of commands required to obtain module information, install the module, and check the log for any errors during module installation?
A) lsmod, modprobe, modinfo
B) modinfo, insmod, modprobe
C) modinfo, insmod, dmesg
D) lsmod, insmod, dmesg
A) lsmod, modprobe, modinfo
B) modinfo, insmod, modprobe
C) modinfo, insmod, dmesg
D) lsmod, insmod, dmesg

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
61
A Linux systems administrator installed a new web server, which failed while attempting to start. The administrator suspects that SELinux is causing an issue and wants to temporarily put the system into permissive mode. Which of the following would allow the administrator to accomplish this?
A) echo SELINUX=PERMISSIVE >> /etc/sysconfig/selinux
B) setenforce 0
C) sestatus 0
D) chcon httpd_sys_content_t /var/
A) echo SELINUX=PERMISSIVE >> /etc/sysconfig/selinux
B) setenforce 0
C) sestatus 0
D) chcon httpd_sys_content_t /var/

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
62
A systems administrator suspects a process with a PID of 2864 is consuming resources at an alarming rate. The administrator uses the command renice -n -5 -p2864 , but it does not solve the issue. Which of the following commands should the administrator execute to correct the issue?
A) nice -n 5 -p 2864
B) nice -n -5 -p 2864
C) renice -n 10 -p 2864
D) renice -n -10 -p 2864
A) nice -n 5 -p 2864
B) nice -n -5 -p 2864
C) renice -n 10 -p 2864
D) renice -n -10 -p 2864

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
63
A junior Linux administrator needs to access production servers using a secure SSH protocol. Which of the following files should contain the public key to gain remote access to the server?
A) ~/ssh/authorized-keys
B) /etc/authorized_keys
C) /etc/sshd/ssh.conf
D) ~/.ssh/authorized_keys
A) ~/ssh/authorized-keys
B) /etc/authorized_keys
C) /etc/sshd/ssh.conf
D) ~/.ssh/authorized_keys

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
64
An analyst is trying to determine which public IP addresses are managed by Company A, but the script is not working correctly. 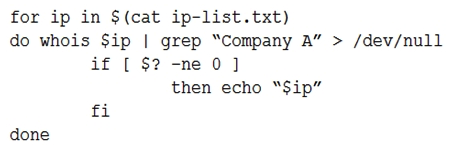 Which of the following explains what is wrong with the script?
Which of the following explains what is wrong with the script?
A) $(cat ip-list.txt) should be changed to `cat ip-list.txt` in the for statement. $(cat ip-list.txt) should be changed to `cat ip-list.txt` in the for statement.
B) The for should be changed to while in the loop. The while in the loop.
C) The > should be changed to 2> in the do statement. > 2> do statement.
D) The -ne flag should be changed to -eq in the if statement. -ne flag should be changed to -eq if
 Which of the following explains what is wrong with the script?
Which of the following explains what is wrong with the script?A) $(cat ip-list.txt) should be changed to `cat ip-list.txt` in the for statement. $(cat ip-list.txt) should be changed to `cat ip-list.txt` in the for statement.
B) The for should be changed to while in the loop. The while in the loop.
C) The > should be changed to 2> in the do statement. > 2> do statement.
D) The -ne flag should be changed to -eq in the if statement. -ne flag should be changed to -eq if

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
65
A four-drive Linux NAS has been improperly configured. Each drive has a capacity of 6TB, for a total storage capacity of 24TB. To reconfigure this unit to be not pluggable for drive replacement and provide total storage of 11TB to 12TB, which of the following would be the correct RAID configuration?
A) RAID 01
B) RAID 03
C) RAID 10
D) RAID 50
A) RAID 01
B) RAID 03
C) RAID 10
D) RAID 50

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
66
An administrator is logged into a server remotely and wants to determine if the system is a VM. Which of the following commands would assist with this?
A) dmesg
B) ps
C) top
D) vmstat
A) dmesg
B) ps
C) top
D) vmstat

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
67
A Linux systems administrator is setting up SSH access with PKI for several using their newly created RSA keys. Which of the following MOST securely achieves this task?
A) Use curl to copy each user's public key file to the respective system Use curl to copy each user's public key file to the respective system
B) Use cp to copy each user's public key file to the respective system cp
C) Use ssh-copy-id to copy each user's public key file to the respective system ssh-copy-id
D) Use ssh-copy-id to copy each user's private key file to the respective system to copy each user's private key file to the respective system
A) Use curl to copy each user's public key file to the respective system Use curl to copy each user's public key file to the respective system
B) Use cp to copy each user's public key file to the respective system cp
C) Use ssh-copy-id to copy each user's public key file to the respective system ssh-copy-id
D) Use ssh-copy-id to copy each user's private key file to the respective system to copy each user's private key file to the respective system

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
68
A user wants to list the lines of a log, adding a correlative number at the beginning of each line separated by a set of dashes from the actual message. Which of the following scripts will complete this task?
A)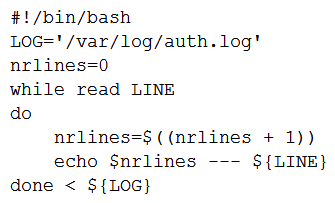
B)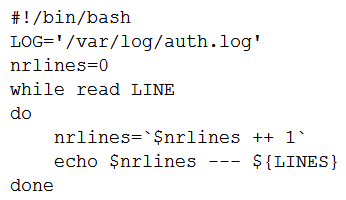
C)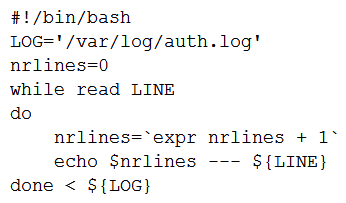
D)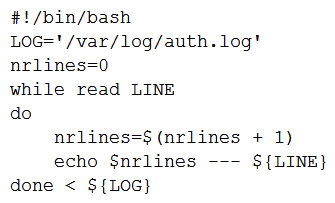
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
69
The development team has automated their software build process so each time a change is submitted to the source code repository, a new software build is compiled. They are requesting that the Linux operations team look into automating the deployment of the software build into the test environment. Which of the following is the benefit to the development team for implementing deployment automation?
A) To ensure the build commits are also deployed to the test environment
B) To enable notifications when builds are deployed to the test environment
C) To ensure software builds in test are not accidentally deployed to production
D) To streamline the deployment process for deploying builds into test environments
A) To ensure the build commits are also deployed to the test environment
B) To enable notifications when builds are deployed to the test environment
C) To ensure software builds in test are not accidentally deployed to production
D) To streamline the deployment process for deploying builds into test environments

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
70
A junior Linux administrator needs to ensure a service will start on system boot. Which of the following commands should be used to accomplish this task?
A) chkconfig on
B) systemctl bootup
C) service enable
D) crontab install
A) chkconfig
B) systemctl
C) service
D) crontab install

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
71
Joe, a member of the accounting group on a Linux system, is unable to write a file called "taxes" in the accounting shared directory. The ownership and permissions on the directory and file are as follows: accounting drwxrw-r-- user = ann, group = accounting taxes -rw-r--r-- , user = ann, group = accounting Which of the following commands would allow Joe to write to the file? (Choose two.)
A) chmod g+x accounting
B) chmod 777 taxes
C) chgrp taxes accounting
D) chgrp accounting taxes
E) chmod 774 accounting
F) chmod u+x accounting
A) chmod g+x accounting
B) chmod 777 taxes
C) chgrp taxes accounting
D) chgrp accounting taxes
E) chmod 774 accounting
F) chmod u+x accounting

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
72
A Linux administrator needs to schedule a cron job to run at 1:15 p.m. every Friday to report the amount of free disk space on the system and to send the output to a file named "freespace". Which of the following would meet this requirement?
A) 13 15 * * 5 df > /freespace
B) 15 13 * * 5 df > /freespace
C) 15 1 * * 6 df > /freespace
D) 15 13 6 * * df > /freespace
A) 13 15 * * 5 df > /freespace
B) 15 13 * * 5 df > /freespace
C) 15 1 * * 6 df > /freespace
D) 15 13 6 * * df > /freespace

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
73
A member of the production group issues the following command: echo "Monday through Friday" > /production_docs/days The command fails to execute, so the user obtains the following output: drwxr--r-- root production 0 Jun 16 2018 production -rw-r--r-- production production 4096 Jun 14 2018 days Which of the following commands should the user execute to BEST fix the issue?
A) chmod g+w production to change the permissions on the days file chmod g+w production to change the permissions on the days file
B) chgrp root production_docs/days to change the group ownership of the production_docs/days file chgrp root production_docs/days to change the group ownership of the production_docs/days
C) chmod g+S production to set the GUID on the production_docs directory chmod g+S production to set the GUID on the production_docs directory
D) chown production to change the ownership of the production_docs directory chown production to change the ownership of the
A) chmod g+w production to change the permissions on the days file chmod g+w production to change the permissions on the days file
B) chgrp root production_docs/days to change the group ownership of the production_docs/days file chgrp root production_docs/days to change the group ownership of the production_docs/days
C) chmod g+S production to set the GUID on the production_docs directory chmod g+S production to set the GUID on the production_docs directory
D) chown production to change the ownership of the production_docs directory chown production to change the ownership of the

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
74
Ann, a Linux administrator, wants to edit a configuration management file. When she opens the file to edit, her text editor reports that the file has been opened in read-only mode. She then tries to edit the file as root by elevating via sudo and is still unable to save any changes. The error message in her text editor says that the read-only option is set on the file. Ann checks the permissions on the file and sees the following: -rw-rw-r-- 1 root wheel 30 Jun 13 15:38 infrastructure.yml Which of the following commands is the BEST option to allow her to successfully modify the file?
A) chmod 600 infrastructure.yml
B) chown root: infrastructure.yml
C) chattr -i infrastructure.yml
D) chmod o+w infrastructure.yml
A) chmod 600 infrastructure.yml
B) chown root: infrastructure.yml
C) chattr -i infrastructure.yml
D) chmod o+w infrastructure.yml

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
75
A systems administrator wants to download a package from a remote server. Which of the following are the BEST commands to use for this task? (Choose two.)
A) curl
B) wget
C) make
D) tar
E) zip
F) nc
A) curl
B) wget
C) make
D) tar
E) zip
F) nc

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
76
An administrator needs to generate a list of services that are listening on TCP and/or UDP ports. Which of the following tools should the administrator use?
A) ethtool
B) route
C) netstat
D) portmap
A) ethtool
B) route
C) netstat
D) portmap

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
77
A Linux administrator has installed a web application firewall in front of a web server running on HTTP port 8080 and successfully started the HTTP server. However, after opening the application URL in an Internet browser, the administrator discovered that the application does not work. The administrator performed the following diagnostic steps: Output of sysctl -a command: 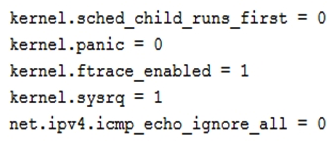 iptables -L
iptables -L 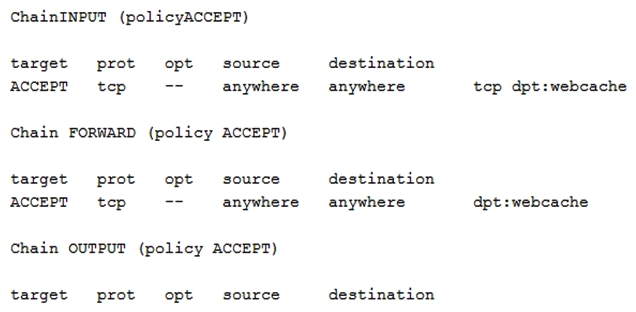 netstat -nltop | grep "8080" :
netstat -nltop | grep "8080" : 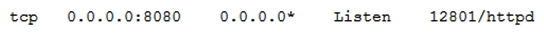 Which of the following is the NEXT step the administrator should perform to permanently fix the issue at the kernel level?
Which of the following is the NEXT step the administrator should perform to permanently fix the issue at the kernel level?
A) sysctl -w net.ipv4.ip_forward=1 then run sysctl -w /etc/sysctl.conf to enable the change sysctl -w net.ipv4.ip_forward=1 then run sysctl -w /etc/sysctl.conf to enable the change
B) Edit /etc/sysctl.conf file and add net.ipv4.ip_forward = 1 then run sysctl -p /etc/sysctl.conf to enable the change Edit /etc/sysctl.conf file and add net.ipv4.ip_forward = 1 sysctl -p /etc/sysctl.conf
C) Add iptables rule iptables -A INPUT -m state --state NEW -p tcp --dport 8080 -j then restart httpd daemon Add iptables rule iptables -A INPUT -m state --state NEW -p tcp --dport 8080 -j then restart httpd daemon
D) Add iptables rule iptables -A FORWARD-m state --state NEW -p tcp --dport 8080 -j ACCEPT then restart httpd daemon iptables -A FORWARD-m state --state NEW -p tcp --dport 8080 -j ACCEPT
 iptables -L
iptables -L  netstat -nltop | grep "8080" :
netstat -nltop | grep "8080" : 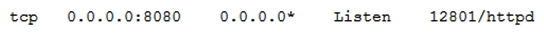 Which of the following is the NEXT step the administrator should perform to permanently fix the issue at the kernel level?
Which of the following is the NEXT step the administrator should perform to permanently fix the issue at the kernel level?A) sysctl -w net.ipv4.ip_forward=1 then run sysctl -w /etc/sysctl.conf to enable the change sysctl -w net.ipv4.ip_forward=1 then run sysctl -w /etc/sysctl.conf to enable the change
B) Edit /etc/sysctl.conf file and add net.ipv4.ip_forward = 1 then run sysctl -p /etc/sysctl.conf to enable the change Edit /etc/sysctl.conf file and add net.ipv4.ip_forward = 1 sysctl -p /etc/sysctl.conf
C) Add iptables rule iptables -A INPUT -m state --state NEW -p tcp --dport 8080 -j then restart httpd daemon Add iptables rule iptables -A INPUT -m state --state NEW -p tcp --dport 8080 -j then restart httpd daemon
D) Add iptables rule iptables -A FORWARD-m state --state NEW -p tcp --dport 8080 -j ACCEPT then restart httpd daemon iptables -A FORWARD-m state --state NEW -p tcp --dport 8080 -j ACCEPT

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
78
A junior systems administrator is creating a cron job. The cron job requirements are as follows: Run the hello.sh script every hour (24 times in one day). Run it on Monday only. Given this scenario, which of the following crontab options should be configured to meet these requirements?
A) 0 *** 1 hello.sh
B) 0 24 ** Monday hello.sh
C) 24 *** Monday hello.sh
D) 1 *** 0 hello.sh
A) 0 *** 1 hello.sh
B) 0 24 ** Monday hello.sh
C) 24 *** Monday hello.sh
D) 1 *** 0 hello.sh

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
79
A technician wants to secure a sensitive workstation by ensuring network traffic is kept within the local subnet. To accomplish this task, the technician executes the following command: echo 0 > /proc/sys/net/ipv4/ip_default_ttl Which of the following commands can the technician use to confirm the expected results? (Choose two.)
A) tcpdump
B) traceroute
C) route
D) iperf
E) ip
F) arp
A) tcpdump
B) traceroute
C) route
D) iperf
E) ip
F) arp

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck
80
A junior systems administrator created a new filesystem /dev/sda1 with mountpoint /data and added it to the /etc/fstab for auto-mounting. When the systems administrator tries to mount the file system, the system refuses. Given the output below: 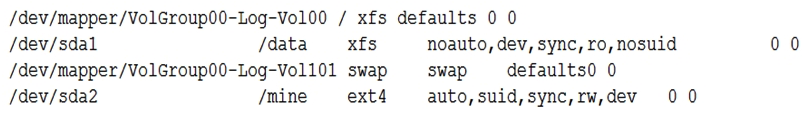 Which of the following steps is necessary?
Which of the following steps is necessary?
A) Change the filesystem from /dev/sda1 to /dev/sda2 and reboot. Change the filesystem from to /dev/sda2 and reboot.
B) Change the options to auto,dev,sync,rw,nosuid and run the mount -a command. Change the options to auto,dev,sync,rw,nosuid and run the mount -a command.
C) Change the mount point to data and reboot.
D) Change the dump column to 1 and run the mount -a command. Change the dump column to 1 and run the
 Which of the following steps is necessary?
Which of the following steps is necessary?A) Change the filesystem from /dev/sda1 to /dev/sda2 and reboot. Change the filesystem from to /dev/sda2 and reboot.
B) Change the options to auto,dev,sync,rw,nosuid and run the mount -a command. Change the options to auto,dev,sync,rw,nosuid and run the mount -a command.
C) Change the mount point to data and reboot.
D) Change the dump column to 1 and run the mount -a command. Change the dump column to 1 and run the

Unlock Deck
Unlock for access to all 252 flashcards in this deck.
Unlock Deck
k this deck


