Exam 18: CompTIA Linux+
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A junior administrator of a physical server receives log messages indicating the out-of-memory killer has been active. All memory slots are in use on the motherboard, but additional disk space is available. Space has been allocated for a swap file. Which of the following should the administrator use to reduce the output of memory messages?
Free
(Multiple Choice)
4.9/5  (36)
(36)
Correct Answer:
A
Which of the following can be used to boot a DVD from a remote device to initialize a Linux system setup on bare metal hardware as if it is a local DVD?
Free
(Multiple Choice)
4.8/5  (36)
(36)
Correct Answer:
A
A junior Linux administrator is trying to verify connectivity to the remote host host1 and display round-trip statistics for ten ICMP requests. Which of the following commands should the administrator execute?
Free
(Multiple Choice)
4.8/5  (30)
(30)
Correct Answer:
A
A Linux administrator recently reprovisioned a new corporate web server to replace a legacy one. To minimize the impact on the company's users, the administrator modified the network and DNS settings of the new server to be the same as the legacy server. When attempting to log in to the new server remotely over SSH, the following error message is displayed: WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! Which of the following should the administrator do to resolve the issue?
(Multiple Choice)
4.8/5  (40)
(40)
A Linux administrator needs to remotely update the contents of the www.comptia.org/contacts URL. Which of the following commands would allow the administrator to download the current contents of the URL before updating?
(Multiple Choice)
4.9/5  (35)
(35)
Ann, a Linux administrator, wants to edit a configuration management file. When she opens the file to edit, her text editor reports that the file has been opened in read-only mode. She then tries to edit the file as root by elevating via sudo and is still unable to save any changes. The error message in her text editor says that the read-only option is set on the file. Ann checks the permissions on the file and sees the following: -rw-rw-r-- 1 root wheel 30 Jun 13 15:38 infrastructure.yml Which of the following commands is the BEST option to allow her to successfully modify the file?
(Multiple Choice)
4.8/5  (34)
(34)
A user has connected a Bluetooth mouse to a computer, but it is not working properly. Which of the following commands should the systems administrator use to fix the issue?
(Multiple Choice)
4.9/5  (27)
(27)
The development team has automated their software build process so each time a change is submitted to the source code repository, a new software build is compiled. They are requesting that the Linux operations team look into automating the deployment of the software build into the test environment. Which of the following is the benefit to the development team for implementing deployment automation?
(Multiple Choice)
4.8/5  (40)
(40)
An analyst is trying to determine which public IP addresses are managed by Company A, but the script is not working correctly. 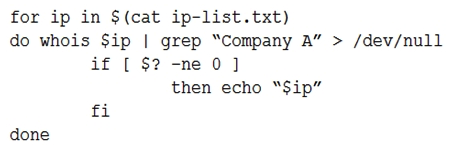 Which of the following explains what is wrong with the script?
Which of the following explains what is wrong with the script?
(Multiple Choice)
4.8/5  (30)
(30)
A systems administrator has finished building a new feature for the monitoring software in a separate Git branch. Which of the following is the BEST method for adding the new feature to the software's master branch?
(Multiple Choice)
4.9/5  (37)
(37)
An administrator receives an alarm because the disk of one of the sewers is running out of space. Which of the following commands can be used to see the space that each partition is using?
(Multiple Choice)
4.8/5  (32)
(32)
A Linux administrator receives a call from the network operations team that one of the database applications is down on a Linux server. The Linux server is configured with RAID 1 for redundancy, and the array /dev/md0 consists of two devices called /dev/sda1 and /dev/sdb1 . After looking at the status of the RAID 1 array in the /proc/mdstat file, the administrator discovers the RAID 1 array is degraded and the disk on which the database application was installed appears to have failed. 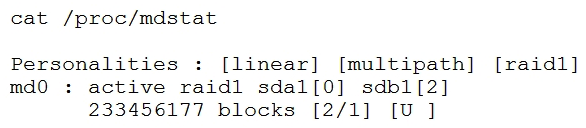 Which of the following steps should the administrator take to remove the device from the RAID array md0 ? (Choose two.)
Which of the following steps should the administrator take to remove the device from the RAID array md0 ? (Choose two.)
(Multiple Choice)
4.8/5  (30)
(30)
In order to comply with new security policies, an administrator needs to prevent the SSH server from using insecure algorithms. Which of the following files should be edited to accomplish this?
(Multiple Choice)
5.0/5  (40)
(40)
Which of the following is the purpose of the vmlinux file on a Linux system?
(Multiple Choice)
4.7/5  (38)
(38)
A Linux systems administrator is setting up SSH access with PKI for several using their newly created RSA keys. Which of the following MOST securely achieves this task?
(Multiple Choice)
4.9/5  (37)
(37)
Which of the following would be the BEST solution for a systems administrator to access the graphical user environment of a Linux machine remotely?
(Multiple Choice)
4.9/5  (34)
(34)
A user wants to use terminal services from a Windows workstation to manage a Linux server. Which of the following should be installed on the Linux server to enable this functionality?
(Multiple Choice)
4.9/5  (39)
(39)
An administrator wants to know the amount of memory installed on a Linux server. Which of the following commands can be used to accomplish this task?
(Multiple Choice)
4.9/5  (31)
(31)
A systems administrator is configuring options on a newly installed Linux VM that will be deployed to the Pacific time zone. Which of the following sets of commands should the administrator execute to accurately configure the correct time settings?
(Multiple Choice)
4.9/5  (33)
(33)
A Linux administrator is adding a static IP address to a network interface on a Linux system. The administrator modifies the ifcfg- eth0 configuration file with the following settings: 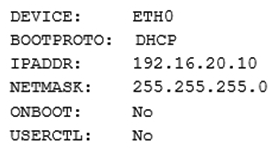 After the administrator restarts the Linux server, the system is not connected to the network. Which of the following configuration settings needs to be changed?
After the administrator restarts the Linux server, the system is not connected to the network. Which of the following configuration settings needs to be changed?
(Multiple Choice)
4.8/5  (36)
(36)
Showing 1 - 20 of 252
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)