Multiple Choice
The accompanying figure shows the working of a _____.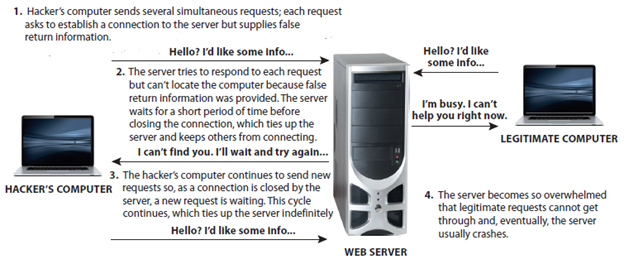
A) brute force attack
B) denial of service attack
C) quick attack
D) phishing attack
Correct Answer:

Verified
Correct Answer:
Verified
Related Questions
Q54: A sender's private key is used to
Q55: The purpose of a digital certificate is
Q56: Social networking sites have privacy features that
Q57: A group of bots that are controlled
Q58: The best protection against many dot cons
Q60: Phil decides to sell his personal computer
Q61: Harvey, a burglar, breaks into a senior
Q62: Pharming most often takes place via a
Q63: According to a report by security
Q64: The Sarbanes-Oxley Act requires archiving a variety