Multiple Choice
The accompanying figure shows the working of _____ .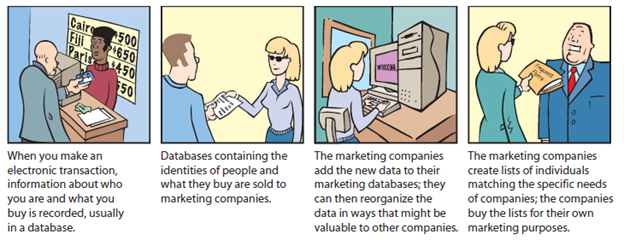
A) electronic profiling
B) big data
C) a surge suppressor
D) a data encryptor
Correct Answer:

Verified
Correct Answer:
Verified
Related Questions
Q32: _ is accessing someone else's unsecured Wi-Fi
Q33: _ occurs when someone obtains enough information
Q34: Harassment others via the Internet, such as
Q35: _ steal credit card or debit card
Q36: Rosanna has assembled her new personal computer
Q38: The _ has been controversial since it
Q39: _ involves terrorists launching attacks via the
Q40: Abby writes a program that redirects users
Q41: Antivirus can infect any device, including personal
Q42: Leslie, a computer hacker, creates a game