Multiple Choice
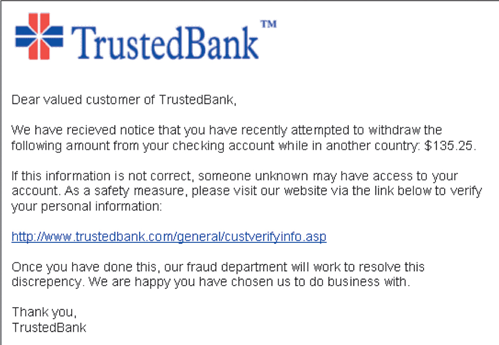
The accompanying figure shows a likely ____ scheme.
A) sniffing
B) phishing
C) hijacking
D) adware
Correct Answer:

Verified
Correct Answer:
Verified
Related Questions
Q9: Abby is a human resource director. She
Q10: Which of the following is NOT true
Q11: Computer hacking involves invading someone else's computer
Q12: Identity theft is an example of unethical
Q13: Which of the following is NOT an
Q15: A _ is an act intended to
Q16: An ergonomic workstation requires a wireless connection.
Q17: Abby is a human resource director. She
Q18: Public domain software provides remote access to
Q19: A time bomb virus replicates itself and