True/False
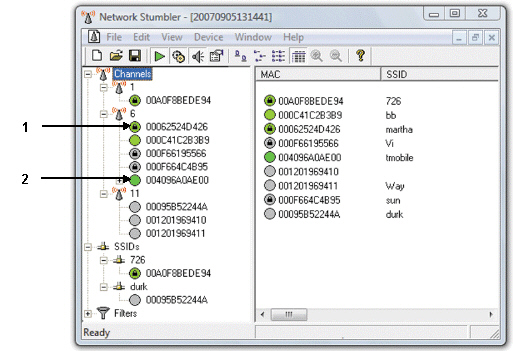 LANjackers use network-detecting and monitoring software, like the software shown in the figure above, to help locate and identify secured and unsecured networks.
LANjackers use network-detecting and monitoring software, like the software shown in the figure above, to help locate and identify secured and unsecured networks.
Correct Answer:

Verified
Correct Answer:
Verified
Related Questions
Q27: A virus _ is a file that
Q28: Your coworker, Casey, asks you to explain
Q29: <img src="https://d2lvgg3v3hfg70.cloudfront.net/TBX8740/.jpg" alt=" The device shown
Q30: Authentication protocols that use more than one
Q31: A(n)_ verifies a user ID and guarantees
Q33: _ scrambles the data transmitted between wireless
Q34: _ authentication verifies identity using two independent
Q35: Describe at least five tips for keeping
Q36: _ protocol refers to any method that
Q37: You have just been hired as an