Multiple Choice
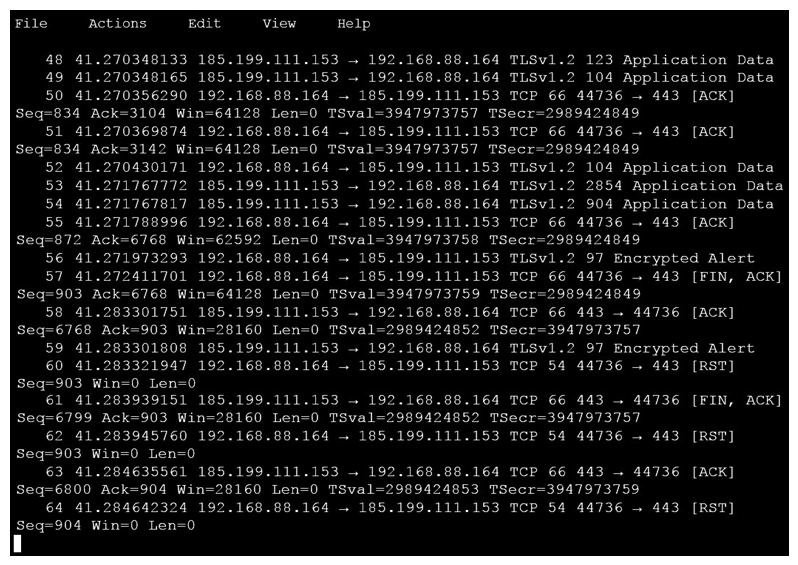 An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication. Which obfuscation technique is the attacker using?
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication. Which obfuscation technique is the attacker using?
A) Base64 encoding
B) transport layer security encryption
C) SHA-256 hashing
D) ROT13 encryption
Correct Answer:

Verified
Correct Answer:
Verified
Q63: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q64: How does certificate authority impact a security
Q65: An engineer is investigating a case of
Q66: When trying to evade IDS/IPS devices, which
Q67: Which two elements are assets in the
Q69: Which action should be taken if the
Q70: What is a difference between tampered and
Q71: During which phase of the forensic process
Q72: Which category relates to improper use or
Q73: What should a security analyst consider when