Multiple Choice
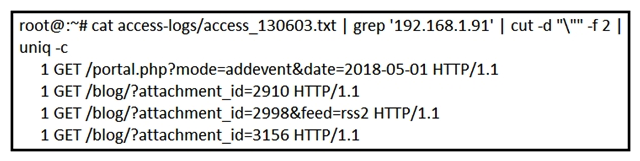 Refer to the exhibit. What is depicted in the exhibit?
Refer to the exhibit. What is depicted in the exhibit?
A) Windows Event logs
B) Apache logs
C) IIS logs
D) UNIX-based syslog
Correct Answer:

Verified
Correct Answer:
Verified
Related Questions
Q48: How is attacking a vulnerability categorized?<br>A) action
Q49: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q50: What does an attacker use to determine
Q51: At which layer is deep packet inspection
Q52: Which filter allows an engineer to filter
Q54: Which two elements of the incident response
Q55: What is the virtual address space for
Q56: An analyst received an alert on their
Q57: Which type of attack occurs when an
Q58: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the