Multiple Choice
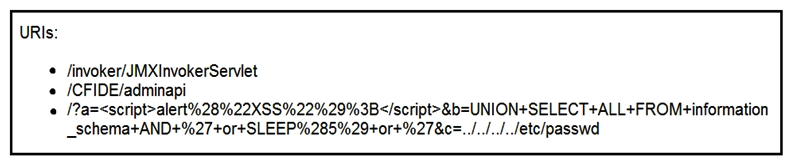 Refer to the exhibit. At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests from known malicious Internet scanners?
Refer to the exhibit. At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests from known malicious Internet scanners?
A) exploitation
B) actions on objectives
C) delivery
D) reconnaissance
Correct Answer:

Verified
Correct Answer:
Verified
Related Questions
Q7: What is idempotence?<br>A) the assurance of system
Q8: An engineer received multiple reports from users
Q9: A logistic company must use an outdated
Q10: What is a limitation of cyber security
Q11: An engineer received an alert of a
Q13: Which bash command will print all lines
Q14: An analyst is alerted for a malicious
Q15: The incident response team receives information about
Q16: Refer to the exhibit. What is occurring
Q17: A SIEM tool fires an alert about