Multiple Choice
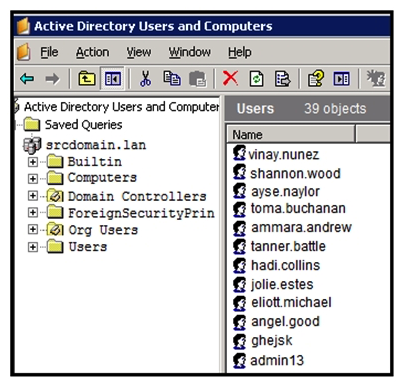 Refer to the exhibit. An engineer is investigating a case with suspicious usernames within the active directory. After the engineer investigates and cross-correlates events from other sources, it appears that the 2 users are privileged, and their creation date matches suspicious network traffic that was initiated from the internal network 2 days prior. Which type of compromise is occurring?
Refer to the exhibit. An engineer is investigating a case with suspicious usernames within the active directory. After the engineer investigates and cross-correlates events from other sources, it appears that the 2 users are privileged, and their creation date matches suspicious network traffic that was initiated from the internal network 2 days prior. Which type of compromise is occurring?
A) compromised insider
B) compromised root access
C) compromised database tables
D) compromised network
Correct Answer:

Verified
Correct Answer:
Verified
Q55: Refer to the exhibit. A threat actor
Q56: A SOC team is informed that a
Q57: An engineer implemented a SOAR workflow to
Q58: What is the impact of hardening machine
Q59: What is the difference between process orchestration
Q61: An engineer receives a report that indicates
Q62: An engineer detects an intrusion event inside
Q63: Where do threat intelligence tools search for
Q64: An engineer notices that every Sunday night,
Q65: The incident response team was notified of