Multiple Choice
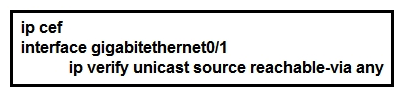 Refer to the exhibit. Router 1 was experiencing a DDoS attack that was traced to interface gigabitethernet0/1. Which statement about this configuration is true?
Refer to the exhibit. Router 1 was experiencing a DDoS attack that was traced to interface gigabitethernet0/1. Which statement about this configuration is true?
A) Router 1 accepts all traffic that ingresses and egresses interface gigabitethernet0/1.
B) Router 1 drops all traffic that ingresses interface gigabitethernet0/1 that has a FIB entry that exits a different interface.
C) Router 1 accepts source addresses that have a match in the FIB that indicates it is reachable through a real interface.
D) Router 1 accepts source addresses on interface gigabitethernet0/1 that are private addresses.
Correct Answer:

Verified
Correct Answer:
Verified
Q28: Which regular expression query modifier function indicates
Q29: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q30: What is the characteristic of the TI-LFA?<br>A)
Q31: How does model-driven telemetry use YANG?<br>A) to
Q32: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q34: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q35: Which additional feature does MPLS DiffServ tunneling
Q36: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q37: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1178/.jpg" alt=" Refer to the
Q38: Which utility can you use to locate