Multiple Choice
A company has two AWS accounts, each containing one VPC. The first VPC has a VPN connection with its corporate network. The second VPC, without a VPN, hosts an Amazon Aurora database cluster in private subnets. Developers manage the Aurora database from a bastion host in a public subnet as shown in the image. 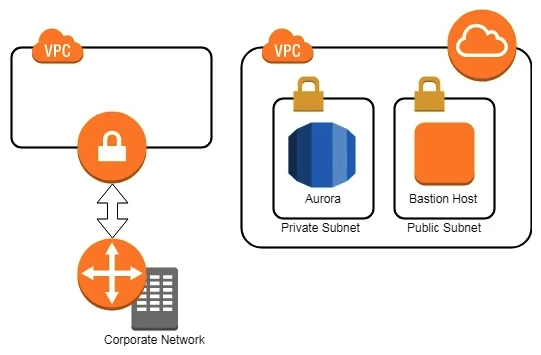 A security review has flagged this architecture as vulnerable, and a Security Engineer has been asked to make this design more secure. The company has a short deadline and a second VPN connection to the Aurora account is not possible. How can a Security Engineer securely set up the bastion host?
A security review has flagged this architecture as vulnerable, and a Security Engineer has been asked to make this design more secure. The company has a short deadline and a second VPN connection to the Aurora account is not possible. How can a Security Engineer securely set up the bastion host?
A) Move the bastion host to the VPC with VPN connectivity. Create a VPC peering relationship between the bastion host VPC and Aurora VPC.
B) Create a SSH port forwarding tunnel on the Developer's workstation to the bastion host to ensure that only authorized SSH clients can access the bastion host.
C) Move the bastion host to the VPC with VPN connectivity. Create a cross-account trust relationship between the bastion VPC and Aurora VPC, and update the Aurora security group for the relationship.
D) Create an AWS Direct Connect connection between the corporate network and the Aurora account, and adjust the Aurora security group for this connection.
Correct Answer:

Verified
Correct Answer:
Verified
Q95: A company became aware that one of
Q96: A Security Engineer has created an Amazon
Q97: A company is developing a highly resilient
Q98: An AWS account includes two S3 buckets:
Q99: Auditors for a health care company have
Q101: A company's Chief Security Officer has requested
Q102: Developers in an organization have moved from
Q103: The InfoSec team has mandated that in
Q104: A Security Engineer must implement mutually authenticated
Q105: To meet regulatory requirements, a Security Engineer