Multiple Choice
A recent security audit identified that a company's application team injects database credentials into the environment variables of an AWS Fargate task. The company's security policy mandates that all sensitive data be encrypted at rest and in transit. Which combination of actions should the security team take to make the application compliant with the security policy?
A) Store the credentials securely in a file in an Amazon S3 bucket with restricted access to the application team IAM role. Ask the application team to read the credentials from the S3 object instead.
B) Create an AWS Secrets Manager secret and specify the key/value pairs to be stored in this secret.
C) Modify the application to pull credentials from the AWS Secrets Manager secret instead of the environment variables.
D) Add the following statement to the container instance IAM role policy: 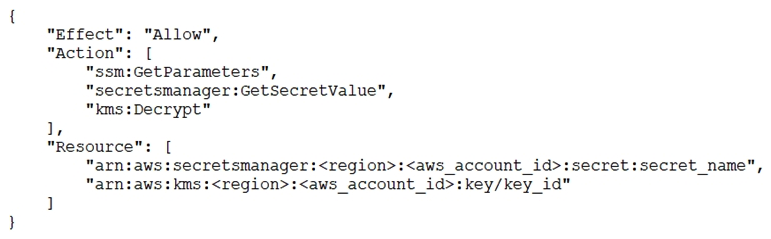
E) Add the following statement to the task execution role policy 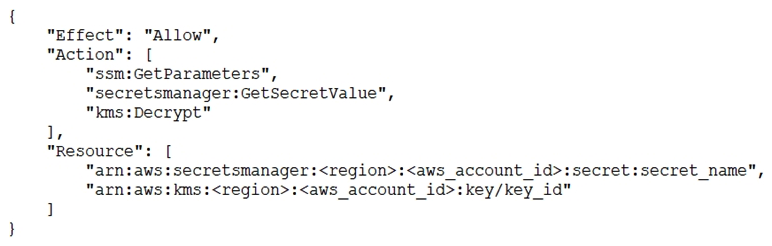
Correct Answer:

Verified
Correct Answer:
Verified
Q148: A company's architecture requires that its three
Q149: During a manual review of system logs
Q150: A company had one of its Amazon
Q151: A company has multiple AWS accounts that
Q152: A security engineer is responsible for providing
Q154: A company's web application is hosted on
Q155: A company is undergoing a layer 3
Q156: An application makes calls to AWS services
Q157: An application running on Amazon EC2 instances
Q158: The Security Engineer has discovered that a