Multiple Choice
A security engineer noticed an anomaly within a company EC2 instance as shown in the image. The engineer must now investigate what is causing the anomaly. 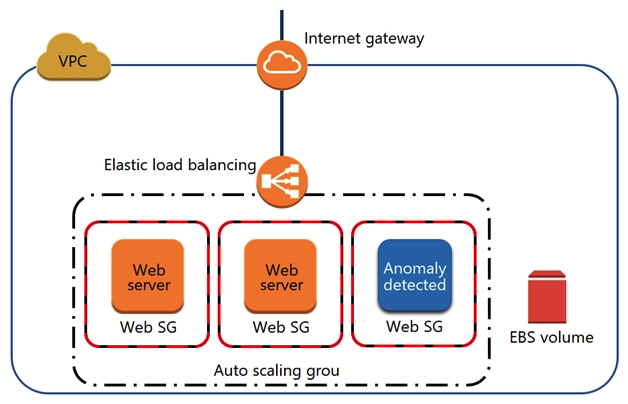 What are the MOST effective steps to take to ensure that the instance is not further manipulated, while allowing the engineer to understand what happened?
What are the MOST effective steps to take to ensure that the instance is not further manipulated, while allowing the engineer to understand what happened?
A) Remove the instance from the Auto Scaling group. Place the instance within an isolation security group, detach the EBS volume, launch an EC2 instance with a forensic toolkit, and attach the EBS volume to investigate.
B) Remove the instance from the Auto Scaling group and the Elastic Load Balancer. Place the instance within an isolation security group, launch an EC2 instance with a forensic toolkit, and allow the forensic toolkit image to connect to the suspicious instance to perform the investigation.
C) Remove the instance from the Auto Scaling group. Place the instance within an isolation security group, launch an EC2 instance with a forensic toolkit, and use the forensic toolkit image to deploy an ENI as a network span port to inspect all traffic coming from the suspicious instance.
D) Remove the instance from the Auto Scaling group and the Elastic Load Balancer. Place the instance within an isolation security group, make a copy of the EBS volume from a new snapshot, launch an EC2 instance with a forensic toolkit, and attach the copy of the EBS volume to investigate.
Correct Answer:

Verified
Correct Answer:
Verified
Q164: A Security Engineer who was reviewing AWS
Q165: A Security Engineer is asked to update
Q166: A company is storing data in Amazon
Q167: A large government organization is moving to
Q168: An organization wants to deploy a three-tier
Q170: The Development team receives an error message
Q171: A company has developed a new Amazon
Q172: While analyzing a company's security solution, a
Q173: The Security Engineer is given the following
Q174: A Security Engineer is setting up an