Multiple Choice
A security analyst sees some suspicious entries in a log file from a web server website, which has a form that allows customers to leave feedback on the company's products. The analyst believes a malicious actor is scanning the web form. To know which security controls to put in place, the analyst first needs to determine the type of activity occurring to design a control. Given the log below: 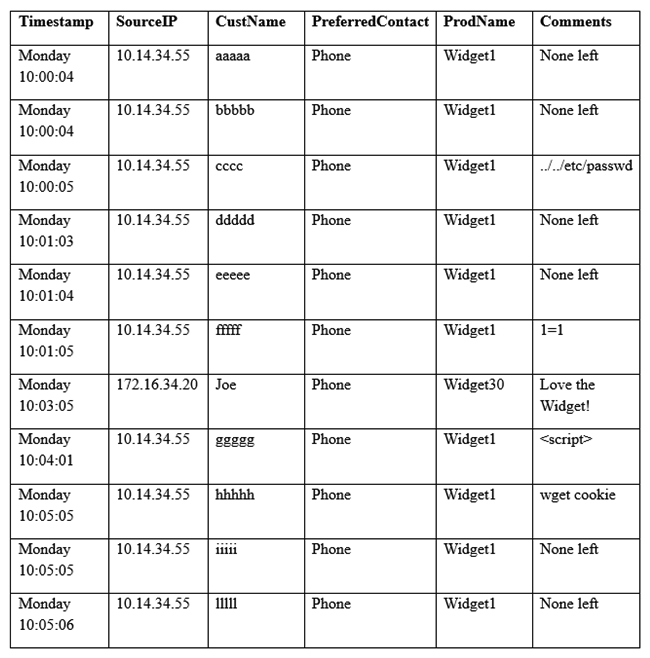 Which of the following is the MOST likely type of activity occurring?
Which of the following is the MOST likely type of activity occurring?
A) SQL injection
B) XSS scanning
C) Fuzzing
D) Brute forcing
Correct Answer:

Verified
Correct Answer:
Verified
Q187: A request has been approved for a
Q188: Following a recent outage, a systems administrator
Q189: A company uses an enterprise desktop imaging
Q190: An international e-commerce company has identified attack
Q191: While attending a meeting with the human
Q193: A deployment manager is working with a
Q194: A medical device company is implementing a
Q195: A team is at the beginning stages
Q196: Several recent ransomware outbreaks at a company
Q197: The audit team was only provided the