Multiple Choice
A security engineer successfully exploits an application during a penetration test. As proof of the exploit, the security engineer takes screenshots of how data was compromised in the application. Given the information below from the screenshot. 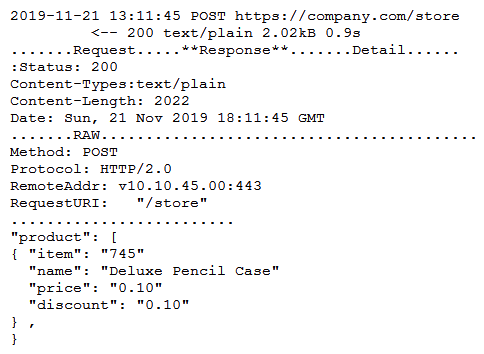 Which of the following tools was MOST likely used to exploit the application?
Which of the following tools was MOST likely used to exploit the application?
A) The engineer captured the data with a protocol analyzer, and then utilized Python to edit the data
B) The engineer queried the server and edited the data using an HTTP proxy interceptor
C) The engineer used a cross-site script sent via curl to edit the data
D) The engineer captured the HTTP headers, and then replaced the JSON data with a banner-grabbing tool
Correct Answer:

Verified
Correct Answer:
Verified
Q417: After embracing a BYOD policy, a company
Q418: A security engineer is assessing a new
Q419: As part of the development process for
Q420: A company has completed the implementation of
Q421: Given the following: <img src="https://d2lvgg3v3hfg70.cloudfront.net/C1257/.jpg" alt="Given the
Q423: An internal penetration tester finds a legacy
Q424: To meet an SLA, which of the
Q425: A systems administrator at a medical imaging
Q426: Which of the following may indicate a
Q427: A security architect has been assigned to