Multiple Choice
An information security officer is responsible for one secure network and one office network. Recent intelligence suggests there is an opportunity for attackers to gain access to the secure network due to similar login credentials across networks. To determine the users who should change their information, the information security officer uses a tool to scan a file with hashed values on both networks and receives the following data: 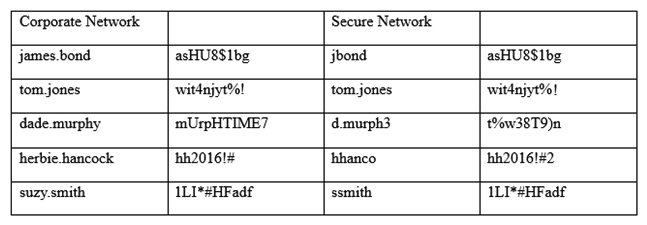 Which of the following tools was used to gather this information from the hashed values in the file?
Which of the following tools was used to gather this information from the hashed values in the file?
A) Vulnerability scanner
B) Fuzzer
C) MD5 generator
D) Password cracker
E) Protocol analyzer
Correct Answer:

Verified
Correct Answer:
Verified
Q157: A large industrial system's smart generator monitors
Q158: Users have reported that an internally developed
Q159: When implementing a penetration testing program, the
Q160: A recent security assessment revealed a web
Q161: A software development company lost customers recently
Q163: A company is not familiar with the
Q164: A user asks a security practitioner for
Q165: An organization is reviewing endpoint security solutions.
Q166: A company has decided to replace all
Q167: A firewall specialist has been newly assigned