Multiple Choice
After a breach involving the exfiltration of a large amount of sensitive data, a security analyst is reviewing the following firewall logs to determine how the breach occurred: 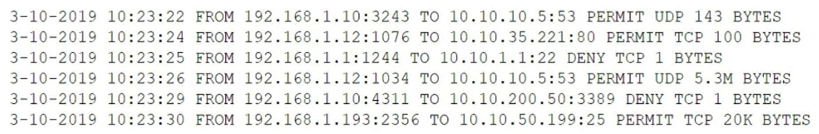 Which of the following IP addresses does the analyst need to investigate further?
Which of the following IP addresses does the analyst need to investigate further?
A) 192.168.1.1
B) 192.168.1.10
C) 192.168.1.12
D) 192.168.1.193
Correct Answer:

Verified
Correct Answer:
Verified
Q153: An analyst is performing penetration testing and
Q154: A security analyst recently discovered two unauthorized
Q155: Which of the following policies would state
Q156: A security analyst received a series of
Q157: A financial institution's business unit plans to
Q159: A company's marketing emails are either being
Q160: An information security analyst discovered a virtual
Q161: As part of an organization's information security
Q162: A security analyst is supporting an embedded
Q163: Which of the following BEST describes the