Multiple Choice
A security analyst has received reports of very slow, intermittent access to a public-facing corporate server. Suspecting the system may be compromised, the analyst runs the following commands: 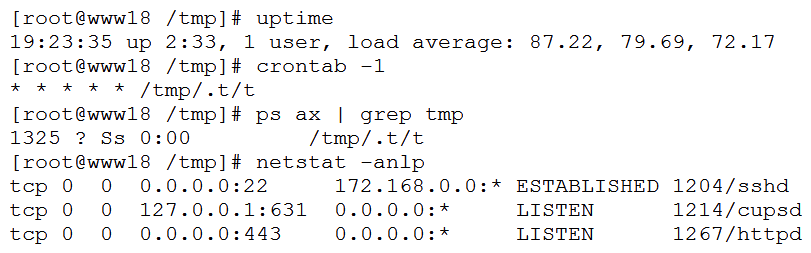 Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
A) Run crontab -r; rm -rf /tmp/.t to remove and disable the malware on the system. Run crontab -r; rm -rf /tmp/.t to remove and disable the malware on the system.
B) Examine the server logs for further indicators of compromise of a web application.
C) Run kill -9 1325 to bring the load average down so the server is usable again. kill -9 1325 to bring the load average down so the server is usable again.
D) Perform a binary analysis on the /tmp/.t/t file, as it is likely to be a rogue SSHD server. Perform a binary analysis on the /tmp/.t/t file, as it is likely to be a rogue SSHD server.
Correct Answer:

Verified
Correct Answer:
Verified
Q88: A critical server was compromised by malware,
Q89: A security analyst has observed several incidents
Q90: A security analyst is providing a risk
Q91: A security analyst for a large financial
Q92: A SIEM solution alerts a security analyst
Q94: An organization developed a comprehensive incident response
Q95: Which of the following should a database
Q96: A web-based front end for a business
Q97: Which of the following roles is ultimately
Q98: Which of the following technologies can be