Multiple Choice
A penetration tester identifies the following findings during an external vulnerability scan: 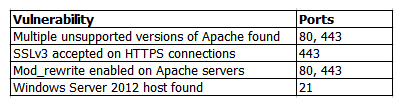 Which of the following attack strategies should be prioritized from the scan results above?
Which of the following attack strategies should be prioritized from the scan results above?
A) Obsolete software may contain exploitable components.
B) Weak password management practices may be employed.
C) Cryptographically weak protocols may be intercepted.
D) Web server configurations may reveal sensitive information.
Correct Answer:

Verified
Correct Answer:
Verified
Q155: A penetration tester successfully exploits a DMZ
Q156: The following command is run on a
Q157: A penetration tester discovers an anonymous FTP
Q158: Which of the following BEST describes some
Q159: A penetration tester has been asked to
Q160: A penetration tester successfully exploits a system,
Q161: A penetration tester compromises a system that
Q162: During a web application assessment, a penetration
Q163: A penetration tester is testing a banking
Q165: A penetration tester has performed a security