Multiple Choice
Click the exhibit button. 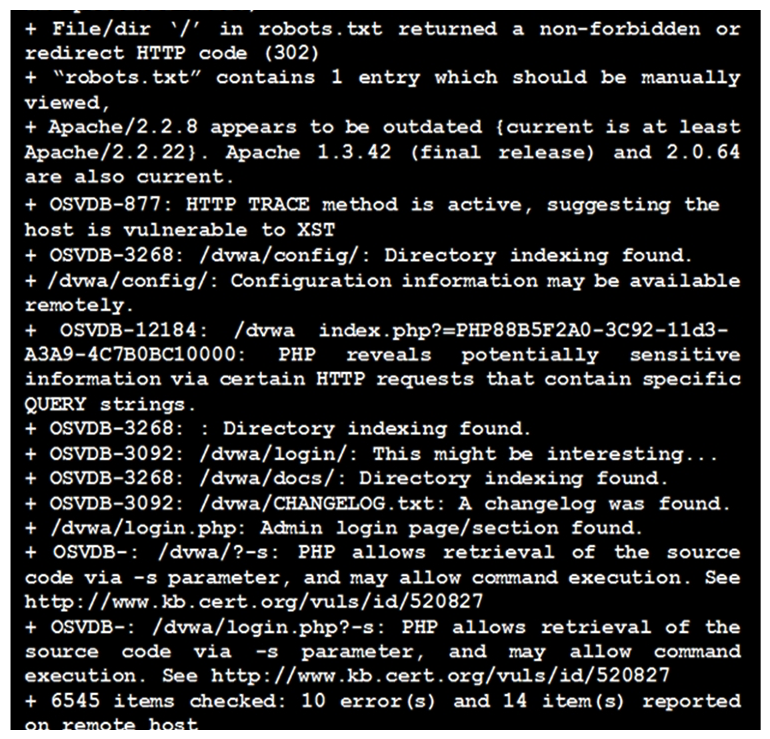 Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)
Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)
A) Arbitrary code execution
B) Session hijacking
C) SQL injection
D) Login credential brute-forcing
E) Cross-site request forgery
Correct Answer:

Verified
Correct Answer:
Verified
Q90: A penetration tester is testing a web
Q91: A penetration tester is reviewing the following
Q92: For which of the following reasons does
Q93: Black box penetration testing strategy provides the
Q94: A penetration tester is checking a script
Q96: A penetration tester is able to move
Q97: If a security consultant comes across a
Q98: While performing privilege escalation on a Windows
Q99: A penetration test was performed by an
Q100: Which of the following actions BEST matches