Related Questions
Q24: Who is responsible for decisions about security
Q30: The most common password of all in
Q32: What is Poulson's Law?
Q33: This is a situation in which the
Q34: Examples of multi-factor authentication are:<br>A) passwords and
Q35: If you receive an email from your
Q36: What is a challenge question?
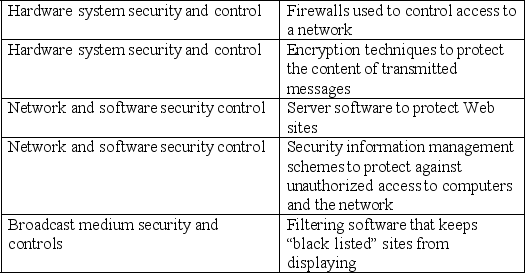
Q37: What security and controls should a company
Q37: It usually takes _ for someone in
Q38: The Deep Web is reputed to be