Multiple Choice
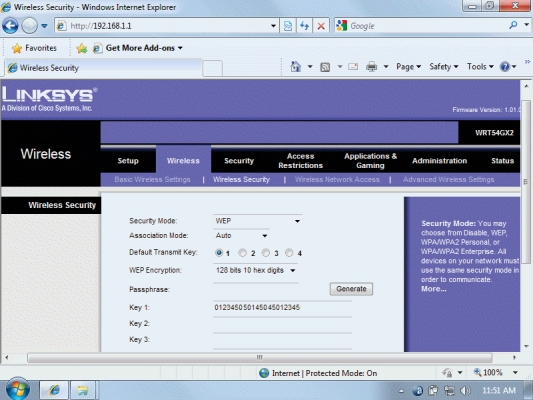
-In the figure above, the "Key 1:" that is shown is also referred to as a(n) ____ key.
A) encryption
B) part-time
C) password
D) portal
Correct Answer:

Verified
Correct Answer:
Verified
Related Questions
Q4: A(n) _ is issued by a certificate
Q5: The original wireless encryption was called _
Q6: <u>Coded</u> software scrambles your data by using
Q7: A typical _ scam begins with a
Q8: Case 22-1<br>Genevieve is in charge of Internet
Q10: _ typically protect works such as software,
Q11: _ refers to any physical method used
Q12: Most malicious code is stored in executable
Q13: A _ worm makes use of information
Q14: A _ uses a home-based computer and