Multiple Choice
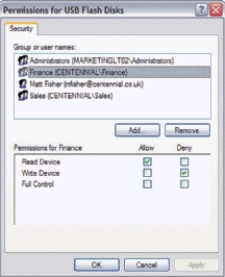
-____ software,such as that shown in the accompanying figure,can control which devices can be connected to an employee's computer.
A) Data-leakage prevention
B) Device authentication
C) Professional firewall
D) Network quarantine
Correct Answer:

Verified
Correct Answer:
Verified
Related Questions
Q6: Antispam programs are used to detect and
Q12: Botnets are a major security threat since
Q36: The _,implemented in 2001,grants federal authorities expanded
Q41: _ occurs whenever an individual gains access
Q43: Like a computer virus, a _ is
Q44: Phishing schemes use legitimate-looking e-mails to trick
Q45: How do firewalls work?
Q68: Private key encryption is also called symmetric
Q75: Possessed knowledge access systems use physical objects
Q82: The Fair and Accurate Credit Transactions Act